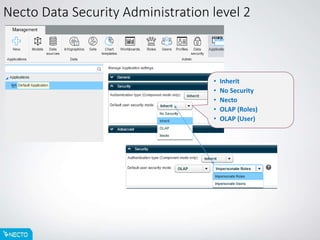
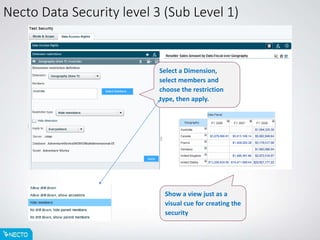
This document provides an overview of Necto data security setup and administration. It discusses the different levels of Necto data security including administration, application, and data levels. It also describes the hierarchy and precedence of security levels, with data security being the highest. An example is given of how data security restrictions would override other security settings for a specific user. The agenda covers Necto data security administration, roles, and custom restrictions that can be applied at the dimension and member levels.