The document introduces Vehicular Ad Hoc Networks (VANETs) as a subtype of Mobile Ad Hoc Networks (MANETs), emphasizing their role in enabling real-time communication for intelligent transportation systems. It outlines the architecture of VANETs, including components such as On-Board Units (OBUs) and Road-Side Units (RSUs), and discusses various applications aimed at enhancing road safety and comfort for drivers and passengers. The thesis proposes a new adaptive AODV routing protocol using a genetic algorithm to improve performance metrics like throughput and packet delivery in VANETs.
![For More Info: Https://www.ThesisScientist.com
Chapter 1
INTRODUCTION OF VANET
1.1 Introduction:
The increasing demand of wireless devices and wireless communication tends to research on self
organizing, self healing networks without the interference of any pre-established or centralised
infrastructure/authority [2]. The networks with the absence of any pre-established or centralised
authority are known as Ad hoc networks [4]. Ad hoc Networks are the kind of wireless networks
that uses multi hop radio relay.
Figure 1.1: Working structure of VANET
Vehicular Ad hoc Networks (VANET) is the subtype of Mobile Ad Hoc Networks
(MANETs) [4]. It is the most developed technology that confers Intelligent Transportation
System (ITS) in wireless communication among road side equipment (RSUs) to vehicles and
vehicles to vehicles (V2V) according to IEEE 802.11p standard. VANET provides broad range
of security and non security applications. Security application provides security to the passengers
such as lane change warning, collision detection etc. It also provides commercial and comfort
applications to the road users such as video exchanging, audio exchanging, electronic payments,
weather information, route guidance, electronic toll collect, mobile E-commerce etc. Figure
1.1[1] shows the overall working structure of Vehicular Ad hoc Network (VANET).](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/75/Aodv-routing-protocol-implementation-design-1-2048.jpg)
![For More Info: Https://www.ThesisScientist.com
1.2 VANET Overview:
VANET can be applied for large vicinity of security and non security purposes, permit for value
added services like traffic management , location based services to finding the fuel station, travel
lodge, restaurants and commercial applications such as providing path to the internet. vehicular
ad hoc network have grown out of the need to support the growing number of wireless products
or instances that can now be used in vehicles. Mobile telephones, PDAs(personal digital
assistants), laptops are some wireless products of instances. VANET is an advance class of
MANET (Mobile Ad-hoc Network). It manages a network in which vehicles are acting nodes
and applied as mobile nodes to make an infrastructure-less ad-hoc network. It makes the
communication network between Inter-Vehicle (V2V), Vehicle-to-Roadside (V2R) and Inter-
Roadside [1]. Vehicular Ad-hoc Network (VANET) is a novel developed kind of Mobile Ad-
hoc Network (MANET), where travelling nodes are vehicles like cars, buses, autos etc.
1.2.1 VANET Architecture:
Vehicular Ad hoc Network (VANET) architecture [5] exists of the different types of domains
such as ad hoc, in-vehicles and infrastructure domains and many components such as
application unit(AU), on-board unit(OBU), and road-side unit(RSU). The figure 1.2[14] shows
the all domains and components of VANET.
In-Vehicle Domain: In-vehicle domain consists of one or more than one applications units
(AUs) and one On-Board Unit (OBU) that inhabits inside a vehicle [19]. Applications Units
(AUs) is an in-vehicle existence, more than one AUs can be plugged in with a one OBU and
share the wireless resources and OBU processing. An On-Board Unit (OBU) is used for
providing the vehicle-to-vehicle (V2V) communication and vehicle-to-infrastructure (V2I)
communication. An OBU is fitted with a sole network device based on IEEE 802.11p radio
technology; basically network device is used for sending, receiving and forwarding the security
and non security messages in the ad hoc domain .
Ad hoc Domain: Ad hoc VANET domain composed of vehicles or nodes that equipped with
On-Board Unit (OBUs) and road-side units (RSUs), that forming the VANET[19]](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-2-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Figure 1.2: VANET System Architecture.
A road side unit (RSU) is a physical device placed at fixed positions like shopping complexes,
colleges, road highways, hospitals etc. An RSU is fitted with at least a network device based on
IEEE 802.11p standard [30]. On-Board Units (OBUs) form a mobile ad hoc network (MANET)
that allows communications between the vehicles without the need of centralised coordination .
Two vehicles directly communicate via On-Board Units (OBUs) if wireless connectivity exists
among them otherwise multi-hop communications are used to forward data.
Infrastructure Domain: This type of domain consists of wireless Hot-Spots (HS) and road side
units(RSU) that the vehicles reach for comfort based applications [18, 29]..In case that neither
road side units(RSUs) nor Hot-Spots (HS) provide internet access, OBUs can also use
communication abilities of several radio networks or technologies such as GPRS if they are
unified in the On-Board Unit (OBU), in particular for non-securable applications.
Application Units (AUs): This is an inter vehicle existence, more than one AUs can be plugged
in with a one OBU and share the OBU processing [29]. Examples of Application Units (AUs)
are : safety applications devices like hazard-warning and a navigation system with
communication capabilities. More than one Application Units can be plugged in with a one On-
Board Unit (OBU) and share the On-Board Units (OBUs) processing . An Application Unit (AU)
communicates merely via the On-Board Unit (OBU), which handles all networking and mobility](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-3-320.jpg)
![For More Info: Https://www.ThesisScientist.com
functions on the Application Unit (AU) behalf. The distinction between Aus and OBU is: On-
Board Unit (OBU) is only logical and an Application Unit (AU) can be physically co-located
with an OBU [29].
On-Board Units (OBUs): This is used for vehicle to vehicle (V2V) communications and vehicle
to infrastructure(V2I) or road side unit (RSU) communications [29]. An On- Board unit also
provides communication services to the application units. It also forwards data on behalf of
other On-Board Units (OBUs) in the ad hoc domain. An On-Board Unit (OBU) is fitted with at
least a one network device of IEEE 802.11p standard. This network device is responsible for
receiving, sending and forwarding securable and non securable messages in the ad-hoc domain.
The main procedures of On-Board Unit (OBU) includes reliable message transfer, geographical
ad hoc routing, network congestion control, data security, wireless internet access and others.
Road-Side Units (RSUs): This is a physical device located at fixed positions along roads or
highways, or at dedicated locations such as shopping complexes, petrol pumps, parking places,
hospitals, schools, colleges, complexes, restaurants etc [19, 29]. A RSU is equipped with at least
one network device based on IEEE 802.11p. The main function of RSU is to provide the inter-
network connectivity to the OBUs. An overview of the functions performed by RSU is given
below.
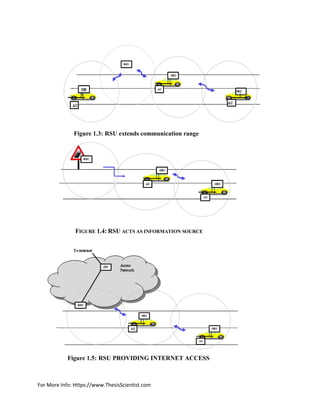
1. Extending the broadcasting range of an ad hoc network by means of re-distribution of
information to other OBUs and cooperating with other RSUs in distributing securable
or comfortable information.
2. Running securable applications, such as for vehicle-to-infrastructure warning like low
bridge warning, work-zone warning and act as information source.
