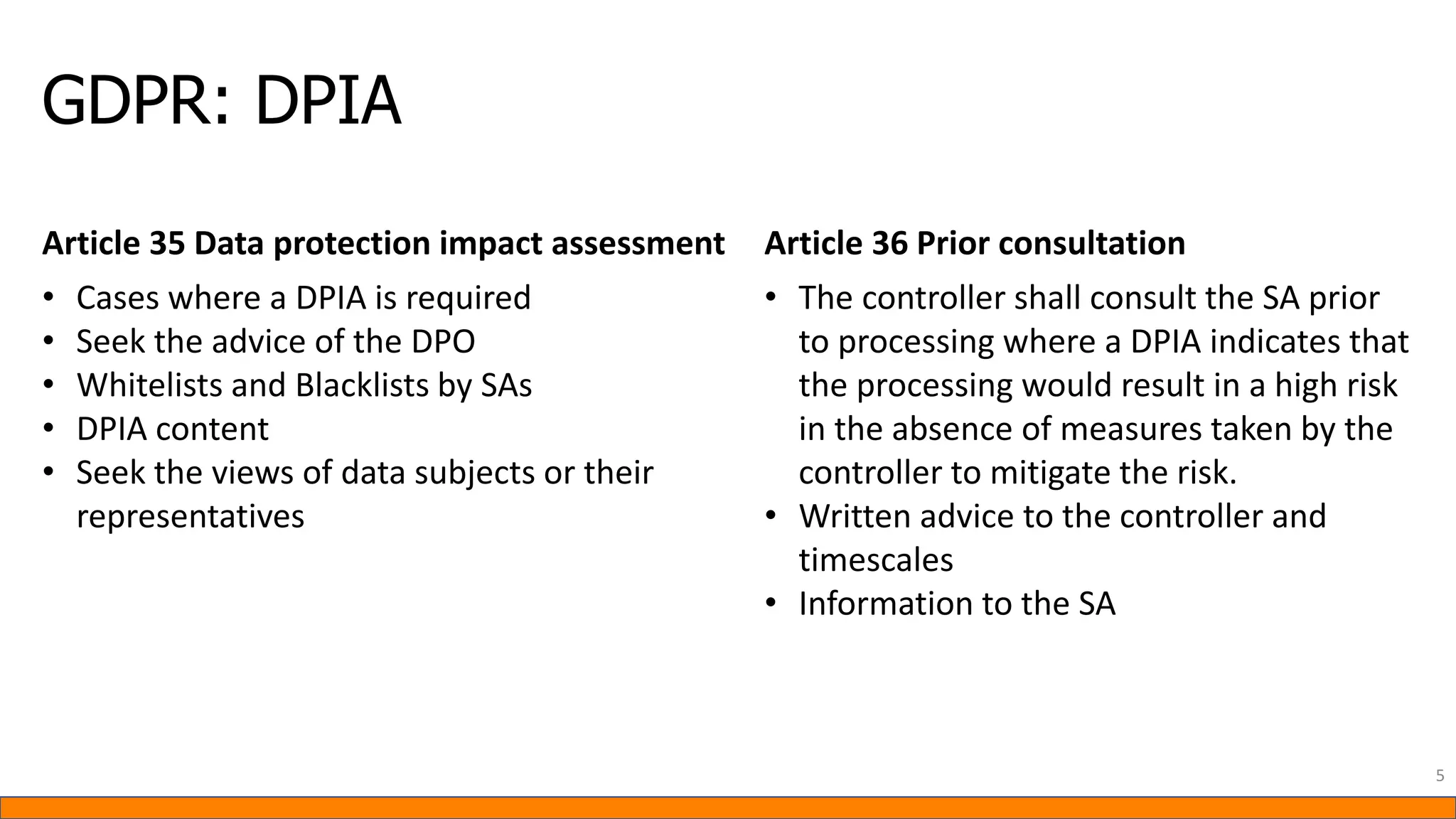
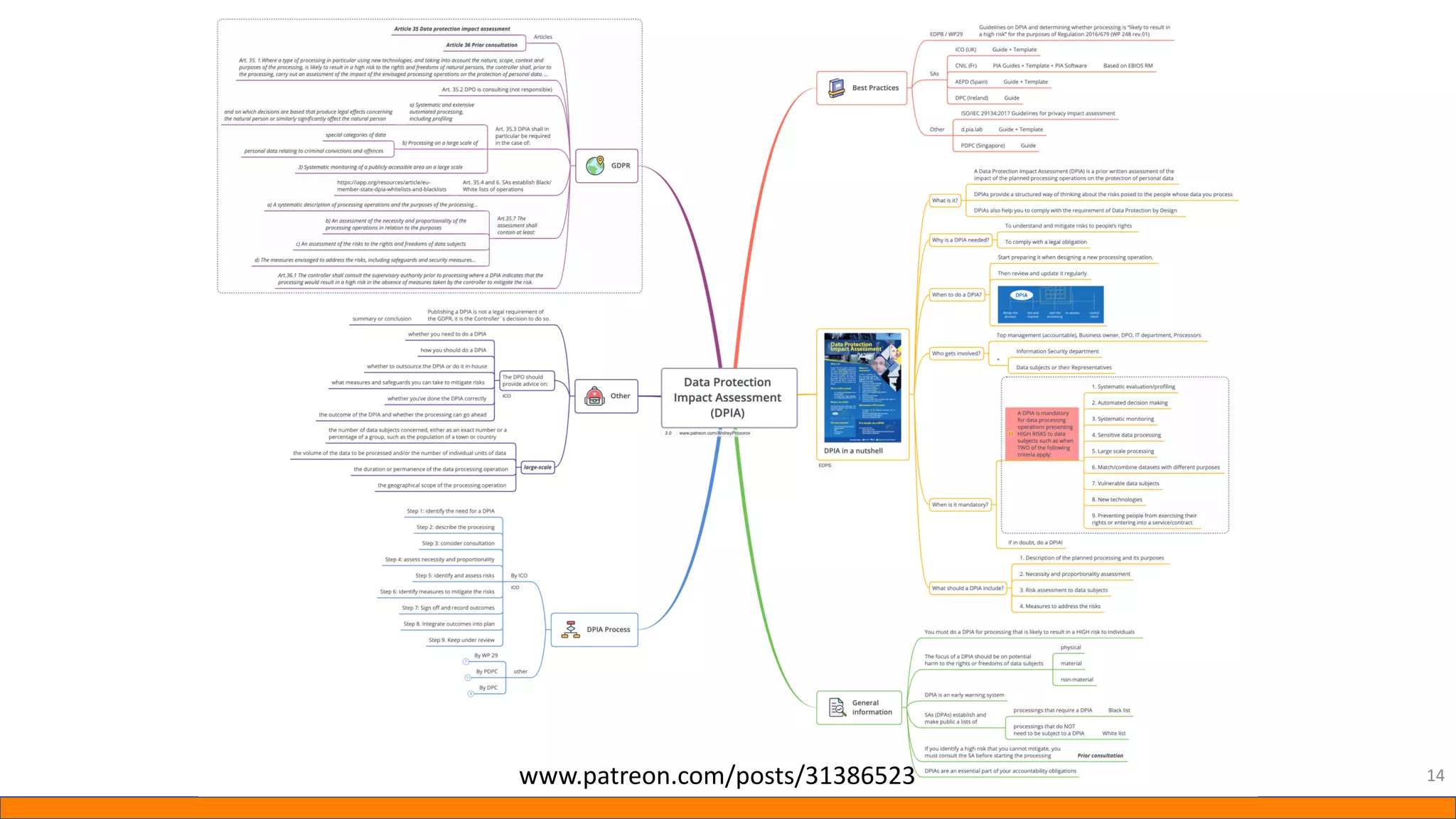
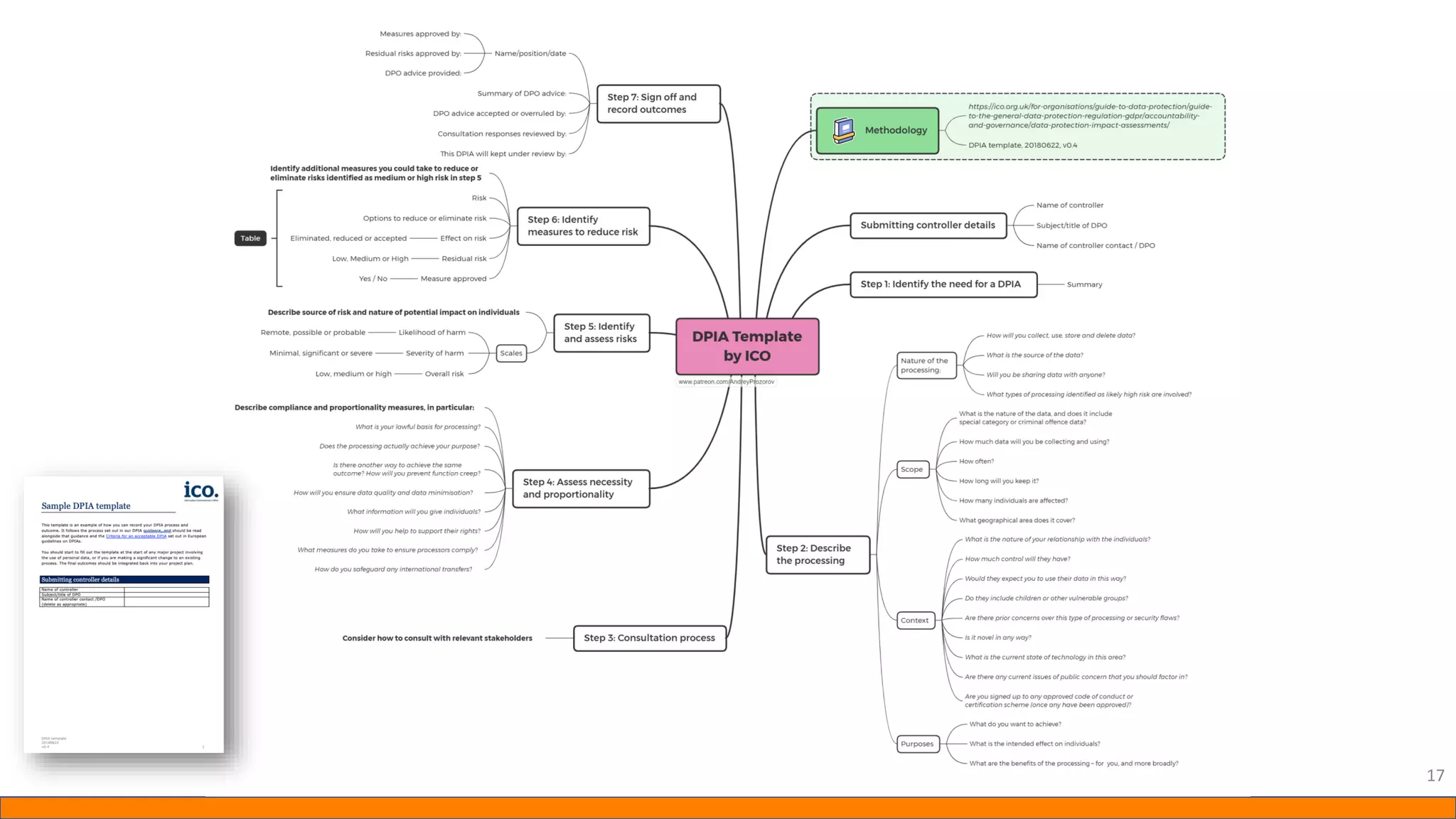
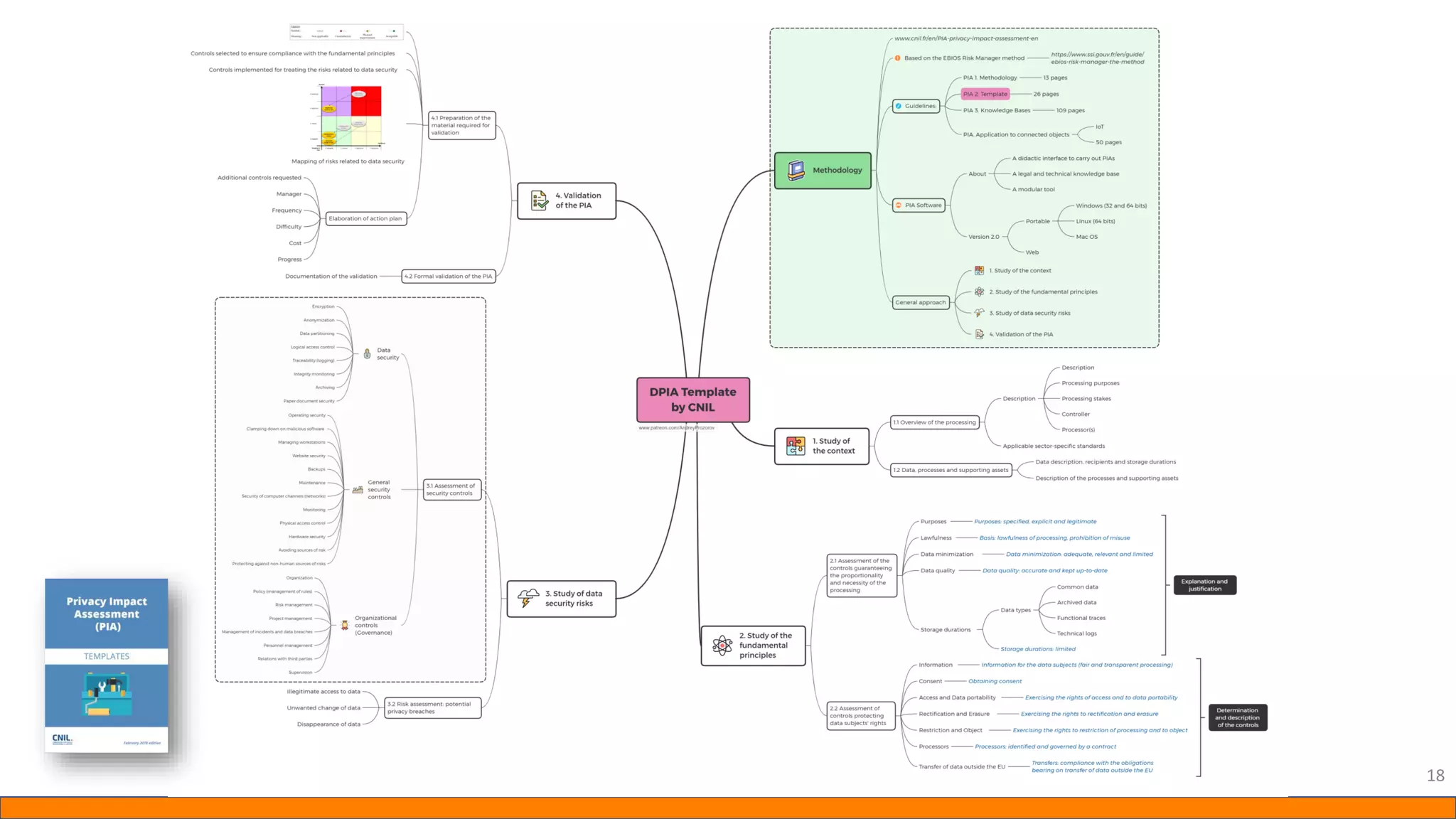
