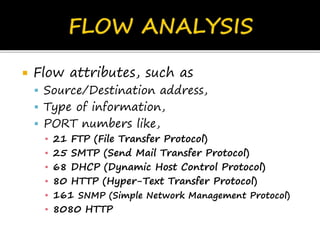
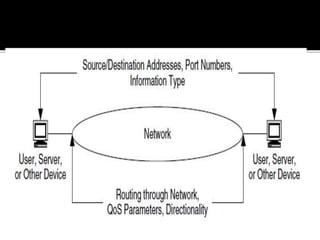
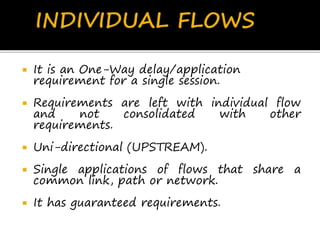
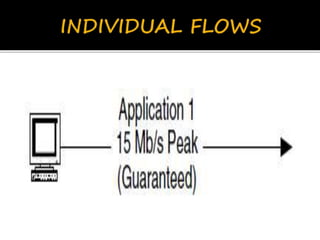
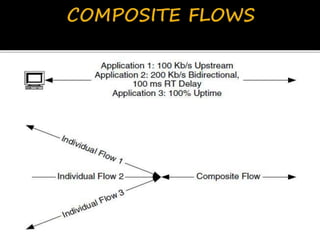
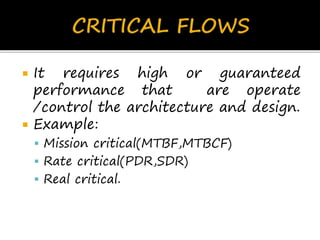
This document discusses network flows and flow analysis. It defines flows as sequences of packets sent from a source to a destination. Flow analysis describes and characterizes traffic flows by identifying where they occur and what performance they require. Flows can be individual, representing a single application, or composite, representing the combination of requirements from multiple applications sharing a network. Flow models help categorize flows based on environment type. Prioritizing flows determines which get more resources based on importance factors.