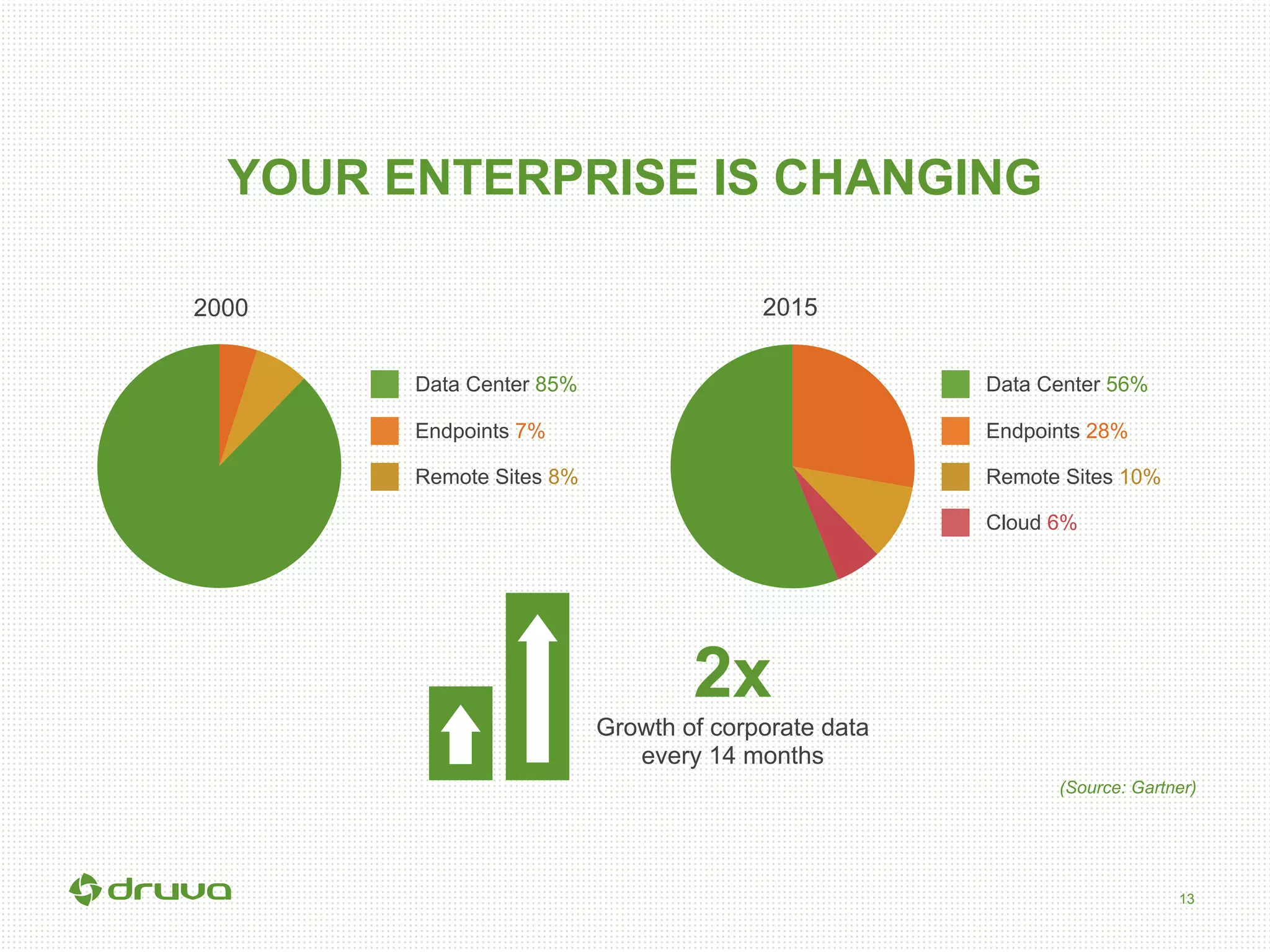
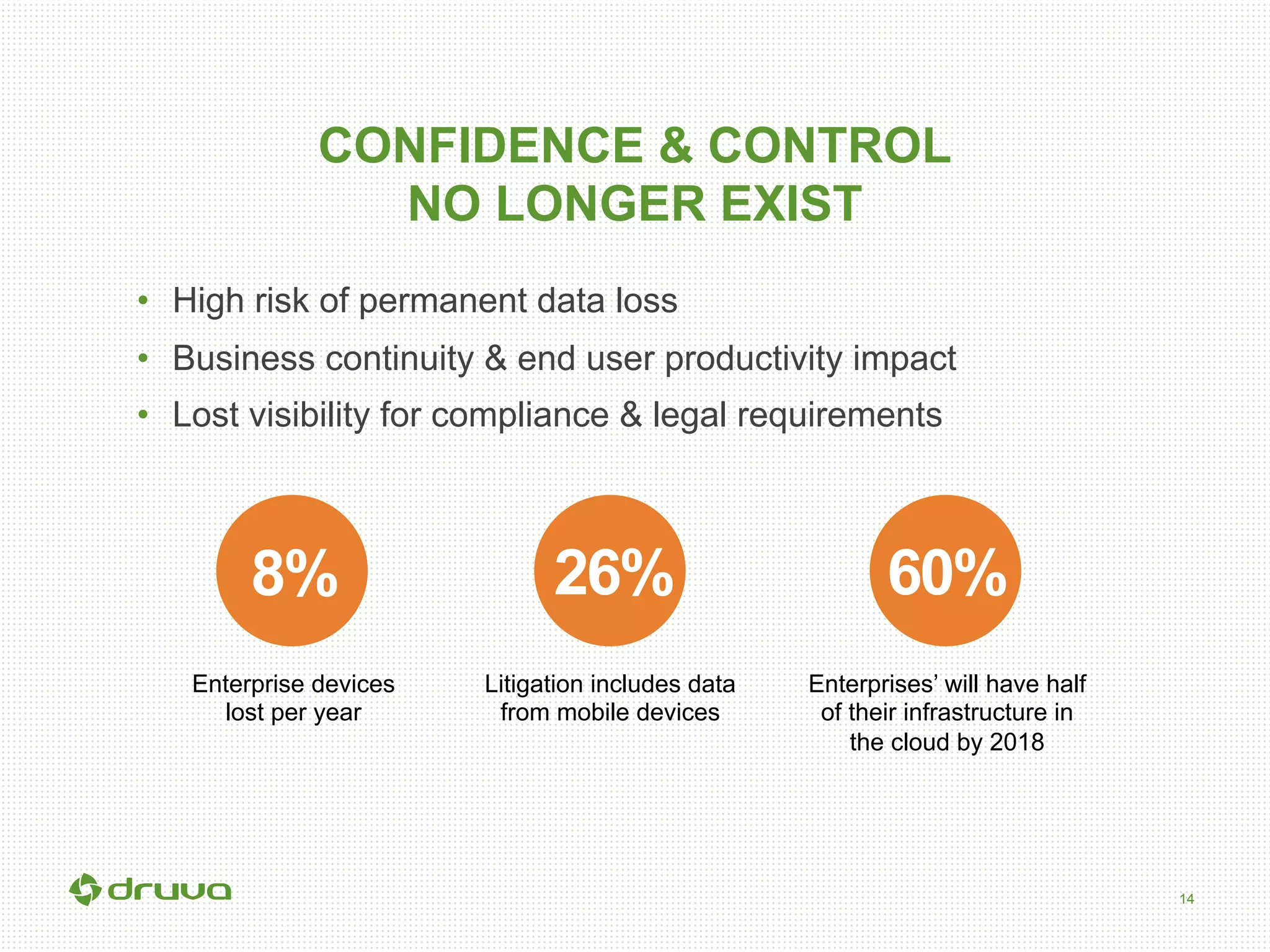
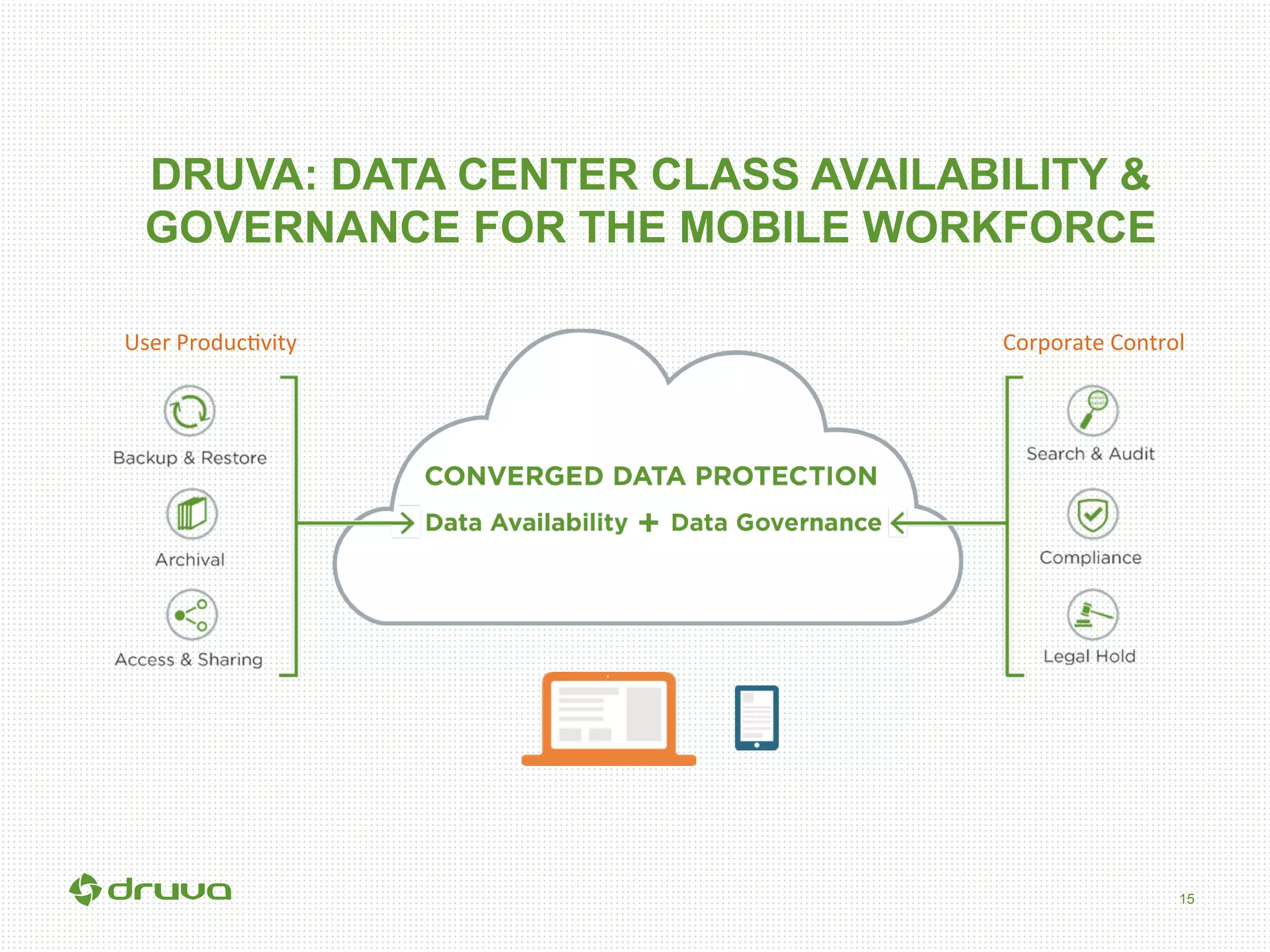