3. Providing internet network connectivity to all OBUs for accessing comfortable,
securable and non securable applications.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-4-320.jpg)

![For More Info: Https://www.ThesisScientist.com
1. Vulnerable Individual Protection: It includes services like audio message for blind
person.
2. On Coming Traffic Warning: It helps the driver about overtaking maneuvers, by provide
information about in-coming traffic.
3. Traffic Signal Violation: RSU broadcast messages to warn vehicles about violation in
traffic signal.
4. Public Safety: Public safety applications are required if an accident has been physically
reported. It alerts the vehicles so that they can give a way to the emergency vehicle.
5. Electronic Brake Warning: It informs the driver that sudden braking is performed by a
preceding vehicle.
6. Post Crash Notification: Vehicle involved in accident alerts other approaching vehicles
by broadcasting warning messages.
7. Intersection Violation Warning: This Intersection violation warning application warns
drivers when they are going to pass over a red light.
1.4 Motivation
Traffic security is a major challenge granted by the major players in the automotive industry and
by many governments. Traffic delays continue to increase and wasting many hours . Apart from
traffic security and efficiency, features like entertainment, payment services, internet access and
information updates can be unified into vehicles to improve passenger convenience. Normally a
driver, has incomplete information about road conditions, speed and location of vehicles around
them, and is forced to make decisions like breaking and lane changing without the benefit of
whole data. Real time communication between vehicles and vehicles to RSU can improve traffic
efficiency and security [7]. For example, if a vehicle needs to slow down due to an accident
ahead, it will broadcast warning messages to neighbouring vehicles. The vehicles behind it will
thus be warned before they actually see the accident, helping the drivers react faster. In another ,
if vehicles can broadcast traffic congestion information to other vehicles in its broadcast range, it
can help variant vehicles catching the information to chose optional or alternate routes and avoid
traffic congestion.
Vehicular Ad hoc Networks (VANETs), subclass of mobile ad hoc networks (MANET) , were
developed with a view to enable real-time communication between mobile nodes (vehicles or](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-7-320.jpg)
![For More Info: Https://www.ThesisScientist.com
road side infrastructure) over wireless links, primarily with a view to enable traffic security and
efficiency. The communication between two or more nodes in a Vehicular Ad hoc Networks
(VANET) faces many unique challenges [8]. This is especially true for safety-critical
applications like lane change, pre-crash sensing, collision avoidance etc. Factors like traffic
density, high vehicle speeds, low signal latencies, total message size etc. induce challenges that
makes conventional wireless technologies and protocols unsuitable for Vehicular Ad hoc
Networks (VANETs).Apart from the performance challenges, there are many security issues
unique to VANET like authenticating message sender, verifying validity of message data,
providing node privacy with non-repudiation, certificate revocation, availability etc. All these
performance and security requirements contribute to make VANET securable applications.
1.5. Problem Statement:
There are many comparative studies and surveys that compare and improve AODV routing
protocol by many ways. This thesis has proposed a different approach to modify AODV and
compare its performance by many ways.
• To implement AODV with GA
• To increase the output by increasing the throughput, packet delivery ratio.
• To decrease the Packet loss.
• To decrease the end-to-end delay.
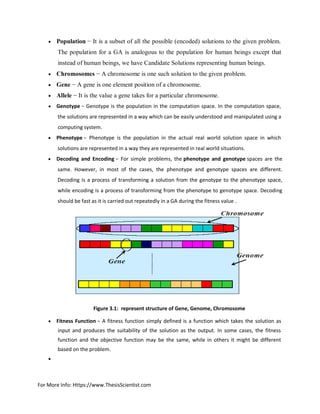
Genetic algorithm (GA) is a subclass of evolutionary algorithms (EA) which generate solutions
to optimization problems using techniques inspired by natural evolution such as selection,
crossover and mutation. The genetic algorithmic rules evaluate every chromosome to fitness
number n and then perform crossover and mutation to find optimal path.
1.6. Aims and objectives:
This thesis presents a new dynamic and adaptive G-AODV routing protocol for VANETs
inspired by the genetic algorithm in combination with network delay analysis. Genetic
Algorithms have been thoroughly investigated in the past for problems such as the
Travelling Salesman problem and even the routing problem in communication networks.
• The proposed G-AODV is compared with another ad hoc routing protocol such as Ad hoc
On-Demand Distance Vector (AODV) by evaluating the throughput, End-to-End delay in](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-8-320.jpg)

![For More Info: Https://www.ThesisScientist.com
Chapter 2
LITERATURE REVIEW
2.1 State of the Art
In recent years, various researchers have examined and compare various ad-hoc Routing
Protocols taking into consideration different performance metrics while basis for performance
evaluation. In this section describes the literature review of various research papers and journals
related to Vehicular Ad hoc Networks (VANET).
Ameur et al. [27]: In this paper authors present a systematic comparative study of three routing
protocols: DSDV, AOMDV and AODV in low, high and middle density regions. In their work,
authors was developed a road traffic scenario with taking 50 vehicle as low density ,100 for
middle density and 150 for high density region respectively. For the simulation purpose, authors
used NS-2.34 network simulator in LINUX platform and VanetMobiSim simulator for generated
road topology for simulations purposes. After the simulation result, authors conclude that in low
density region AODV and AOMDV score almost same range of packet delivery ratio whereas
DSDV packet delivery ratio was situated in between in range of 60-80.In the middle density
region the graph shows that AODV and AOMDV have packet delivery ratio lies between 90 to
100 ranges, whereas DSDV packet delivery ratio is in range of 60-80. And in high density region
the graph shows the AODV and AOMDV score same packer delivery ratio in range of 90-100,
whereas DSDV packet delivery ratio was degrades to 20-3
Amit N. Thakare et al. [10]: In this paper authors analyzed the performance of AODV and DSR
routing protocols using ns-2 simulator with Random Waypoint mobility model. After arriving
simulation results they resolve that packet loss of DSR is higher as equated to AODV and ratio
of packet received was higher for AODV as compared to the DSR routing protocol.
Artimy et al. [18]: in this paper authors try to make best use of DSRC channels by proposing a
cluster based multi channel communication scheme. In this scheme authors assumed that each
vehicles is equipped with two DSRC transceiver that can work on two different channel
simultaneously. In their work they divide time in to periods that can be repeated every T
millisecond. And each period is further divide into sub periods for exchange data.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-10-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Davesh et al. [12]: In this paper authors analyzed the performance of AODV and DSR routing
protocols using ns2 simulator with changing number of nodes. After getting simulation results
they conclude that AODV shows very high packet delivery ratio in 40 mobile nodes, simply
substantially decreases if the simulation node increases. DSR express less end to end delay as
equated to the AODV. Finally they concluded that AODV performs best because it allow for
almost identical result in all assumption and DSR suits for lower scalability networks in which
mobile nodes move at moderate speed.
Fan li. et al. [15]: Here authors provides a comprehensive and comparative survey that dealing
with all issues related to Vehicular Ad hoc Networks like its wireless access technologies and
standards, its characteristics , challenges ,security issues, its applications and various simulators.
In their work, authors present comprehensive and comparative study that focuses on the issues
surrounding VANET and its applications that help to tackle the all issues related to the VANET.
In this paper authors also briefly described the several network simulators like NS-2, MOVE,
Trans, VanetMobiSim, GloMoSim, NCTUns and QualNet.
