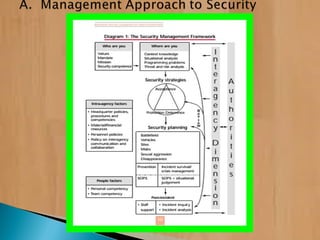
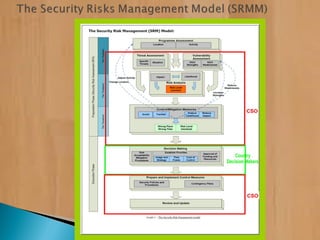
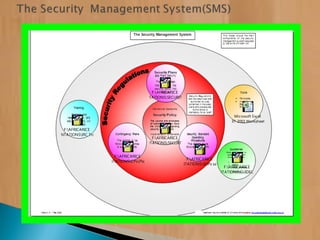
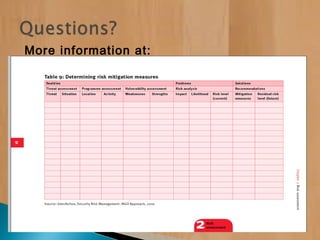
The document provides information on security risk management and security risk assessments for NGOs operating in unstable environments. It defines key terms like strategy, planning, tactics, security risk management, and security risk assessment. It also discusses developing a security risk assessment, identifying threats and vulnerabilities, and using risk assessments to effectively manage security risks. The document provides examples of how to classify risk levels in different areas and outlines contingency plans, relocation thresholds, and evacuation procedures.