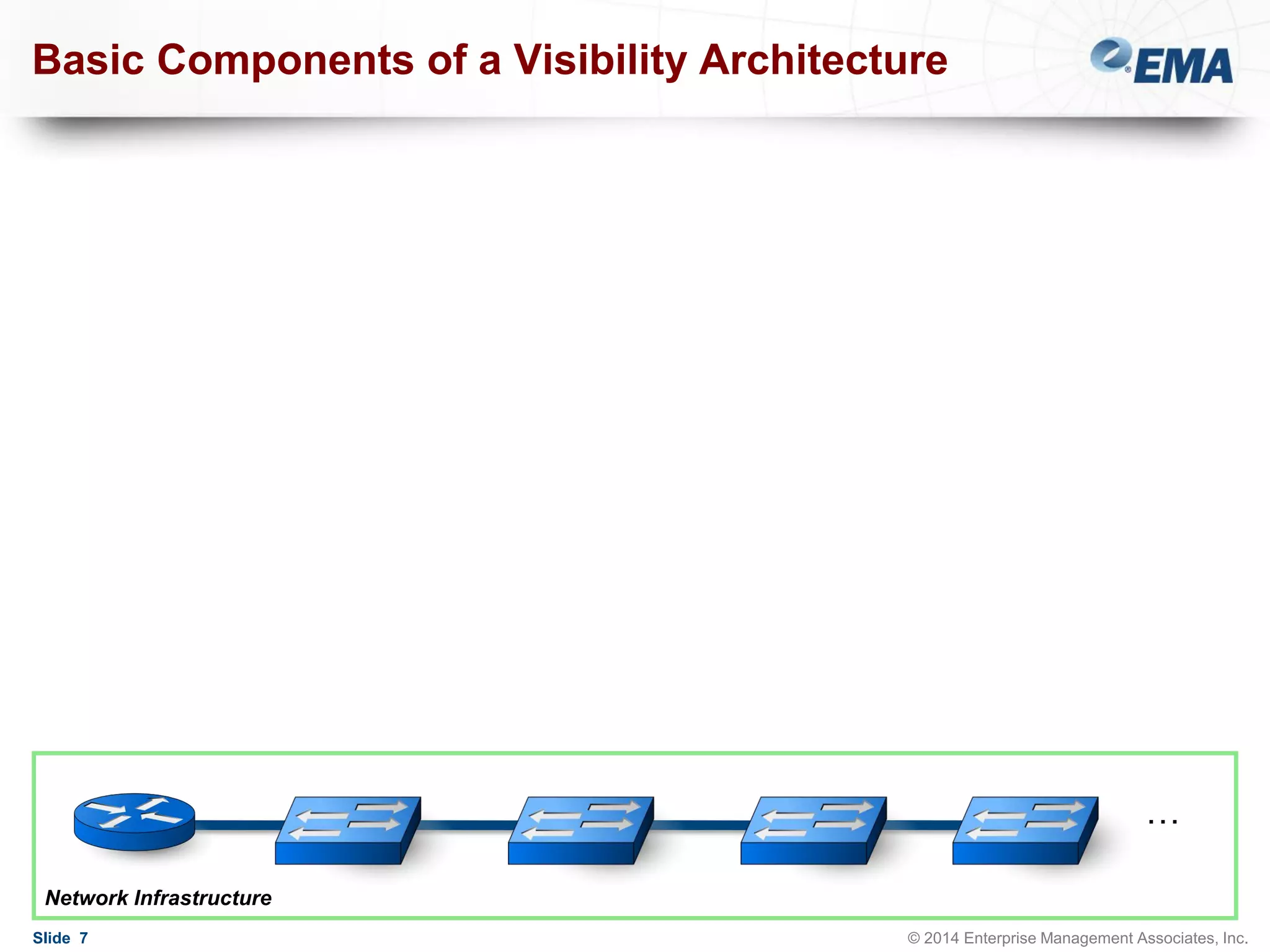