Goel A. et al. [22]: In this paper authors investigate methods on how to propagate safety related
messages to accidental areas. They outline a scenario, in which an accident happened on a city
highway then how a safety message is propagated within one mile of the accidental area, for
telling to the other vehicles to slow down and take alternative route.
Gupta P. et al. [16]: In this paper authors compared and analyzed the performance of AODV
and DSR routing protocols using default random direction point mobility model. For
performance evaluation of considered protocols they used ns-2 simulator with varying pause
time. After arriving simulation results they conclude that DSR outperformed AODV in delay and
throughput on little number of nodes with lower load and mobility while AODV performed
better than DSR on big number of nodes with higher load and mobility. They also found that
DSR has low throughput and delay since of aggressive use of caching and stale routes.
Jerome Haerri et al. [3]: Here, authors evaluate and improve the performance of the AODV
and OLSR routing protocols under two topical and realistic mobility models for VANET. In their
work for the performance evaluation authors used the OMNET++ simulator .In this paper
authors design a convoy scenario that contains several parameters like 400km*400km simulation](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-11-320.jpg)
![For More Info: Https://www.ThesisScientist.com
area, 60 seconds simulating time, 500m communication range, 1440B packet size, 27m inter
vehicle distance and UDP transport protocol .The main objective of this function is improves the
communication performance of routing protocols by increasing the density around the receiver.
In their work authors also analyse the properties of the two mobility models in high density
urban fields. Finally after the simulation result authors conclude that the performance of AODV
is better than OLSR and OLSR routing protocol appear more affected by the density than
AODV, the reason behind is that proactive routing protocol maintains the full network topology
while reactive routing protocol create routes when they need.
Jorjeta G. et al. [32]: In this paper authors discussed several security related issues of mobile ad
hoc networks. In their work, authors described the black hole attack in mobile ad hoc networks
and proposed a feasible solution for it. Authors used the Global Mobile Simulator in this
proposed solution and found to achieve the required reliability and security with minimal
overhead and delay. In their work, authors used several performances metrics like routing
overhead, packet delivery ratio, average end to end delay to evaluate the performance of AODV.
To evaluate the packet delivery ratio authors take several parameters such as25 number of nodes,
5Minutes simulation time and 800m by 800m simulation area.
Thus, in recent years, several researchers have analyzed and compare various ad-hoc Routing
Protocols accepting into consideration different performance metrics as basis for performance
evaluation. They have used different simulators and simulation models as the same. In the next
section describes a conclusion of this chapter.
Kamble et al. [26]: Here Authors, proposed an AODV-R routing protocol that is improved
version of AODV routing protocol. In their work to achieve these objective authors developed a
link reliability model based on the vehicular velocity distribution on highways. In this papers
authors applying a hybrid approach combining both macroscopic and microscopic traffic flow
models is highway mobility model and also applying the link reliability model to improve the
performance of the current routing protocols in VANETs and incorporated vehicular reliability
model into the AODV routing protocol to create a new protocol named as AODV-R routing.
Authors compare both AODV and AODV-R. In their work for the performance comparison and
evaluation authors was taking four performance metrics such as Average packet delivery ratio,
link failures, and average end to end delay. After the simulation result authors found that AODV-](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-12-320.jpg)
![For More Info: Https://www.ThesisScientist.com
R shows higher average end to end values than AODV and route establishment in AODV-R
takes longer than that in AODV because of the processing of multiple routing request and
replies.
Manvi S. et al. [17]: In this paper authors analyse performance of two routing protocols AODV
and OLSR by using OPNET Modeler 14.5.In their work ,authors create a network scenario of 40
nodes with the comparison of network load media access delay and throughput to examine the
AODV and OLSR routing protocols with simulation parameters like 600*600 m campus area ,
40 nodes and 20 minutes simulation time .According to the authors simulation result OLSR
routing protocol shows low media access delay and low network load in comparison of AODV ,
with the overall performance OLSR is better than AODV but it is not necessary that OLSR is
always better than AODV.
Monika et al. [6]: In this paper authors analyzed the performance of AODV and DSR routing
protocols for Vehicular Ad-hoc network with and without RSU (Road Side Unit). For
performance evaluation of conceive protocols they used Estimate Simulator. After getting
simulation results they conclude that throughput was highest for AODV as compared to DSR
with varying number of nodes so AODV performed better than DSR. They also determined that
in presence of RSU whole performance of network was better as compared to absence of RSUs.
N.UMAPATHI et.al.[34]:Swarm Intelligence Based Dynamic Source Routing as Improved
Quality of Service. The OPNET simulation tool is used to evaluate the performance. When a
source node forwards a packet to a destination, it appears into its route cache to see if it already
has destination route. When it locates an unexpired way to the destinations, it uses it to forward
the packet. If the node lacks such a way, then way discovery is initiated by broadcasting a route
request. After simulation results shows that the improved performance of routing in the network.
Nzouonta J. et al. [23]: In this paper authors proposed a Road based vehicular traffic (RBVT)
routing which is a class of VANET routing protocols for the city based environments. In this
work ,authors described a road based vehicular traffic (RBVT) routing protocol that uses real
time vehicular traffic information to create road based paths between endpoints. And also authors
outline how to improve the end to end performance for the high contention areas by using the
distributed mechanism.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-13-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Prabha R et. Al.[36]: Here, authors evaluate an improved multipath MANET routing using link
estimation and swarm intelligence. For the performance evaluation author can take OPNET as an
simulation tool. It can be observed that link quality plays a very important role for obtaining
better QOS in multipath routing protocols. Routing being nondeterministic polynomial (NP)
hard, various meta-heuristic-based routing algorithms have also been proposed in literature using
swarm intelligence meta heuristic. Popular meta-heuristic algorithms including genetic algorithm
and particle swarm optimization (PSO) have shown to have drawbacks when the solution to be
found is multimodal. Simulation results indicate its better performances compared to other
methods.
Reza Fotohi et. Al.[37]:Here in this paper author Improvement over AODV Routing Protocol
by Limiting Visited Hop Count mechanism. For the performance evaluation author can take NS-
2 as an simulation tool.In this paper, an improved AODV routing protocol for mobile ad-hoc
networks. The work was accomplished by limited TTL (Time to Live) of RREP packet that the
route reply (RREP) packet of AODV is modified to limited TTL information of nodes, and
evaluated the four performance measures (i.e. PDR, throughput, good put and jitter with different
number of nodes). Then the performance of our work with regular AODV in one scenario with
20 to 80 nodes. After Simulation results author shows that the improved AODV protocol
provides better delivery ratio throughput and jitter over the normal AODV routing protocol the
proposed technique improve 20% of overall performance.
SangeetaKurundkaret. Al.[35]:Here, authors evaluate the Mobile Ad-hoc Network (MANETs)
are self-configurtion network of mobile nodes connected by wireless links. Self-configurability
and fast deployment feature of the MANET makes it most attractive choice for users. Routing in
such networks is a key issue which decides network performance. Ad Hoc On-Demand Distance
Vector (AODV) one of the widely used reactive routing algorithms. Energy consumption and
delay are the main concern for a number of researchers. Some of the battery powered nodes drain
out faster than others. Simulation results are observed for wireless network scenarios with
variation of node mobility, pause time, network area and packet sent rate. So finally authors
conclude that NS-2 simulator is used to compare performances of AODV and I-AODV.
