This document provides an overview of effective anti-spam techniques utilized to combat unsolicited emails, describing various measures such as sender authentication protocols including SPF and DKIM, and analyzing the structure of email messages. It categorizes anti-spam strategies into four broad types based on the needs and actions of individuals, email administrators, senders, and researchers. The document highlights the challenges of preventing spam while maintaining email functionality, addressing issues like false positives and negatives in spam detection.



![Figure 1: Email Architecture
Spam filters can be implemented at all layers, firewalls exist in front of email server or at
MTA(Mail Transfer Agent), Email Server to provide an integrated Anti-Spam and Anti-Virus
solution offering complete email protection at the network perimeter level, before unwanted or po-
tentially dangerous email reaches the network. At MDA (Mail Delivery Agent) level also spam
filters can be installed as a service to all of their customers. At Email client user can have per-
sonalized spam filters that then automatically filter mail according to the chosen criteria. Figure 1
shows the typical architecture of email.
1.2 Sender Authentication Protocols
Today, the most abusive e-mail messages carry fake sender addresses. The victims whose addresses
are being abused often suffer from the consequences, because their reputation gets diminished. For
instance, when a person received an error message saying that a message allegedly sent by him/her
could not be delivered to the recipient, although he/she never sent a message to that address.
Sender address forgery is a threat to users and companies similarly, and it even undermines the
e-mail medium as a whole because it erodes people’s confidence in its reliability.
There are different e-mail authentication protocols [1]. Mainly, they differ in which addresses
(identities) they authenticate and how they do it. In order to understand how the various protocols
work, firstly it’s better to understand the various parts of which e-mail messages are made. The
Figure 2 shows a message: it has an envelope that represents the SMTP transaction, a header, and
a body which contains the actual text of the message other possible attachments.
Sender authentication protocols are designed to protect against forgery of e-mail sender identities,
either in the envelope or in the header.
In the envelope, there are three identities:
• The ”HELO” identity, which names the mail server (MTA) that is sending the message.
• The ”MAIL FROM” identity that is the e-mail address that is responsible for sending the
message and where delivery errors (bounces) will eventually be reported.
• The ”RCPT TO” identity that is the message’s recipient address.
4](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-4-320.jpg)
![Figure 2: Email Structure
These envelope identities are used during the transport of the message and they are discarded upon
delivery, except the MAIL FROM that is usually retained in the message header as Return-Path.
The typical symptom of forged envelope sender identities are misdirected bounces.
The header contains another set of identities that can be other meta information about the message,
such as the subject and the sending date.
• The ”From” identity denotes the address of the message’s author.
• The ”Sender” identity is listed explicitly only if the author is not the actual sender of the
message.
• The ”To” identity is again the recipient address.
The header identities are irrelevant for message delivery and since they are what is displayed by mail
clients, are solely significant for the use by the message’s recipient. When the header sender address
is forged, the recipient’s mail client will display a misleading sender address and the recipient will
thus be deceived about the message’s real origin.
1.3 Sender Policy Framework
The Sender Policy Framework (SPF) [1] [2] [3] is an open standard specifying a technical method
to prevent sender address forgery. SPF has a long history reaching back to mid-2003 when the
first stable SPF draft was released. In April 2014 IETF publish SPF in RFC 7208 as ”proposed
standard” after a previous standard release publish in RFC 4408 in 2006.
The current version of SPF - called SPFv1 or SPF Classic - protects the envelope sender address,
which is used for the delivery of messages. Therefore SPFv1 allows the owner of a domain to specify
their mail sending policy, that is which mail servers they use to send mail from their domain. The
technology requires two sides to play together:
1. The domain owner publishes this information in an SPF record in the domain’s DNS zone,
and when someone else’s mail server receives a message claiming to come from that domain,
then
5](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-5-320.jpg)








![1.4.3 Security Considerations
This part describes some attacks that could be used to defeat this mechanism.
• DNS Attacks: Sende ID depends on DNS lookups, and is therefore only as secure as DNS.