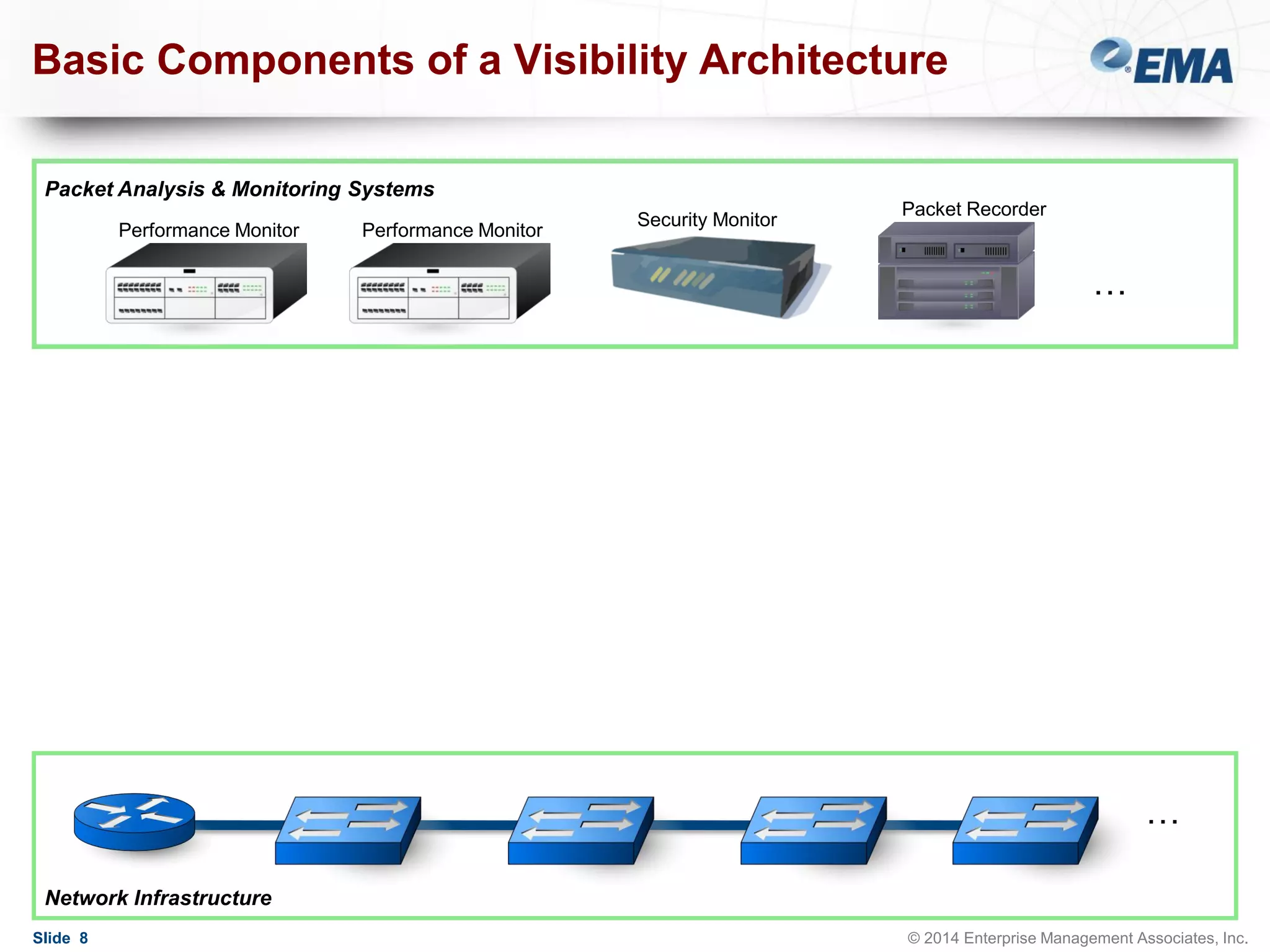
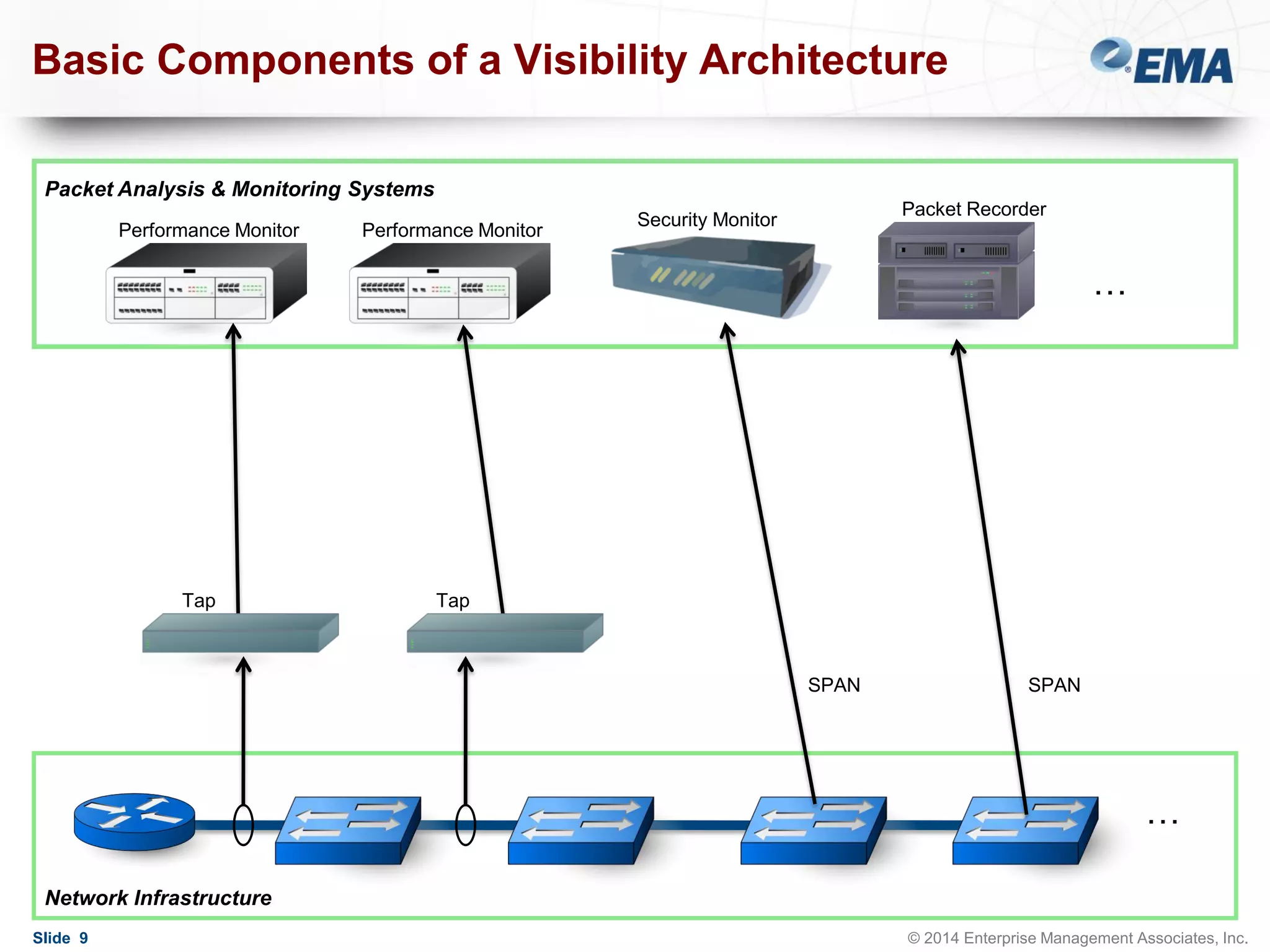