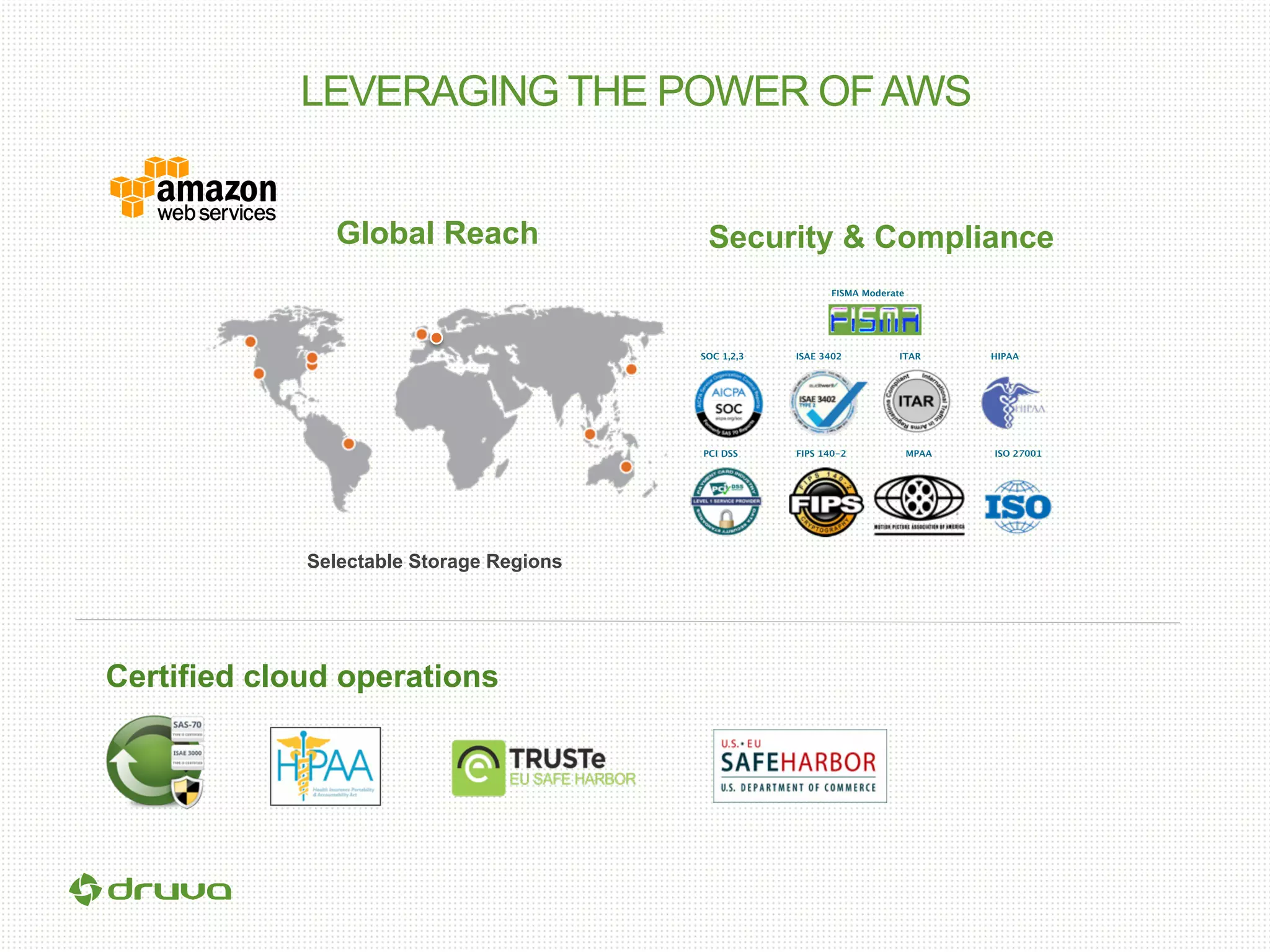
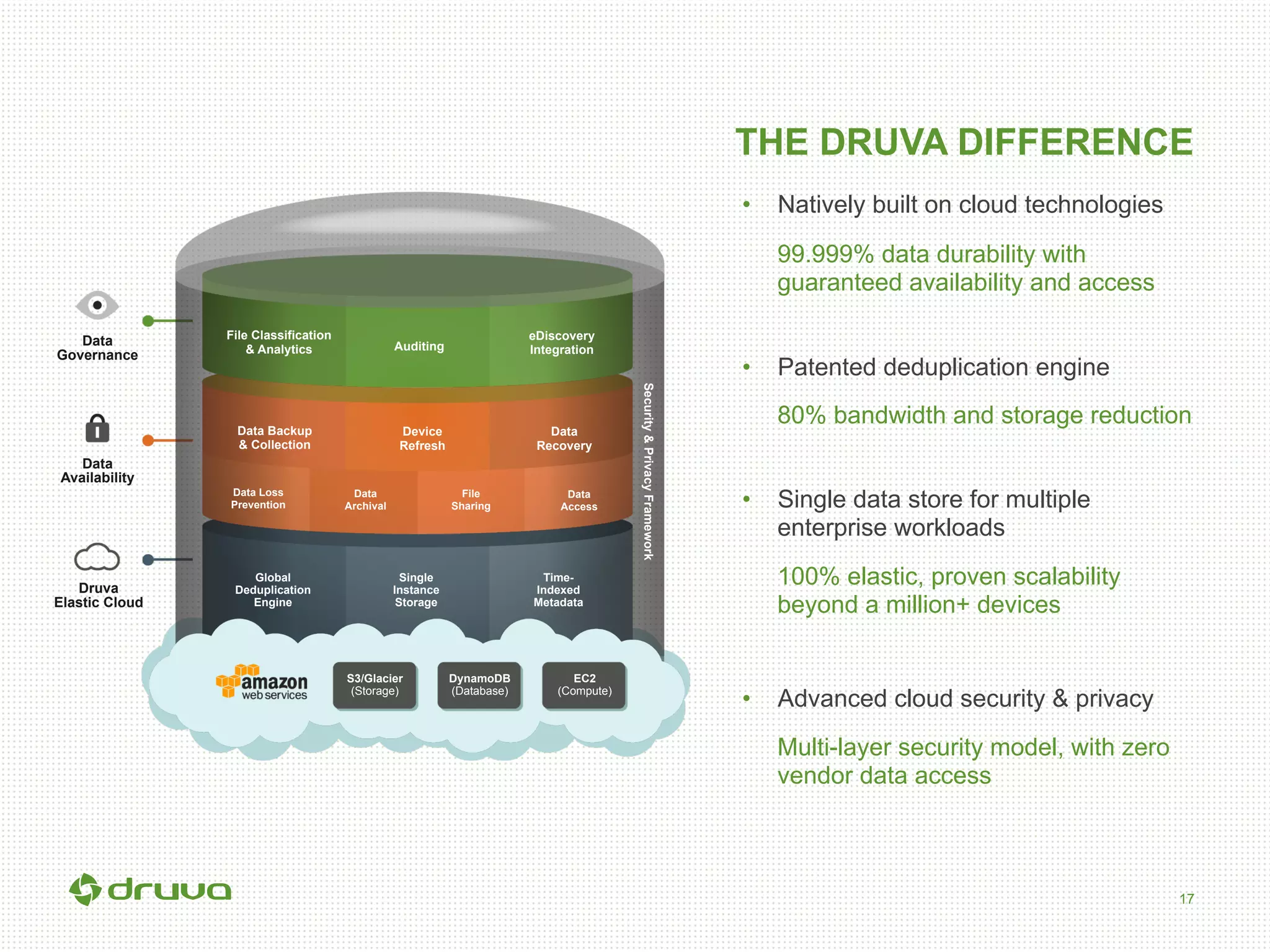
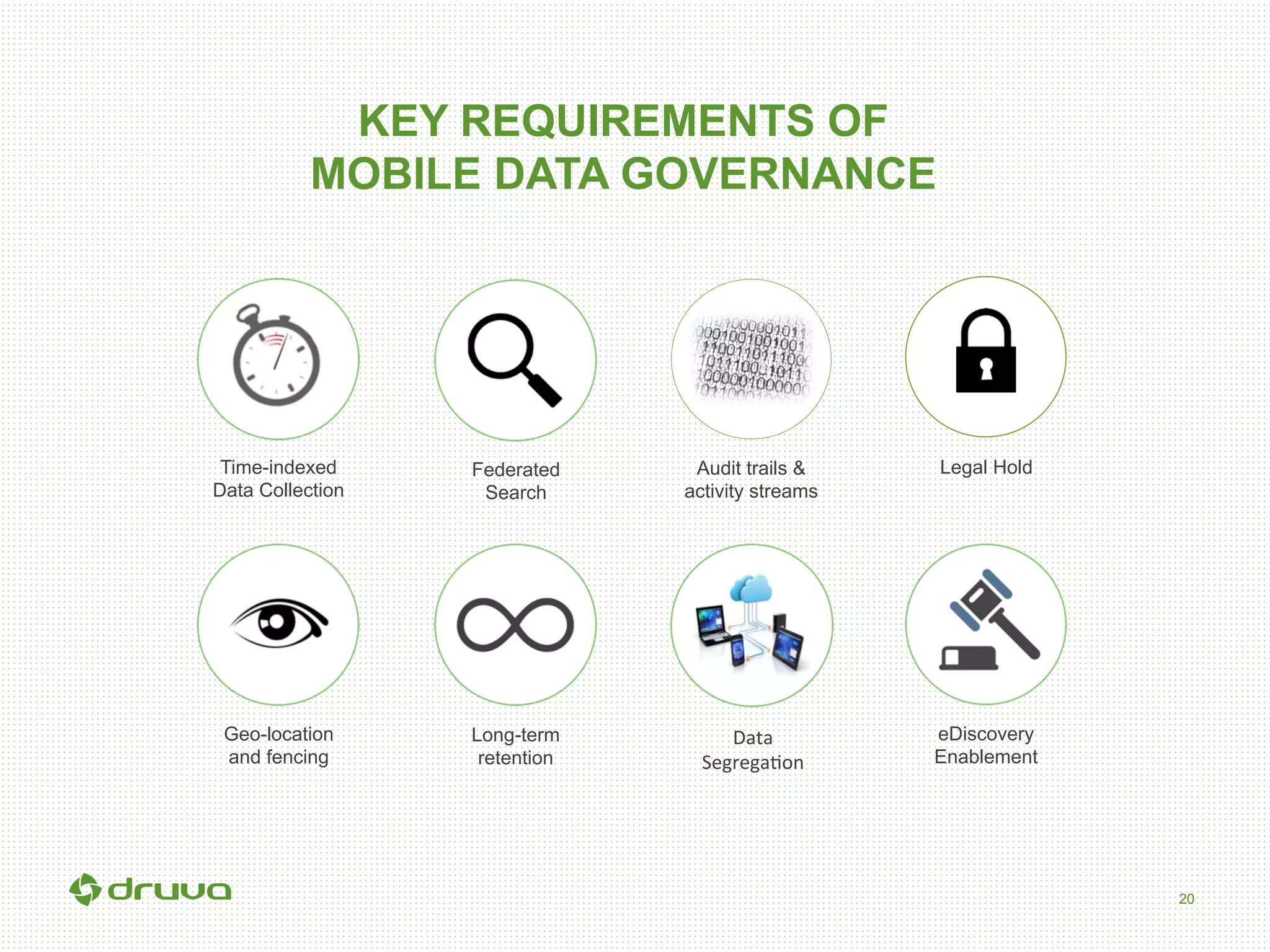
