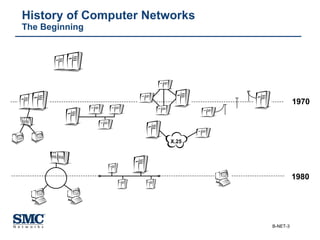
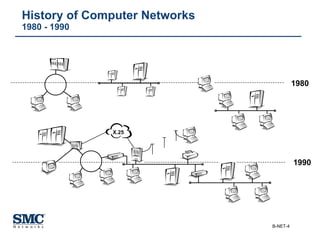
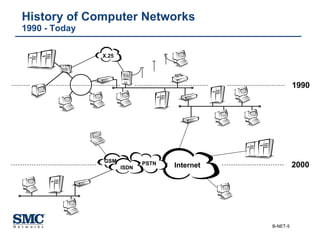
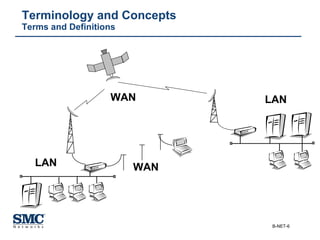
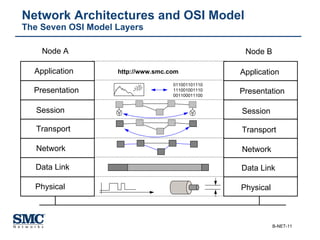
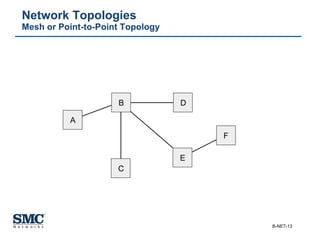
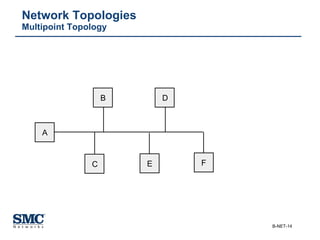
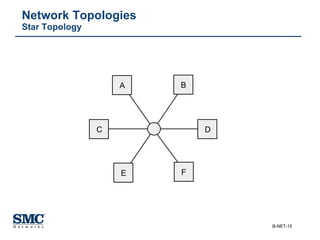
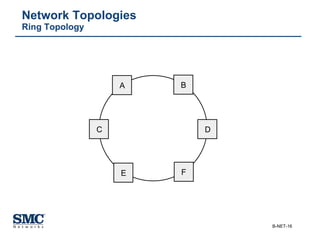
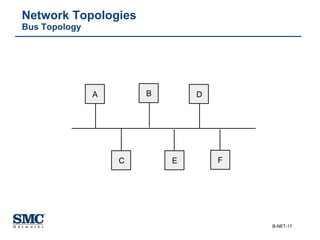
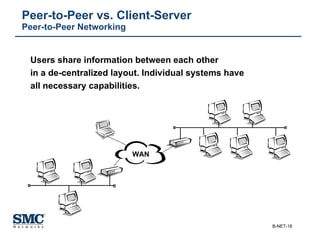
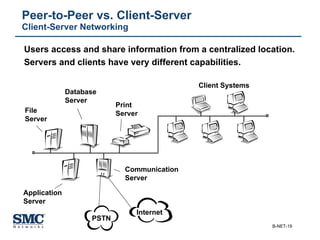
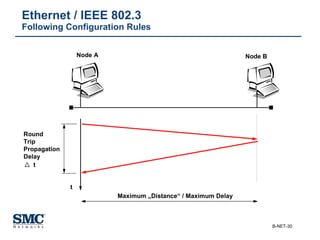
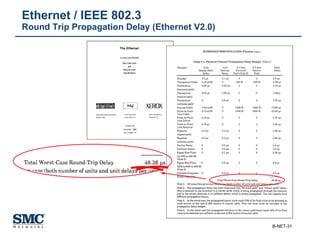
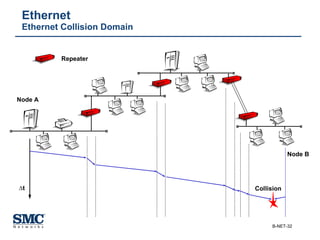
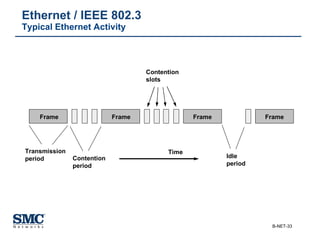
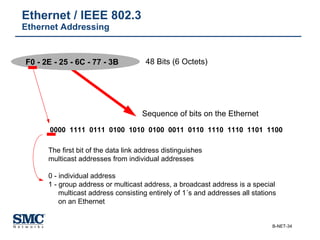
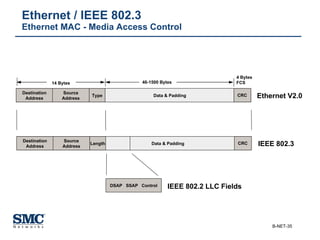
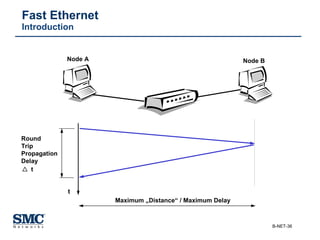