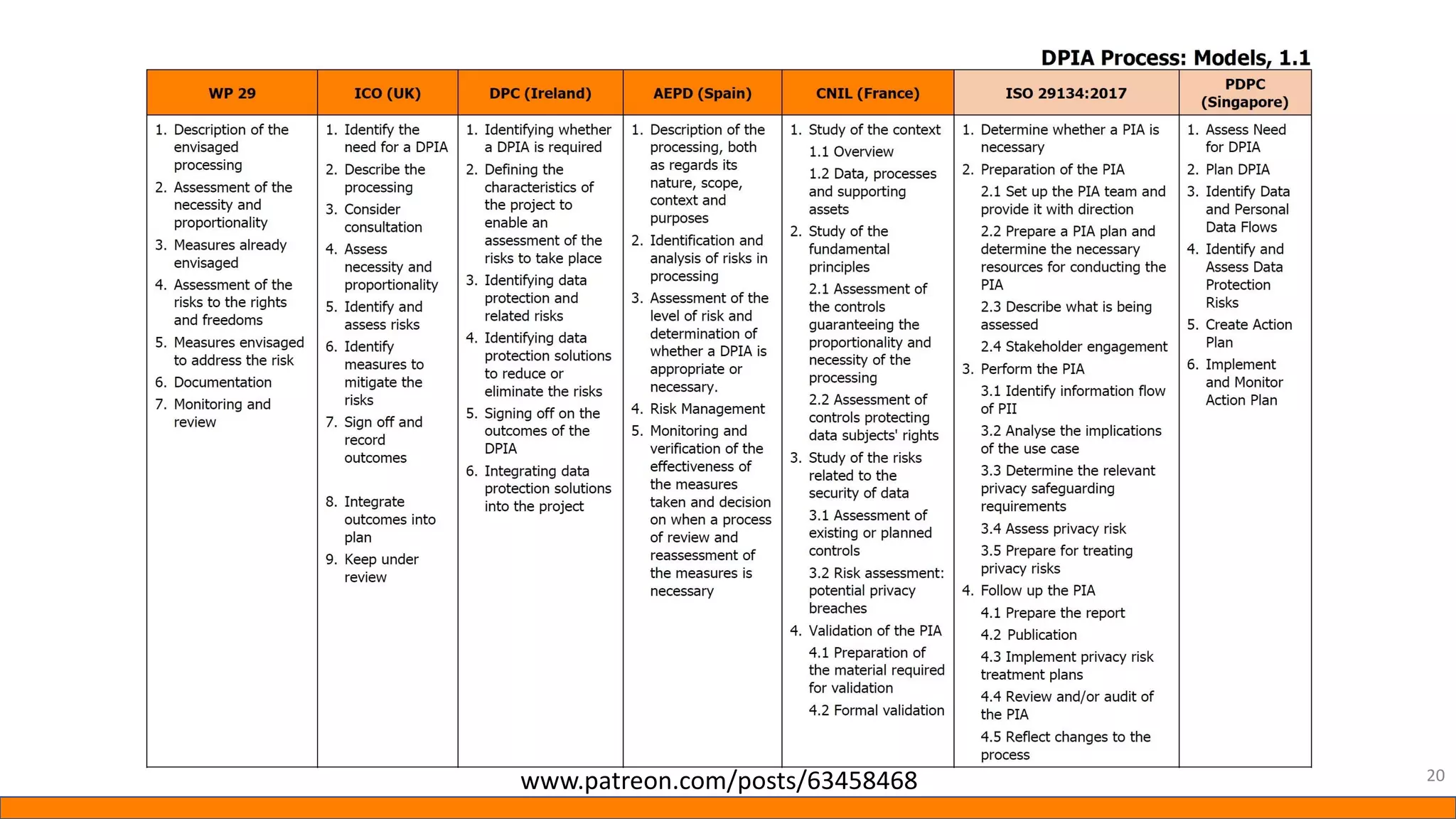
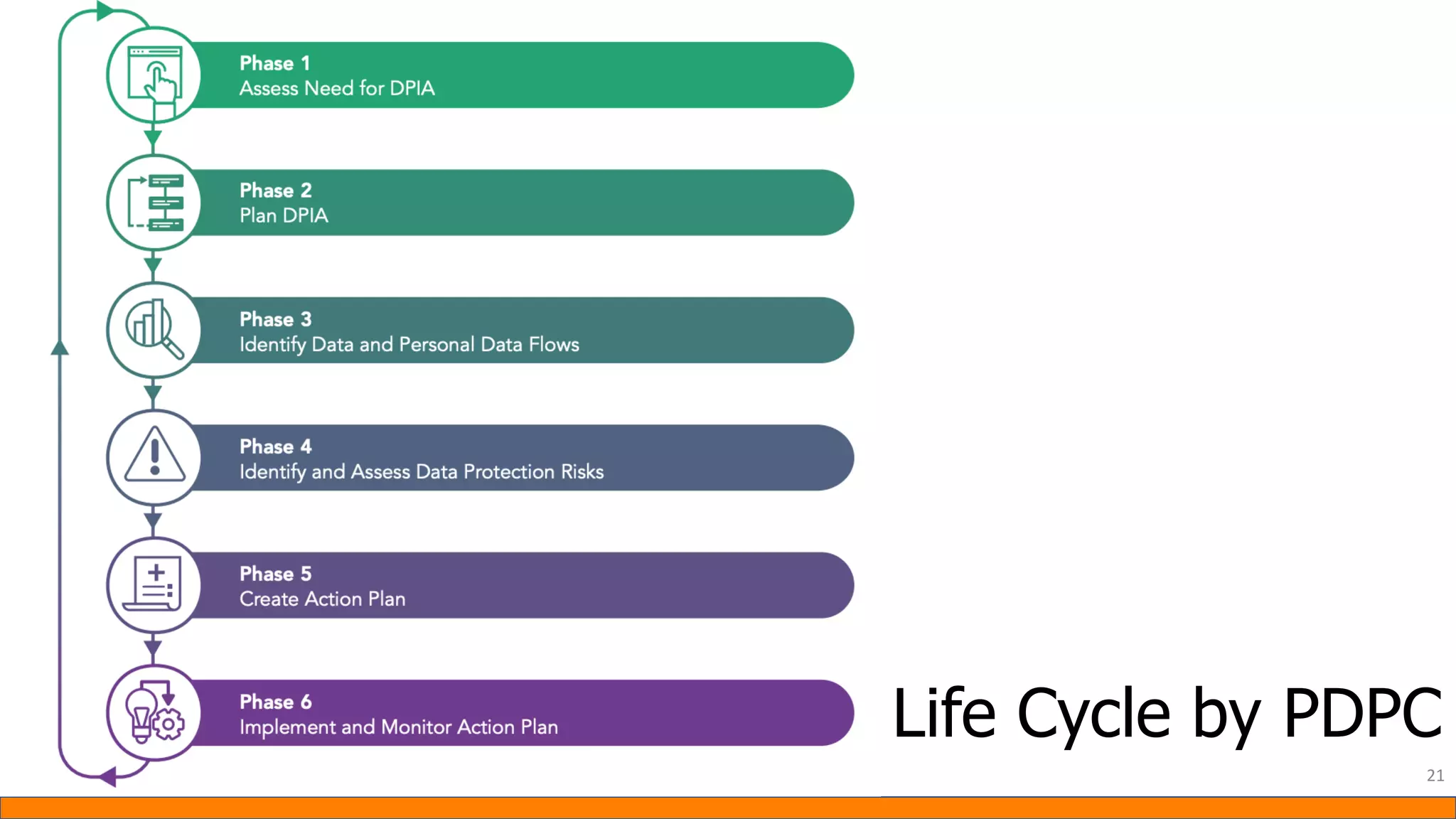
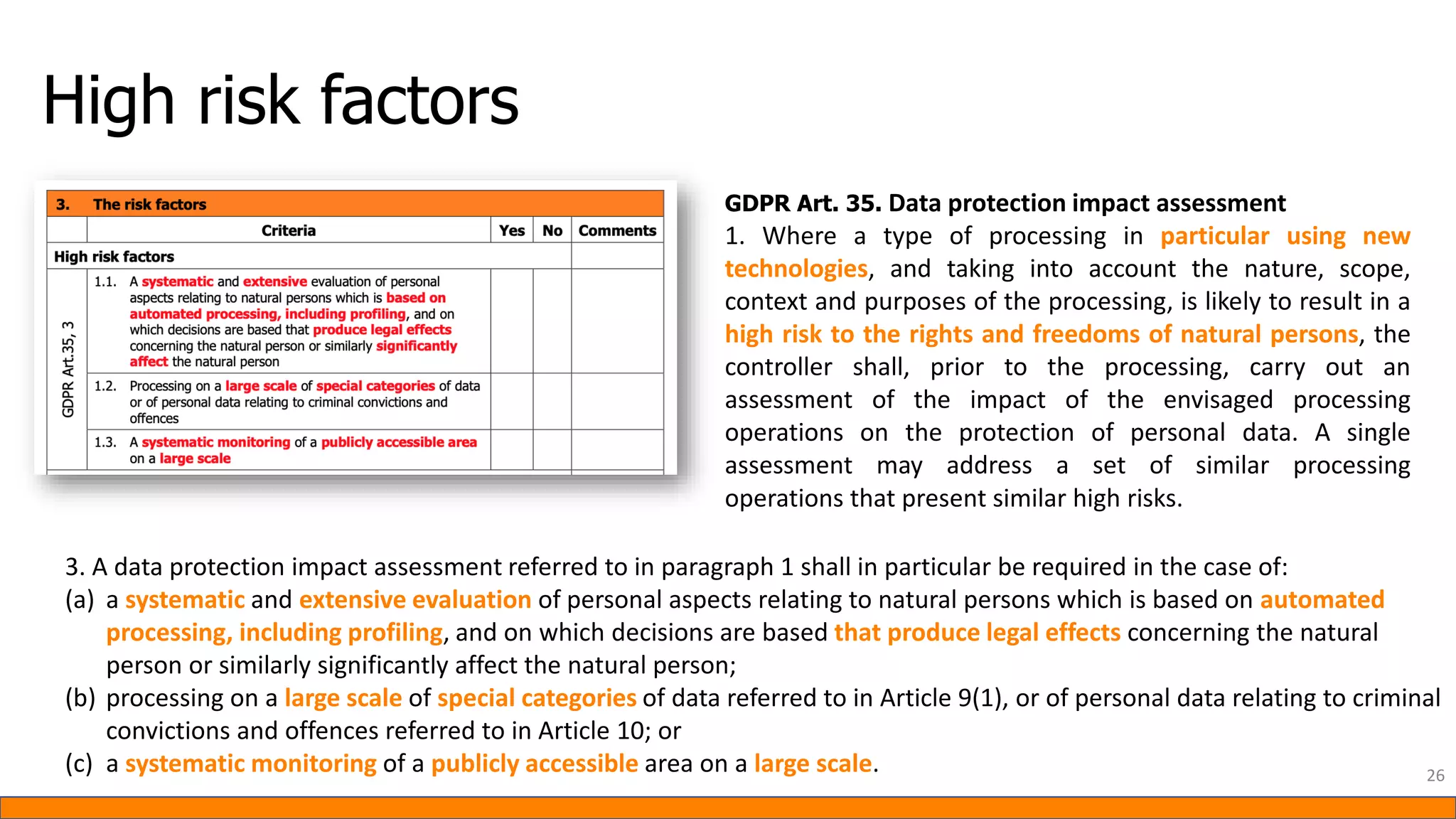
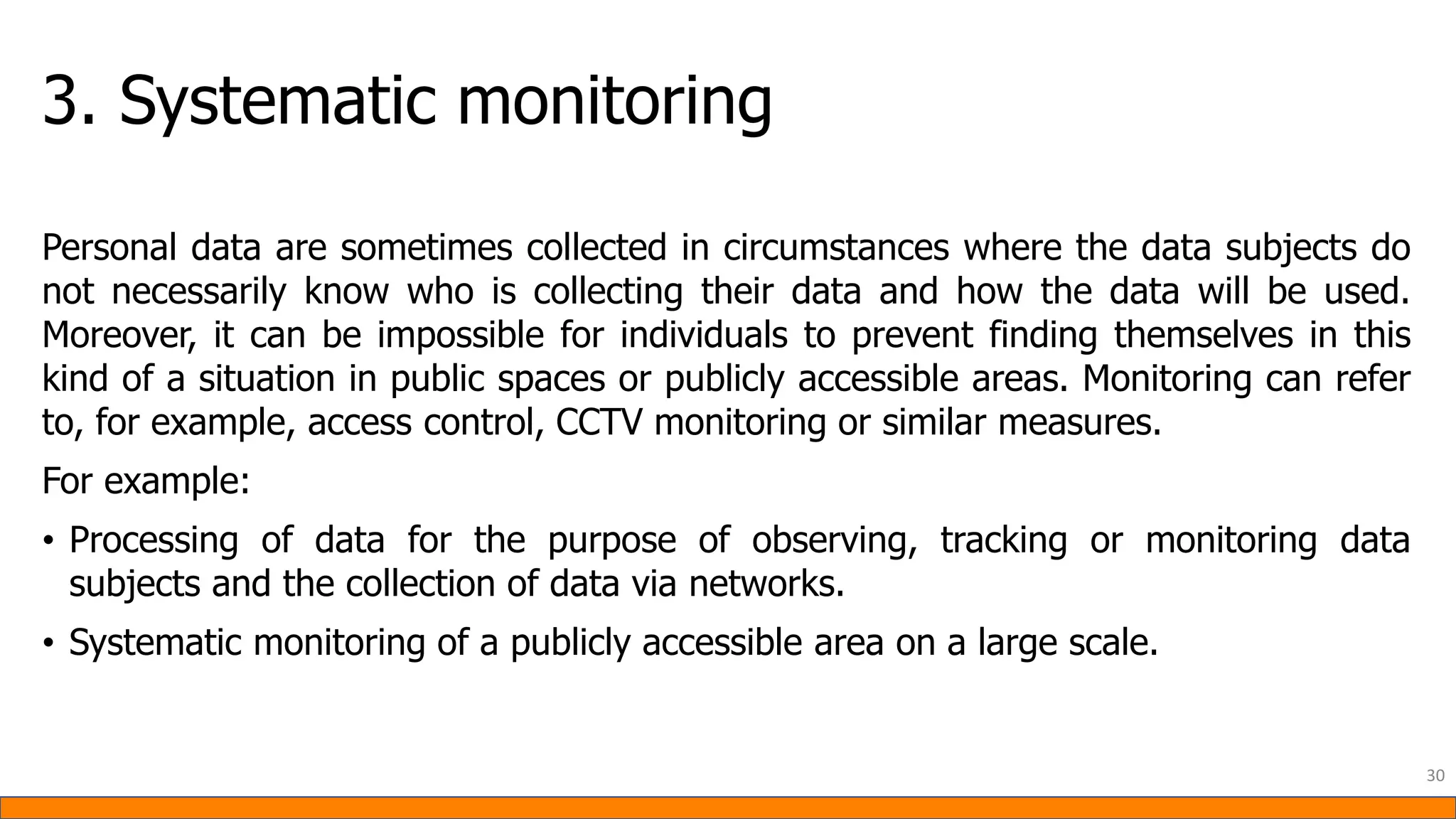
