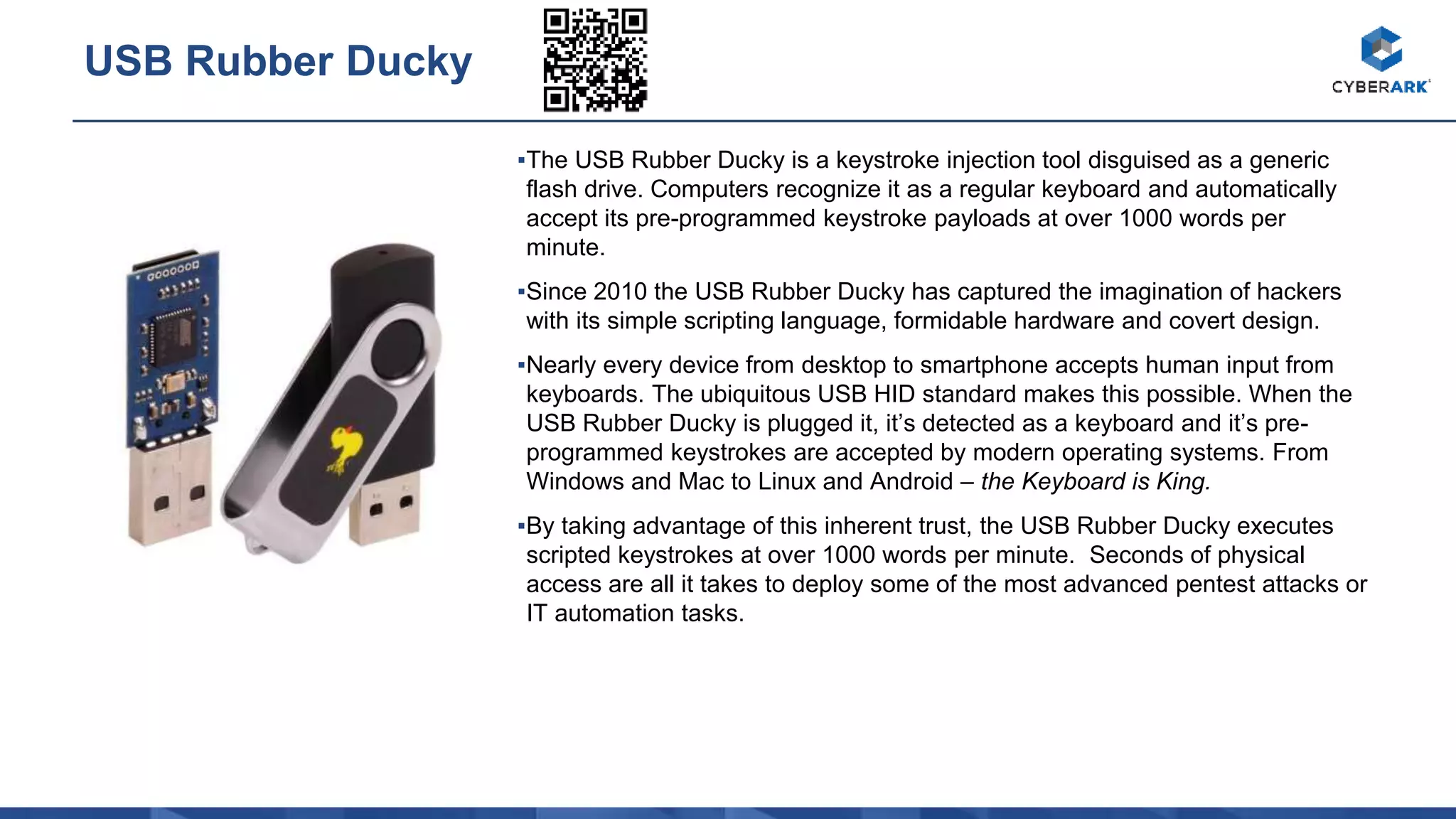
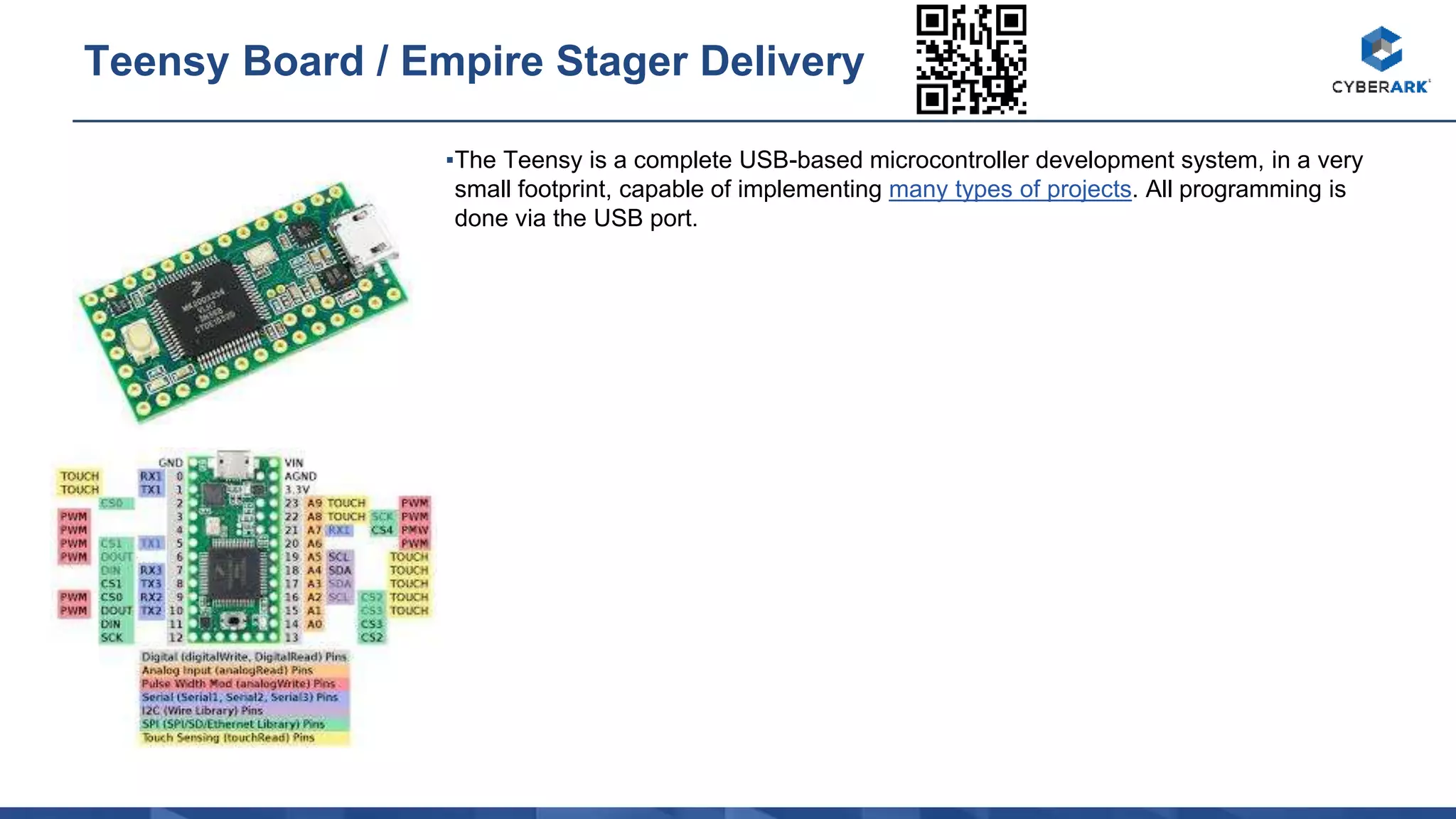
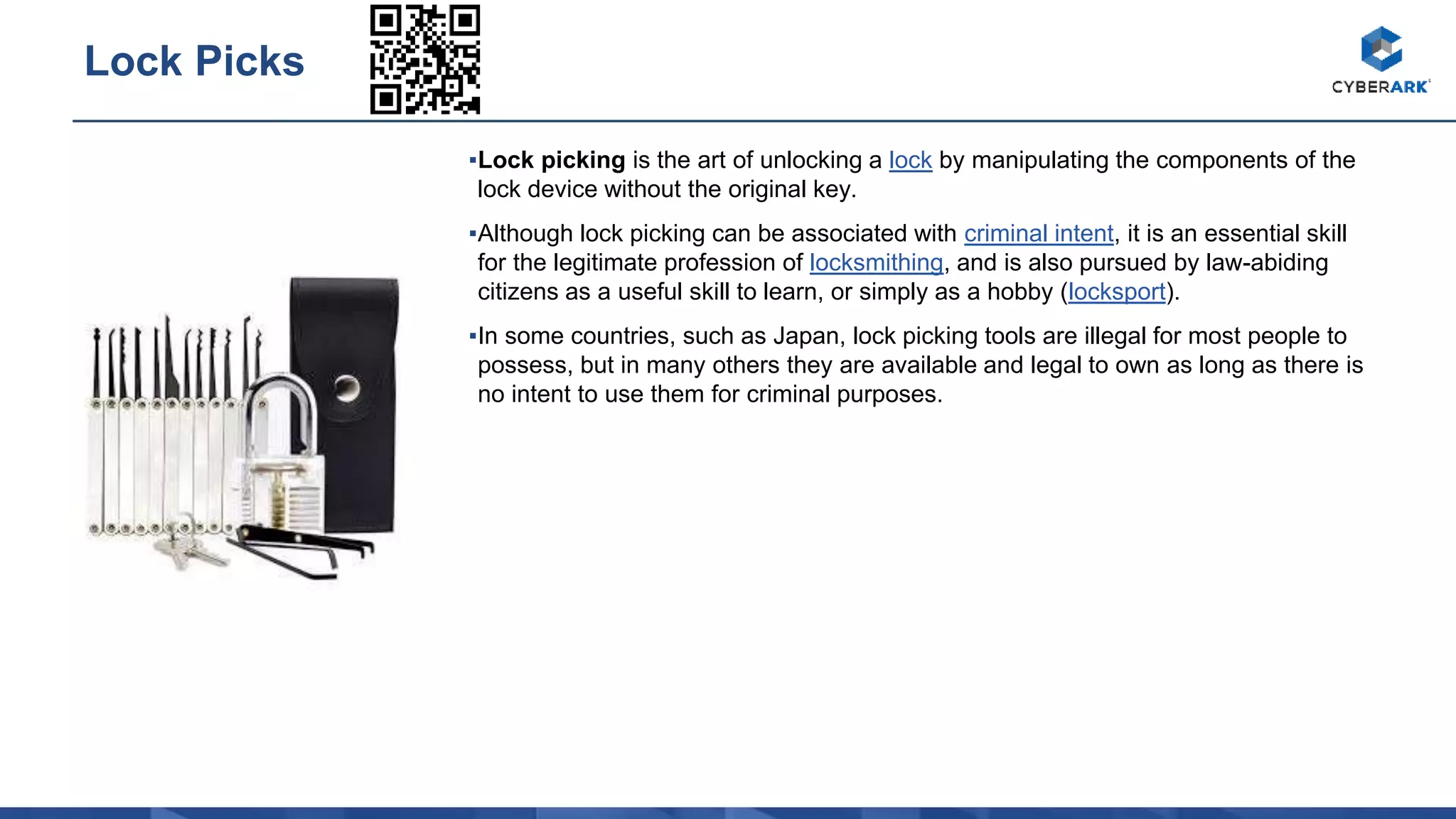
The document provides descriptions of various hacking and security tools including the Bash Bunny USB attack platform, Packet Squirrel network device, LAN Turtle covert access tool, USB Rubber Ducky keystroke injection tool, WiFi Pineapple rogue access point, Proxmark RFID hacking tool, HackRF Software Defined Radio, Crazy Radio wireless keyboard/mouse attack tool, Digispark USB keystroke injection board, Orange Pi single board computer, Raspberry Pi models, RTL-SDR Software Defined Radio, USB magnetic stripe card reader/writer, USB smart card reader, lock picking tools, encrypted USB drive, barcode scanner, portable electronics kit, and standalone RFID cloning device.