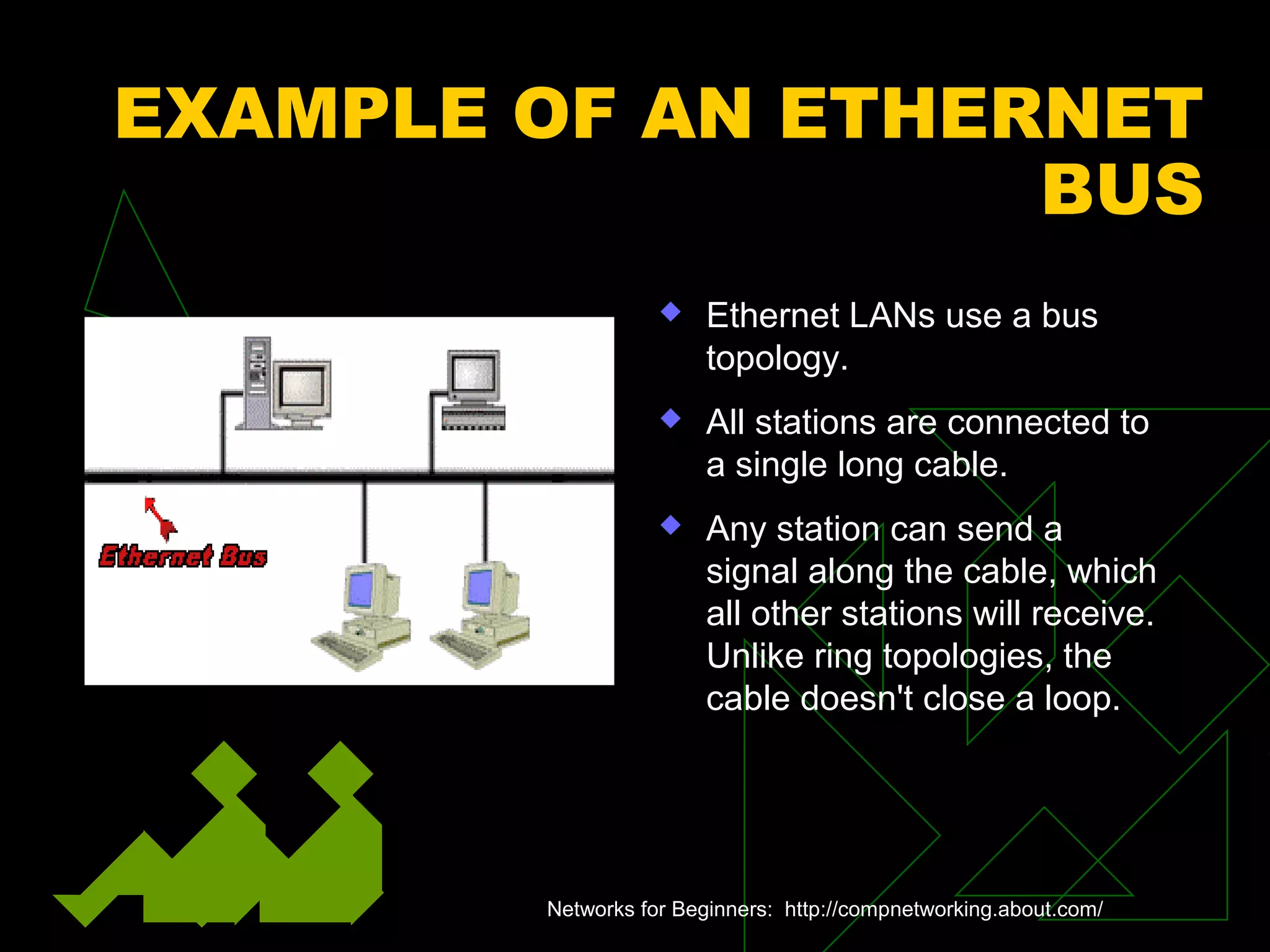
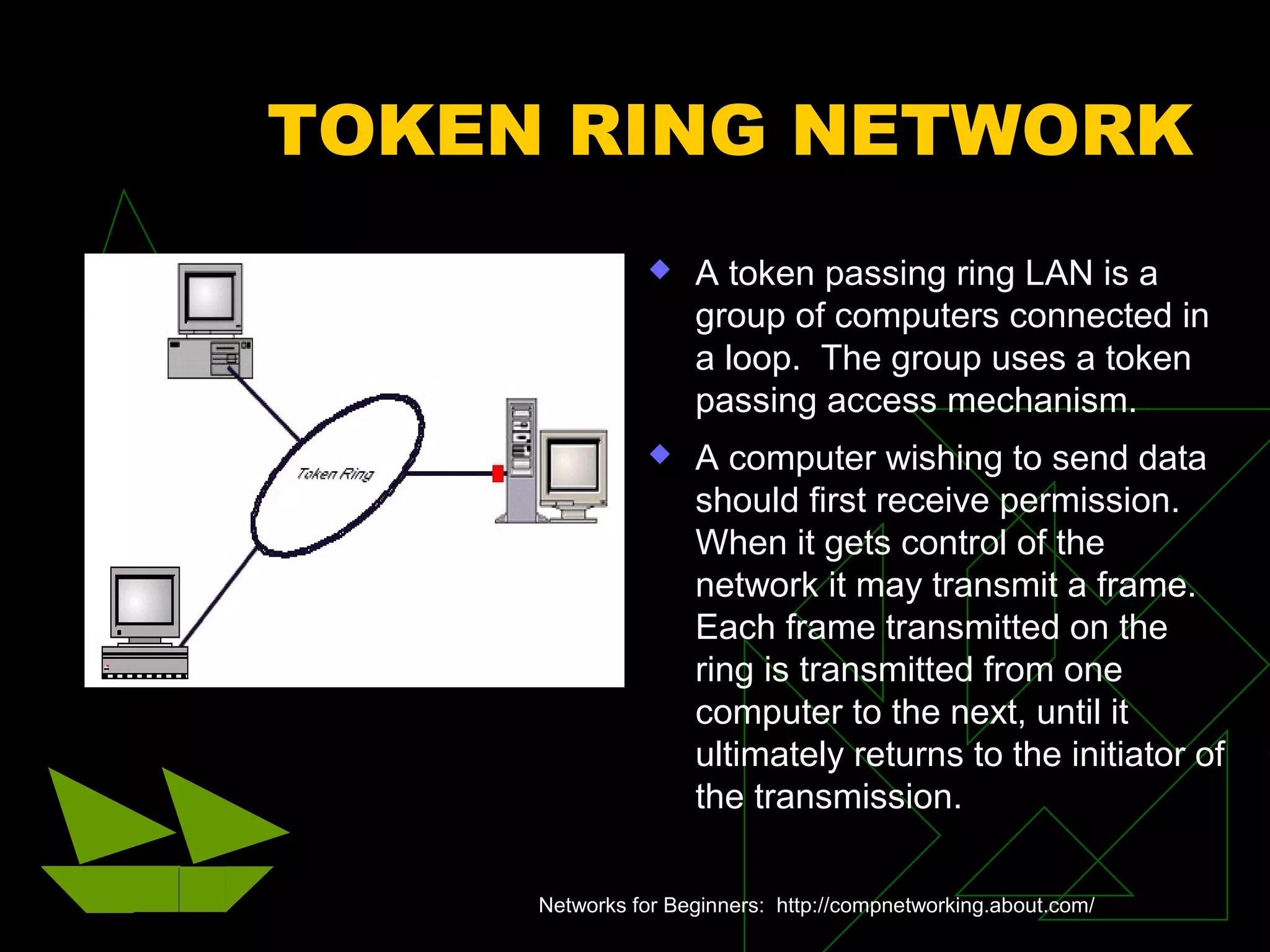
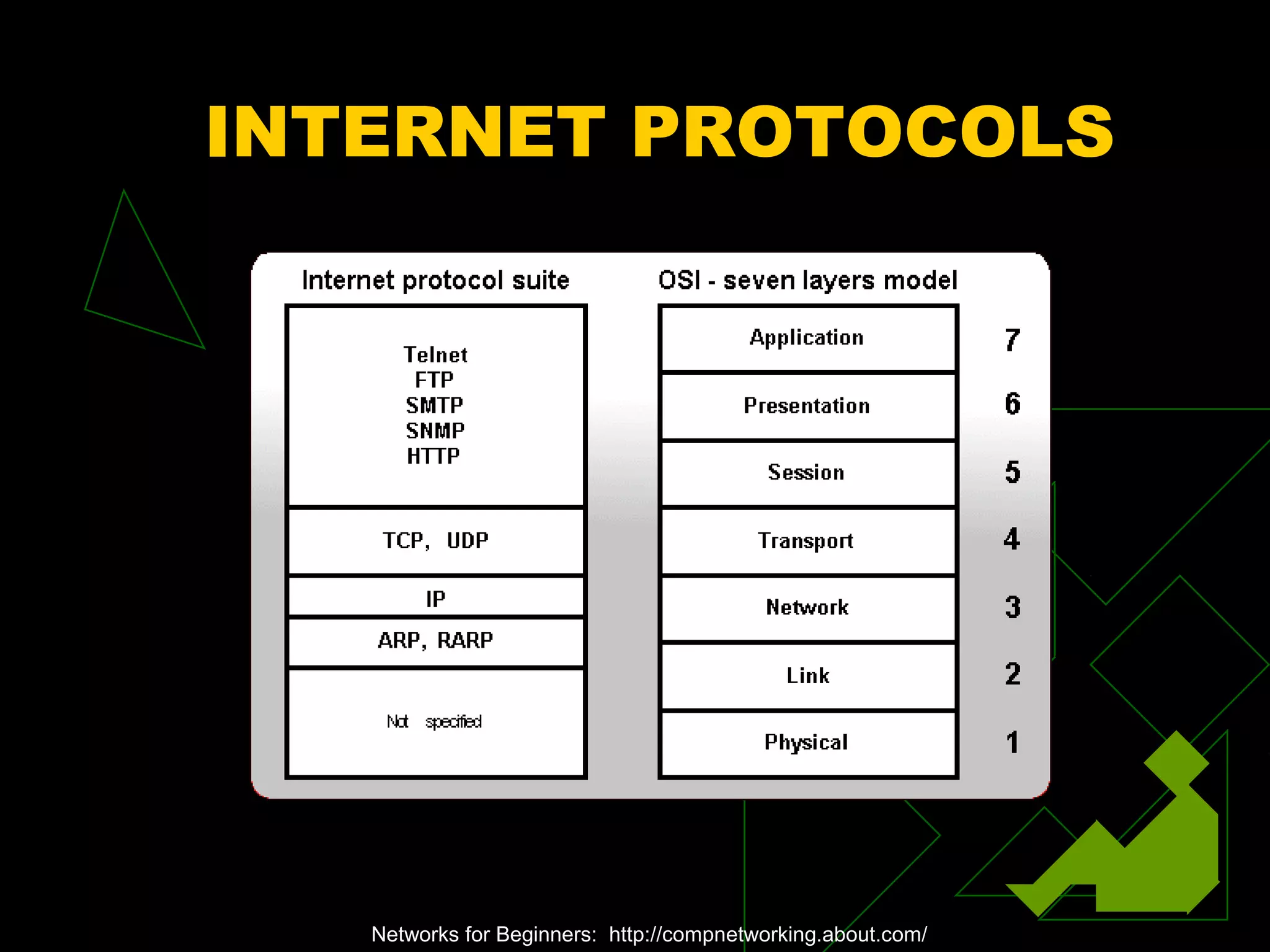
