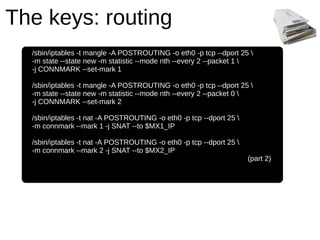
The document discusses using Linux, Postfix, and Ruby on Rails for effective mass emailing, highlighting issues with emails being marked as spam and ways to improve deliverability. It covers both non-technical and technical solutions such as refining content, personalizing emails, email authentication techniques (SPF, Sender ID, DKIM), and managing sending limits. Recommendations for managing user subscriptions and sending flows are also provided to maintain email reputation.

















![The keys: ar_mailer
►Change application ActionMailer's delivery method
environment.rb
ActionMailer::Base.delivery_method = :activerecord
►If you don't have one, create a mailer class
class Newsletter < ActionMailer::ARMailer
end
►If you already had one, simply replace
# class Alerts < ActionMailer::Base
class Alerts < ActionMailer::ARMailer
[...]
end](https://image.slidesharecdn.com/massiveemailer-091120062912-phpapp02/85/Massive-emailing-with-Linux-Postfix-and-Ruby-on-Rails-19-320.jpg)