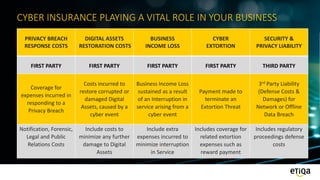
This document discusses cyber insurance and its importance for businesses. It outlines several key types of coverage provided by cyber insurance policies, including privacy breach response costs, digital asset restoration costs, business income loss, cyber extortion, and security and privacy liability. It provides examples of how each type of coverage would apply in different cyber incident scenarios a business might face. It emphasizes that the costs of a cyber attack can far outweigh the costs of investing in cybersecurity solutions and cyber insurance.