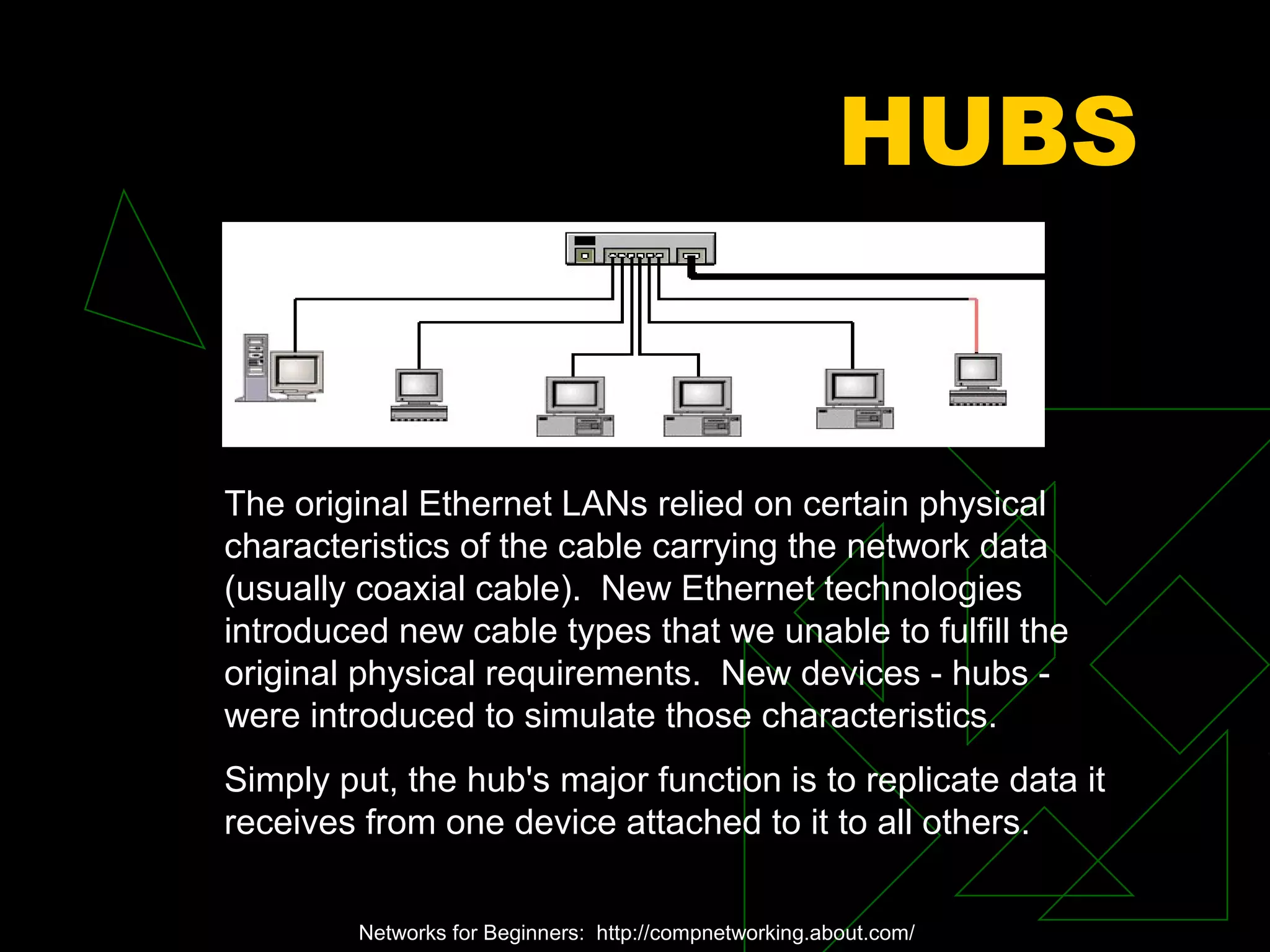
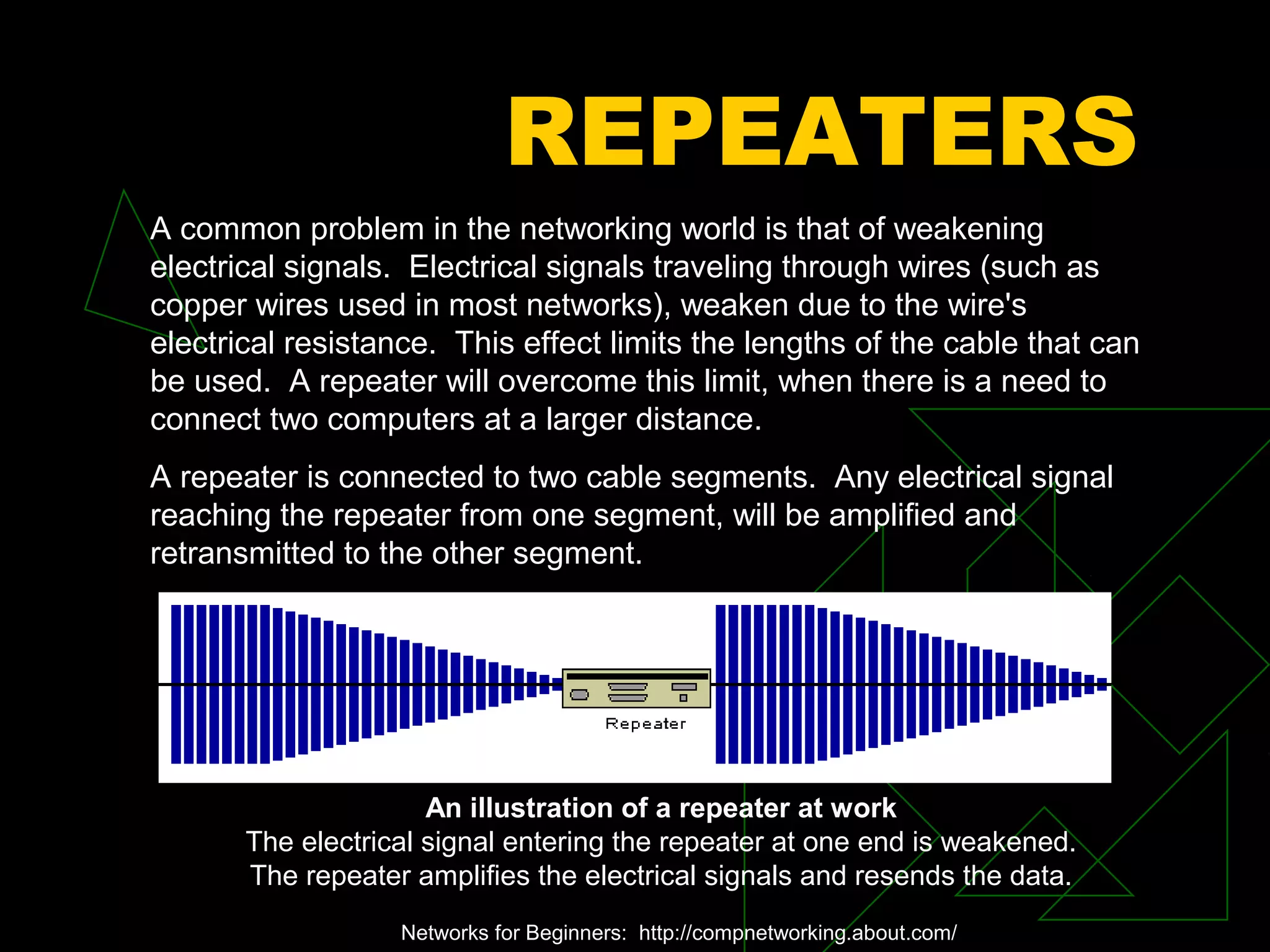
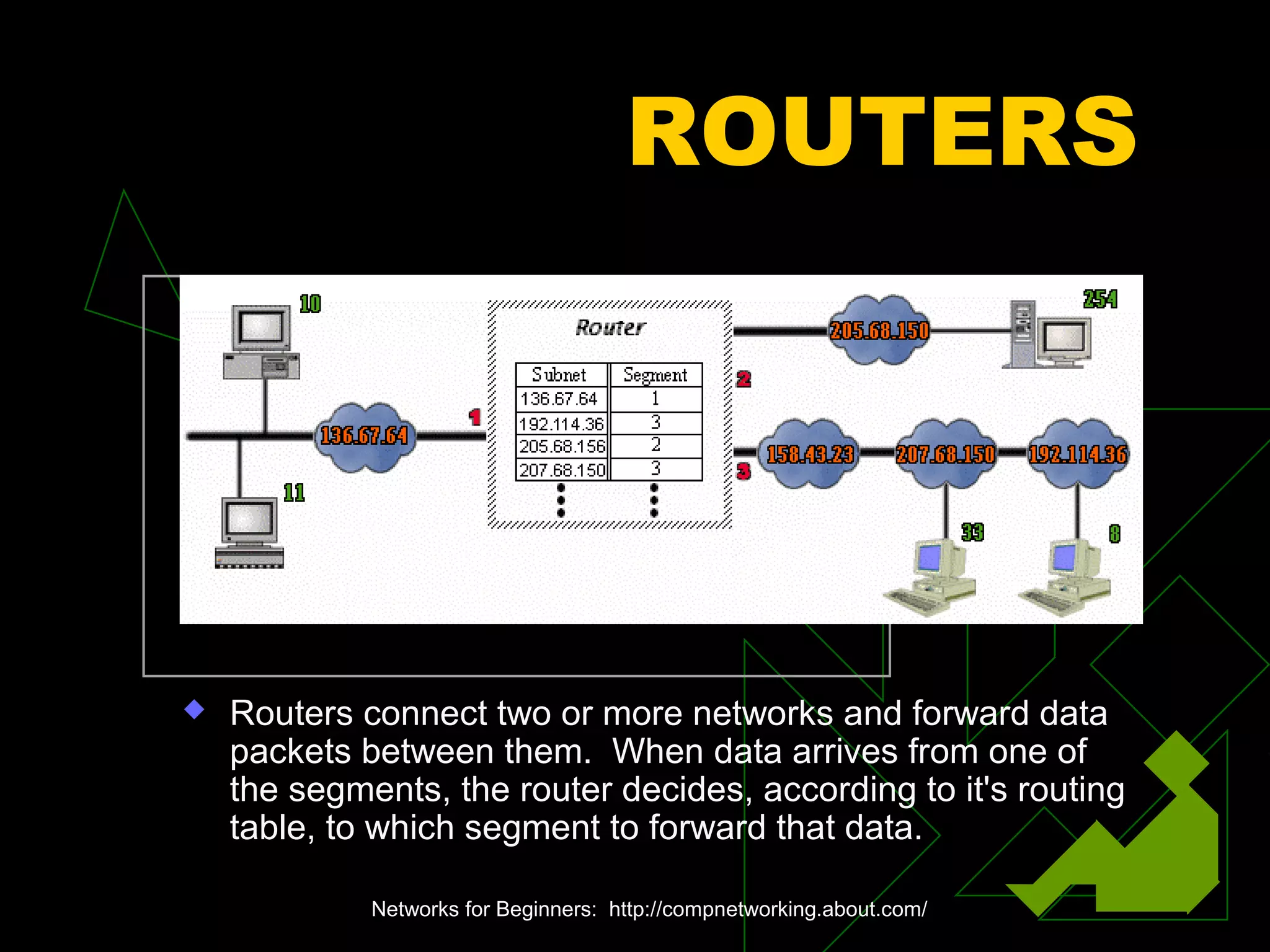