An attacker that want to spoof messages could attempt to get his messages accepted by
sending forged answers to DNS queries. DNS Security (DNSSEC) may ultimately provide a
way to completely neutralize this class of attacks.
• TCP Attacks: This mechanism usually is used in combination with SMTP over TCP. A
attacker that has a lot of resources might be able to send TCP packets with forged from-
addresses, and thus execute an entire SMTP session. Then, it appears to come from some-
where other than its true origin. Such an attack requires guessing what TCP sequence
numbers an SMTP server will use. This type of attack can be ameliorated if IP gateways
refuse to forward packets when the source address is clearly fake.
• Forged Sender Attacks: This mechanism chooses an address for instance from one of a
number of message headers, and then uses that address for validation. A message with a true
Resent-From header or Return-Path, but a forged From header, will be accepted. Since many
MUAs do not display all of the headers of received messages, the message will appear to be
forged when displayed. In order to neutralize this attack, MUAs will need to start displaying
at least the address that was verified.
Today Sender ID is little used. Even Microsoft has migrated away from using Sender ID.
1.5 Content Authentication Protocols
The above authentication protocols refer to the sender. Content (or payload) authentication pro-
tocols do not care about who is the sender of a message but only about who is its author. They
authenticate the author of the message content (body) through asymmetric cryptographic methods.
The cryptographic processing is CPU intensive, and, like in sender authentication protocols that
work on header identities, it requires that the entire message has to be received before that its
validity can be decided and subsequently action can be taken.
The concept of DKIM that we will se below is a hybrid of sender authentication and content
authentication.
1.6 DomainKeys Identified Mail (DKIM)
DomainKeys Identified Mail (DKIM) is an email authentication method designed to detect email
spoofing[10] [11] [12]. It allows an organization to claim responsibility for transmitting a message,
in a way that can be validated by a recipient. It is intended to prevent forged sender addresses in
emails, a technique often used in phishing and email spam.
DKIM resulted in 2004 from merging two similar efforts, ”enhanced DomainKeys” from Yahoo and
”Identified Internet Mail” from Cisco. Source code development of one common library is led by
the OpenDKIM Project.
DKIM provides for two distinct operations, signing and verifying. Either of them can be handled
by a module of a mail transfer agent (MTA). In order to refer to the identity of a responsible
person or organization DKIM uses a domain name as an identifier, it is called the Signing Domain
IDentifier (SDID) and is contained in the DKIM-Signature header fields ”d=” tag.
Therefore, given the presence of that identifier, a receiver can make decisions about further handling
14](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-14-320.jpg)



![considerable computing resources to verify the signature. Verifiers might avoid this attack
by refusing to verify signatures that reference selectors with public keys having unreasonable
exponents.
1.7 Author Domain Signing Practices (ADSP)
Author Domain Signing Practices (ADSP) [13] [14] is an optional extension to the DKIM E-mail
authentication scheme, whereby a domain can publish the signing practices it adopts when relaying
mail on behalf of associated authors. An ”Author Domain Signature” is a Valid Signature in which
the domain name of the DKIM signing entity, i.e., the d= tag in the DKIM-Signature header field,
is the same as the domain name in the Author Address.
There are currently is a total of three different outbound signing practices that can be set:
• all - All mail from the domain is signed with an Author Domain Signature.
• discardable - All mail from the domain is signed with an Author Domain Signature. Further-
more, if such signature is missing or invalid, the domain owners want the receiving server to
drop the message.
• unknown - The domain might sign some or all email.
Any other value than ”all” or ”discardable” is treated as ”unknown”. If we use the term ”all” or
”discardable” that means all the email that we send in the from field with ”user@domain.com”
originates from our mail servers. The main difference between ”all” and ”discardable” is that ”all”
should to be treated suspiciously (given a higher spam score) by the recieving MTA Email Server,
if the email is not signed by the users domain.
1.7.1 How set up ADSP Policy
First, we need to set up your DKIM. Next, we will need to publish a DNS TXT resouce record
type for our domain in this format.
adsp. domainkey. < sub > .domain.example
If our domain email has sub domain emails we will simply replace the < sub >.