Shastri A. et al. [14]: Here authors, reveals the performance analysis of reactive routing
protocols AODV, AOMDV and DSR. In their work, authors performed comparison with
proactive routing protocol DSDV. In this paper authors used NS-2.34 simulation tool for](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-14-320.jpg)
![For More Info: Https://www.ThesisScientist.com
simulation purpose with taking various parameters such as 200 second simulation time,
1000*1000 m simulation area and 100 bytes packet size, by using performance metrics such as
packet delivery ratio, average packet loss ratio and average end to end delay of packets are
investigated on the basis of vehicle velocity and vehicle density. According to the authors
simulation result, DSDV routing protocol shows the worst packet delivery ratio and AOMDV
and AODV have highest average end to end delays.
Sun Xi. et al. [4]: Here, authors evaluate the performance of AODV, ADV and DSR routing
protocols by taking some performance metrics such as packer drop ratio, throughput. In their
work, authors to use an open source simulator tool namely NCTUns-6.0.In this paper, authors
using three different mobility patterns for three Indian Metros cities: Kolkata, Chennai and
Mumbai. After the simulation result authors conclude that almost same performance of ADV and
AODV routing protocol for all different city scenarios, and DSR have less overhead than ADV
and AODV so DSR is not suitable for highly dynamic network.
Uma mani et al. [8]: Here authors examined the performance of AODV, DSR, and OLSR
routing protocol with different nodes density and the number of data traffic sources in order to
shows their advantages and limitations in the context of Vehicular Ad hoc Networks. In their
work, authors considered two propagation models, the first one is the Two Ray Groungand
second one is the adaption model. The first one assumes an unobstructed flat environment and
second one takes into account the terrain characteristics and define three terrain categories. For
the simulation purpose authors used Territories’ Mobile mobility model and NS-2.23 network
simulator. After the simulation result authors conclude that AODV routing protocol shows
higher end to end values.
Vidhale et al. [2]: Here, authors evaluate the MANET routing protocols in VANET environment
by using different mobility models available in VanetMobiSim. In their work, authors using
different simulation parameters such as number of nodes, packet size, simulation area and
performance metrics, average end to end delay, normalized routing load. After the simulation
result authors conclude that DSR has better packet delivery fraction (PDF) and lesser routing
overload than others. But in the case of end to end delay AOMDV protocol performed better
than others. Also it shows that reactive routing protocols performance degrading in space graph
model. So finally authors conclude that AOMDV is more appropriate than DSR in VANET.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-15-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Wang S. et al. [24]: Here, authors proposed a hybrid media access technique for cluster based
vehicular networks ,this technique is based on the scheduled based approach such as TDMA for
intra cluster based communications and management , and contention based approach for the
inter cluster based communications and management. In this scheme authors used a control
channel for delivering the safety and non safety application related messages to the nearby
clusters.
ZuhongFeng et.Al.[33]:Here in this paper author improved routing protocol Ad-AODV Based
on AODV. For the performance evaluation author can take NS-2 as an simulation tool. AODV
routing protocol only pays attention to the path that is the shortest without taking the energy and
load of the nodes. After simulation results, the Ad-AODV routing protocol improves the
efficiency of Ad Hoc network, and the packet delivery ratio, lowers the average end-to-end delay
and reduces the routing load. The packet delivery ratio of Ad-AODV and AODV in the different
residence time of the different number of nodes. The delivery rate of Ad-AODV is an average of
2.4% higher than AODV. In the case of the simulation of forty nodes, the delivery rate of Ad-
AODV is an average of 1.5% higher than AODV.
CHAPTER 3
BACKGROUND
3.1 GENETIC ALGORITHM
GA is a search technique that depends on the natural selection and genetics principles and which
determines a optimal solution for even a hard issue.
Genetic algorithms are normally a family of computational models which are motivated
by the biological evolution. These algorithms encode a powerful solution to a particular
problem on a simple chromosome i.e. data structure and use genetic operators to these
structures so as to preserve severe information.
Genetic algorithms are usually viewed as a function optimizer.
Genetic algorithms can be used to a broad range of problems.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-16-320.jpg)
![For More Info: Https://www.ThesisScientist.com
For solving the issue by genetic algorithm the first step is to generate the chromosomes
population (random). Then these chromosomes are estimated in such a manner that the
chromosome which shows a better solution for the problem will be provided more
opportunities than the poorer solution.
The genetic algorithms are part of the evolutionary algorithms family, which are
computational models, motivated in the Nature.
GAs are more reliable as compared to other most search techniques because they need only
information related to the quality of the solution created by every parameter set (objective
function values) and not like other optimization techniques which needs derivative information,
or worse yet, entire knowledge of the parameters and problem structure[9].There are some
difference between GA’s and other optimization/conventional searching algorithms [14] . They
are briefly explained as follows
1) GAs work with a coding of the parameter set, not the parameters themselves. Thus GAs can
easily manage the discrete or integer variables.
2) GAs search within a points population, not a single point. Thus GAs can offer a globally
optimal solution.
3) GAs employ only objective function information, not derivatives or other auxiliary
knowledge. Thus GAs can manage the non-continuous, non-smooth and non-differentiable
functions which are actually available in a practical optimization issue. 4) GAs employ
probabilistic transition rules, not deterministic rules, Although GAs appear to be a good
mechanism to solve optimization issue, sometimes the solution achieved from GAs is only a near
global optimal solution.
3.2 BASIC FEATURES OF GA
GA is a sub division of artificial intelligence.
AI (Artificial intelligence) is a computer science branch by which researchers implement
an intelligent computer system that has intelligence same as human being.
GA comes in the category of search algorithms that are based on computer and are
random in nature. These algorithms are obtained from the natural theory of “survival of
the fittest” being specified by Darwin.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-17-320.jpg)
![For More Info: Https://www.ThesisScientist.com
The mechanization of intelligent nature is a pre concern of this branch.
GA is also appropriate for complicated problems.
It generates the best of the best solutions.
The aim of GA is to increase the candidate solutions payoff in the population against an
objective function from problem domain. The scheme for the GA is to repeatedly use surrogates
for the mutation and recombination genetic processes on the population of candidate solutions,
where the objective function used to a decoded representation of a candidate governs the
probabilistic contributions a provided candidate solution can build the subsequent generation of
candidate solutions.
3.3 HISTORY OF GENETIC ALGORITHM
John Holland is assumed as the father of Genetic Algorithm. He discovered it in the early
1970's.and after that he and his students contribute much to the growth of this field. Holland
research was not concentrated on domain and optimization specific practical problem but was on
the adaptation concept as viewed in nature [6] and [7]. Other significant contributions were
performed by Frantz in 1972 who inquired what were known as Genetic Algorithm for Search
and in 1971 Holstein inquired genetic plans for adaptive control and function optimization.
Several people involved biologists, are amazed that life at the level of complexity that we realize
could have emerged in the relatively short time proposed by the fossil record [20].
Several human inventions were motivated by the natural selection. Genetic algorithm is one of
them. The main concept of this is the fittest survival or in other words it is called natural
selection. As evidently in nature the individual that has better chances for survival will survive
for a larger period of time. This in turn offers a better chance to create offspring with its genetic
material. In other words They can say that the fittest candidate will survive and unfit will not.
This force of nature is as known natural selection and on this principle GA operates for solving
optimization problems.
