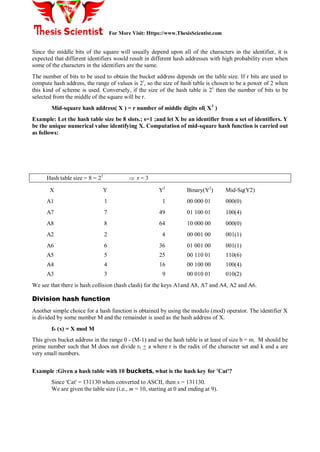
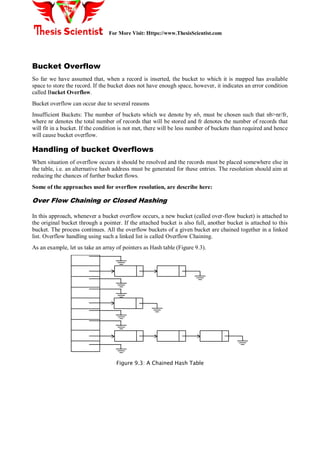
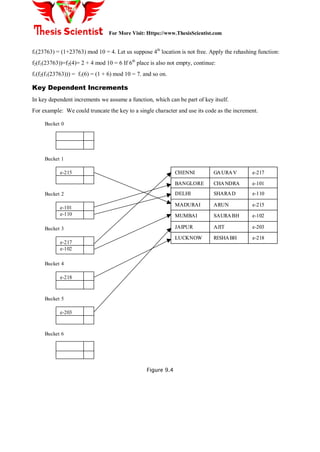
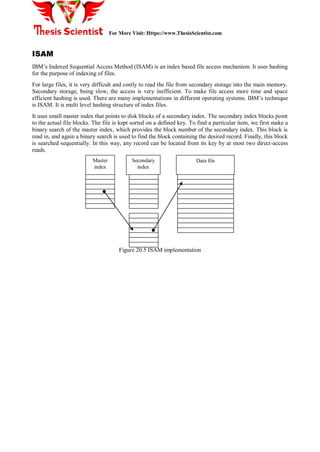
The document discusses hash tables, which are used to maintain a symbol table in memory, explaining concepts like buckets, hash functions, collisions, and how to manage overflow. Various types of hash functions, such as mid-square, division, and folding methods are described, along with techniques for collision resolution such as chaining and rehashing. It concludes with a brief overview of IBM's Indexed Sequential Access Method (ISAM) that employs hashing for efficient file access.