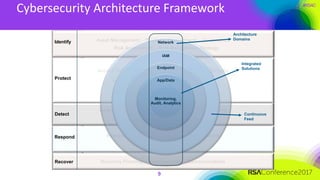
The document outlines a cybersecurity roadmap for the healthcare industry, addressing challenges and proposing a framework for improved security architecture. Key points include the transition from compliance-driven to vulnerability-focused approaches, integration of advanced detection technologies, and the importance of continuous monitoring. It emphasizes current capabilities, gap analysis, and a structured process for developing future security strategies.