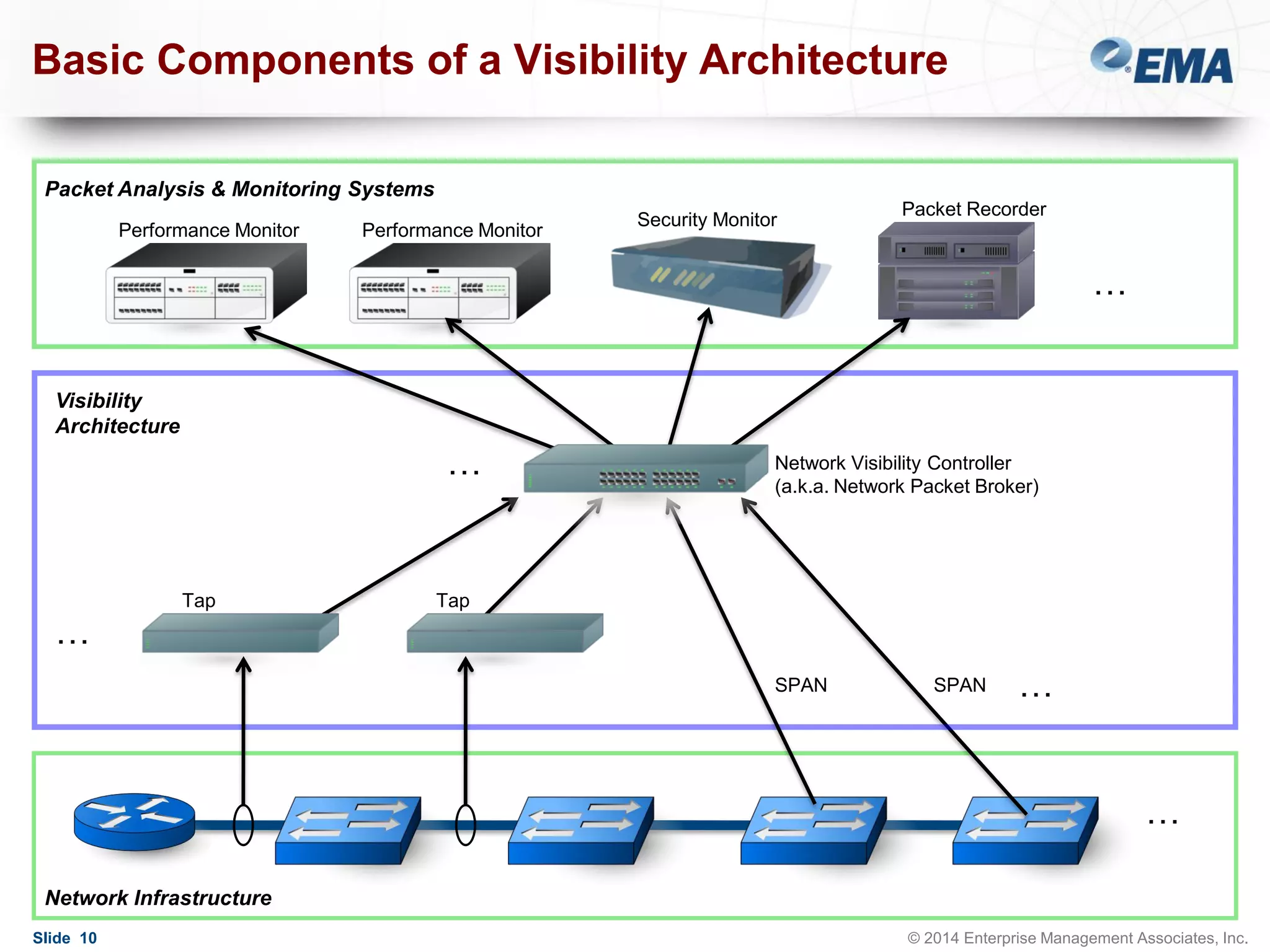
