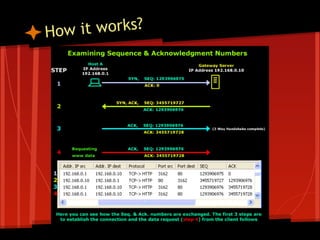
The document discusses the networking abstraction in NachOS which uses mailboxes for communication between closely connected machines, with messages that are unreliable but not corrupted, and provides ordered and fixed-sized messages. It explains the handshake process between a host and gateway server using sequence numbers to establish and acknowledge connections. Sources are provided for further information on TCP sequence and acknowledgement numbers, networking topics, and an open courseware blog.