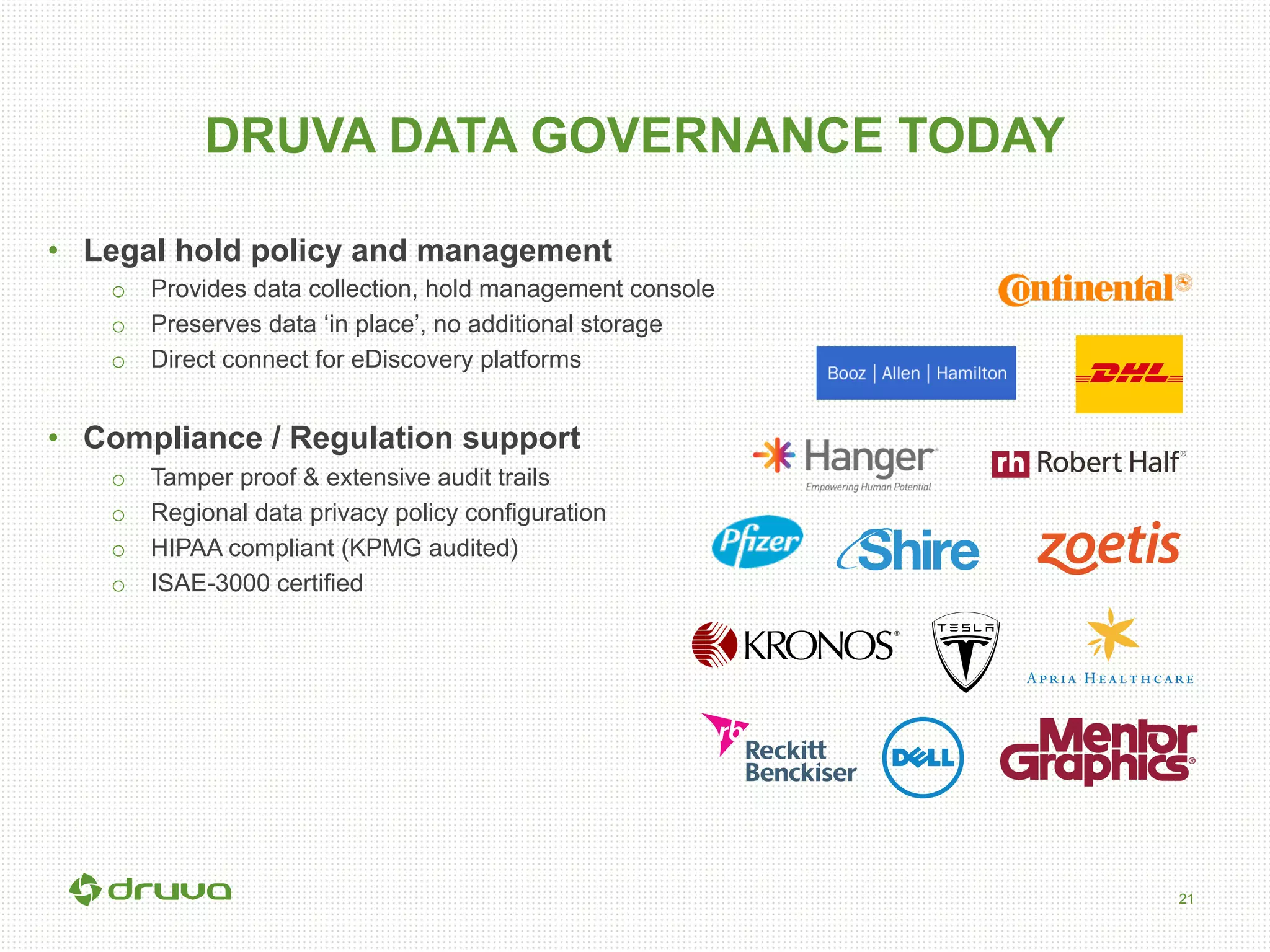
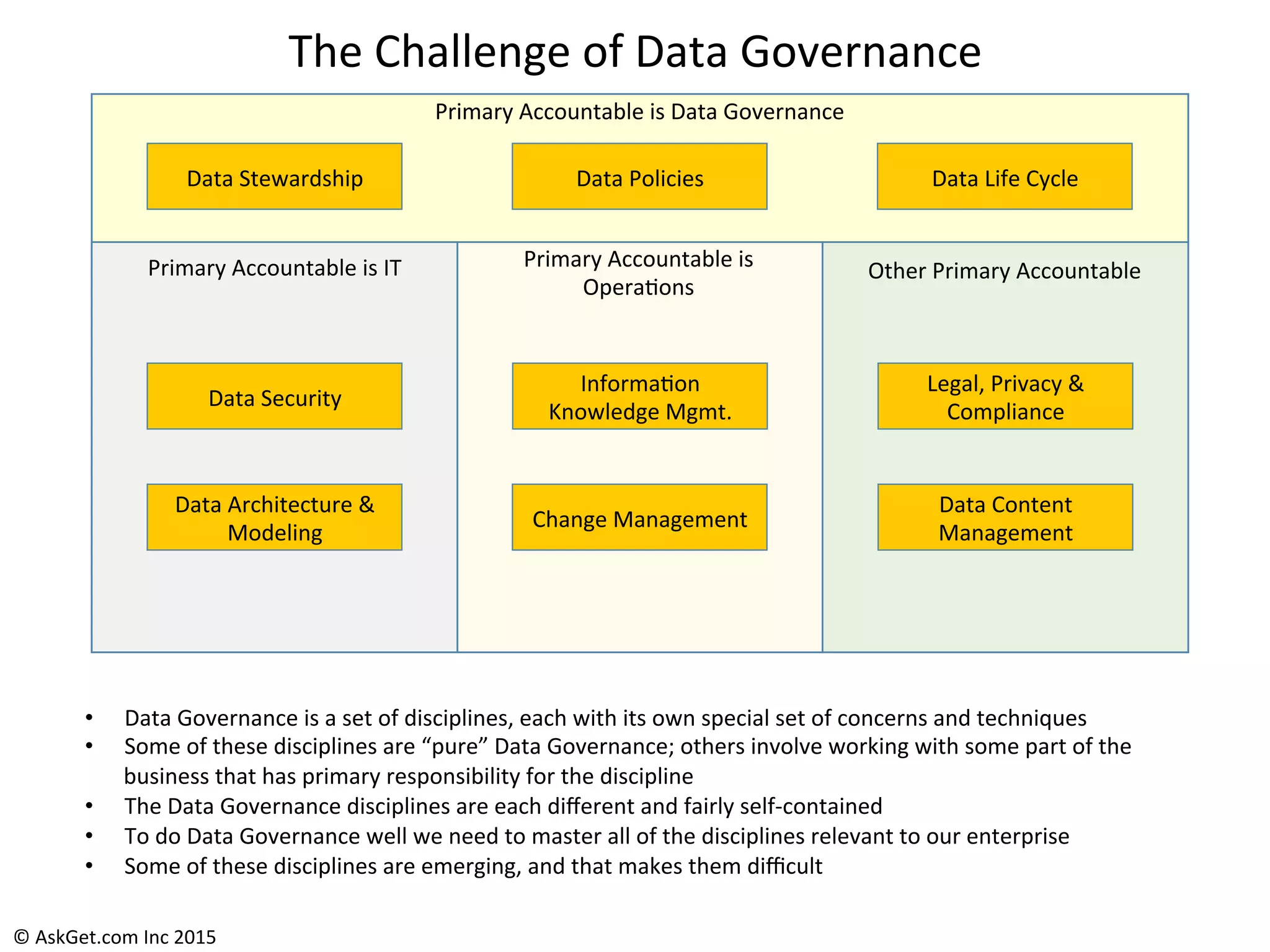
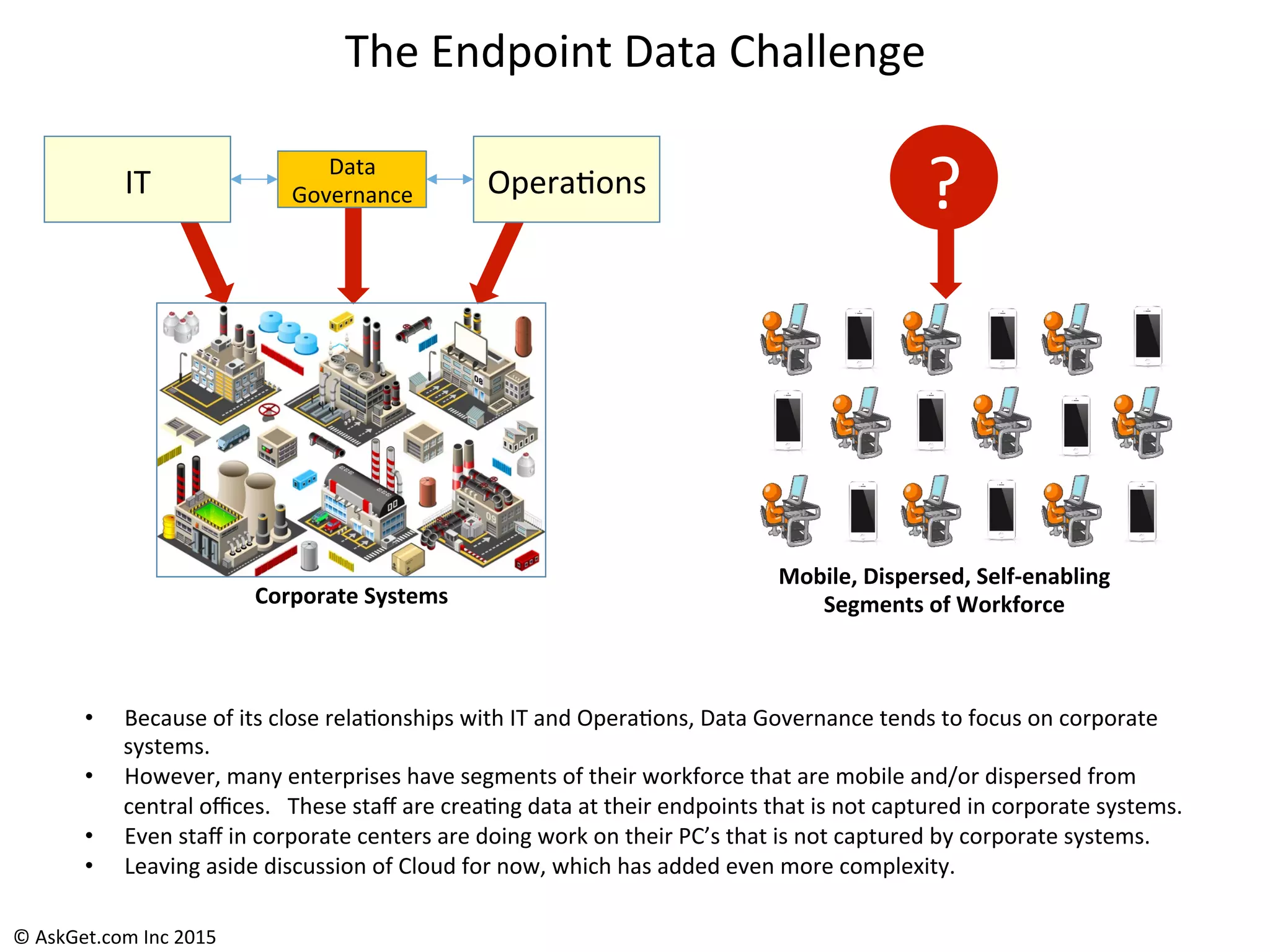
