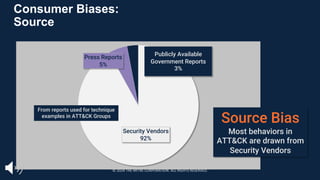
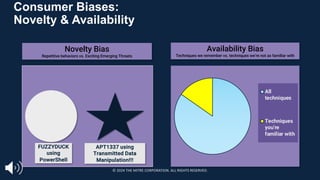
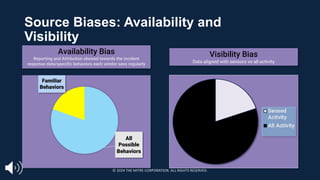
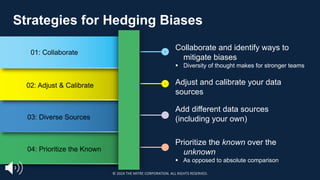
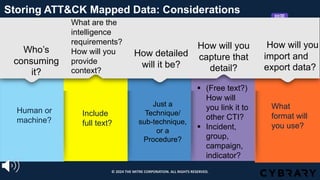
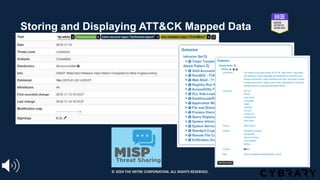
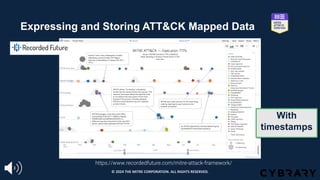
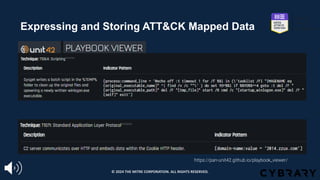
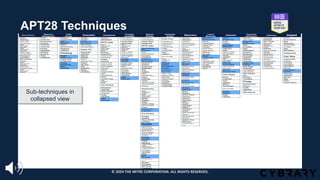
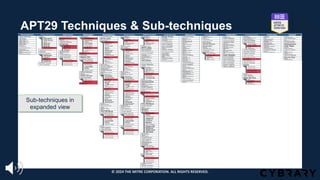
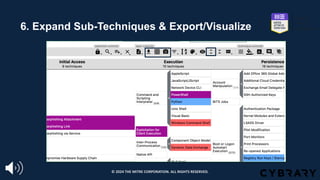
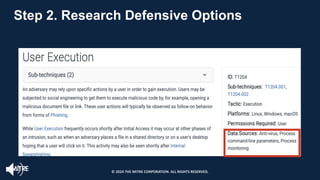
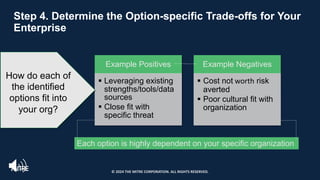
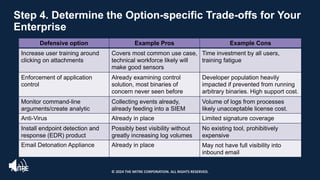
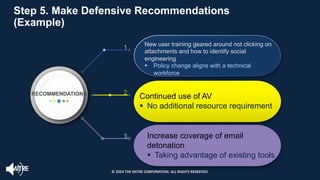
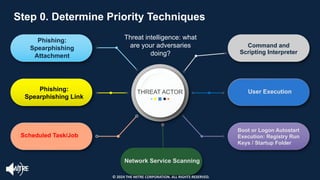
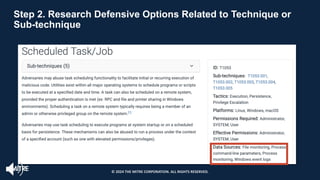
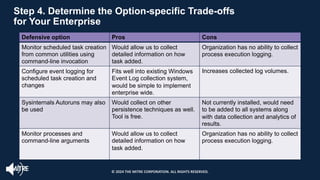
The document introduces the MITRE ATT&CK framework for cyber threat intelligence, detailing its utility in enhancing defenders' understanding of adversarial behaviors and assisting in incident response. It outlines the training structure, objectives, and various modules aimed at mapping narrative and raw data to ATT&CK, storing and analyzing ATT&CK-mapped data, and translating behavioral insights into actionable recommendations. The training promotes a common language and systematic approach for cyber threat analysts to improve communication and effectiveness in addressing threats.


























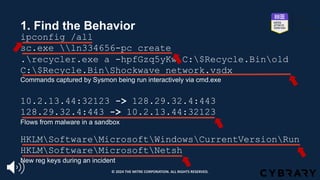
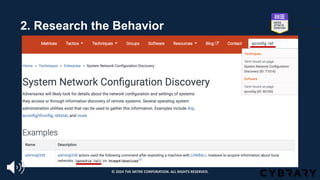
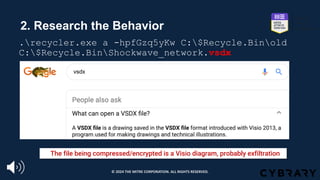
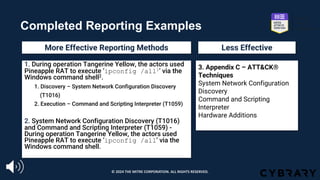
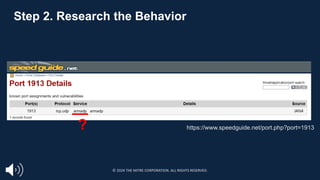
![Step 1: Find the Behavior
https://www.fireeye.com/blog/threat-research/2014/11/operation_doubletap.html
[Tactic] | 1. [Technique/Sub-technique]
[Tactic] | 2. [Technique/Sub-
technique]
© 2024 THE MITRE CORPORATION. ALL RIGHTS RESERVED.](https://image.slidesharecdn.com/ctiworkshopfullslides-241106113343-17d65f61/85/CTI-Workshop-Full-Slides-Workshop-Full-Slides-pdf-28-320.jpg)












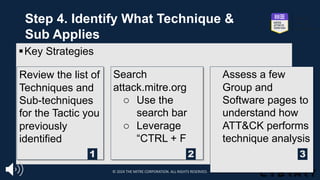
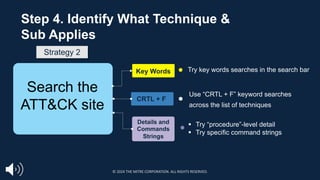
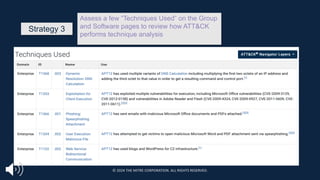
![Step 4. Identify What Technique &
Sub Applies
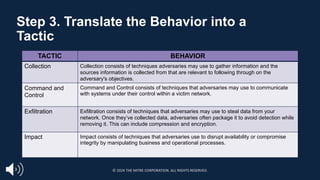
§ Identifying the technique or sub-technique is often the most challenging step
□ Techniques and subs are not always easy to identify
□ Some techniques help facilitate more than one tactic, and this is reflected throughout
ATT&CK
§ For example, Hijack Execution Flow: DLL Side-Loading [T1574.002]
falls under Persistence, Privilege Escalation, Defense Evasion
© 2024 THE MITRE CORPORATION. ALL RIGHTS RESERVED.](https://image.slidesharecdn.com/ctiworkshopfullslides-241106113343-17d65f61/85/CTI-Workshop-Full-Slides-Workshop-Full-Slides-pdf-43-320.jpg)