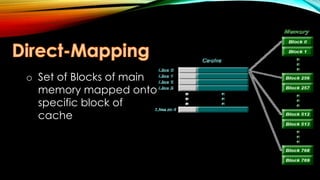
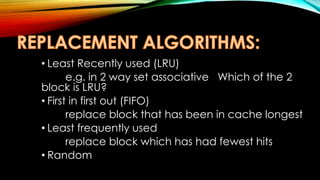
There are three main methods to map main memory addresses to cache memory addresses: direct mapping, associative mapping, and set-associative mapping. Direct mapping is the simplest but least flexible method, while associative mapping is most flexible but also slowest. Set-associative mapping combines aspects of the other two methods, dividing the cache into sets with multiple lines to gain efficiency while remaining reasonably flexible.