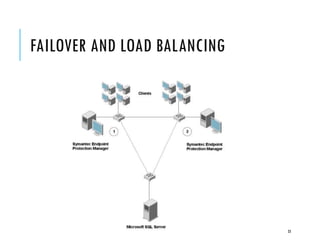
The document provides an overview of configuring replication, failover, and load balancing for Symantec Endpoint Protection across multiple sites. It outlines the necessary steps for setting up replication partners, managing data consistency, and handling conflicts during replication. Additionally, it explains the process of failover and load balancing to ensure continuous client-server communication under various circumstances.