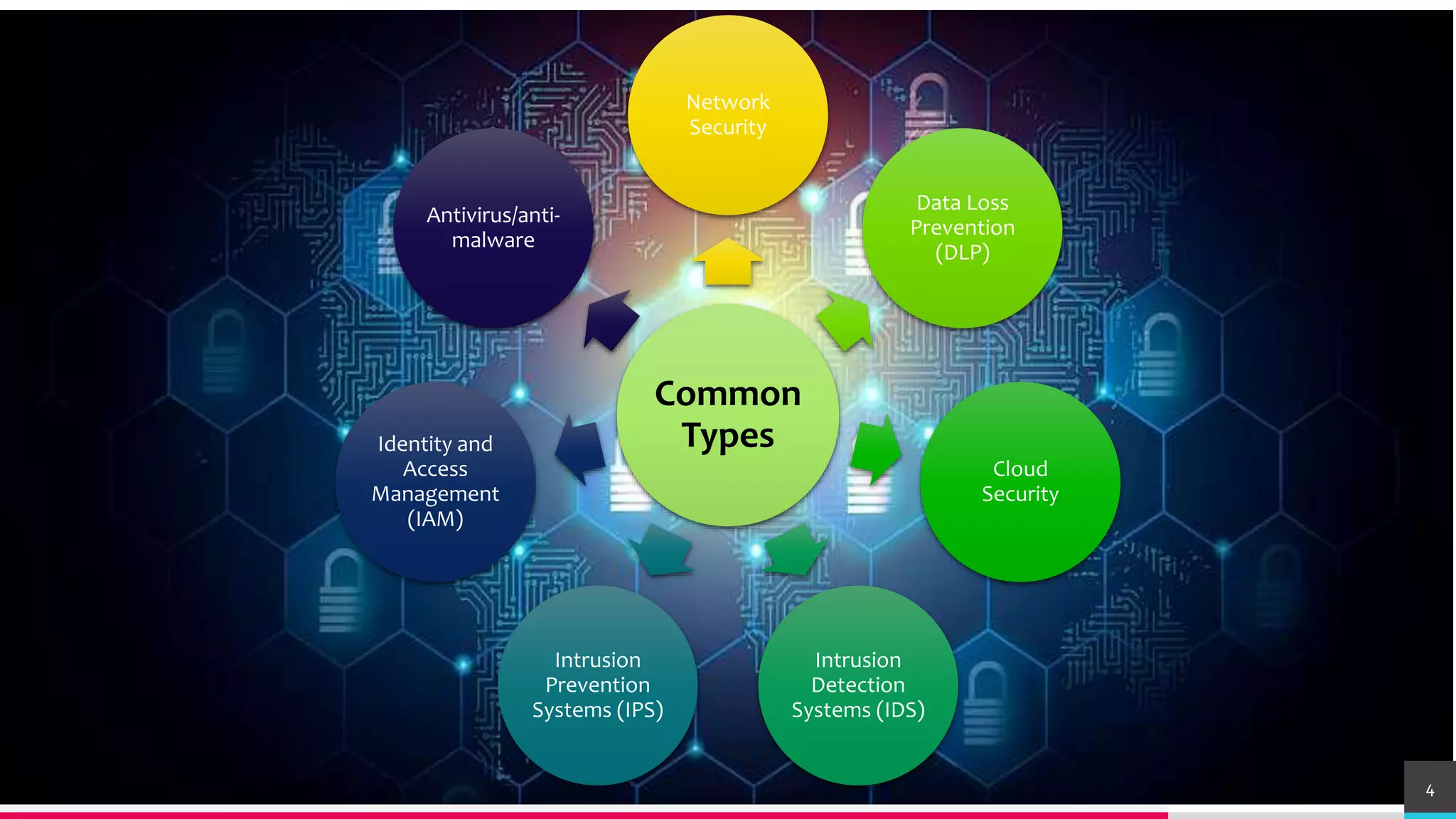
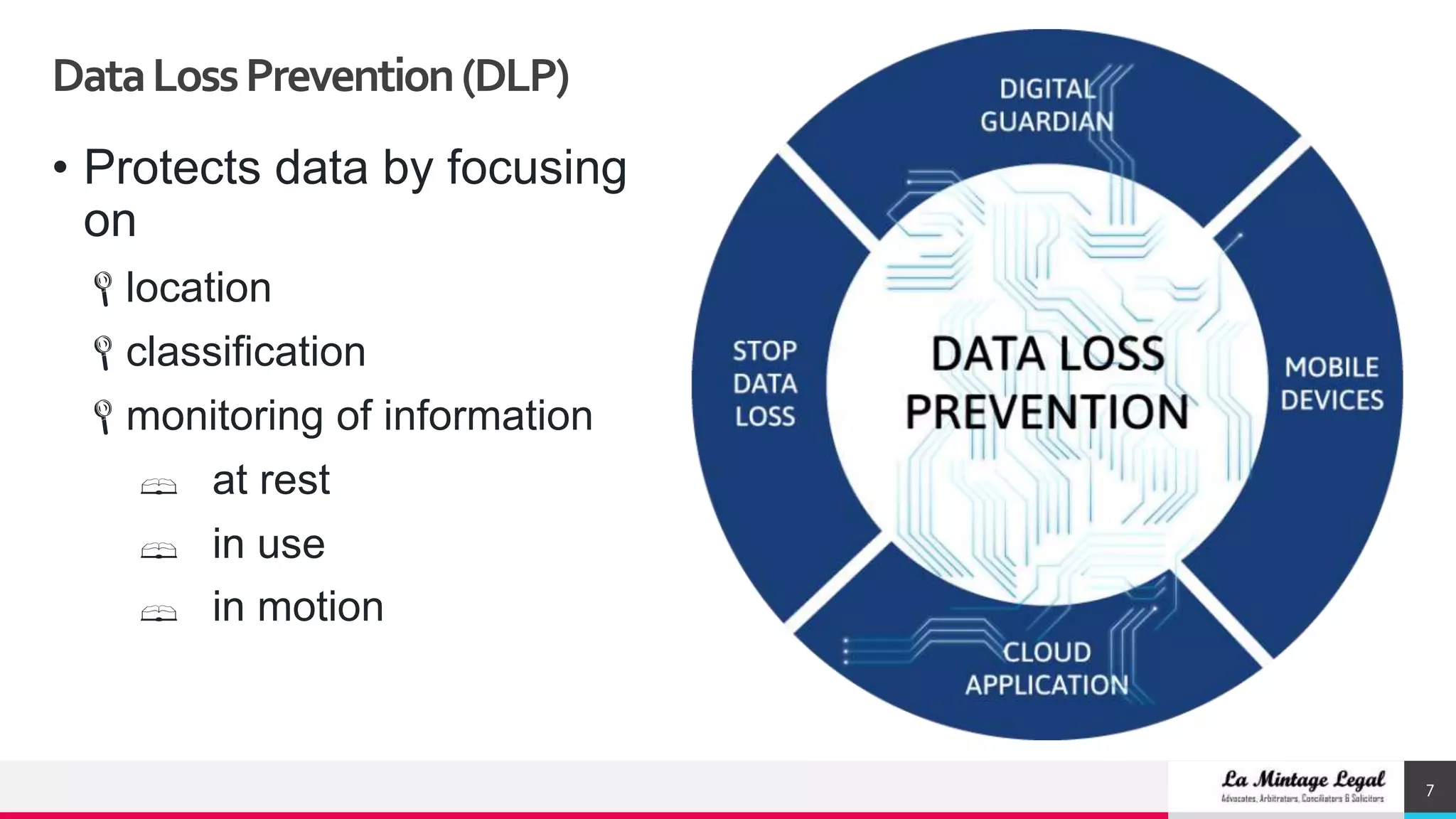