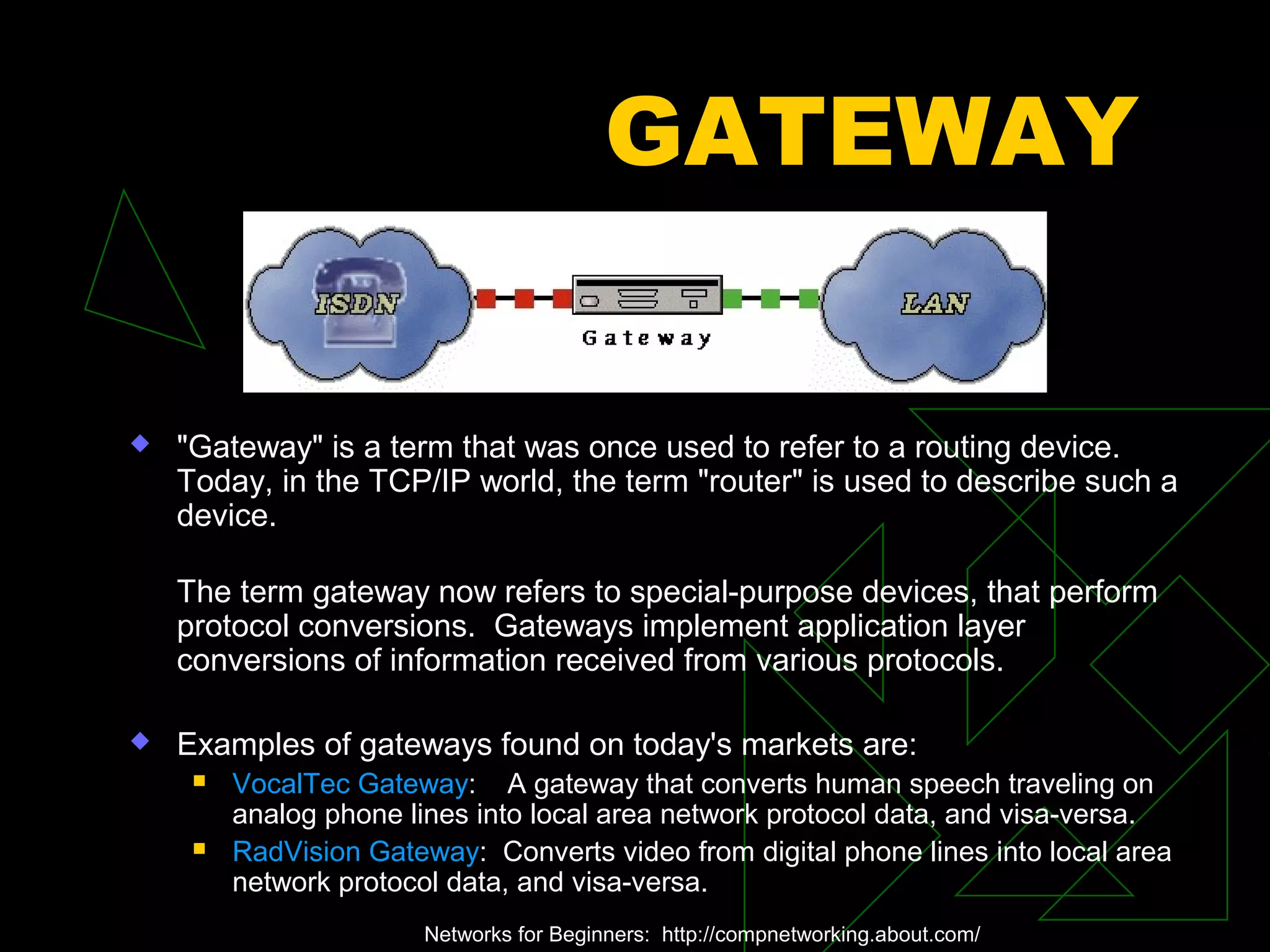
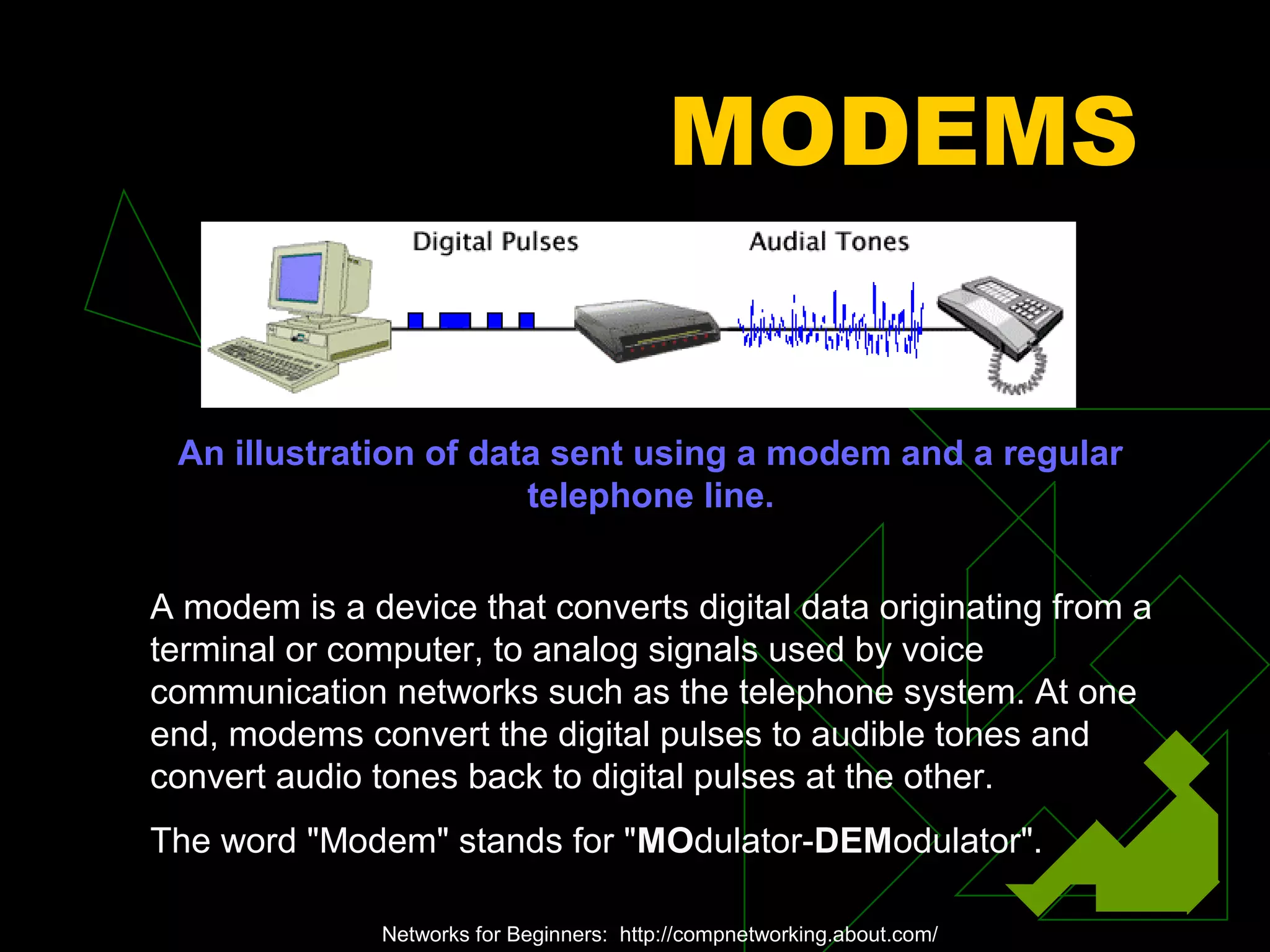
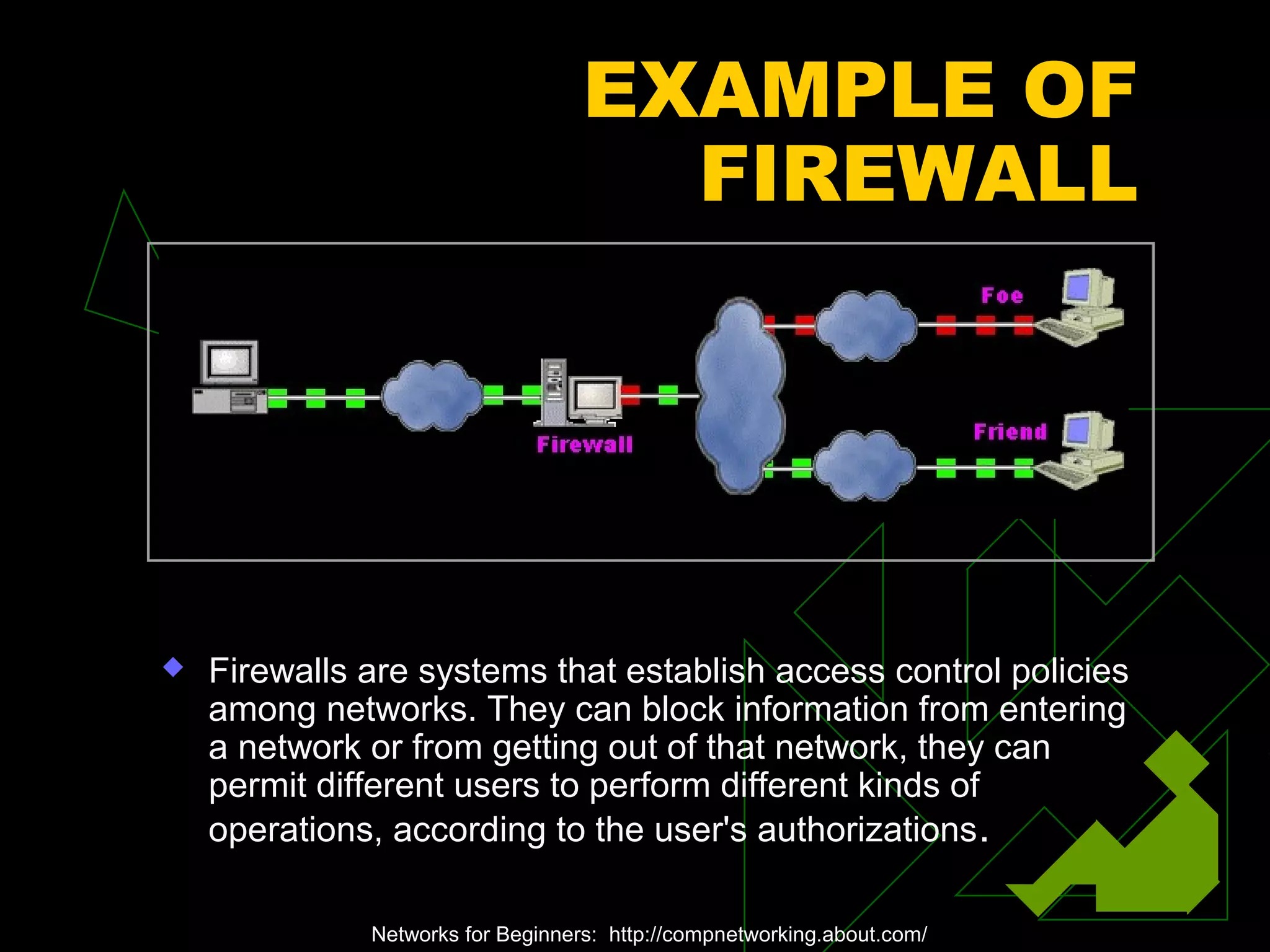