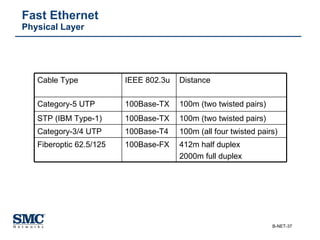
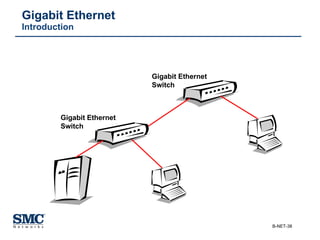
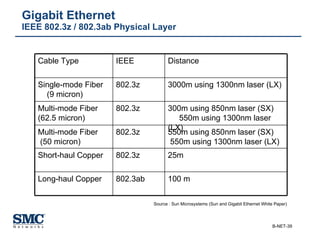
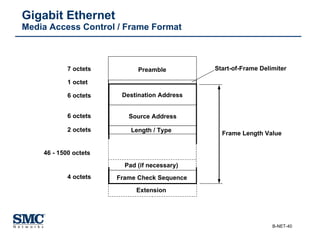
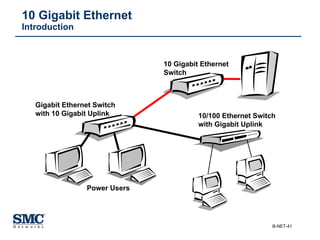
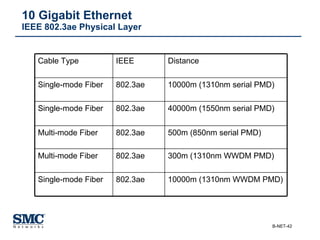
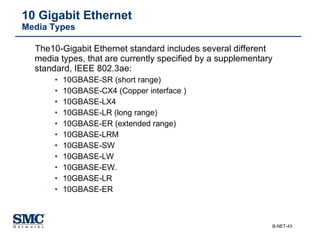
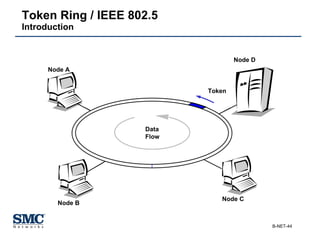
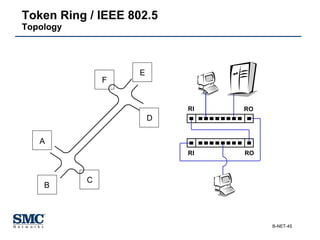
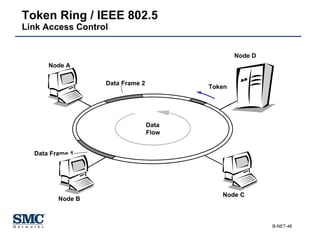
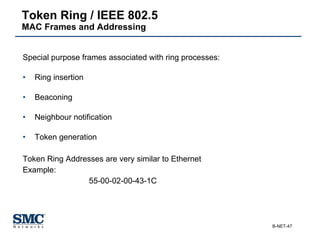
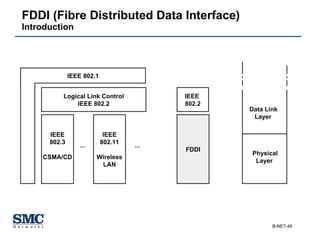
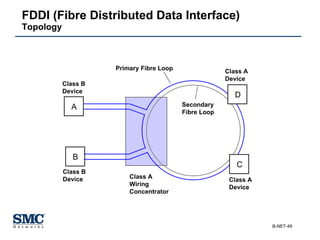
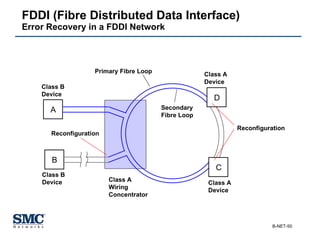
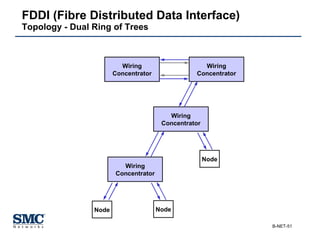
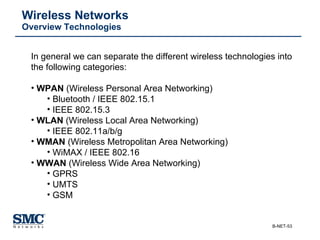
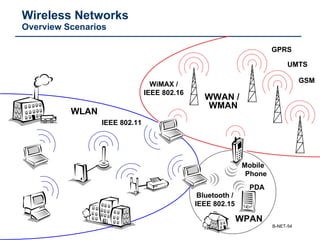
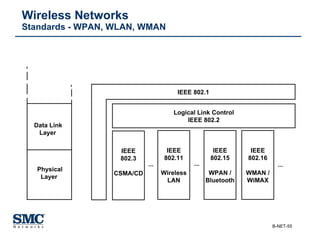
