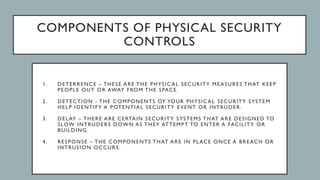
This document discusses physical security. It begins by defining physical security as protecting people, property, and assets from threats that could cause damage or loss. It then identifies some of the most common threats like theft, vandalism, natural disasters, and terrorism. The document explains that human error is a leading cause of security breaches through actions like sharing credentials or accidental data sharing. Physical security components are then outlined, including access control and surveillance. Specific security controls are provided like fences, alarms, and AI analytics. The document concludes by discussing how physical and digital security are becoming more intertwined through devices like internet-connected surveillance systems and how to develop comprehensive physical security policies.