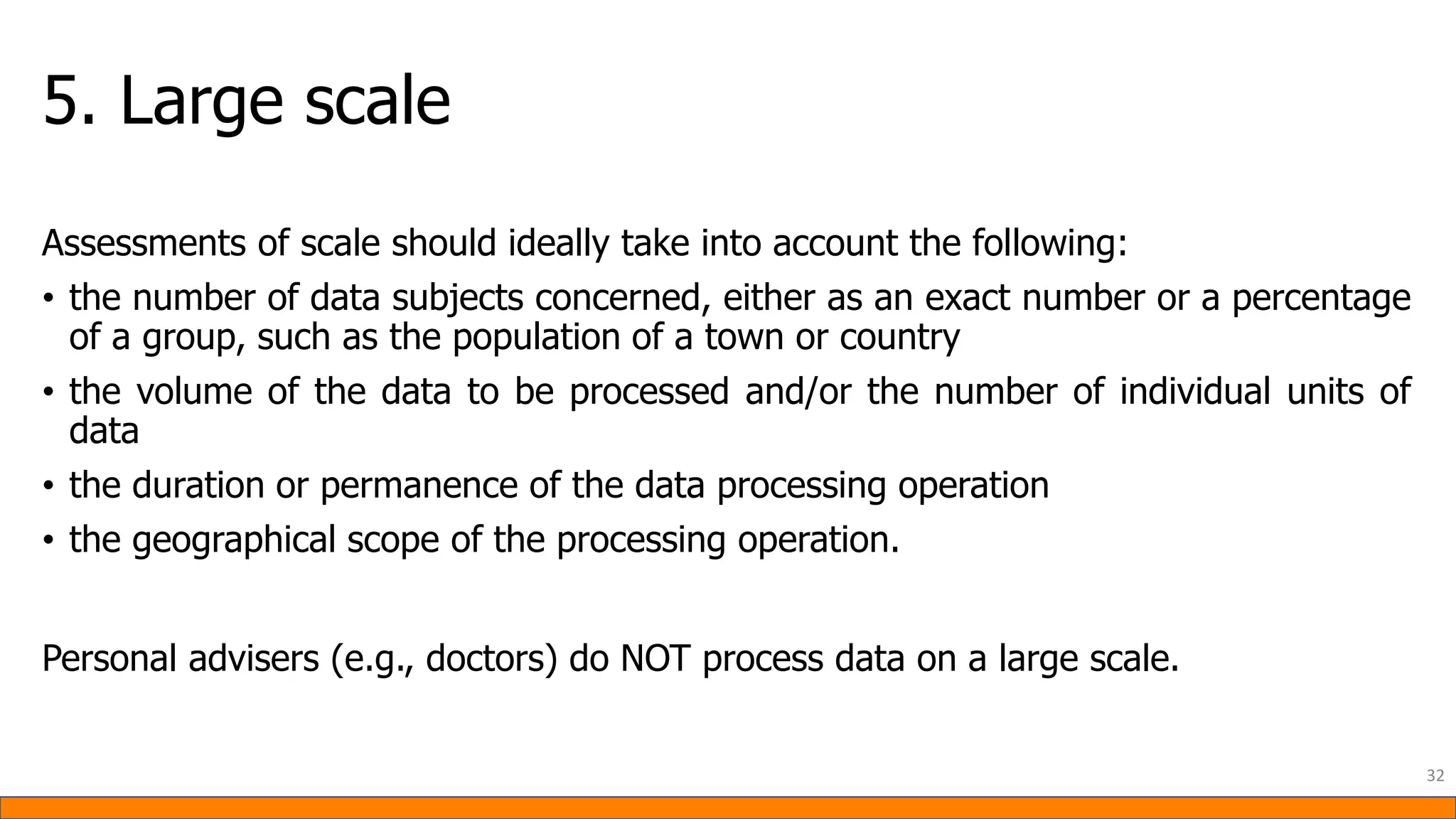
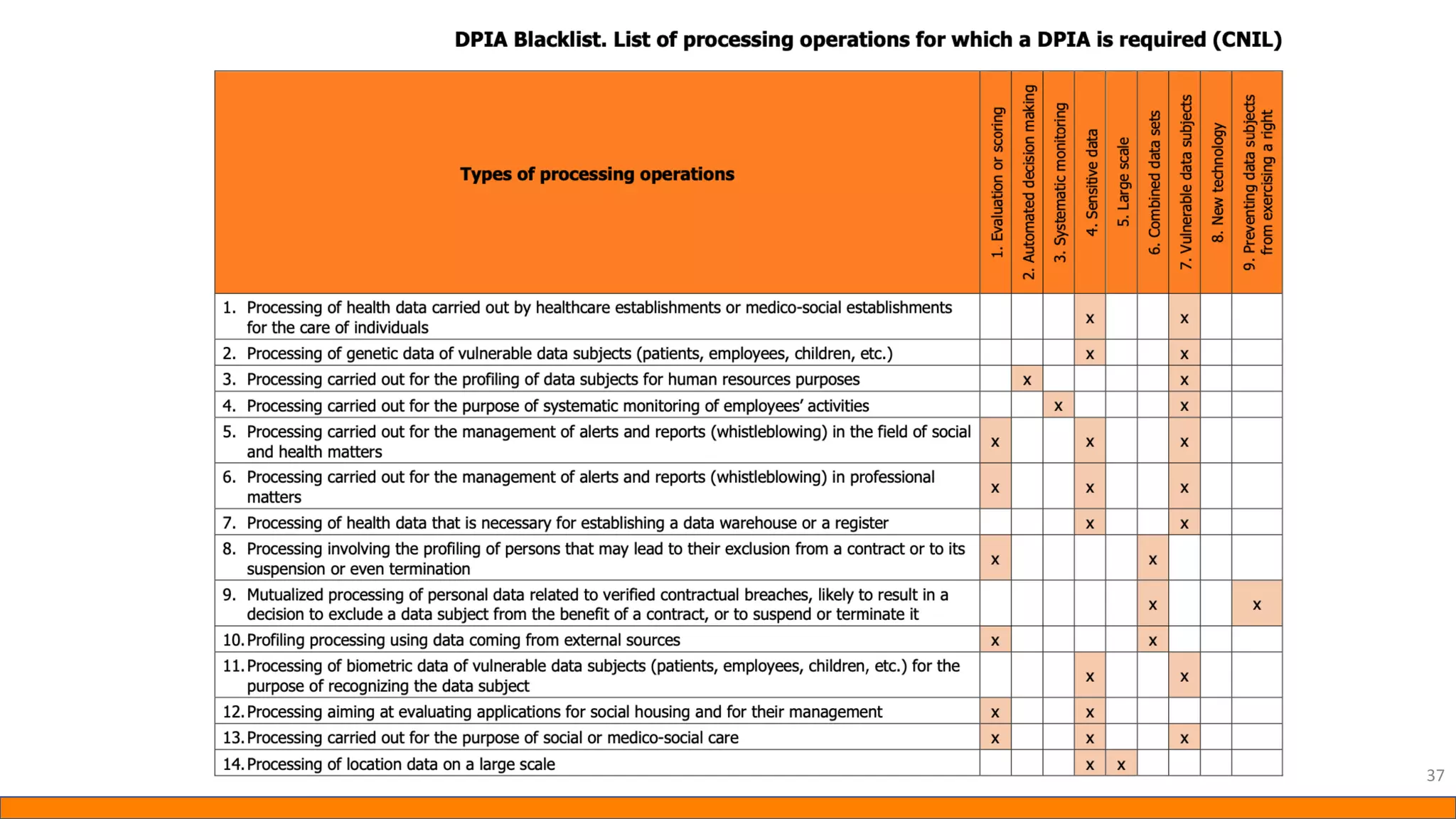
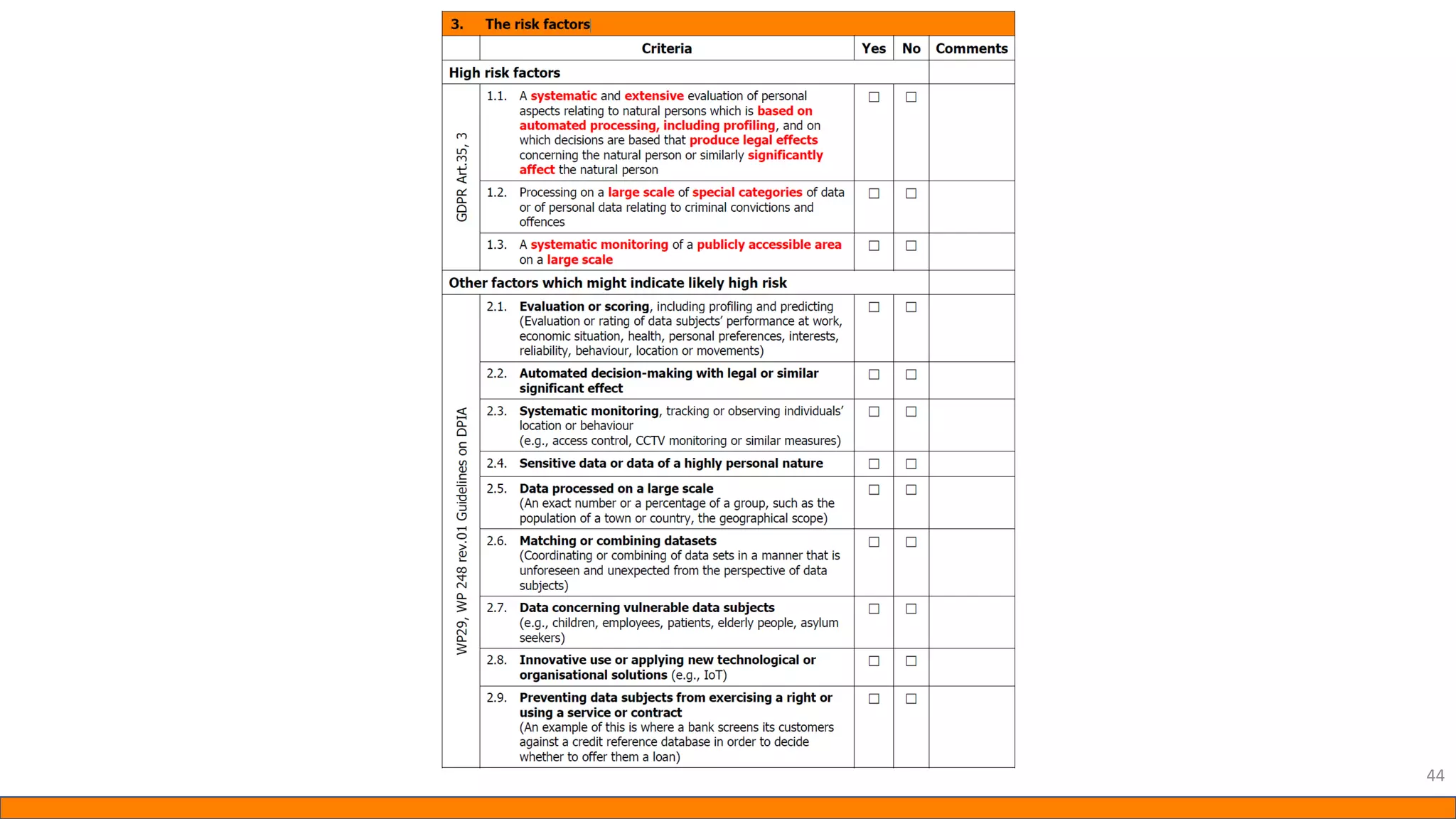
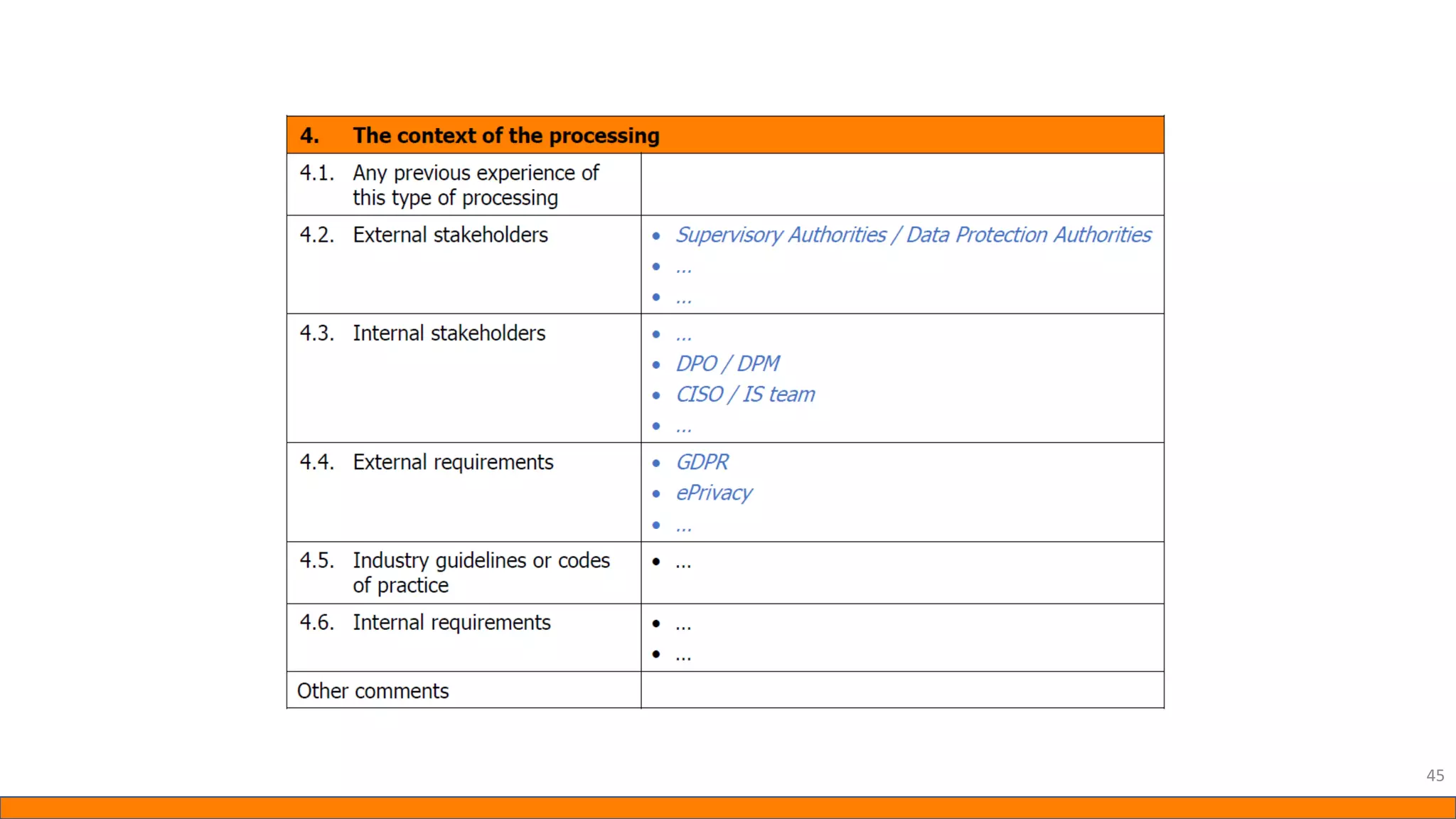
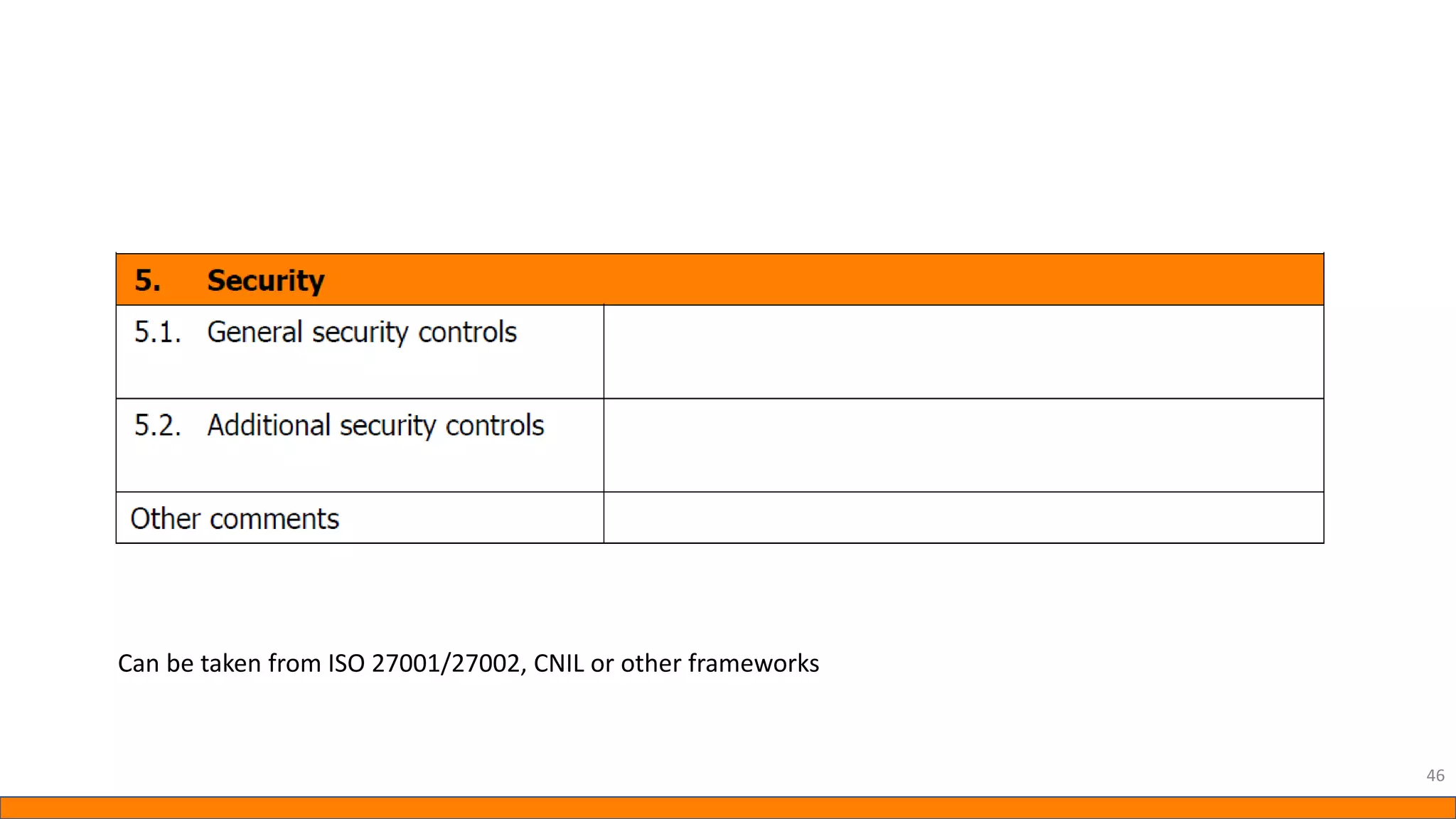