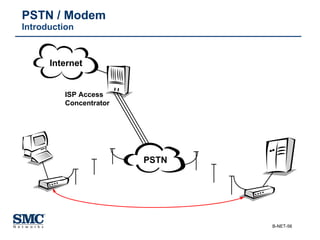
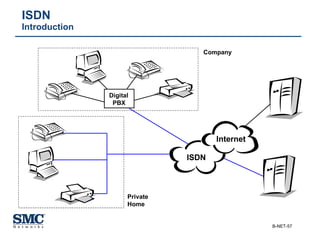
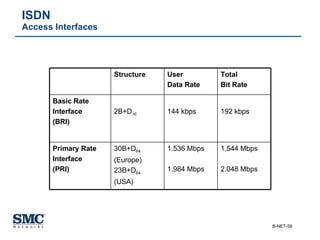
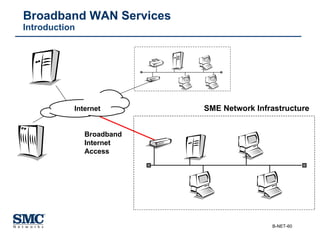
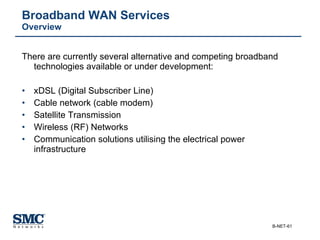
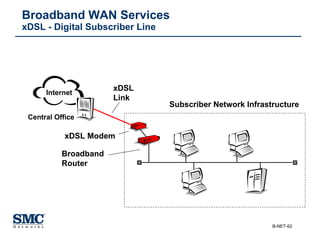
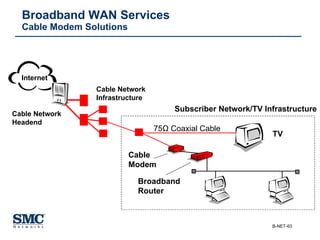
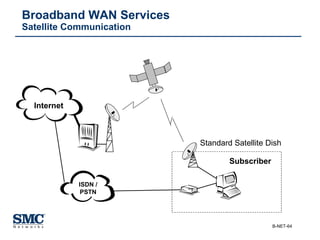
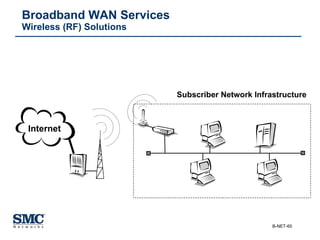
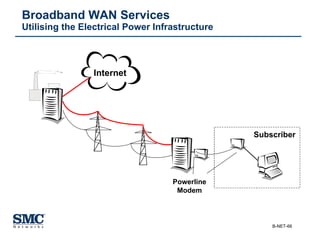
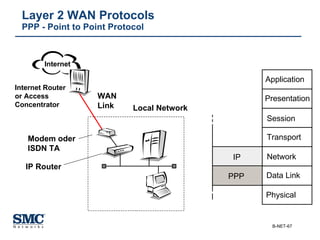
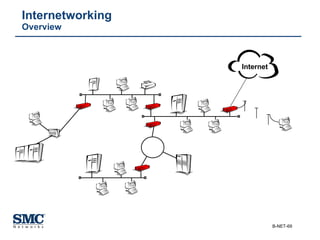
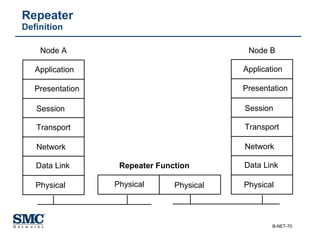
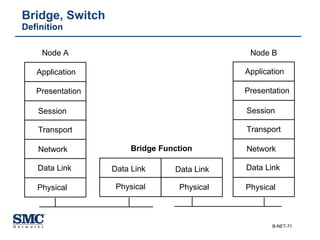
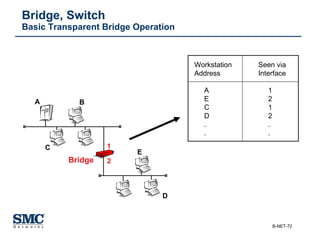
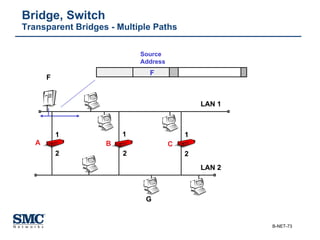
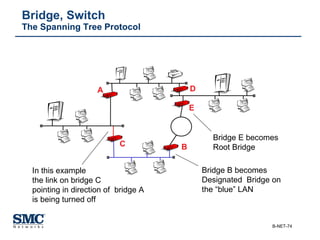
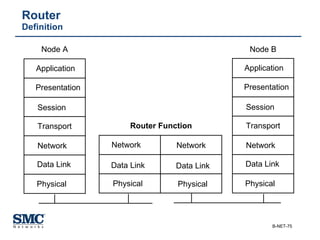
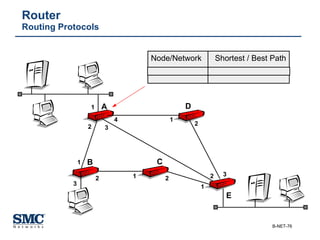