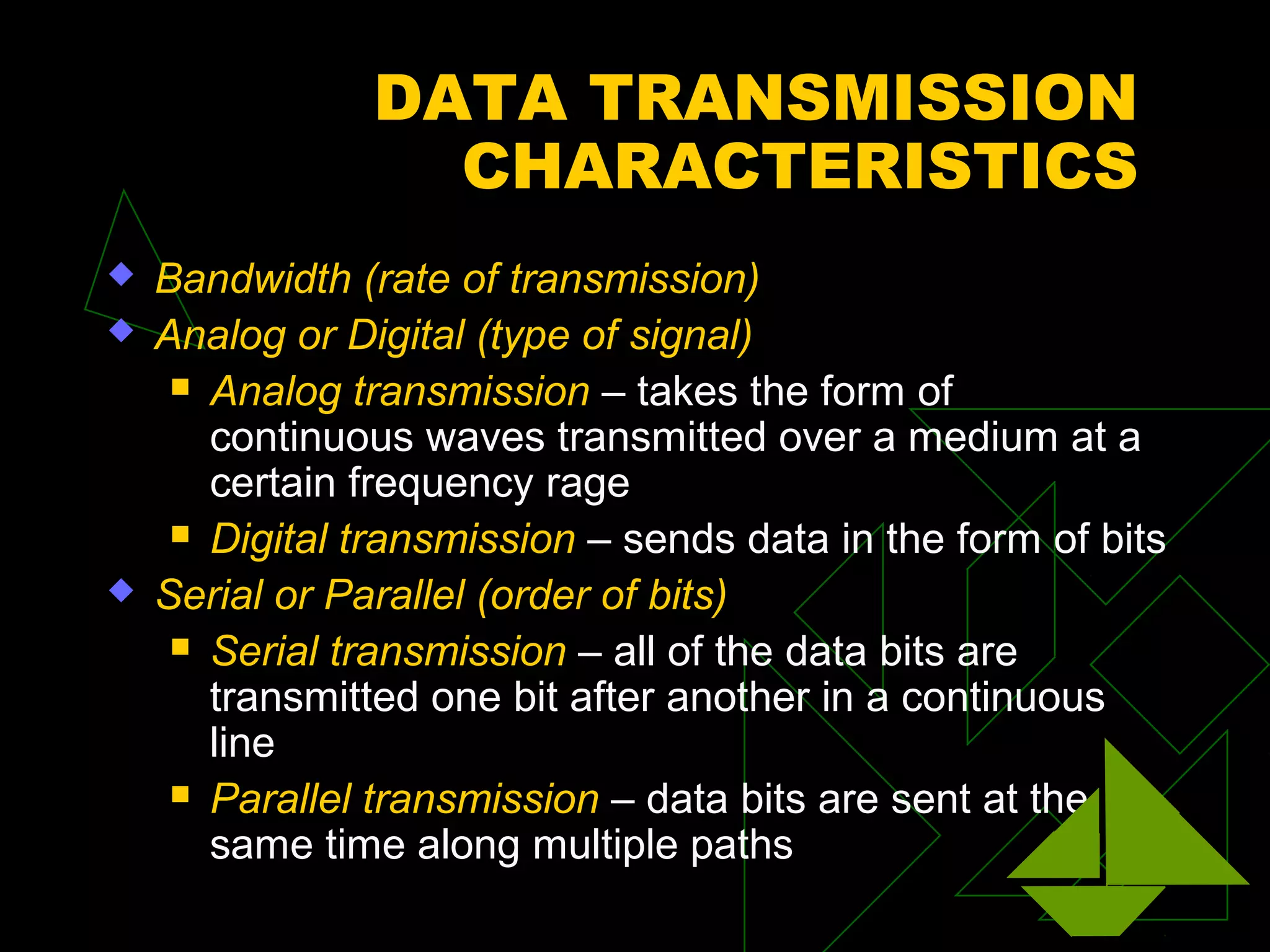
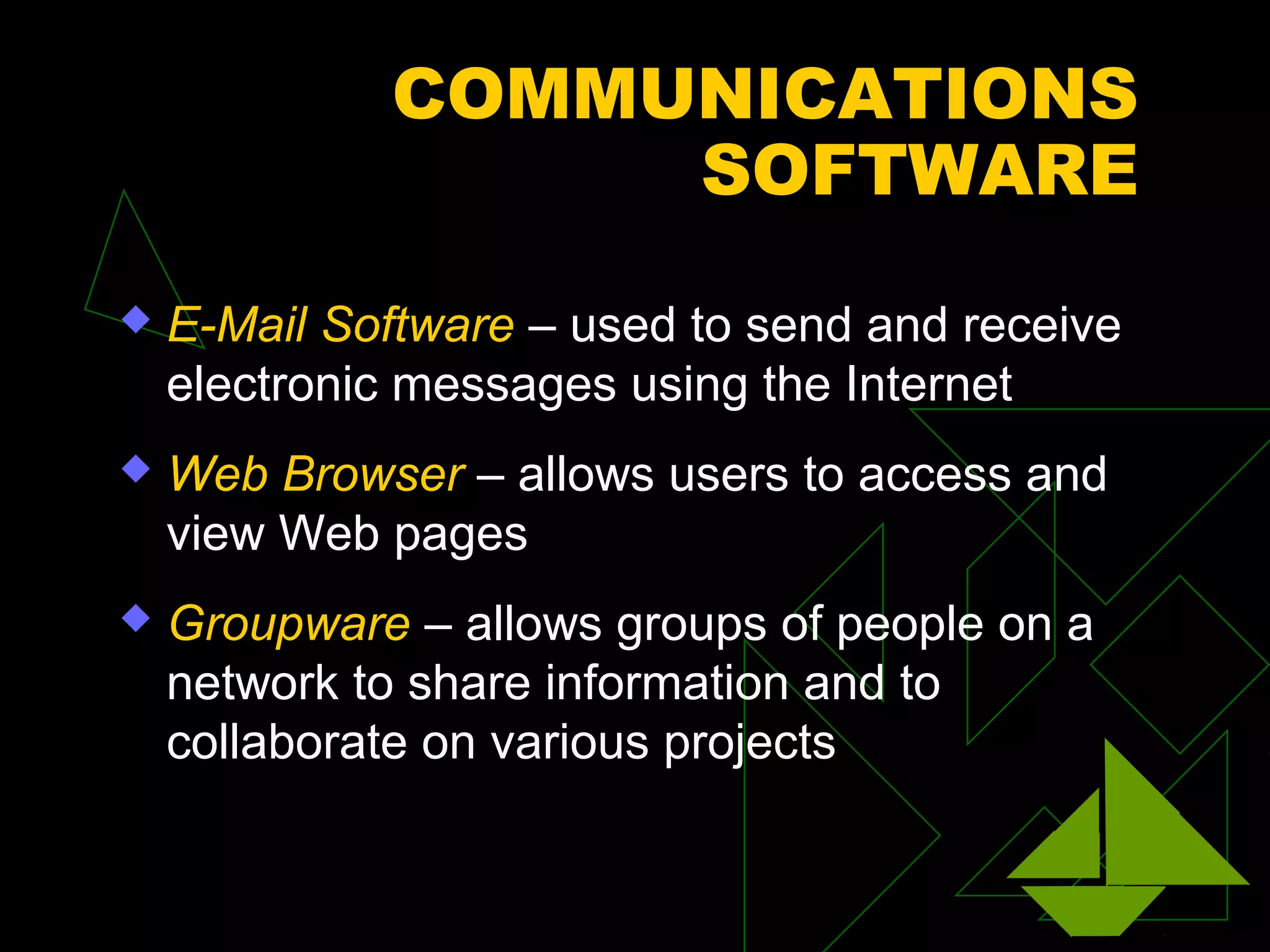
A network is two or more computers connected together. The document discusses different types of networks including local area networks (LANs), wide area networks (WANs), intranets, and extranets. It also covers network topologies like bus, star, and ring as well as protocols like Ethernet and TCP/IP. Key networking hardware is described such as hubs, routers, bridges, and gateways. Communication media including twisted pair cable, coaxial cable, fiber optic cable, and wireless options are also summarized.