For example ”user@blogs.domain.com” would have a key that looks like this:
adsp. domainkey.blogs.domain.com
But, most commonly, most domain owners have emails like ”users@domain.com” and that will look
like this.
adsp. domainkey.domain.com
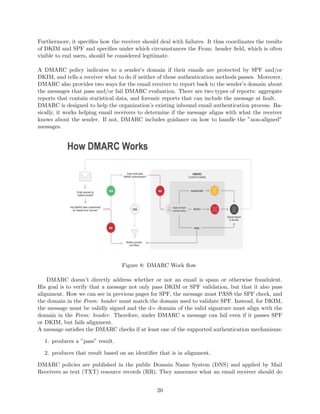
1.8 Domain-based Message Authentication, Reporting & Conformance (DMARC)
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email-validation
system designed to detect and prevent email spoofing [16].
DMARC works with two existing mechanisms, Sender Policy Framework (SPF) and DomainKeys
Identified Mail (DKIM). With DMARC the administrative owner of a domain can publish a policy
on which mechanism (DKIM, SPF or both) is employed when sending email from that domain.
19](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-19-320.jpg)



![1.9 Authenticated Received Chain
Authenticated Received Chain (ARC) [17] is an email-authentication system designed to allow an
intermediate mail server to sign an email’s original authentication results. This system allows a
recipient to validate an email when the email’s SPF and DKIM records are invalidated by an in-
termediate server.
How we have seen, DMARC allows a sender’s domain to indicate that their emails are protected
by SPF and/or DKIM, and tells a receiver what to do if neither of those authentication methods
passes. However, a strict DMARC policy may block legitimate emails sent through a mailing list
or forwarder, as the SPF check will fail due to the unapproved sender and the DKIM signature will
be invalidated if the message is modified.
ARC solves this problem by giving the intermediate server a way to sign the original message’s
validation results. Even if the SPF and DKIM validation fail, the recipient can choose to validate
the ARC. If the ARC indicates that the original message passed the SPF and DKIM checks and the
only modifications were made by well-reputed intermediaries, the recipient may choose to ignore
the failed SPF, DKIM, or DMARC validation.
Figure 10: ARC work flow
1.9.1 Implementation
In order to understand better the headers that we will analyze, let’s see the three new mail headers
of ARC:
• ARC-Authentication-Results (abbreviated AAR): A combination of an instance number (i)
and the results of the SPF, DKIM, and DMARC validation.
• ARC-Seal (abbreviated AS): A combination of an instance number (i), a DKIM-like signature
of the previous ARC-Seal headers, and the validity of the prior ARC entries.
• ARC-Message-Signature (abbreviated AMS): A combination of an instance number (i) and a
DKIM-like signature of the entire message except the ARC-Seal headers
To sign a modification, an intermediate server performs the following steps:
24](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-24-320.jpg)
![• Copies the ”Authentication-Results” field into a new AAR field and prepends it to the mes-
sage.
• Calculates the AMS for the message (with the AAR) and prepends it to the message.
• Calculates the AS for the previous Arc-Seal headers and prepends it to the message.
To validate an ARC, the recipient performs the following steps:
• Validates the chain of ARC-Seal headers.
• Validates the newest ARC-Message-Signature.
1.10 Microsoft Anti-Spam Policy
Microsoft company has developed Microsoft Exchange Server that is a mail server and calendaring
server[7]. It runs exclusively on Windows Server operating systems. The first version of Exchange
Server to be published by Microsoft was Exchange Server 4.0. The client is Microsoft Outlook.
Microsoft Exchange Online provides built-in malware and spam filtering capabilities that help
protect inbound and outbound messages from malicious software and help protect your network
from spam transferred through email. Administrators do not need to set up or maintain the filtering
technologies, which are enabled by default. However, administrators can make company-specific
filtering customizations in the Exchange admin center (EAC).
