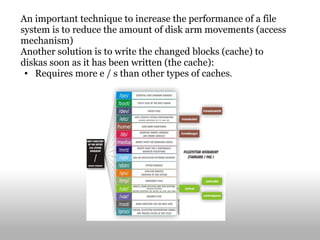
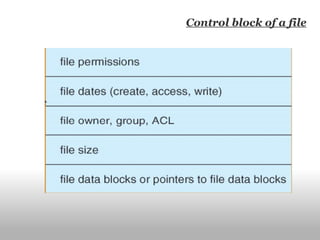
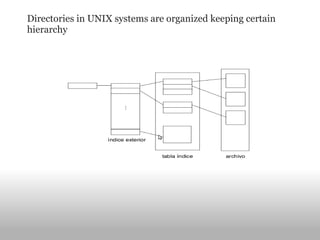
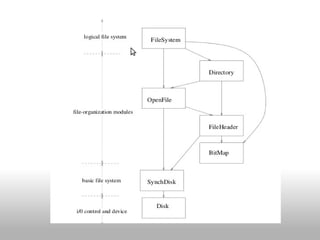
The document discusses the differences between user programs and the kernel. It explains that the kernel runs in supervisor mode and manages system resources, loading and allocating memory for user programs. It also covers virtual memory systems, how they use page tables to map virtual to physical addresses, and how the page fault handler works to load pages from disk when needed. Finally, it discusses file systems and techniques used like block buffer caches to reduce disk access and improve performance.