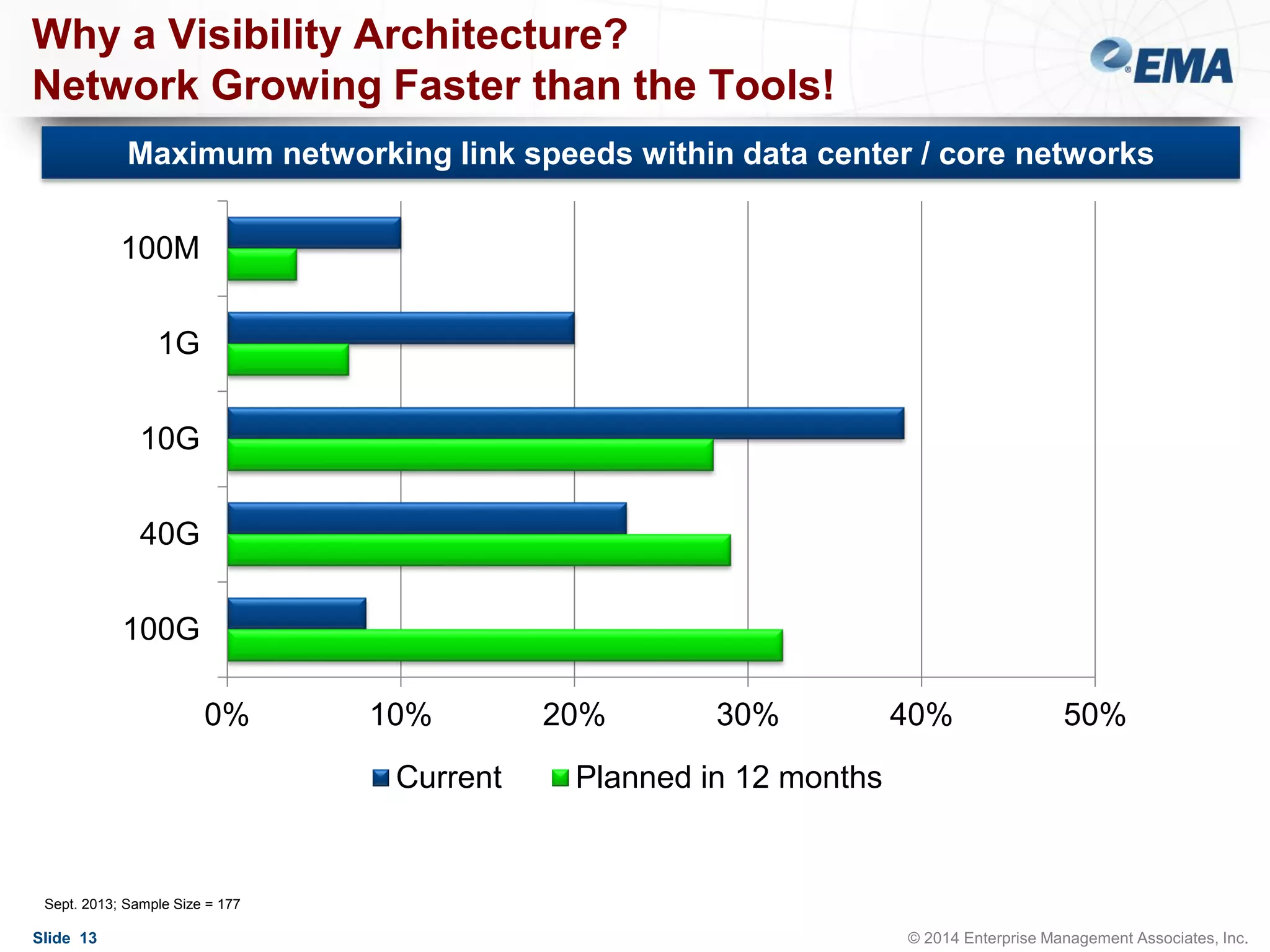
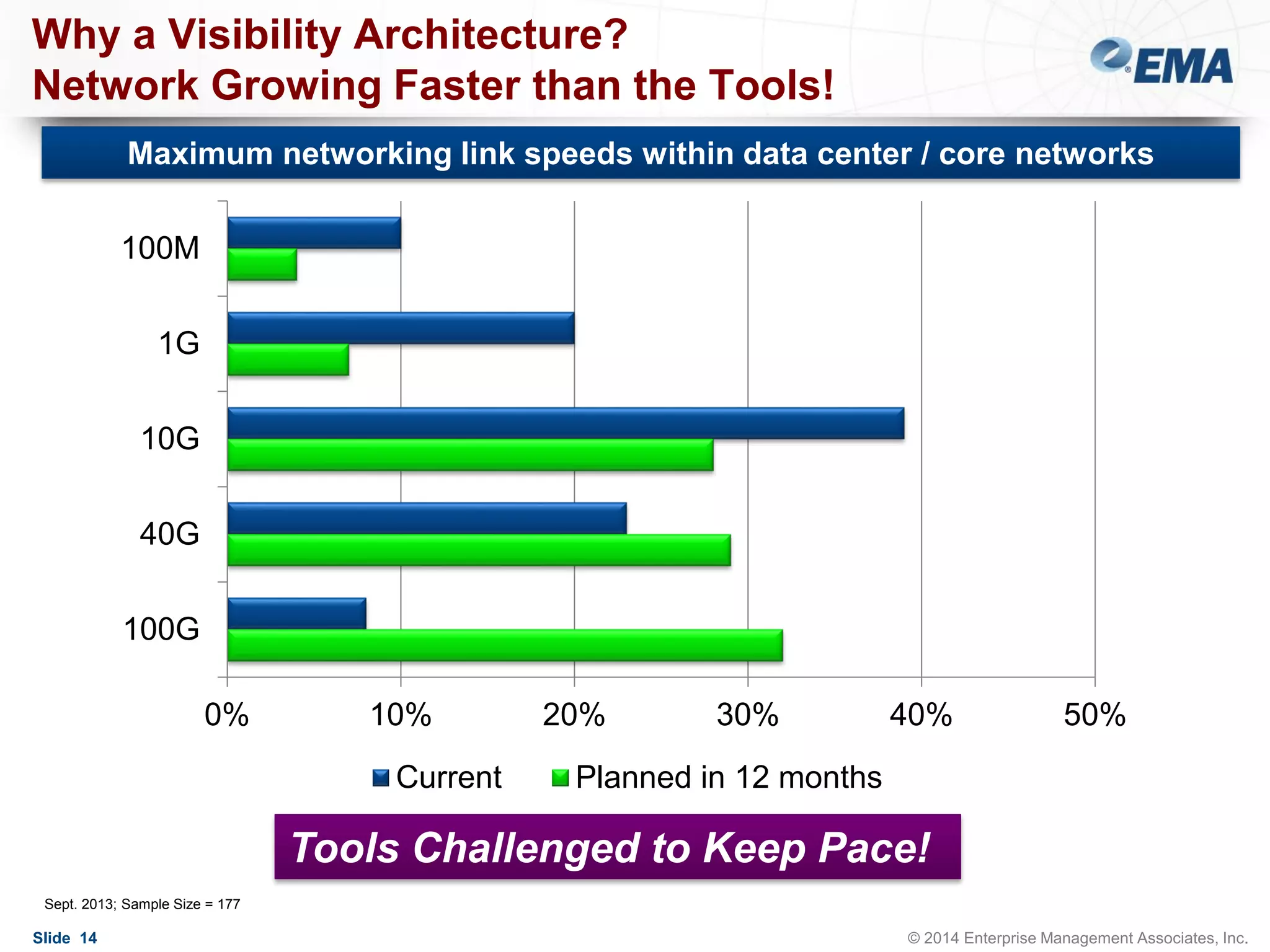