1.10.1 Office 365 email anti-spam protection
In the last years Office 365 is the brand name Microsoft that consists of a group of software[8]. All
of Office 365’s components can be managed and configured through an online portal. The email
service Outlook is included. In Office 365, it is possible to change a protection setting to deal with
a specific issue in a specific organization. The following are some options that help to prevent spam
in Office 365:
• Connection filtering: This mechanism consists of checking the reputation of the sender
before allowing a message to get through. In order to do this it is possible to create an allow
list, or safe sender list, to be sure about the received message sent from a specific IP address
or IP address range. Furthermore, it is also possible to create a list of IP addresses from
which to block messages, called a block list.
• Spam filtering: This technique checks for message has characteristics like a spam. It is
possible to change what actions to take on messages identified as spam, and choose whether
to filter messages written in specific languages, or sent from specific countries or regions.
There are also advanced spam filtering options in order to pursue an aggressive approach to
spam filtering.
• Outbound filtering: It is used when you want that your users don’t send spam. For
instance, a user’s computer may get infected with malware that causes it to send spam
messages, so is possible to have a protection against that into the product.
• Email authentication : Techniques that use the Domain Name System (DNS) to add
verifiable information to email messages about the sender of an email message. These are:
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain-based
Message Authentication, Reporting, and Conformance (DMARC). Is recommended to use
SPF, DKIM, and DMARC together to help prevent spam and unwanted spoofing.
25](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-25-320.jpg)
![It is possible to change the default personal mail in Office 365 following the video of the page [8].
In order to understand better how Office 365 uses and set Sender Policy Framework (SPF) to
prevent spoofing, how uses DKIM to validate email and how configures your spam filter policies
see [9].
1.10.2 Anti-spam message headers
Exchange Online Protection (EOP) is a hosted e-mail security service, owned by Microsoft, that
filters spam and removes computer viruses from e-mail messages. The service does not require
client software installation and each customer pays for the service by means of a subscription.
When Exchange Online Protection scans an inbound email message it inserts the X-Forefront-
Antispam-Report header into each message. The fields in this header can help provide adminis-
trators with information about the message and about how it was processed. The fields in the
X-Microsoft-Antispam header provide additional information about bulk mail and phishing.
A quite useful tool provided by Office 365 is Message Header Analyzer that with a copy and paste
header from an email retrieves information about the header. Figure 7 is a personal example of the
use of this tool with my personal Outlook mail and the Figure 8 shows the two additional headers
for anti-spam.
Figure 11: Output of Message Header Analyzer
Figure 12: Forefront Antispam Report Header and Microsoft Antispam Header
From the analysis of some email sent with my personal account Microsoft (Outlook) I noticed
that it uses a lot of non-standard or custom headers. Some of these are:
• X-MS-Has-Attach: Tells whether the e-mail has an attached document with it or not. When
we send a message without any text it has a blank value.
26](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-26-320.jpg)




![Figure 16: Particular headers of Yahoo
2 Personal Investigation for Spam
In this section I have analyzed a suitable number of message headers found both in my regular
INBOX and in the SPAM folder. Furthermore, I tried to determine a few categories/patterns of
information in the relevant header fields so that my SPAM folder can be partitioned into homo-
geneous subsets, such that most of the messages belonging to the same subset are based on the
same/similar techniques/patterns for bypassing the anti-spam measures [19].
How we have seen for my personal experience, we have analyzed some message sources from differ-
ent email services like Yahoo, Microsoft and GMail. For this experiment I used different personal
Gmail accounts and one Yahoo mail. In the Spam folder of these emails every month I receive a
lot of spam.
It’s important to specify that Gmail service automatically delete the spam emails that date back
to more than 30 days. In my personal Gmail account t.florin92@gmail.com I have a Spam folder
with 90 elements and in florin.tanasache@gmai.com only 2 elements as I was writing this report.
Furthermore, I have verified also the institutional GMail tanasache.1524243@studenti.uniroma1.it
but its Spam folder is empty. The Yahoo mail mr.boss4@yahoo.it has a Spam folder containing 23
elements.
2.1 Spam Folder
In order to understand why Gmail or Yahoo classifies some emails as spam and under which
consideration we can partition the Spam folder it is necessary to examine the headers from different
31](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-31-320.jpg)








![Figure 28: Example spam folder organization
Between the messages of the GMail and Yahoo spam folder I want to underline a particular
type of spam that I found only in the Yahoo spam folder. This type of spam is about ”sexual”
meetings. Usually, this type is constituted by a description of this ”proposal” and it ends with a
not secure URL.
