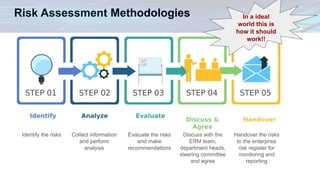
The document outlines the evolving role of Chief Security Officers (CSOs) in decision-making related to physical security and risk management, detailing four distinct eras from guardian to integrated security leader. It emphasizes the importance of various decision-making approaches, including organizational, industry, collaborative, and data-driven methods, supported by practical scenarios. Additionally, it presents a case study on the September 14, 2012 Tunis incident, illustrating risk assessment methodologies and the necessity for proactive security measures in managing threats.