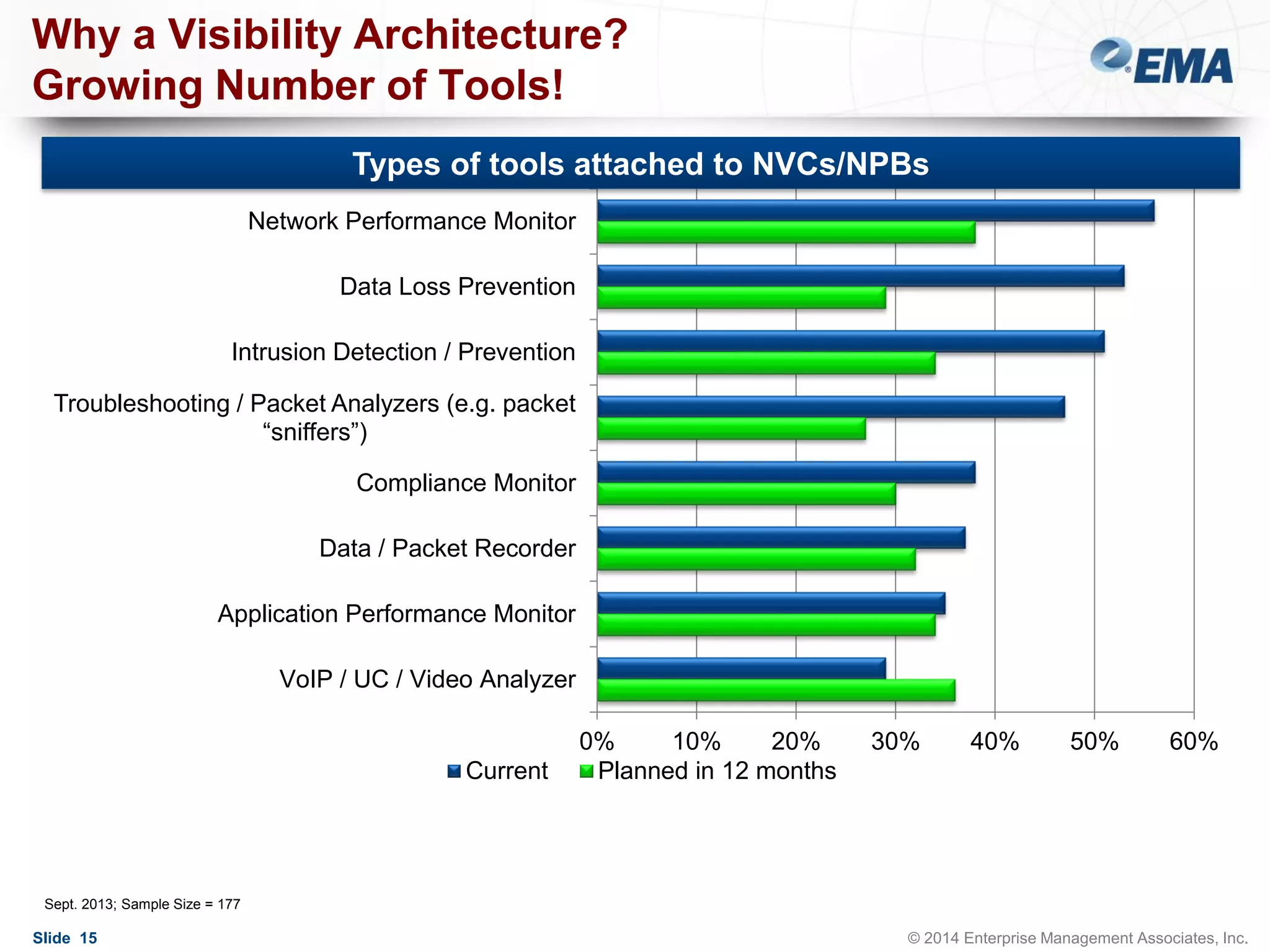