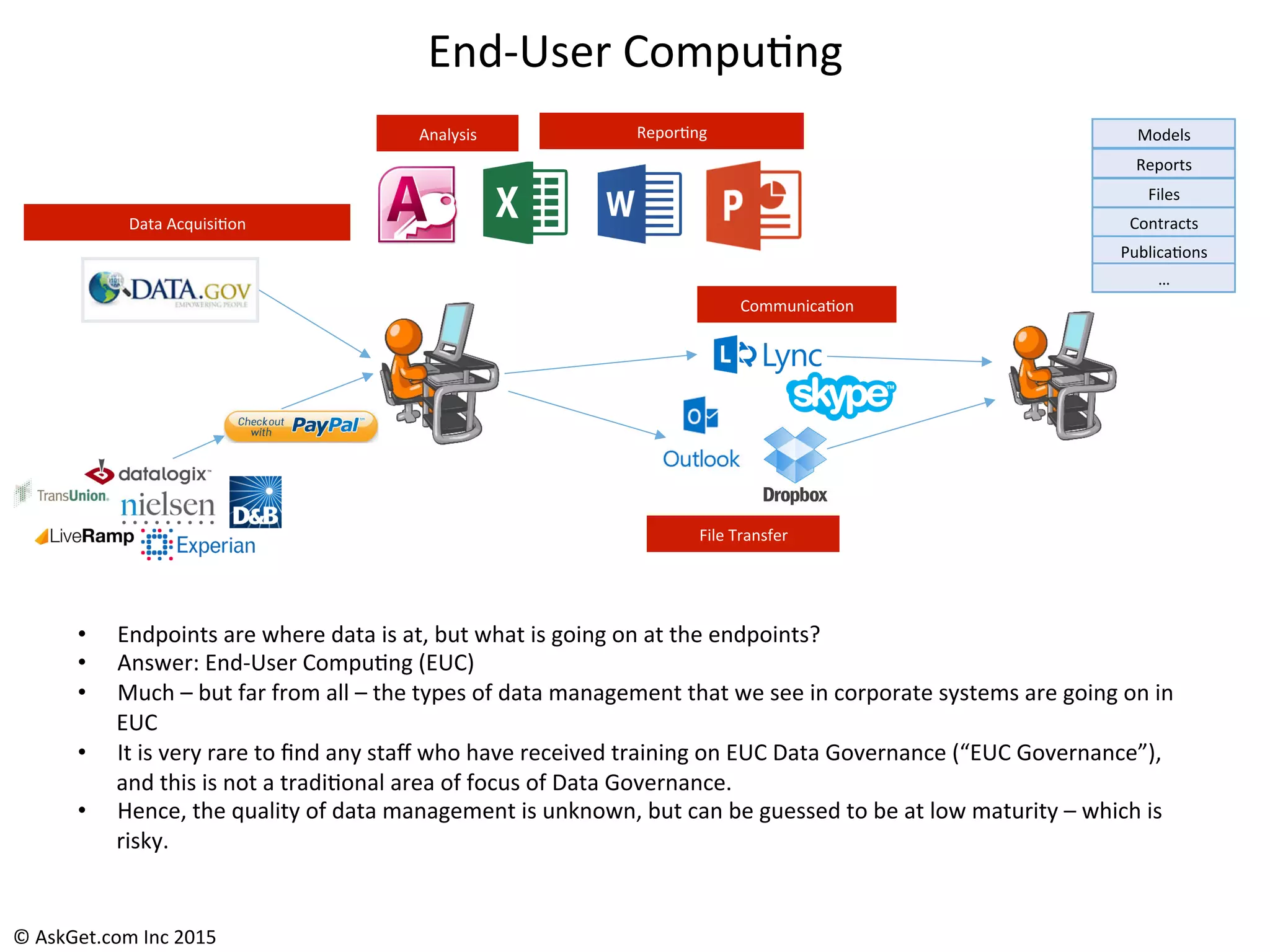
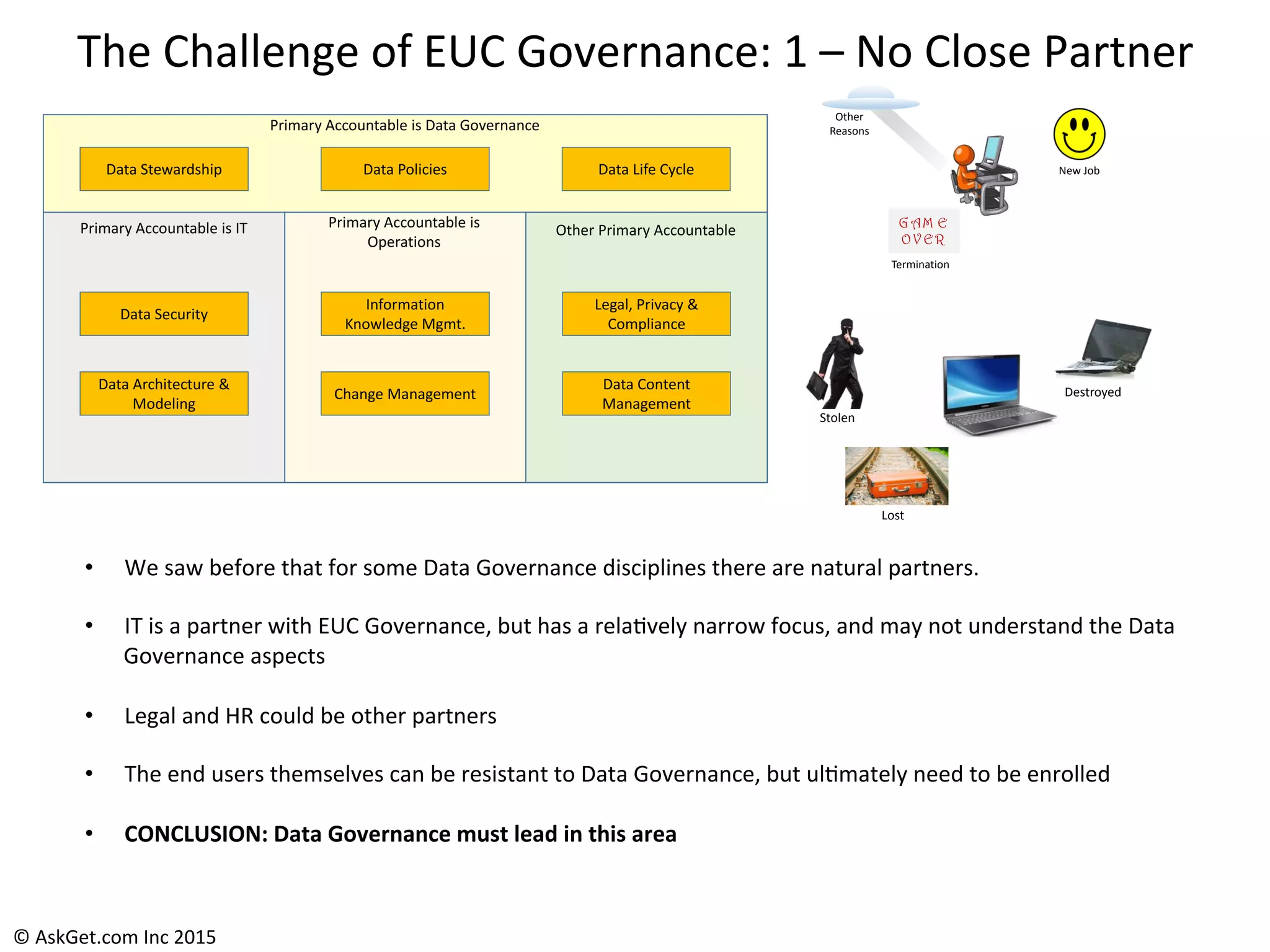
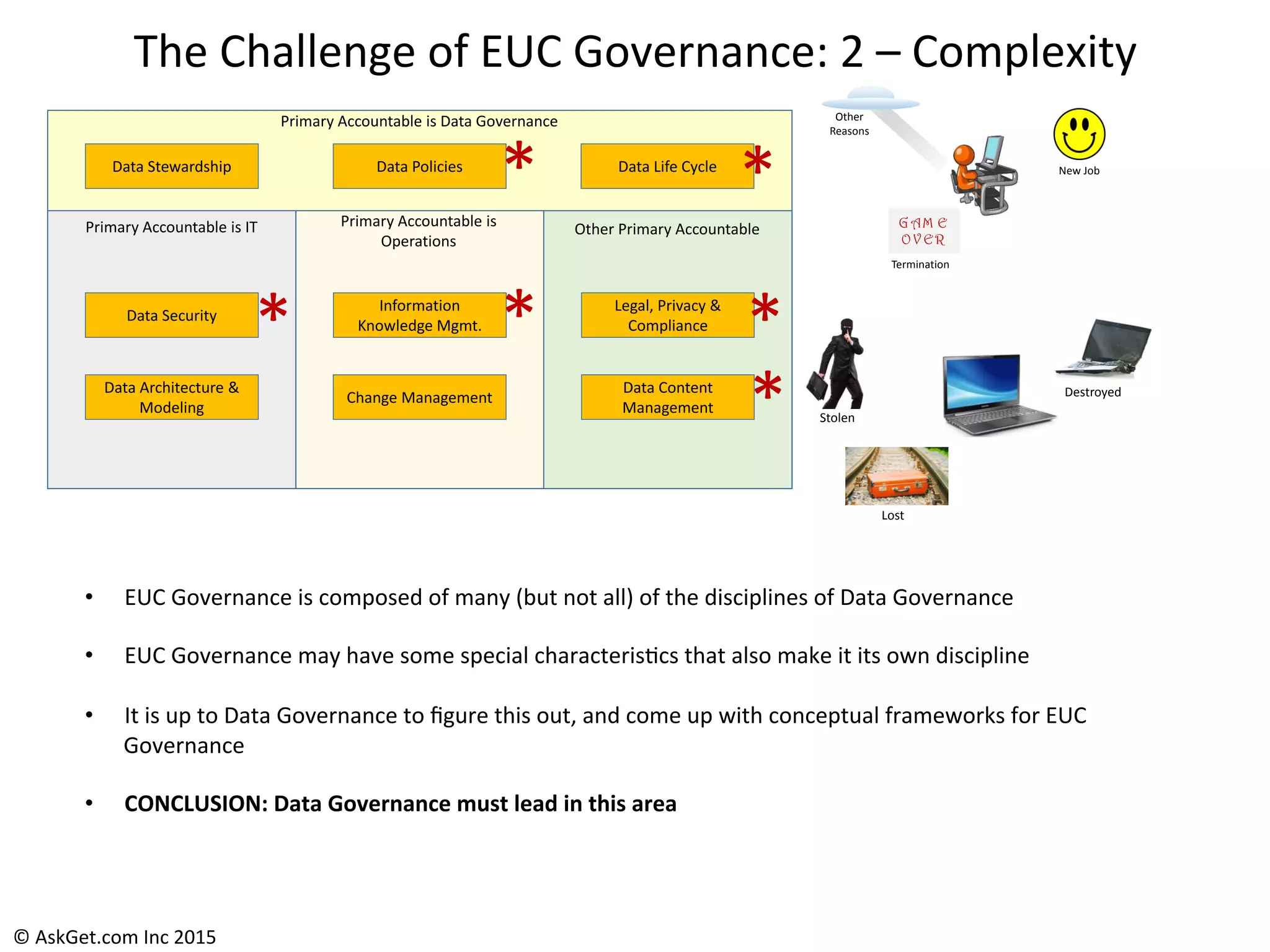
The document outlines a briefing led by Eric Kavanagh on data availability and governance in a mobile world, focusing on the importance of data protection, particularly through the lens of the company Druva. It highlights the challenges of endpoint data governance, including issues with mobile workforces and the need for robust data management practices. The document also discusses the crucial role of data governance in maintaining control over enterprise data amidst the rapid growth of corporate data and the shift to cloud infrastructures.