3.4BASICTERMINOLOGYofGA
Before beginning a discussion on Genetic Algorithms, it is essential to be familiar with some
basic terminology which will be used throughout this tutorial.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-18-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Figure 3.2: structure of Fitness Computation
Genetic Operators − These alter the genetic composition of the offspring. These include
crossover, mutation, selection, etc.
3.5 OPERATORS OF GA
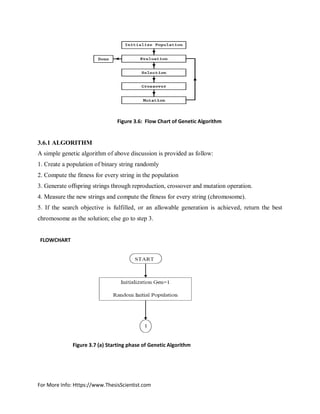
GA begins with random creation of initial population and then the selection, crossover and mutation
operations are conducted until best population is determined. Gas are practical and simple algorithm
and easy to be implemented in power system.
In other words, considering an initial random population generated and measured, genetic
evolution happens by means of three basic genetic operators [22].
1) Parent selection.
2) Crossover.
3) Mutation.
The descriptions of these genetic operators are provided below [23]:
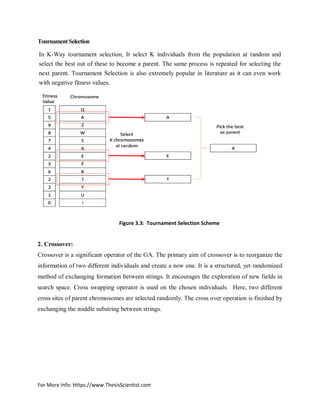
1. Parent Selection/Selection Strategy:
The selection of parents to generate successive generations plays a significant role in the GA.
This permits the fitter individuals to be chosen more usually to reproduce. There is a no. of
selection techniques introduced in the literature [24].
In this technique, n individuals are copied from the population randomly and the best of the n is
introduced into population for further genetic processing. This process is repeated until the
mating pool is filled.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-20-320.jpg)

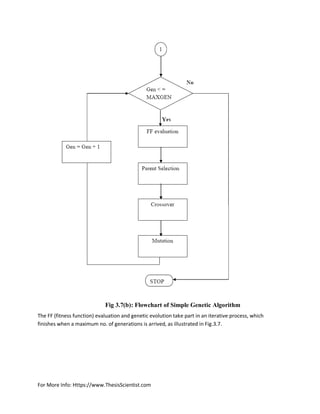
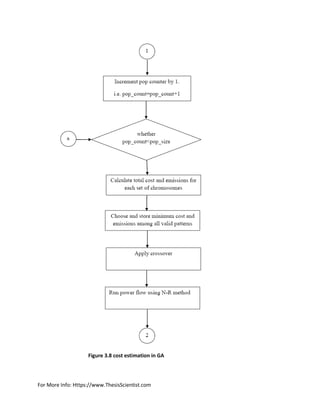
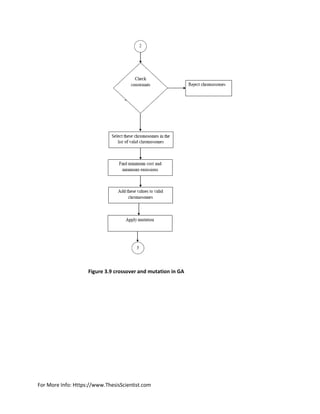
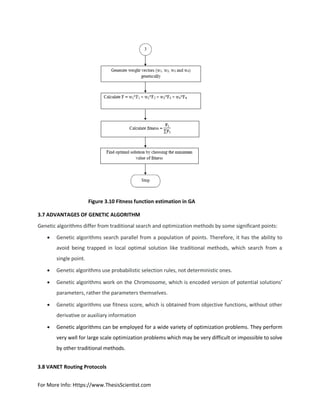
![For More Info: Https://www.ThesisScientist.com
Routing is a mechanism to establish and to select a specific path in order to send data from source to
destination [14, 16]. There are various routing algorithm designed for ad-hoc networks. Classification of
various VANET routing protocols can be divided in two broad categories: proactive or Table Driven
Routing Protocols (DSDV, OLSR, FSR) and reactive or On-demand routing protocols (AODV, DSR, TORA)
that shown in figure 3.11. In the next section describes a detail overview of various reactive routing
protocols (AODV, DSR).
Figure 3.11 VANET Routing Protocols
3.9 Reactive/On Demand Routing Protocols
Reactive routing protocols were designed to reduce the overheads by maintaining information for active
routes at each node [8]. This means that each node determined and maintained routes only when it
requires sending data to a particular destination. It using two main mechanisms for route establishment:
Route discovery and Route maintenance [17, 25]. Route discovery mechanism uses two messages:
Route Request (RREQ) and Route Reply (RREP).](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-28-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Figure 3.12: Route Request Propagation in Reactive Routing Protocols
The basic approach is when a node needs to send a message to a particular destination, it broadcasts
the RREQ message in the network that shown in figure 3.12 When RREQ message found a destination
node then destination node send a RREP message to source node that shown in figure 3.13.
Figure 3.13: Route Reply Propagation in Reactive Routing Protocols
Ad hoc On Demand Distance Vector (AODV): Ad hoc On Demand Distance Vector (AODV) is a pure
reactive routing protocol which is capable of both unicasting and multicasting. In Ad hoc On Demand
Distance Vector (AODV), like all reactive protocols, it works on demand basis when it is required by the
nodes within the network [8, 14]. When source node has to send some data to destination node then
initially it propagates Route Request (RREQ) message which is forwarded by intermediate nodes until
destination is reached. A route reply message is unicasted back to the source node if the receiver is
either the node using the requested address, or it has a valid route to the requested address that is
shown is figure 3.14.
(a) (b)
Figure 3.14: AODV Route Discovery Process. (a) Propagation of the RREQ.
(b) Path of the RREP to the source.
Working of Ad Hoc On Demand Distance Vector Routing (AODV): In this type of routing [14, 16] allows
the communication between two nodes via intermediated nodes, if those two nodes are not within the
range of each other. To establish a route between source to the destination, AODV using route discovery](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-29-320.jpg)
![For More Info: Https://www.ThesisScientist.com
phase, along which Route Request message (RREQ) messages are broadcasted to all its neighbouring
nodes. This phase makes sure that these routes do not forms any loops and find only the shortest
possible route to the destination node. It also uses destination sequence number for each route entry,
which ensures the loop free route, this is the one of the main benefit of AODV routing protocol. For
example if two different sources send two different requests to a same destination node, then a
requesting node selects the one with greatest sequence number. In the route discovery phase several
control messages are defined in AODV that are defined as follows.
a) RREQ (Route Request): When any node wants to communicate with other node then it
broadcast route request message (RREQ) to its neighbouring nodes [14, 16]. This message is
forwarded by all intermediate nodes until destination is reached. The route request messages
(RREQ) contains the some information such as RREQ id or broadcast id, source and destination
IP address, source and destination sequence number and a counter.
b) RREP (Route Reply): When any intermediate nodes received Route Request (RREQ) message
then it unicast the route reply message (RREP) to source node either it is valid destination or it
has path to destination and reverse path is constructed between source and destination [14,
16]. Each route reply message (RREP) packet consist of some information such as hop count,
destination sequence number, source and destination IP address.
c) RERR (Route Error): Whenever there is any link failure arises in the routing process then route
error message (RERR) is used for link failure notifications. The route error message (RERR)
consist of some information such as Unreachable Destination node IP Address, Unreachable
Destination node Sequence Number.