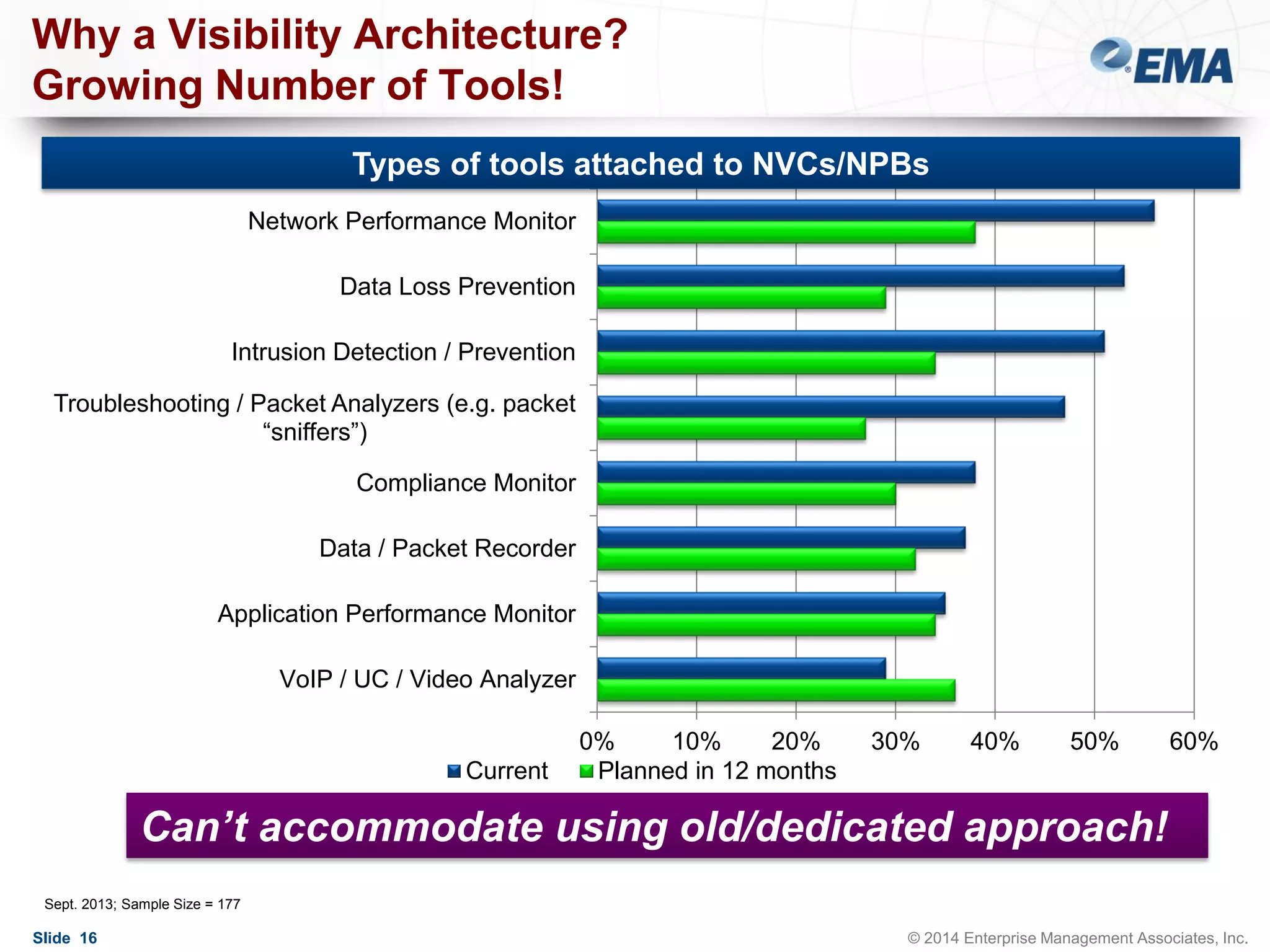