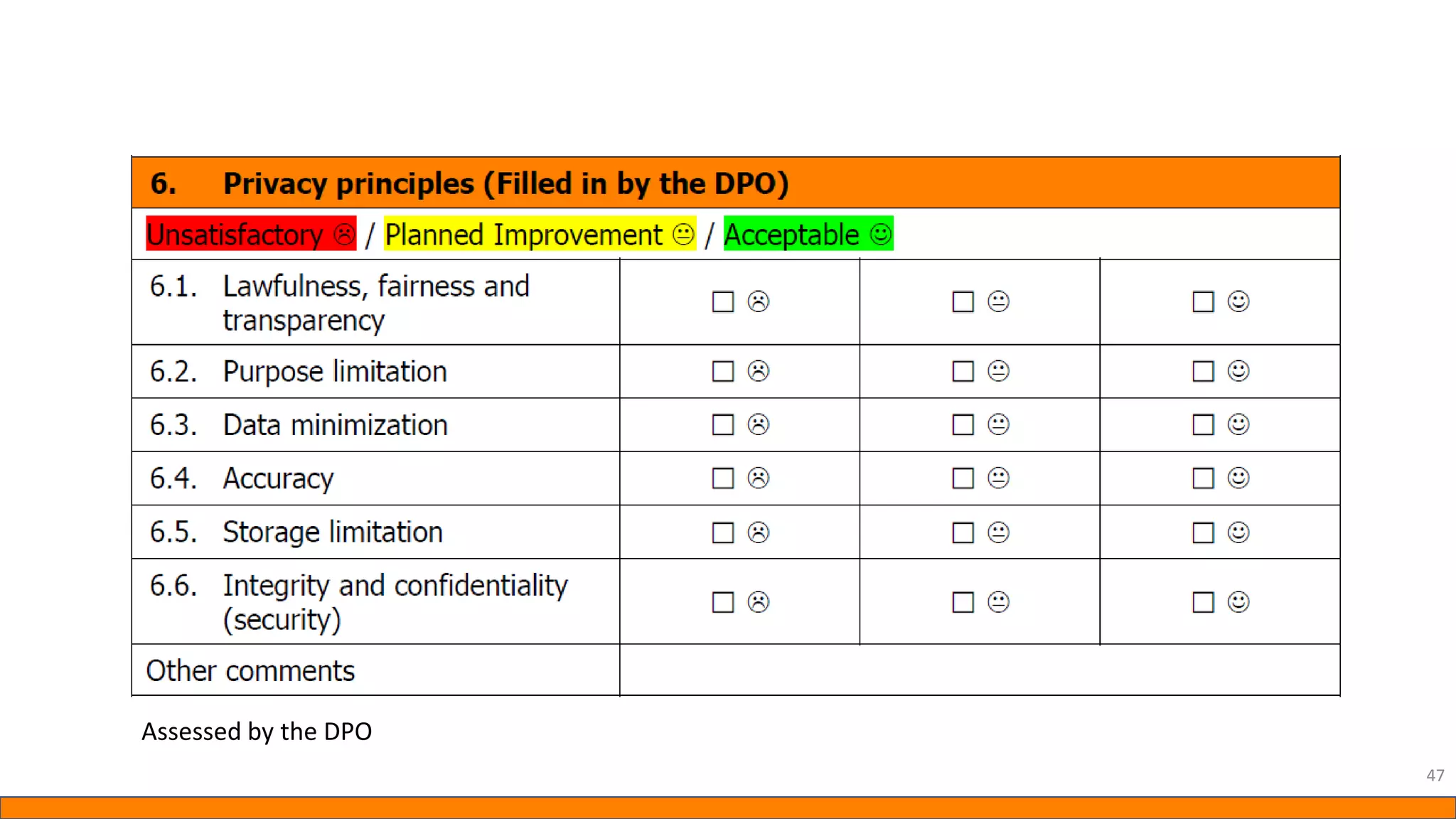
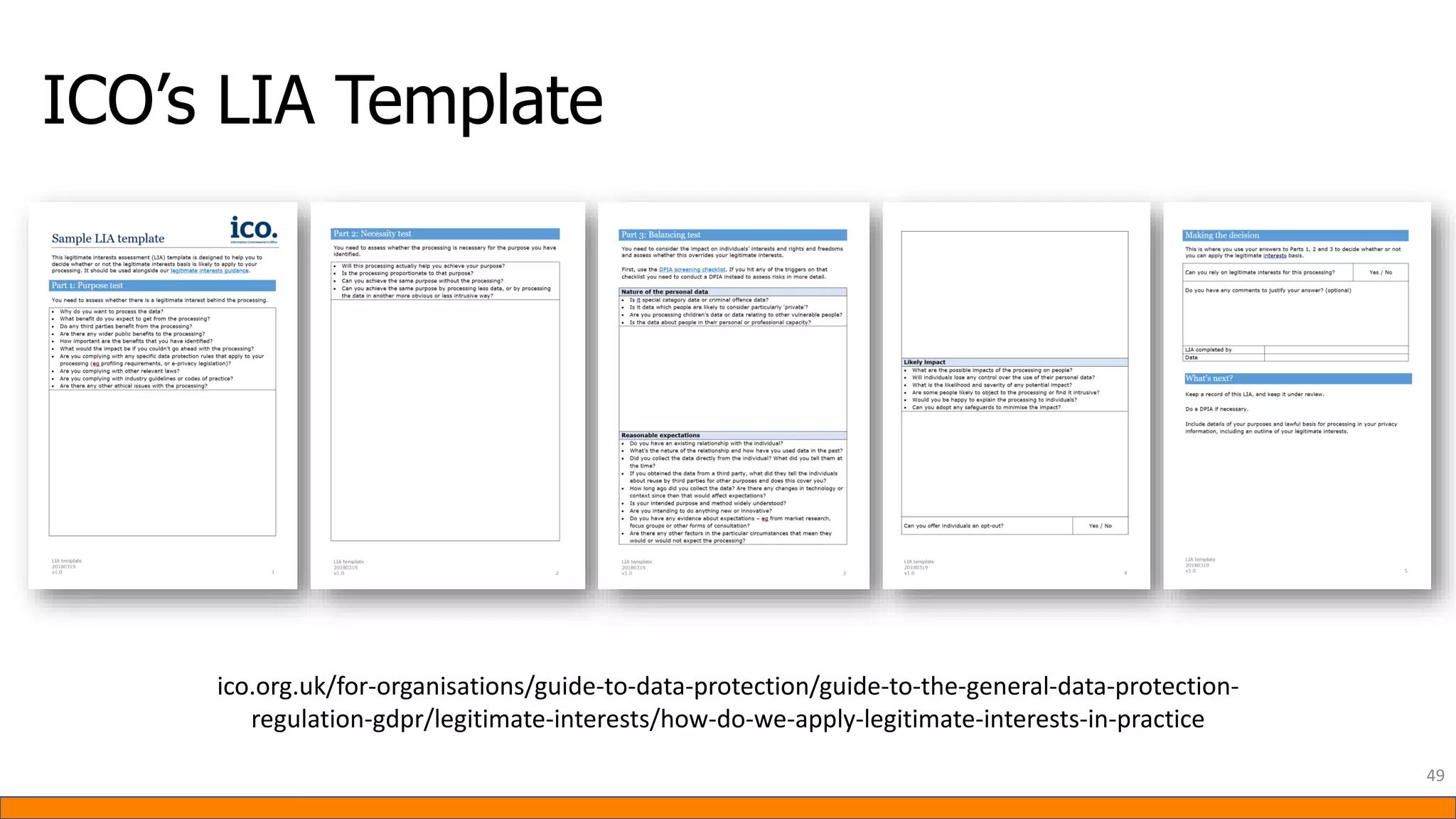
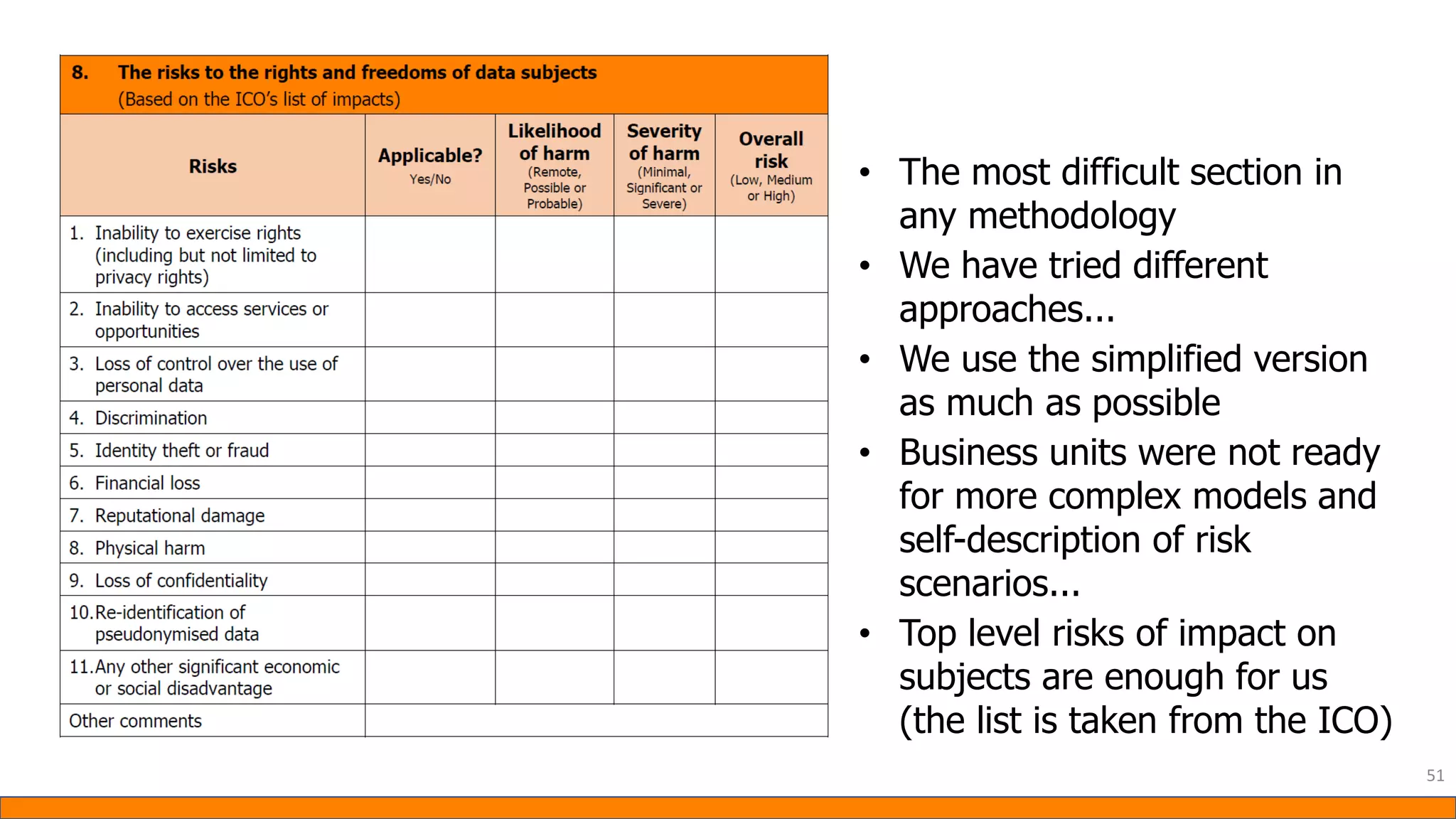
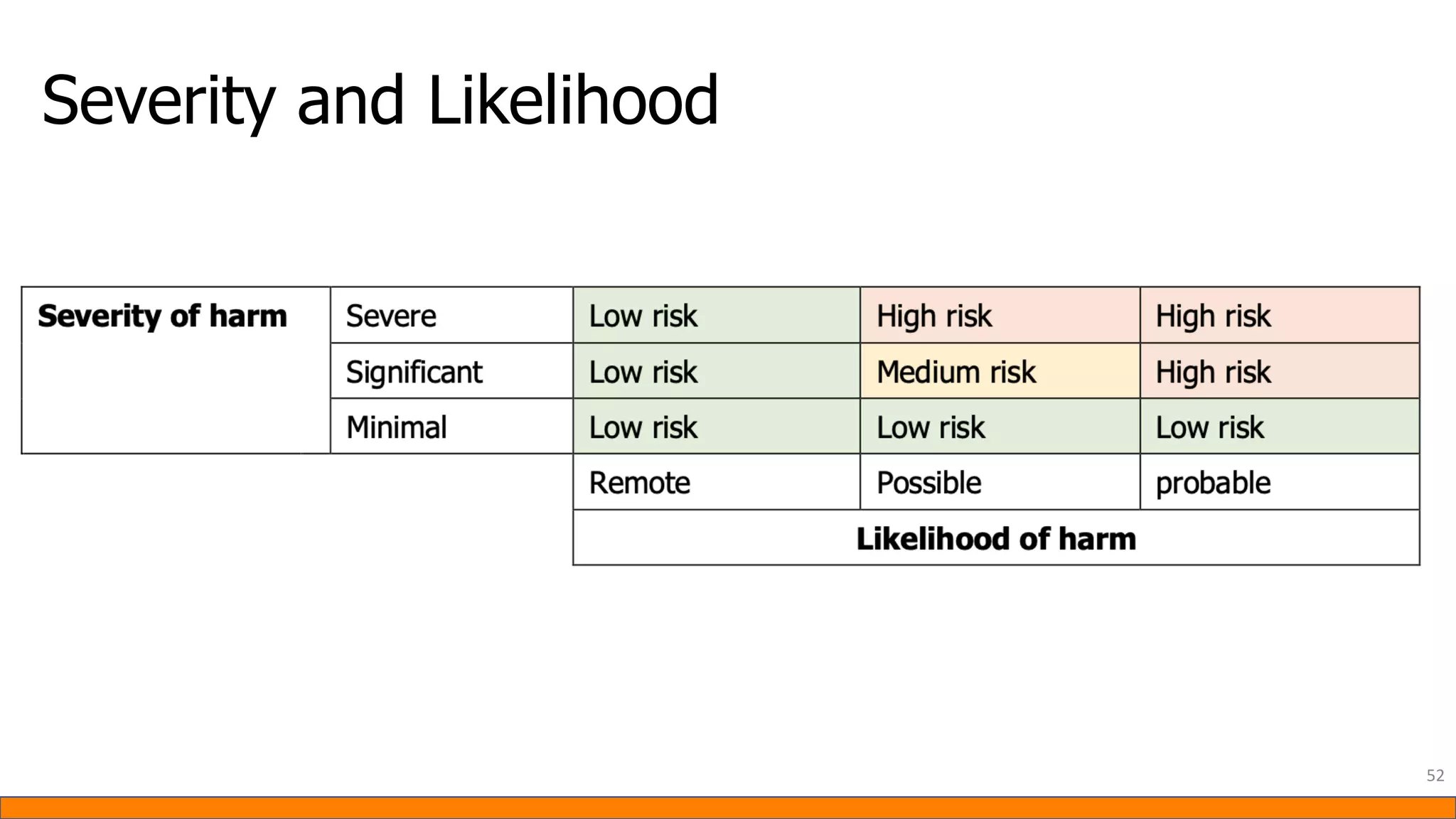