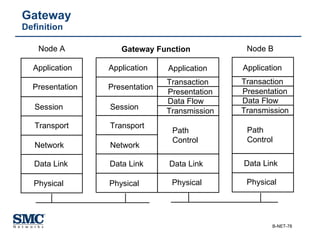
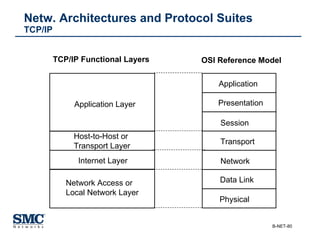
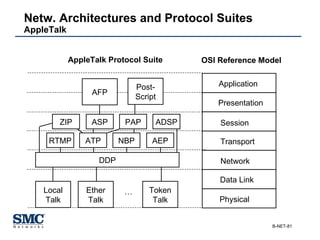
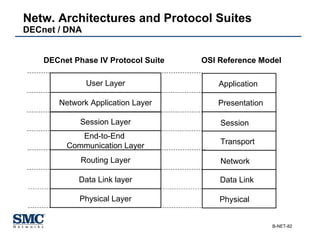
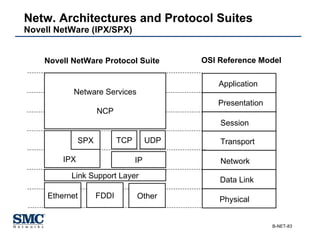
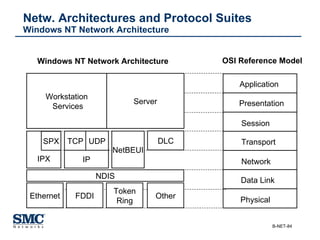
The document provides an extensive overview of networking fundamentals, including the history of computer networks, the OSI model, networking protocols, and various network topologies. It covers different types of networks such as LAN, WAN, and wireless technologies, alongside detailed discussions of Ethernet standards and configurations. Additionally, it addresses WAN services, protocols, and architectures, offering insights into data link layer operations and the evolution of networking technologies.