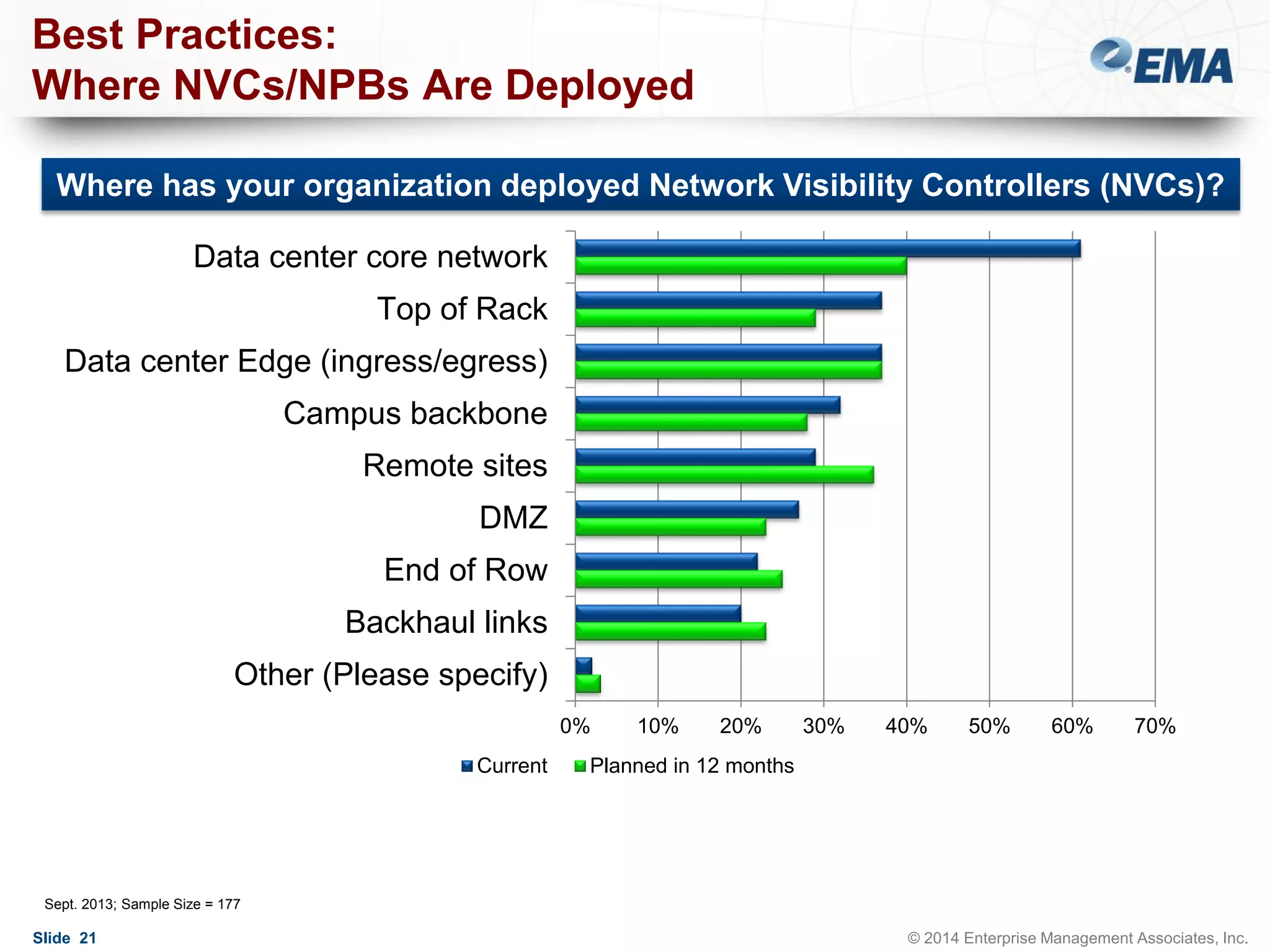
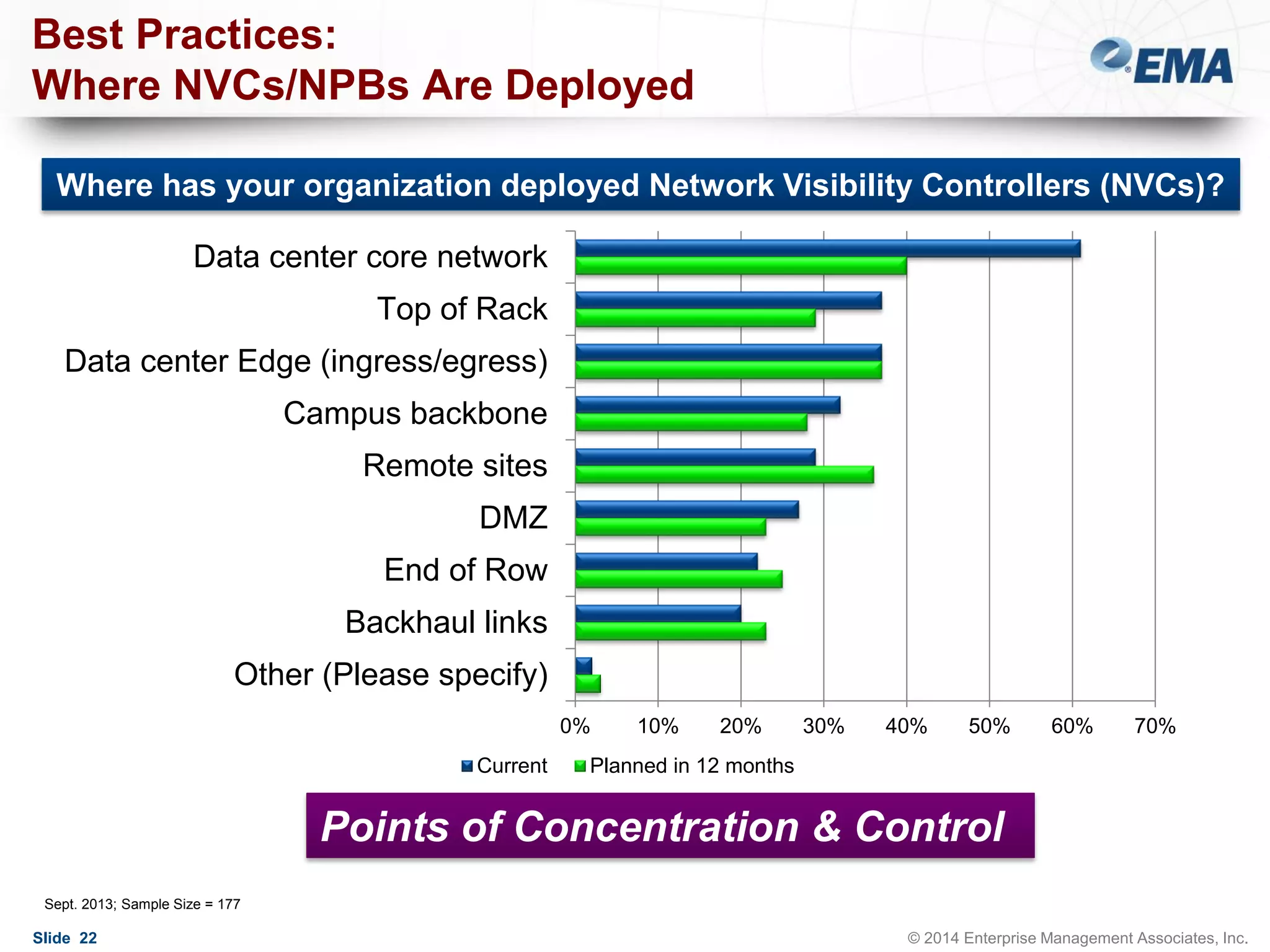