Routing in AODV: There are various mechanisms which are followed in AODV routing approach:
a) AODV Route Discovery phase: To establish a route between source node to the destination
node, AODV using route discovery phase, along which the Route Request message (RREQ)
messages are broadcasted to all its neighbouring nodes [14]. This phase makes sure that these
routes do not forms any loops and find only the shortest possible path to the destination node.
It also uses destination sequence number for each route entry that ensures the loop free route,
this is the one of the main benefit of AODV routing protocol. For example if two different
sources sends two different request to a same destination node, then a destination node selects
only that node having largest sequence number. In the route discovery phase several control
messages are defined in AODV protocol.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-30-320.jpg)
![For More Info: Https://www.ThesisScientist.com
b) AODV Route Table Management: In AODV, Routing table management is required to avoid
those entities of nodes that do not exist or having invalid route from source to destination. The
need for routing table management is important to make communication loop free. It consists
of following characteristics to maintain the route table for each node.
• Destination IP address
• Total number of hops to the destination
• Destination sequence numbers
• Number of active neighbours
• Route expiration time
c) AODV Route Maintenance: In AODV, when any node in the network detects that a route is not
valid anymore for communication it delete all the related entries from the routing table .And it
sends the Route reply message (RREP) to all current active neighbouring nodes to inform that
the route is not valid anymore for communication purpose.
Dynamic Source Routing Protocol (DSR)
Dynamic Source Routing is a reactive routing protocol that is based on the concept of source routing [8,
16]. Source routing means source has the complete knowledge of entire route to the destination before
transmitting data. In DSR each node maintains a route cache where it records all possible learned
routes. It using two main mechanisms: Route discovery and Route maintenance.
Route Discovery: Whenever a source node wants to send a data packet to destination node in the
network, it first looks in its Route Cache to find a valid hop sequence to the destination [1].
Figure 3.15: Route Request Propagation in DSR](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-31-320.jpg)
![For More Info: Https://www.ThesisScientist.com
If such a route exists, the source node attaches to the packet header the complete route to the
destination and forwards the packet to the next node. The next node checks the packet header and
forwards the packet to the next node. The process terminates when the packet reaches the destination.
If the source node cannot find a valid hop sequence to the destination in its Route Cache then it initiates
a route discovery process [17].
In route discovery process a route request (RREQ) message is broadcasts to all its neighbouring nodes,
adding a unique request ID to each request to prevent
Figure 3.16: Route Reply Propagation in DSR
Figure 3.15 shows the RREQ message propagation in the network. And figure 3.16 shows the
propagation of RREP message that carries the entire hop sequence.
a) Route Maintenance: Route Maintenance is done by the propagation of route error message
(RERR). Whenever any active node sees or detects the link failure, it propagates the route error
message to its upstream neighbours along the reverse path till it reaches the source node. To
verify the correct operation of the router links, HELLO messages and acknowledgement
messages can be used.
3.10 Classification of the VANET Applications:
The applications of Vehicular Ad hoc Networks (VANET) are classified into three major groups:
1)comfort oriented applications 2) convenience-oriented applications and 3)safety oriented applications
[11]. Safety oriented related applications look for the increasing security of passengers by exchanging
relevant information through vehicle-to-infrastructure and vehicle-to-vehicle. And comfort and
convenience applications improve passenger’s comfort and traffic efficiency.
3.10.1 Safety-Oriented Applications: These types of applications help the driver to avoid potential
dangers through the exchange of information among vehicles. They are the important applications
because they serve to avoid accidents [11].](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-32-320.jpg)
![For More Info: Https://www.ThesisScientist.com
Figure 3.17: Safety Applications provided by VANET
They can take control of the vehicle in case of hazardous conditions, as in the case of the automatic
braking and only send warning/emergency messages to drivers. Some safety oriented application shown
in Table 3.1[11].
Table 3.1: Examples of Safety-Oriented Applications
Name Description
Intersection violation warning Intersection violation warns drivers when they are going to
pass over a traffic red light .
On-coming traffic warning It assists the driver during over taking manoeuvres
Electronic brake warning It alerts to the driver that a preceding vehicle has performed
a emergent braking.
Vehicle stability warning It reports drivers that they should activate the vehicle stability
control system.
Post-crash notification A vehicle involved in an accident sends warning /emergency
messages in broadcast to approaching vehicles.
Traffic signal violation warning A roadside unit (RSU) sends messages in broadcast to warn
drivers of potential violations of traffic signals.
Lane change warning It assists drivers to perform a safe lane change
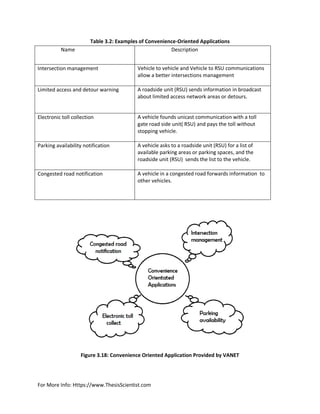
3.10.2 Convenience-Oriented Applications: These types of applications improve the efficiency of the
roads and to save drivers time . Various Convenience oriented application shown in Table 3.2[11]. Some
examples of Convenience Oriented Applications in VANET as shown in table 3.2.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-33-320.jpg)
![For More Info: Https://www.ThesisScientist.com
3.10.3 Commercial-Oriented Applications: These types of applications serve to make the travelling
more comfortable for example, by means of the internet connection. Few Commercial oriented
application shown in Table 3.3[11].
Table 3.3: Examples of Commercial-Oriented Applications
Name Description
Remote diagnosis The vehicle driver can start a wireless connection with the
dealer to upload the vehicle diagnostics information to identify
the possible problems.
Media or map download A vehicle can start a wireless connection with the hot-spot
network and home network to download multimedia contents
and location map.
Service announcement Restaurants and other businesses can use a roadside unit(RSU)
to send promotional messages to the drivers that are in their
communication range.
REFERENCES
[1] Abedi Berangi and R.; Azgomi, M. A., "Improving Route Stability and Overhead on
AODV Routing Protocol and Make it Usable for VANET," In Proceedings of 29th IEEE
International Conference on Vehicular Ad hoc Networks, June 2009, pp.464-467.
[2] Ameur Bennaoul, Mustapha Guezouri and Mokhtar Keche,” Performance Evaluation of
Routing protocols in Vehicular Networks” International Journal of Computer Network and
Information Security,2013,pp. 11-16.
[3] Amit Kumar Saha and David B. Johnson, “Modeling mobility for Vehicular Ad-hoc
Networks”Tthe first ACM workshop on Vehicular Ad hoc Networks, Philadelphia, PA, USA,
Oct. 2004, pp. 22-34.
[4] Amit N. Thakare, Mrs. M. Y. Joshi, “Performance Analysis of AODV & DSR Routing
Protocols in Mobile Ad hoc Networks”,Indian Journal of Computer Application, Special Issues,
2010, pp. 231-240.