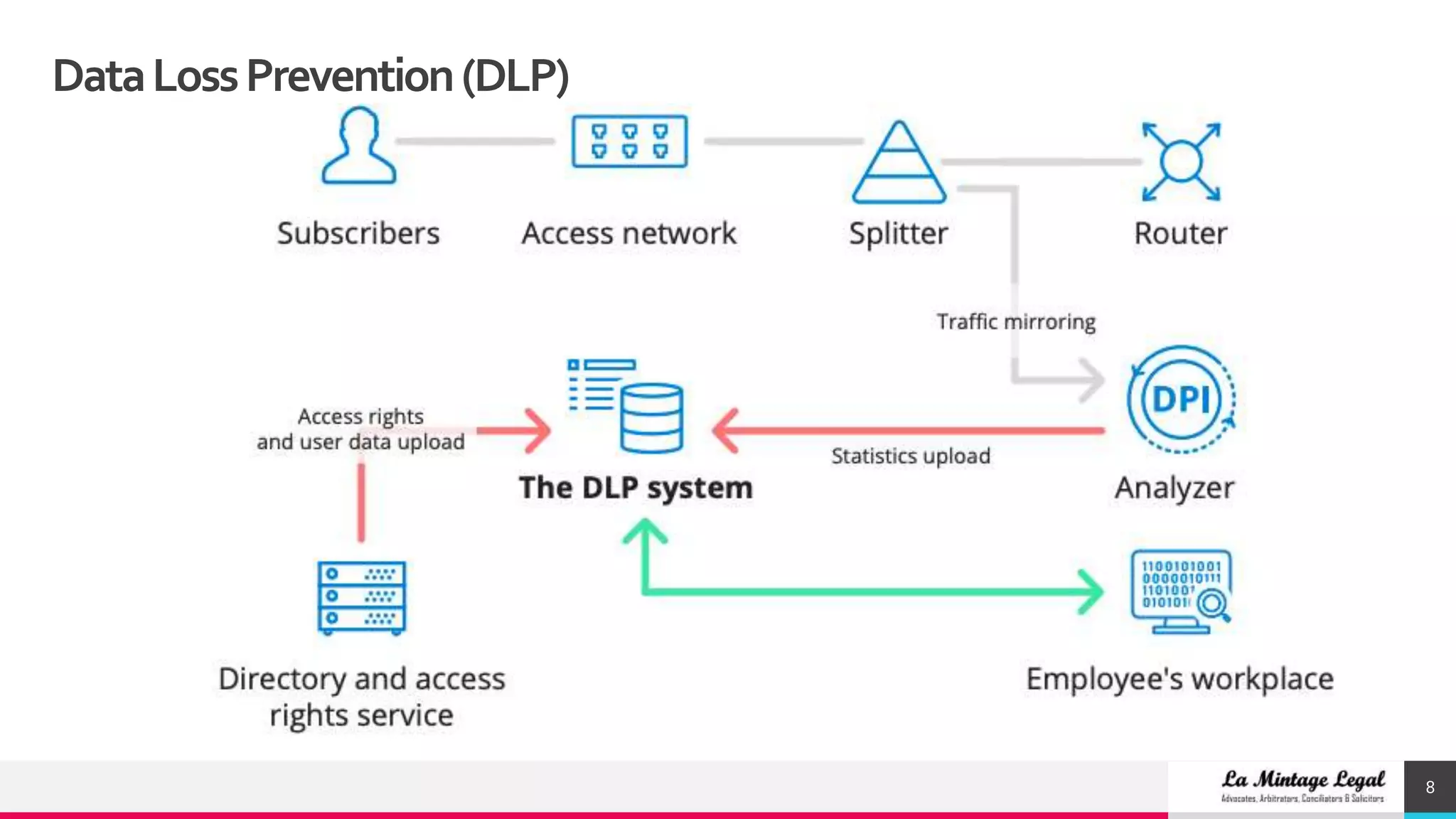
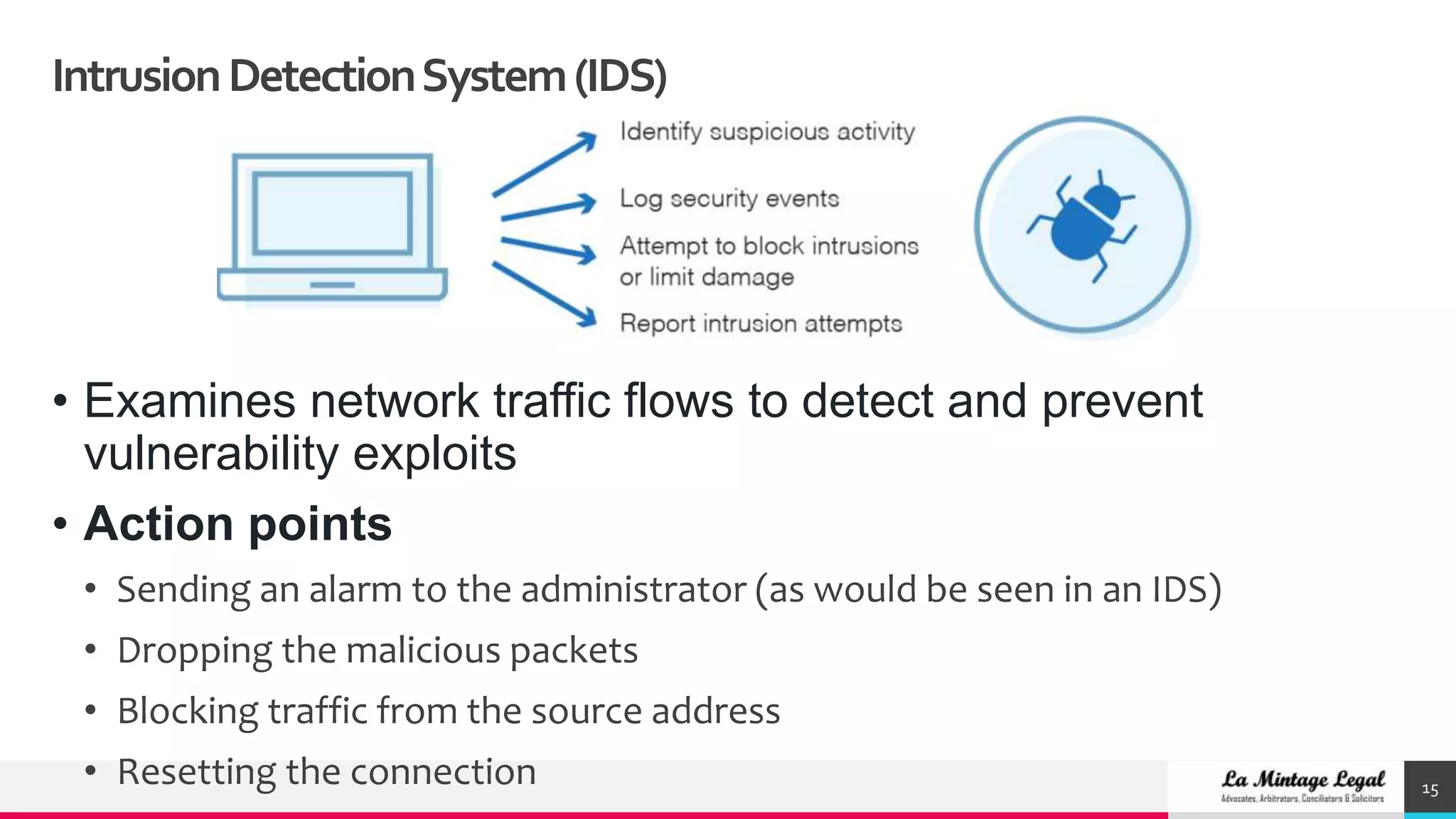
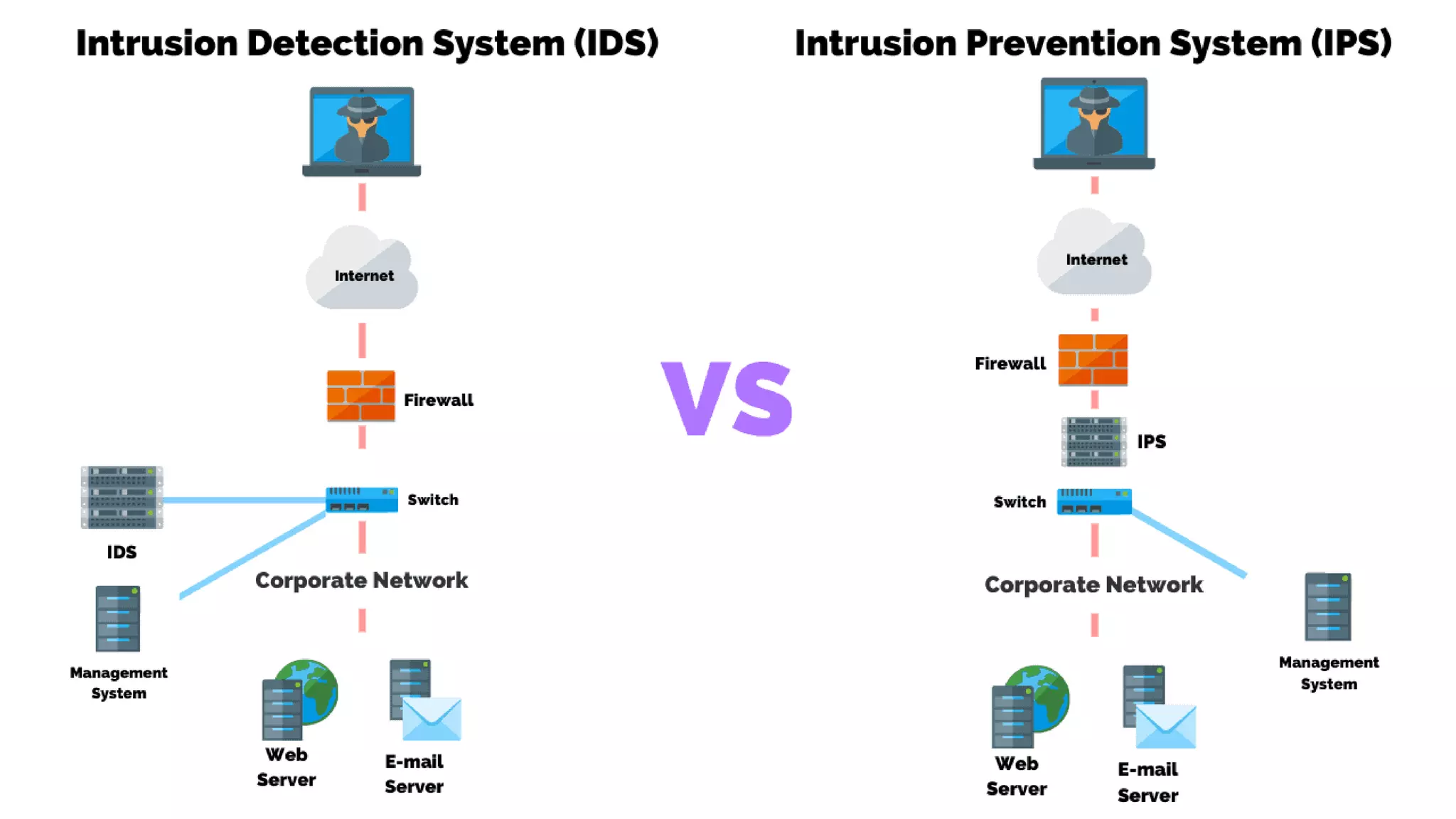
