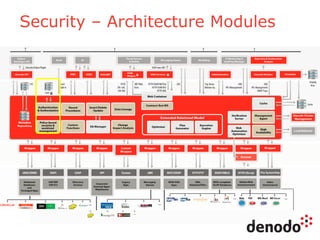
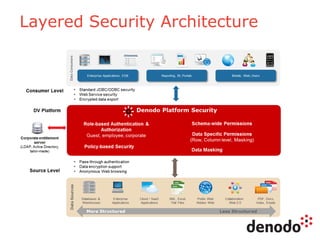
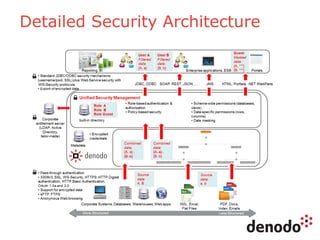
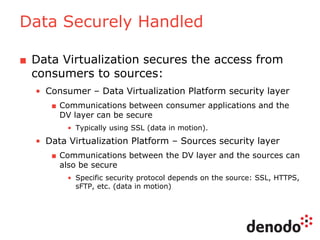
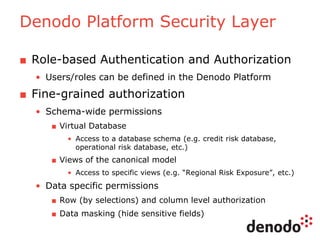
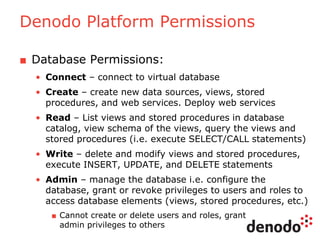
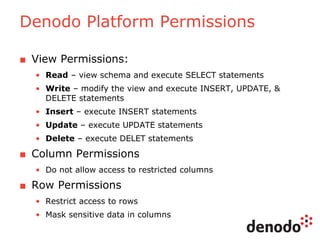
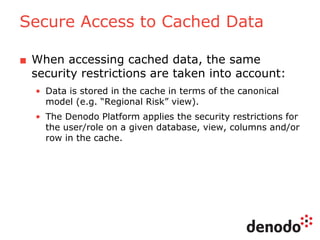
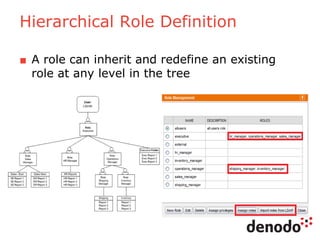
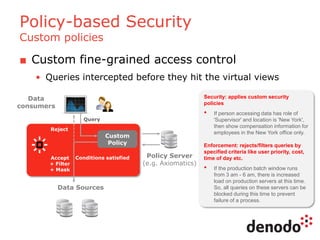
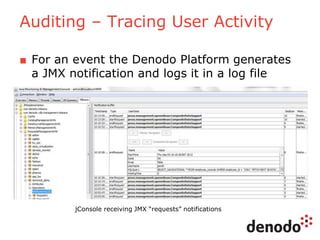
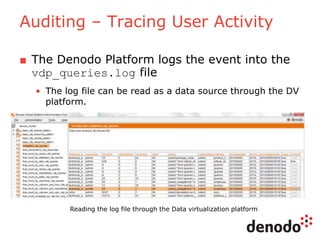
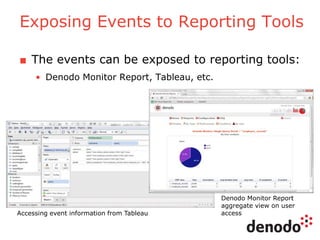
The document outlines a technology session on security within the Denodo data virtualization platform, highlighting features such as user authentication, role management, and access controls. It describes a three-layered security architecture with fine-grained permissions and integration with existing security systems like LDAP and Active Directory. The session emphasizes comprehensive auditing capabilities and the importance of secure data access for consumers, with details on custom policy enforcement.