[5] Artimy M.M., W. Robertson, and W. J. Phillips. “Connectivity in inter-vehicle ad
hoc networks”.Engineering Canadian Conference on Electrical and Computer, Volume: 1, May
2004, pp. 100-112.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-35-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[6] Balon N., and J. Guo, “Increasing Broadcast Reliability in Vehicular Ad hoc
Networks(VANET),” In Proceeding of the 3rd ACM International Workshop on Vehicular Ad
hoc Networks VANET, NY,USA,2006, pp. 104-105.
[7] Bernsen, J. Manivannan, “Routing Protocols for Vehicular Ad hoc Networks That Ensure
Quality of Service” In Proceedings of the fourth international conference on Wireless and
Mobile Communications, Aug. 2008, pp.1-6.
[8] Blum J., Eskandarian A., and HoffmanL. "Performance Characteristics of Inter- Vehicle Ad
Hoc Networks". In Proceedings of IEEE 6th International Conference on Intelligent
Transportation Systems, Shanghai, China, 2004, Pp. 115-119.
[9] Brian D. Noble, Jungkeun Yoon ,Mingyan Liu, Minkyong Kim, ”Building realistic mobility
models in VANET”, In Proceeding of the ACM International Conference On Mobile Systems,
Applications And Services,2006, pp. 177-190.
[10] Chen Y. S., Y. W. Lin, and S. L. Lee, “A mobicast routing protocol for Vehicular Ad hoc
Networks,” ACM/Springer Mobile Networks and Applications, Vol. 15, 2010, pp. 20-35.
[11] Davesh Singh and Dhananjaya Singh,“Performance Analysis and Simulation of AODV,
DSR and TORA Routing Protocols in MANETs” International Journal of Recent Technology
and Engineering (IJRTE), Vol. 1, Issue-3, August 2012, pp. 218-224.
[12] Chowdhury S.I., Won-Il Lee, Youn-Sang Choi, and Guen-Young Kee "Performance
evaluation of reactive routing protocols in VANET,"Communications (APCC), 2011 17th Asia-
Pacific Conference on Vehicular Ad hoc Networks ,2011, pp.559-564.
[13] David B. Johnson, David A. Maltz, and Josh Broch, “The Dynamic Source Routing
Protocol for Multi-Hop Wireless Ad Hoc Networks”, In Ad Hoc Networking, Editor: Charles E.
Perkins, Addison-Wesley, Chapter 5, 2001 , pp. 139-172.
[14] Dirk Reichardt, Maurizio Miglietta, and Wolfgang Schulz “CARTALK 2000 Safe and
Comfortable Driving Based Inter-Vehicle-Communication in VANET”, In proceedings of IEEE
Intelligent Vehicle Symposium, June 2002, pp.145-147.
[15] Fan Li and Yu Wang; “Survey of Routing in Vehicular Ad hoc Networks”, In Proceedings
of IEEE Vehicular Technology Magazine, Volume 2, Issue 2, June 2007; pp. 12-22.
[16] Goel A., Ramakrishnan K. G., D. Kataria, and D. Logothetis, “Efficient computation of
delay-sensitive routes from one source to all destinations,” In Proceedings of IEEE Conference
on Computer Communications, 2001, pp. 854-858.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-36-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[17] Heissenbüttel M., T. Braun, M. Wälchli, and T. Bernoulli, “Optimized stateless
broadcasting in wireless multi-hop networks,” In proceeding of 4th
IEEE international conference
on Infocom Barcelona,2006,pp.234-240.
[18] H.P. Glathe, L. Karlsson, G.P. Brusaglino, L. Calandrino, “The PROMETHEUS
Programme– Objectives, Concepts and Technology for Future Road Traffic”, In Proceedings
of12th
conference of networking, May 1990, pp. 477-484.
[19] H. Safa, H. Artail, and R. Shibli, “An Interoperability model for supporting reliability and
power-efficient routing in mobile ad hoc network,” International Journal of Ad Hoc and
Ubiquitous Computing, Vol. 4, 2009, pp. 74-83.
[20] H. Wu, Fujimoto, R., Guensler, R., and Hunter, M, “MDDV: a mobility-centric data
dissemination algorithm for vehicular network,” The 1st ACM international Workshop on
Vehicular Ad hoc Networks, October, 2004, pp. 47-56.
[21] Jahanzeb Farooq and Bilal Rauf “ Implementation and Evaluation of IEEE 802.11e
Wireless LAN in GloMoSim” In Proceeding of the 1st ACM International Workshop on
Vehicular Ad hoc Networks, NY, USA, 2004,pp. 76-85.
[22] Jerome Haerri “Performance Comparison of AODV and OLSR in VANETs Urban
Environments under Realistic Mobility Patterns” Department of Mobile Communications, June
2005, pp. 123-134.
[23] Jorjeta G. Jetcheva, Yih-Chun Hu, Amit Kumar Saha, and David B. Johnson. “Design and
Evaluation of a Metropolitan Area Multitier Wireless Ad Hoc Network Architecture in
VANET”. In Proceedings of the Fifth IEEE Workshop on Mobile Computing Systems &
Applications, Monterey, CA, Oct. 2003,pp 32-37.
[24] kamble P.A. and M.M. Kshirsagar, “ Improvement over AODV Routing Protocol in
VANET” International Journal of Computer Engineering & Technology, Vol. 4, Issue 4, July
2013, pp. 315-320.
[25] Korkmaz G., E. Ekici, F. Ozgüner, and U. Ozgüner, "Urban multi-hop broadcast protocol
for inter-vehicle communication systems in VANET," In Proceeding of the 1st ACM
International Workshop on Vehicular Ad hoc Networks, NY, USA, 2004,pp. 76-85.
[26] Manoharan R. and S. L. P. Thambidurai, “Energy efficient robust on-demand multicast
routing protocol for mobile ad hoc network,” International Journal of Ad Hoc and Ubiquitous
Computing, Vol. 3, 2008, pp. 90-98.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-37-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[27] Manvi S., Kakkasageri M.S. and Mahapurush , “Performance Analysis of AODV, DSR,
Routing Protocols In Vehicular Ad hoc Network Environment”International conference on future
Computer and Communication., April. 2009, pp. 21-26.
[28] Monika, Sanjay Batish and Amardeep Dhiman, “Comparative Study of AODV, DSDV and
DSR Routing Protocols in vehicular Network Using EstiNet Simulator”, International Journal of
Scientific & Engineering Research , Vol. 3, Issue 6, June 2012.
[29] N.UMAPATHI and N.RAMARAJ, “swarm intelligence based dynamic source routing for
improved quality of service”. In Proceedings of Journal of Theoretical and Applied Information
Technology, Vol.61, 2014, pp.604-608
[30] Nzouonta, J., Rajgure, N., Guiling Wang and Borcea, C., "VANET Routing on City Roads
Using Real-Time Vehicular Traffic Information," In proceeding of Vehicular Technology, IEEE
Transactions on on Vehicular Ad hoc Networks, vol.58, no.7, 2011,pp.3609-3626.
[31] Nzouonta J. R., Guiling N. and Wang Borcea C., “VANET Routing on City Roads Using
Real-Time Vehicular Traffic Information,” In Proceedings of Vehicular Technology, IEEE
Transactions on Vol. 58, Issue. 7, Sept. 2009, pp. 33-37.
[32] Pooja Gupta and Rajesh Kumar Tyagi” A significant study and comparison of DSDV,
AODV and DSR protocols in MANET using NS-2” In Proceeding of International Journal of
Engineering Research and technology, Vol. 2, Issue 3, 2013, pp. 1-8.