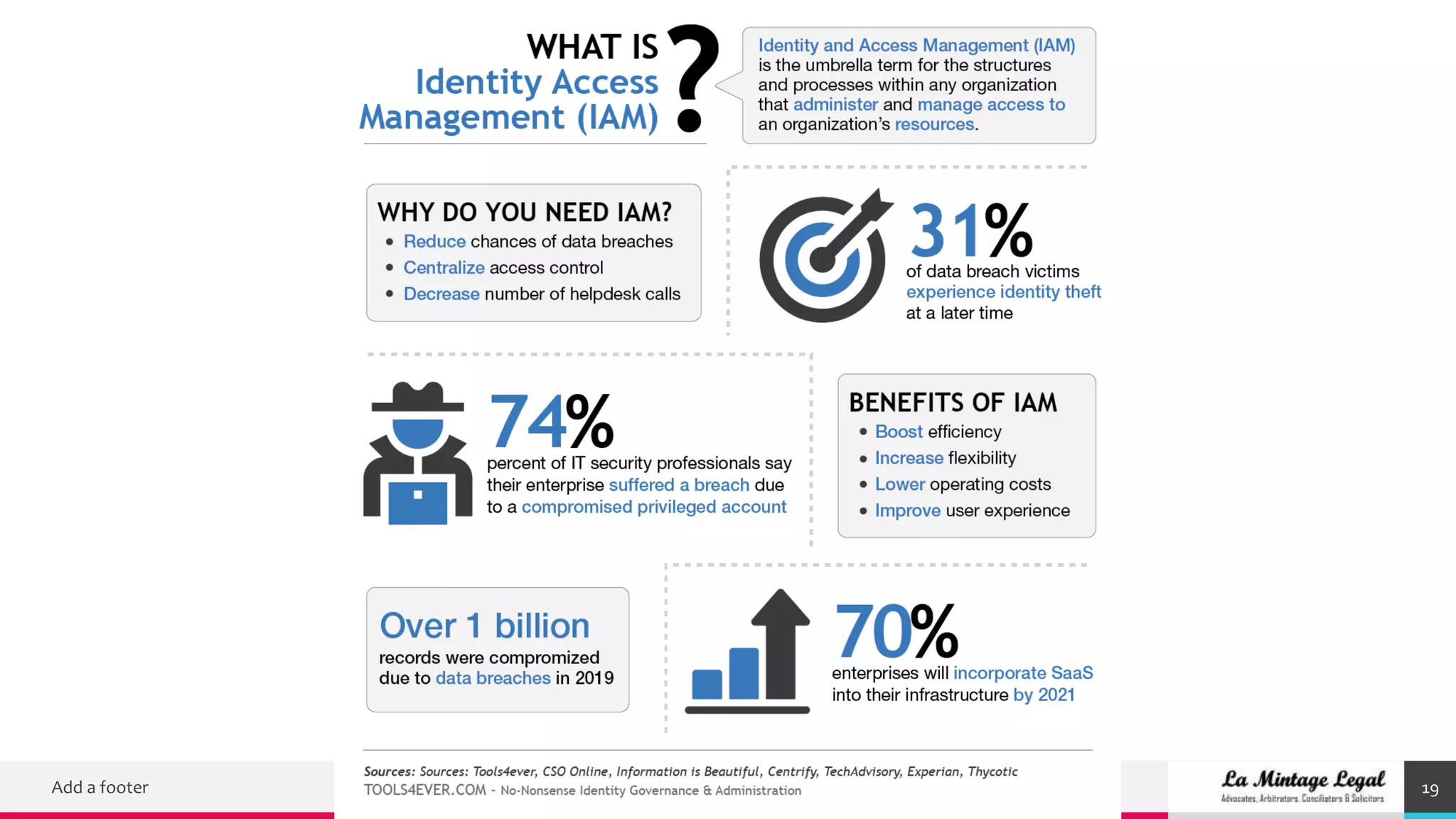
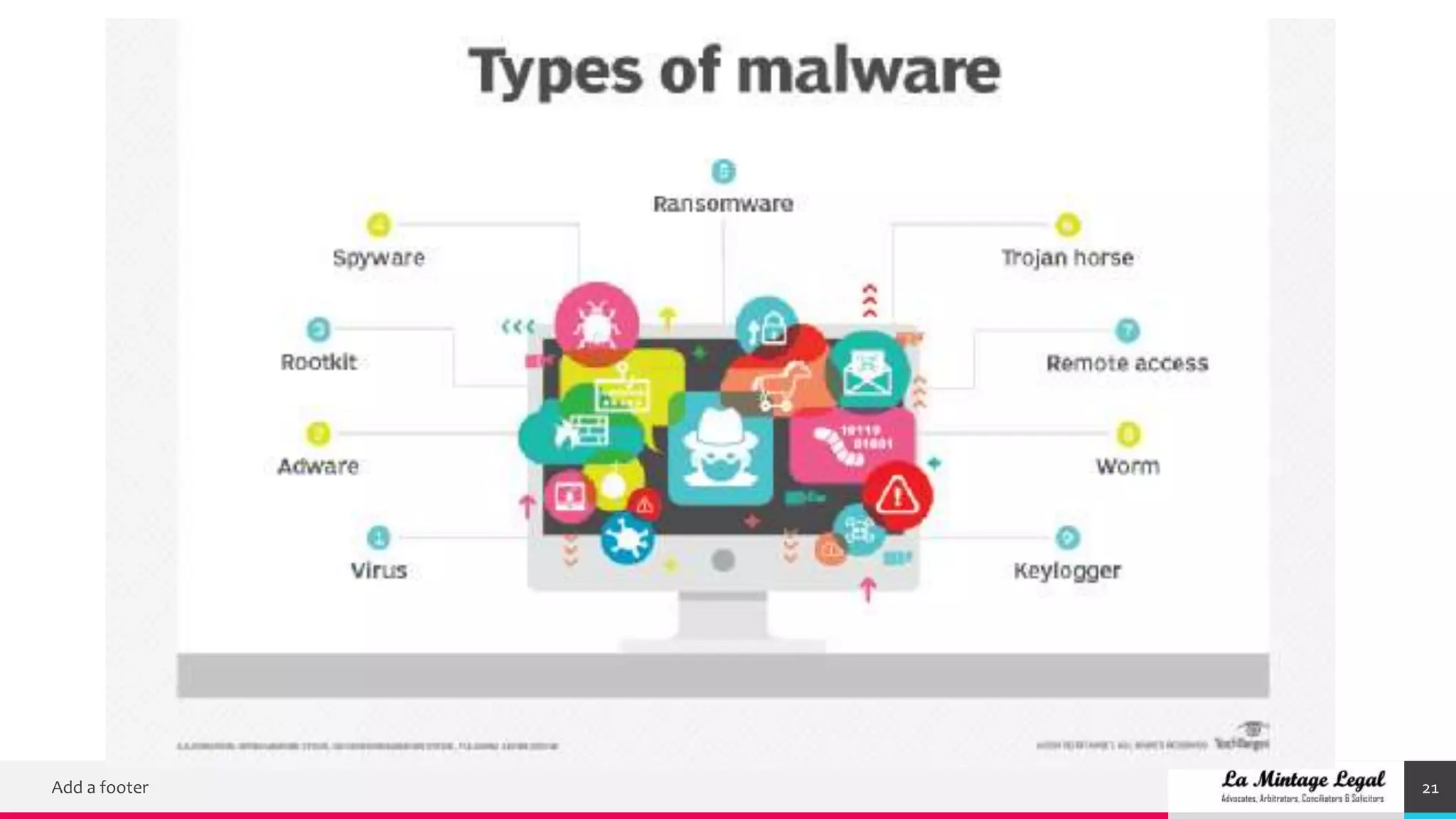
