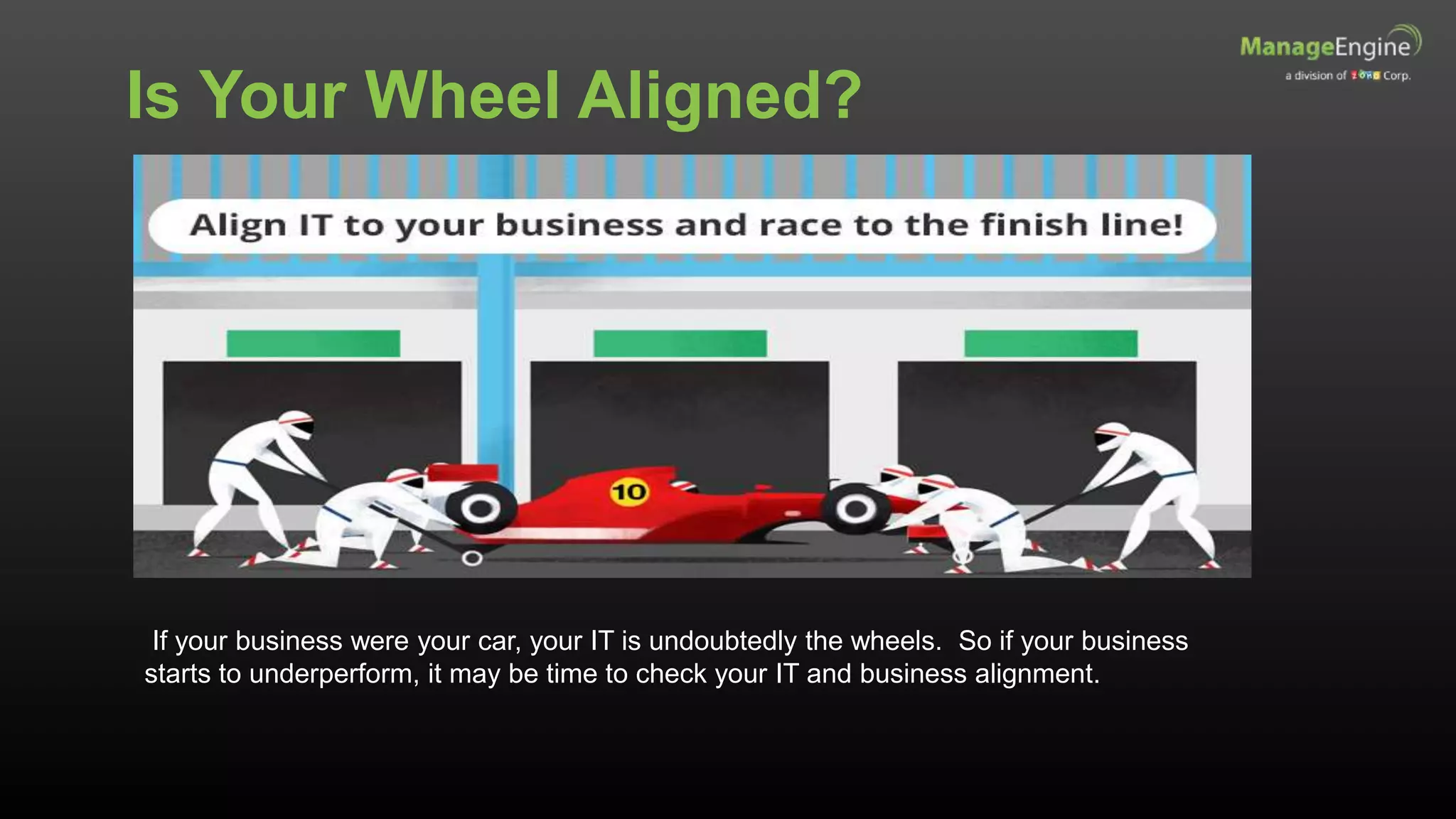
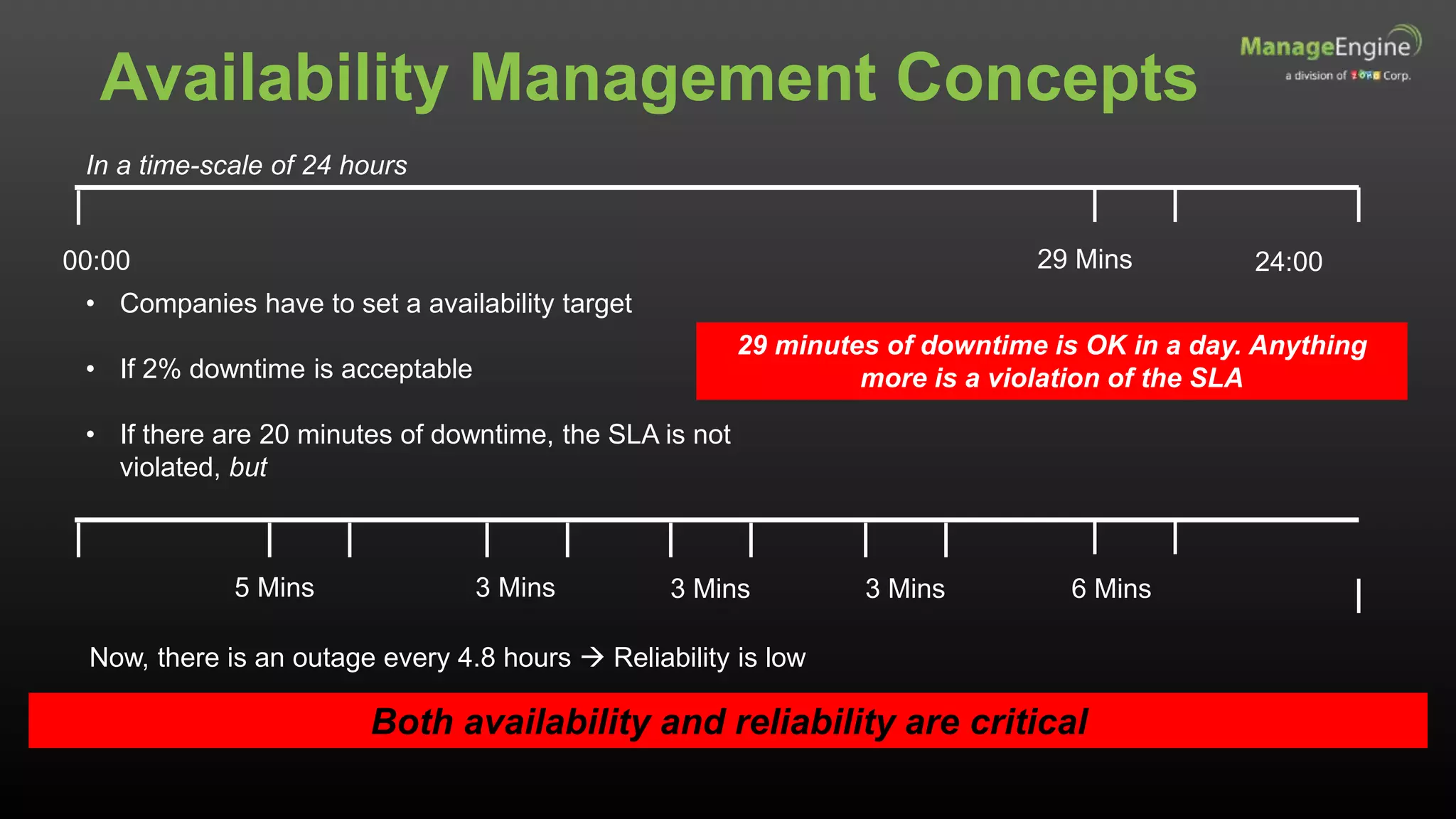
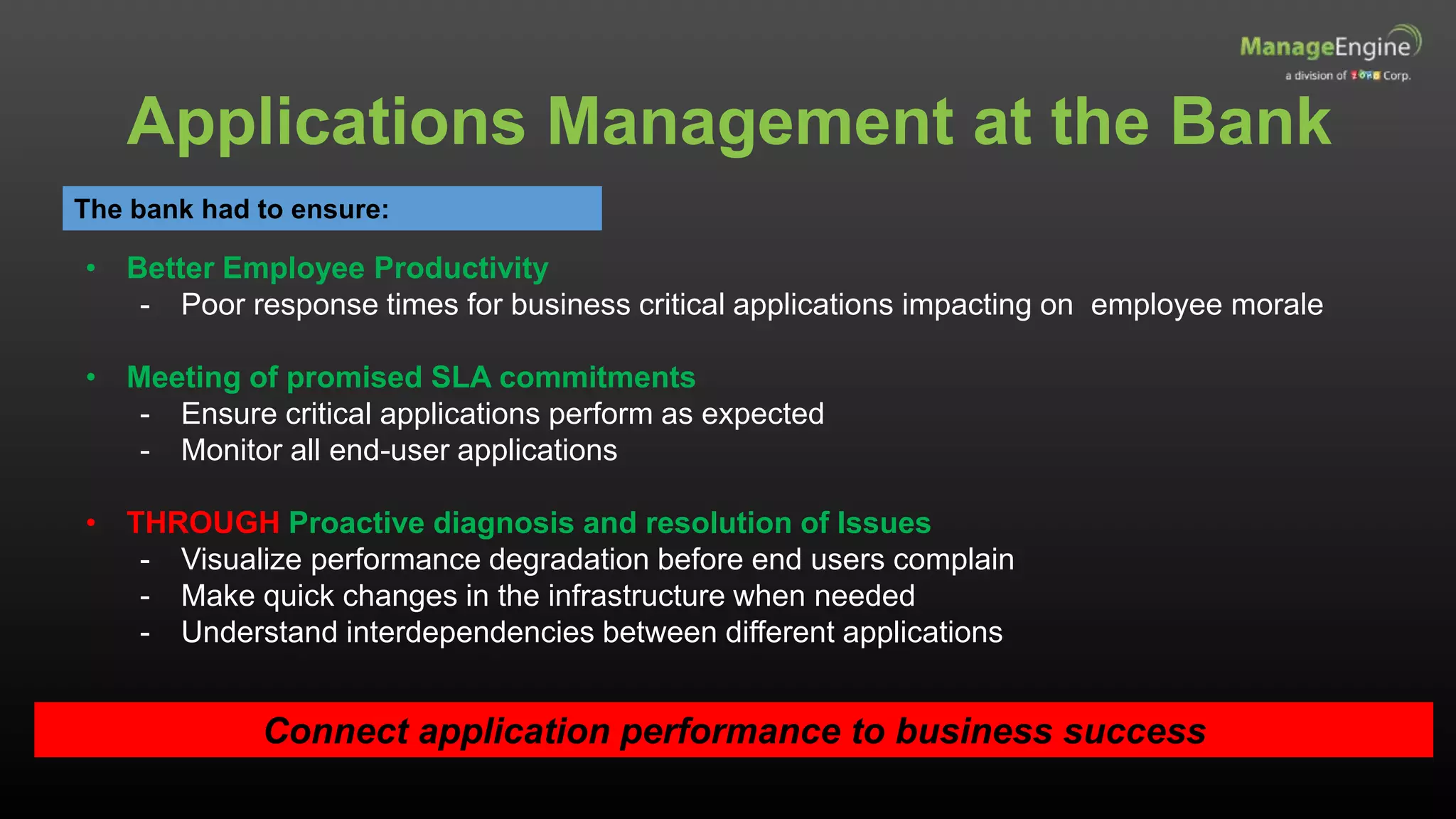