[33] Prem Chand and Deepak Kumar” Performance comparison of two on-demand routing
protocols for mobile ad-hoc networks” International journal of Advances in Engineering and
technology,2011, pp. 283-289.
[34] Rajive Bagrodia, Richard Meyer, Mineo Takai, Yu an Chen, Xiang Zeng, Jay Martin, and
Ha Yoon Song. “A parallel simulation environment for complex systems” In Proceedings of the
1st ACM international workshop on Vehicular Ad hoc Networks, 2004, pp. 66 – 75.
[35] Reza Fotohi and Shahram Jamali and Fateme Sarkohaki and Shahram Behzad, “An
Improvement over AODV Routing Protocol by Limiting Visited Hop Count”, In Proceedings of
I.J. Information Technology and Computer Science,Vol.09, 2013, pp.87-93
[36] Robert E. Chandler, Robert Herman, Elliott W. Montroll, ”Traffic Dynamics: Studies in Car
Following”, Operations Research, Vol. 6, 2004, pp. 165-184.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-38-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[50] Robert E. Chandler, Robert Herman, Elliott W. Montroll, ”Traffic Dynamics: Studies in Car
Following”, In proceeding of 4th
IEEE International Conference on Infocom, Barcelona, 2006,
pp.234-240.
[37] Sangeeta Kurundkar and Apoorva Maidamwar, “An improved AODV routing protocol for
mobile ad-hoc networks”. International Journal of Advanced Research in Electrical, Electronics
and Instrumentation Engineering, Vol.2, 2013, pp.3003-3008
[38] Prabha R and Ramaraj N, “An improved multipath MANET routing using link estimation
and swarm intelligence”. R. and N. EURASIP Journal on Wireless Communications and
Networking, 2015, pp.2-9
[39] Saha A. K. and Johnson D.B., “Modeling the mobility for Vehicular Ad hoc
Networks(VANET),”The ACM International Workshop on Vehicular Ad hoc Networks,2004,
pp. 91-96.
[40] Shastri A., R. Dadhich and Ramesh C. Poonia” Performance analysis of on-demand routing
protocols for Vehicular Ad hoc Networks” International Journal of wireless and mobile
networks, Vol. 3,2011, pp. 103-109.
[41] Sherali Zeadally, Ray hunt and Yuh Shayan Chan, “Vehicular Ad hoc Networks
(VANETs): Status, Results and Challenges” Springer Science, Dec. 2011, pp. 217-241.
[42] Skordylis A. and Trigoni N., “Delay-bounded routing in vehicular ad-hoc networks
(VANET),” ACM International Symposium on Mobile Ad hoc Networking and Computing,
2008, pp. 3020-3026.
[43] Sommer, C.; Dietrich, I.; Dressler, F. “Realistic Simulation of Network Protocols in
VANET Scenarios” International Journal of Ad Hoc and Ubiquitous Computing, Vol. 3, 2008,
pp. 217-223.
[44] Sun Xi and Xia-Miao Li, "Study of the Feasibility of VANET and its Routing
Protocols," Wireless Communications, Networking and Mobile Computing, 2008. 4th
International Conference on Vehicular Ad hoc Networks, 2008, pp.1-4.
[45] T. Taleb, E. Sakhaee, K. Hashimoto, N. Kato, and Y. Nemoto, “A stable routing protocol to
support ITS services in VANET networks,” In Proceedings of IEEE Transactions on Vehicular
Technology, Vol. 56, 2007, pp. 3337-3347.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-39-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[46] Taleb T., E. Sakhaee, A. Jamalipour, K. Hashimoto, N. Kato, and Y. Nemoto, “A stable
routing protocol to support its services in VANET” In Proceedings of IEEE Transactions on
Vehicular Technology, vol. 56, no. 6, November 2007, pp.3337–3347.
[47] Tonguz, F. Bai and P. Mudalige, “Broadcasting in VANET,” In Proceedings of IEEE
Mobile Networking for Vehicular Environments, 2007, pp. 7-12.
[48] T. Sawamura, K. Tanaka, M. Atajanov, N. Matsumoto, and N. Yoshida, “Adaptive router
promotion and group forming in ad-hoc networks,” International Journal of Ad Hoc and
Ubiquitous Computing, Vol. 3, 2008, pp. 217-223.
[49] Tsugawa, S.; Kato, S.; Tokuda, K.; Matsui, T.; Fujii, H., “A cooperative driving system with
automated vehicles and inter-vehicle communications in Demo 2000”, In proceedings of IEEE
Intelligent Transportation Systems,2006, pp.178-189.
[50] Tseng Y.C., Y.S. Chen, and J.P. Sheu, "The broadcast storm problem in a mobile ad hoc
network(MANET)," In Proceeding of the 5th ACM/IEEE International Conference on Mobile
Computing and Networking, NY, USA, 1999, pp. 51-162.
[51] Uma mani, Ramasamy Chandrasekaran and V. R Sharma” Study and analysis of routing
protocols in mobile ad hoc networks” Journals of Computer science, 2013, pp. 1519-1525.
[52] Vidhale, B. and Dorle S.S., "Performance Analysis of Routing Protocols in Realistic
Environment for Vehicular Ad hoc Networks," Systems Engineering (ICSEng), 2011 21st
International Conference on , vol.2, Aug. 2011, pp.267-272.
[53] Vinod Namboodiri, Manish Agarwal and Lixin Gao; “A Study on the Feasibility of Mobile
Gateways for Vehicular Ad-hoc Networks (VANET)”,Wireless Communications Networking
and Mobile Computing 6th International Conference on 2010,Sept. 2010, pp. 23-25.
[54] Wang S. Y. “Predicting the lifetime of repairable unicast routing paths in vehicle formed
mobile ad hoc networks on highways” In Proceedings of 15th IEEE International Symposium on
Personal, Indoor and Mobile Radio Communications, Volume: 4, Sept. 2005, pp. 2815-2819.
[55] Wan S., Tang J., and Wolff R. “Reliable routing for roadside to vehicle communications in
rural areas,” In Proceedings of the IEEE International Conference on Communications, 2008, pp.
3017-3028.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-40-320.jpg)
![For More Info: Https://www.ThesisScientist.com
[56] Yamaguchi H., K. Yukimasa, and S. Kusumoto, “QoS routing Protocol for Vehicular Ad
hoc Networks,” In Proceedings of IEEE International Workshop on Quality of Service, 2006, pp.
132-139.
[57] Yang X., L. Liu, N.H. Vaidya, and F. Zhao, "A vehicle-to-vehicle communication protocol
for cooperative collision warning in VANET," In Proceedings of the 1st International
Conference on Networking and Services,2004, pp.114-123.
[58] Yue Liu, Jun Bi and Ju Yang;, “Research on Vehicular Ad hoc Networks” Chinese Control
and Decision Conference (CCDC), 2009, pp. 4430 – 4435.
[59] Zhao J. C. and Josh Broch “Vehicle-Assisted Data Delivery in Vehicular Ad hoc Networks”
In Proceedings of 25th IEEE International Conference on Computer Communications.
Proceedings, April 2006, pp. 6-12.](https://image.slidesharecdn.com/vanetthesisreportthesisscientist-170507081446/85/Aodv-routing-protocol-implementation-design-41-320.jpg)