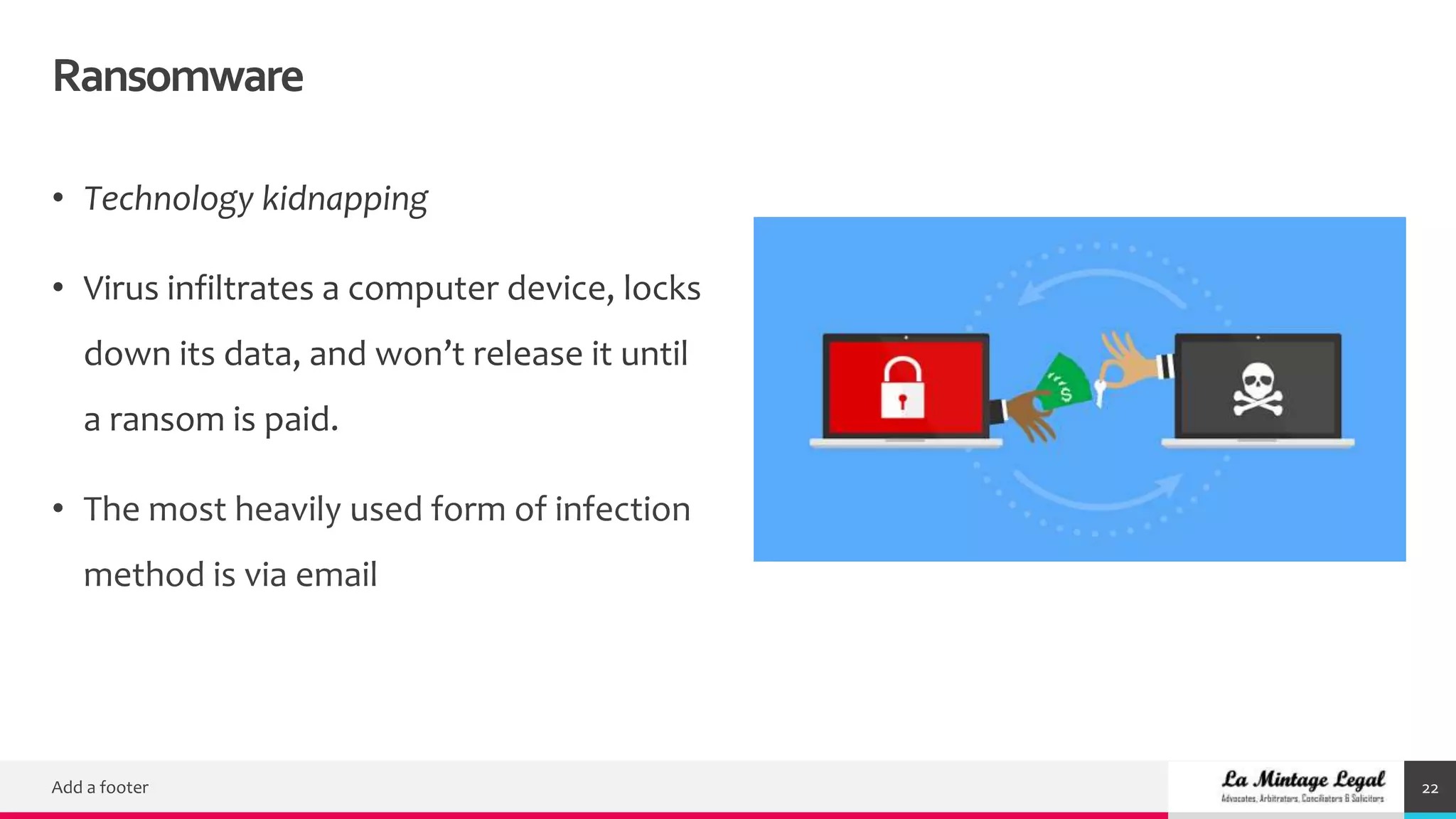
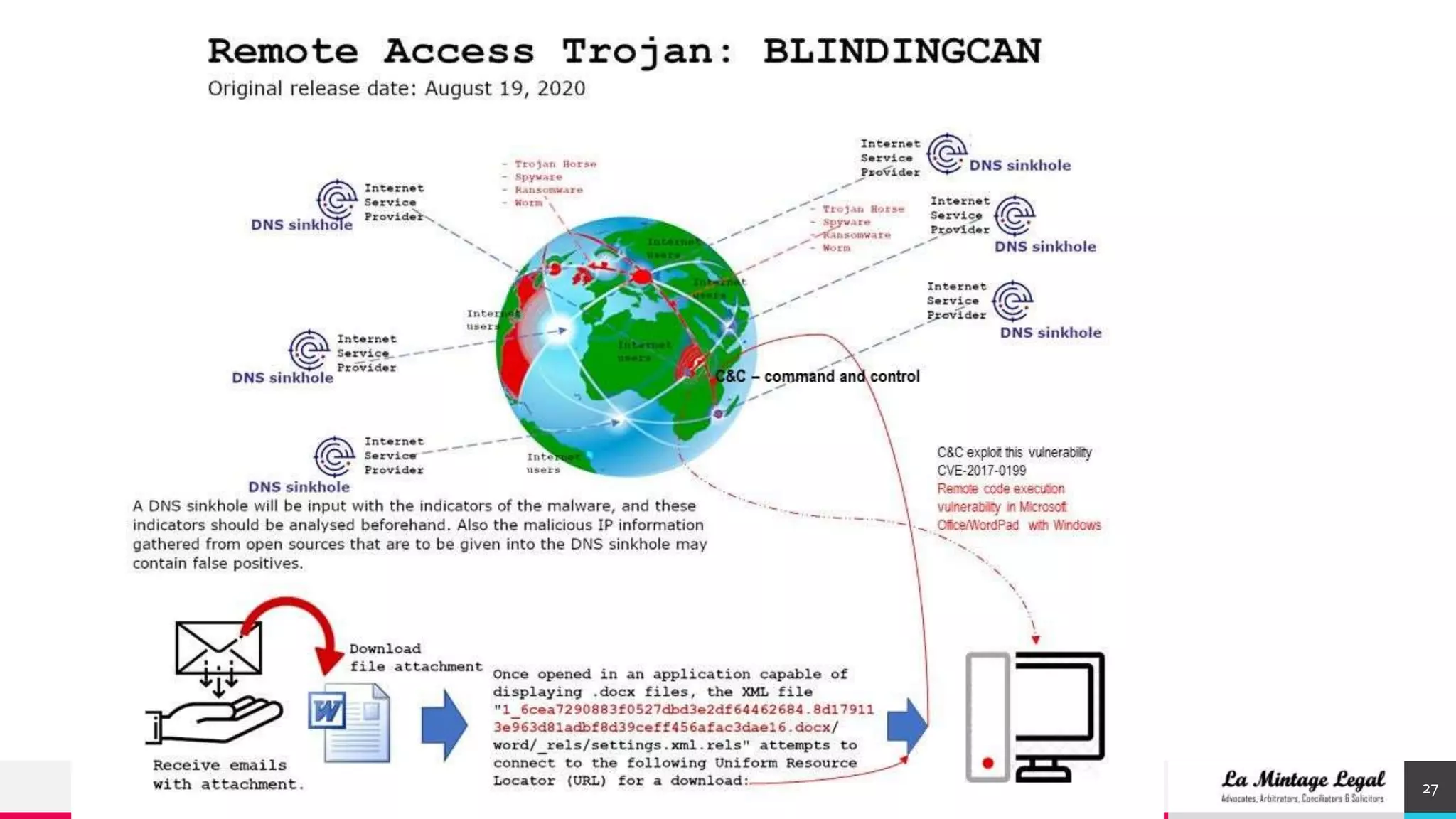
This document discusses various cybersecurity case studies including network security, data loss prevention, cloud security, intrusion detection systems, ransomware, remote access trojans, and data breaches involving Facebook, Google, WhatsApp, and Wells Fargo. It examines the technical aspects of these security issues and potential discussion points around topics like trust, transparency, data usage, privacy, and responses to security incidents.