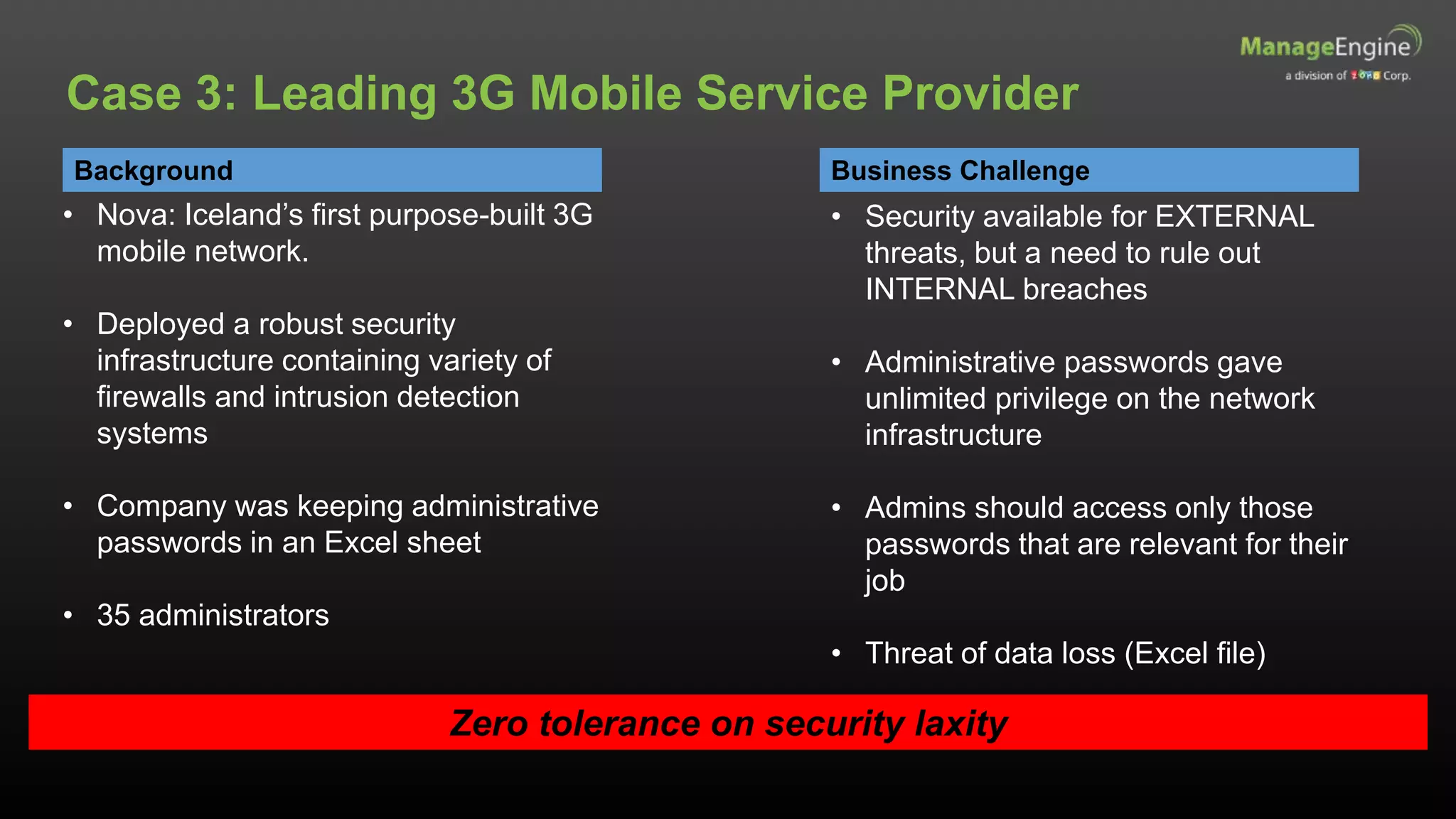
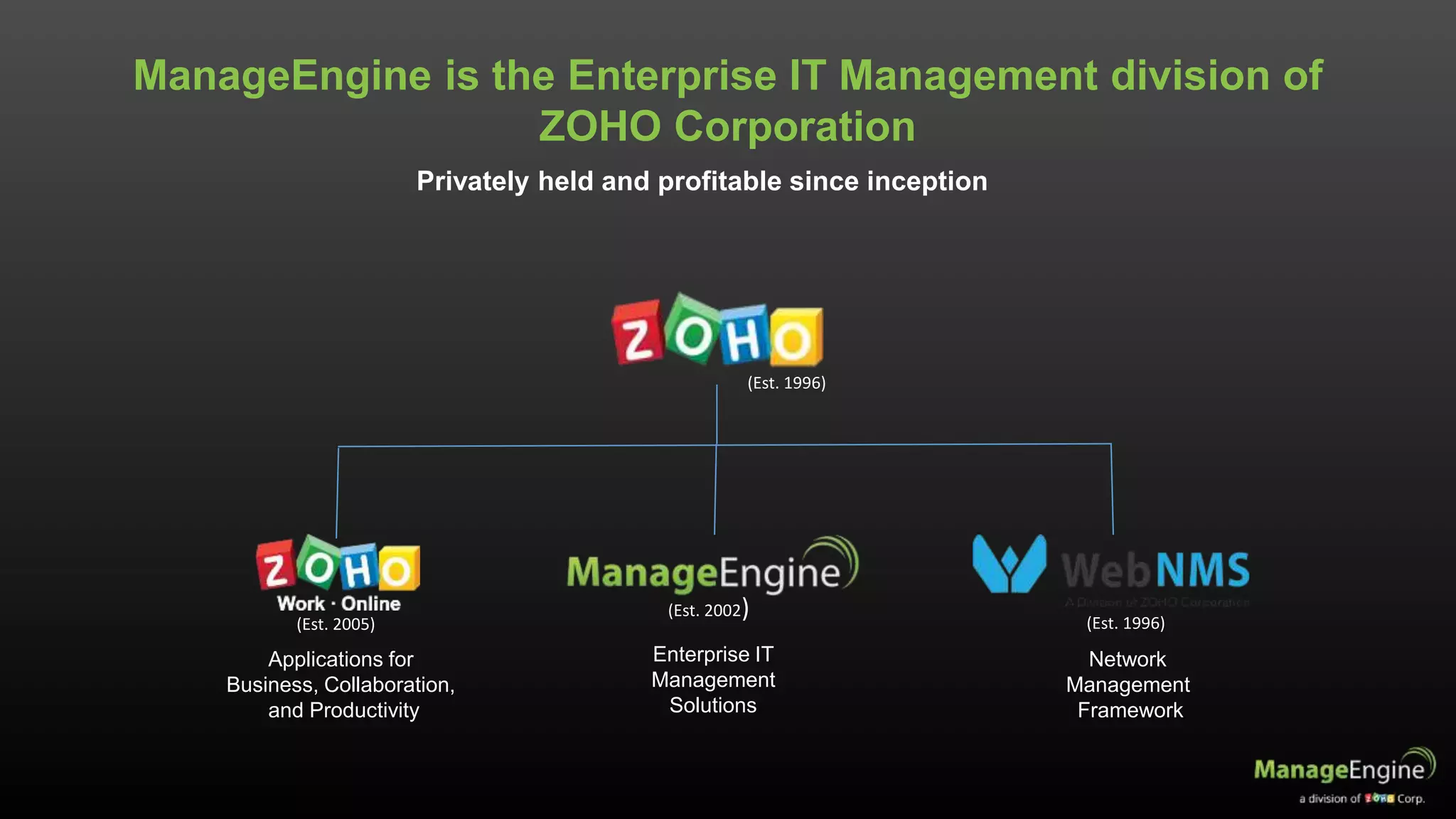
The document discusses IT management solutions by Claire Brereton, emphasizing the need for alignment between IT and business to enhance efficiency and productivity. It outlines eight strategies for achieving this alignment, including creating an IT brand, leveraging social media, and utilizing big data. Additionally, it highlights case studies demonstrating the importance of effective IT management in various organizational contexts.