Figure 29: Example Yahoo spam
2.10 Mozilla Thunderbird
This personal experiment has been done using the email client Mozilla Thunderbird[18]. Thunder-
bird can be configured to work seamlessly with Google’s Gmail service. Messages are synchronized
between my local version of Thunderbird and the web-based Gmail. Gmail uses a special imple-
mentation of IMAP. In this implementation, Gmail labels become Thunderbird folders. When is
applied a label to a message in Gmail, Thunderbird creates a folder with the same name as the
label and stores the message in that folder. Therefore, we have the same folders as we are using
40](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-40-320.jpg)





![References
[1] Sender Policy Framework. Related Solutions, Project Overview
http://www.openspf.org/
[2] RFC 4408. Sender Policy Framework, 2006
https://www.ietf.org/rfc/rfc4408.txt
[3] RFC 7208. Sender Policy Framework, 2014
https://tools.ietf.org/html/rfc7208
[4] RFC 4406. Sender ID, 2006
https://tools.ietf.org/html/rfc7208
[5] Sender ID. SPF vs Sender ID
http://www.openspf.org/SPF_vs_Sender_ID
[6] Microsoft anti-spam protection. Sender ID
https://technet.microsoft.com/en-us/library/aa996295(v=exchg.150).aspx
[7] Microsoft anti-spam policy. Anti-Spam and Anti-Malware Protection
https://technet.microsoft.com/it-it/library/exchange-online-antispam-and-antimalware-protec
aspx
[8] Microsoft Office 365. Office 365 email anti-spam protection
https://support.office.com/en-us/article/Office-365-Email-Anti-Spam-Protection-6a601501-a6a
ui=en-US&rs=en-US&ad=US
[9] Microsoft Office 365 Utilities.
How Office 365 uses Sender Policy Framework (SPF) to prevent spoofing
https://technet.microsoft.com/library/mt712724(v=exchg.150).aspx
Set up SPF in Office 365 to help prevent spoofing
https://technet.microsoft.com/library/dn789058(v=exchg.150).aspx
Use DKIM to validate outbound email sent from your custom domain in Office 365
https://technet.microsoft.com/library/mt695945(v=exchg.150).aspx
Use DMARC to validate email in Office 365
https://technet.microsoft.com/library/mt734386(v=exchg.150).aspx
Configure your spam filter policies
https://technet.microsoft.com/library/jj200684(v=exchg.150).aspx
[10] DomainKeys Identified Mail (DKIM). RFC 6376, September 2011
https://tools.ietf.org/pdf/rfc6376.pdf
[11] DKIM Community. DKIM.org
http://dkim.org/
[12] DomainKeys Identified Mail (DKIM) Service Overview. RFC 5585, June 2009
https://tools.ietf.org/html/rfc5585
[13] Author Domain Signing Practices (ADSP). Wikipedia page
https://en.wikipedia.org/wiki/Author_Domain_Signing_Practices
46](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-46-320.jpg)
![[14] Author Domain Signing Practices (ADSP). RFC 5617, August 2009
https://tools.ietf.org/html/rfc5617
[15] Domain-based Message Authentication, Reporting, and Conformance (DMARC). RFC 7489,
March 2015
https://tools.ietf.org/html/rfc7489
[16] Domain-based Message Authentication, Reporting, and Conformance (DMARC). Wikipedia
page
https://en.wikipedia.org/wiki/DMARC
[17] Authenticated Received Chain. ARC Specification for Email
arc-spec.org
[18] Moziella Thunderbird. Thunderbird and Junk/Spam Messages
https://support.mozilla.org/en-US/kb/thunderbird-and-junk-spam-messages
[19] ReturnPath Blog. Discover Where, When, and How Subscribers are Interacting With Email
https://blog.returnpath.com
47](https://image.slidesharecdn.com/anti-spamtechniques-171123211850/85/Anti-spam-techniques-47-320.jpg)