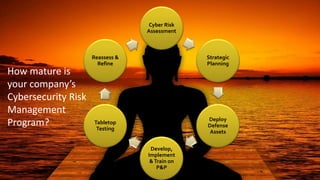
The document emphasizes that cybersecurity is a critical business risk that extends beyond IT, necessitating legal compliance with various regulations like GDPR and HIPAA. It outlines common vulnerabilities and preventative best practices including risk assessments, employee training, and incident response plans to safeguard companies against cyber threats. It also discusses the importance of maintaining a comprehensive cybersecurity program tailored to the specific needs and risks of the organization.







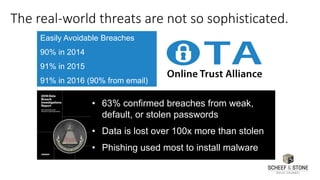







![www.solidcounsel.com
New York Department of Financial Services Cybersecurity (NYDFS)
Requirements for Financial Services Companies + [fill in]
• All NY “financial institutions” + third party service providers.
• Third party service providers – examine, obligate, audit.
• Establish Cybersecurity Program (w/ specifics):
• Logging, Data Classification, IDS, IPS;
• Pen Testing, Vulnerability Assessments, Risk Assessment; and
• Encryption, Access Controls.
• Adopt Cybersecurity Policies.
• Designate qualified CISO to be responsible.
• Adequate cybersecurity personnel and intelligence.
• Personnel Policies & Procedures, Training, Written IRP.
• Chairman or Senior Officer Certify Compliance.](https://image.slidesharecdn.com/2017-170908022806/85/The-Legal-Case-for-Cybersecurity-16-320.jpg)