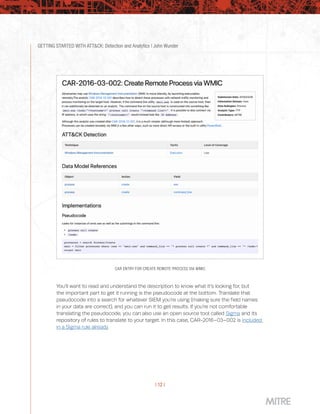
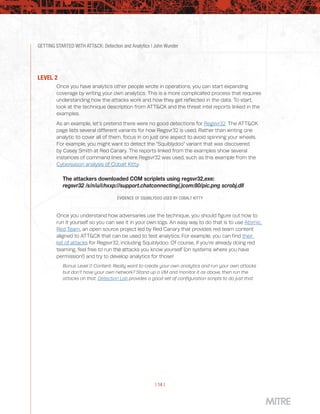
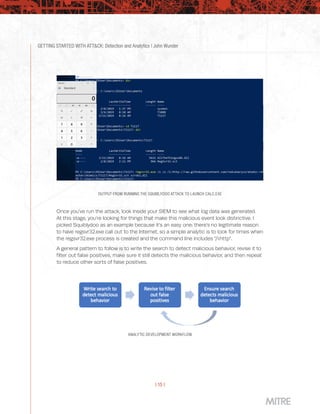
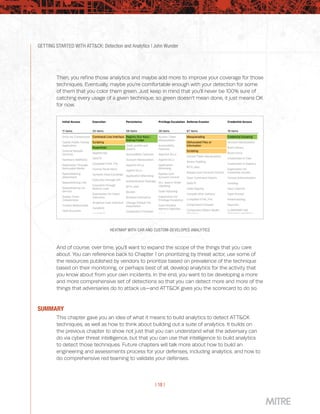
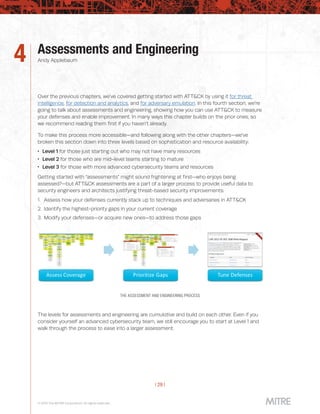
This document provides guidance on getting started with using the MITRE ATT&CK framework for threat intelligence, detection and analytics, adversary emulation and red teaming, and assessments and engineering. It is broken into chapters that each focus on one of these use cases and provide advice at three different levels - level 1 for those just starting out, level 2 for mid-level teams, and level 3 for more advanced teams. The chapter on detection and analytics discusses starting with understanding available data sources and search capabilities, collecting relevant data into a security information and event management system, and running example analytics created by others to detect adversary techniques.