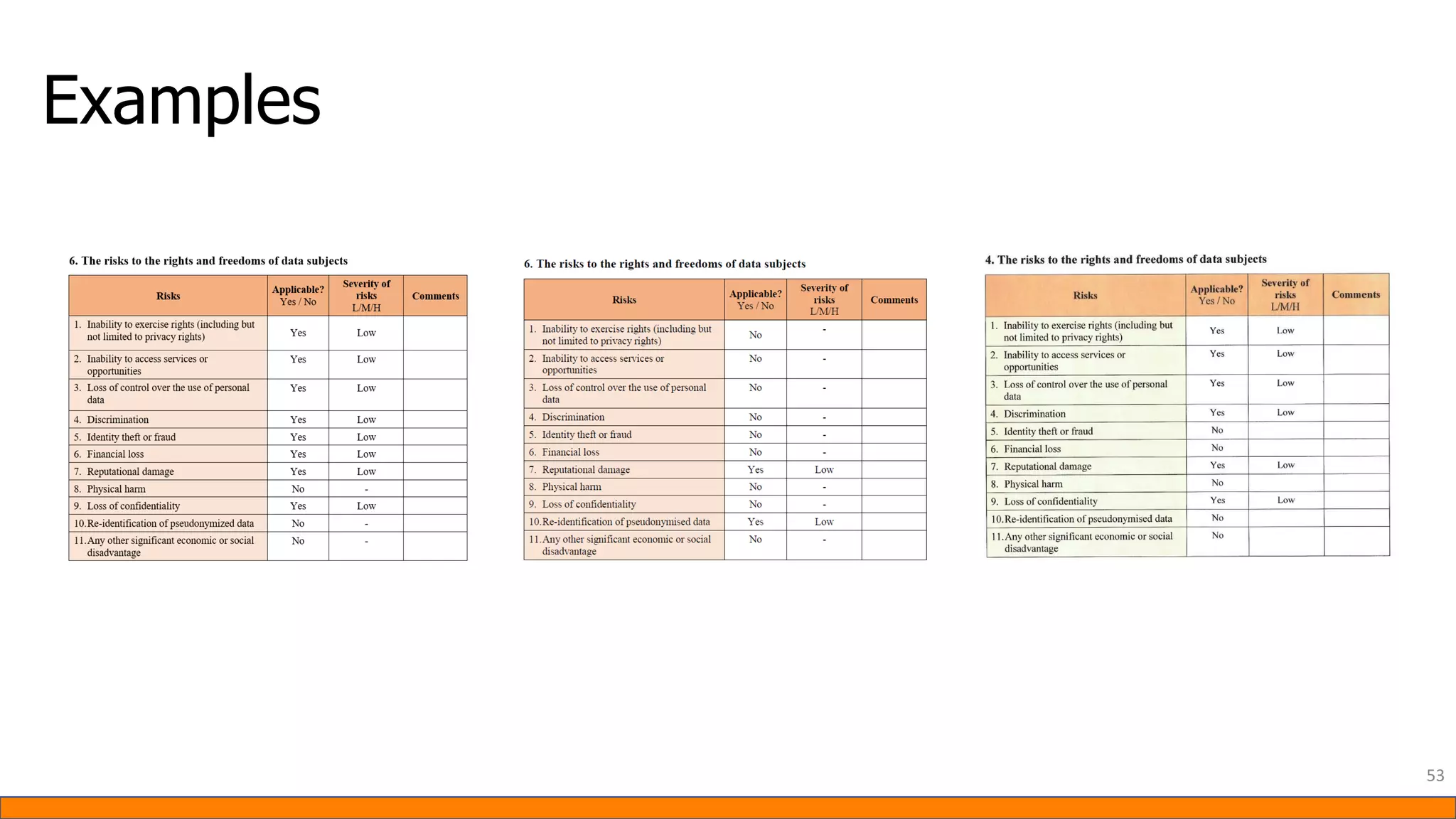
This document provides information about Data Protection Impact Assessments (DPIAs). It begins with an introduction and agenda. It then covers the definition of a DPIA, why they are needed, when they are mandatory under GDPR, and what they should include. It discusses templates, methodologies, and examples of high risk factors that require a DPIA. It also provides the presenter's templates for a DPIA, including a lighter version, and discusses ways to improve the templates by making them more specific and complicated. The document is an overview of DPIAs aimed at helping organizations understand and comply with requirements.