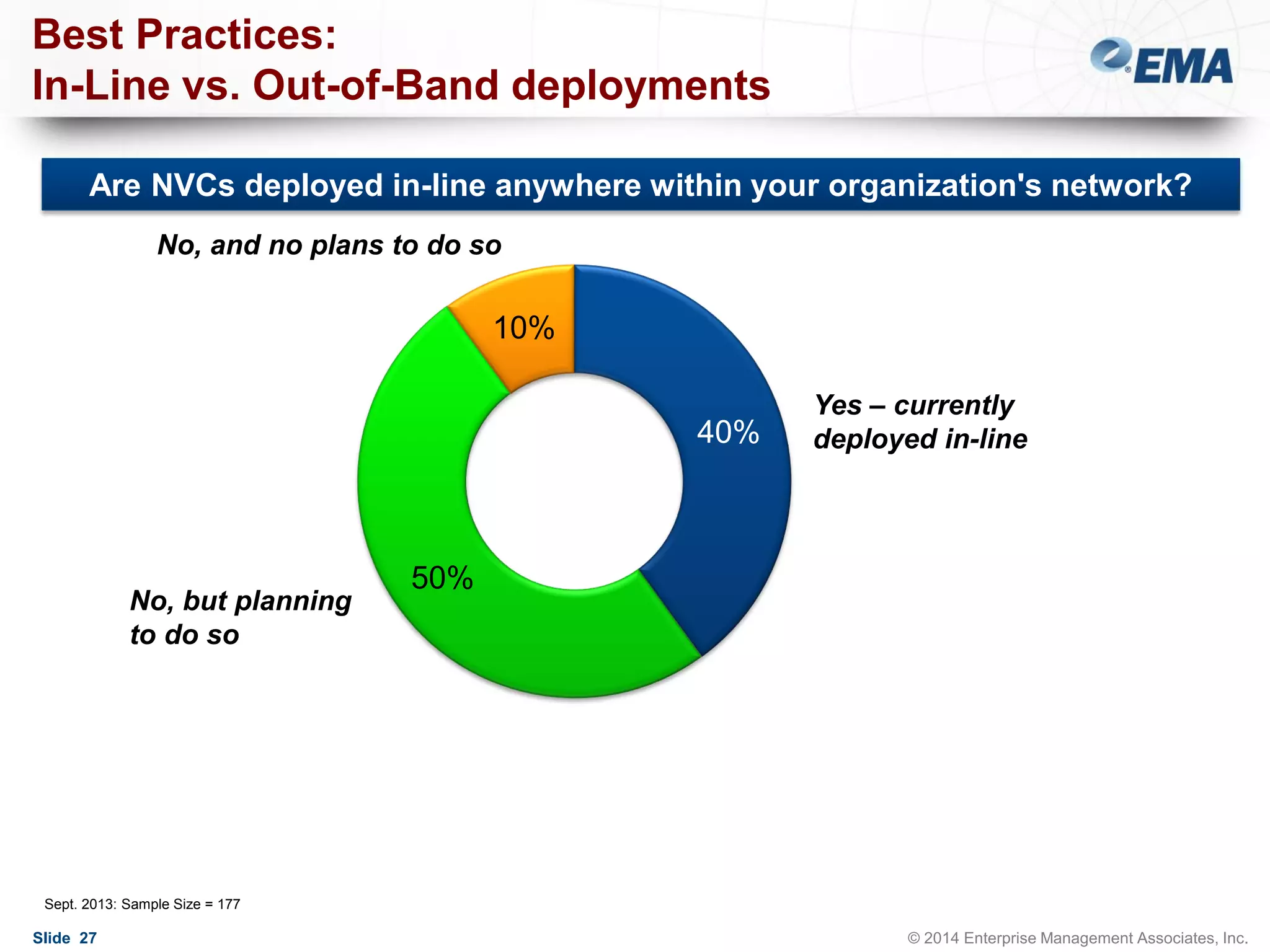
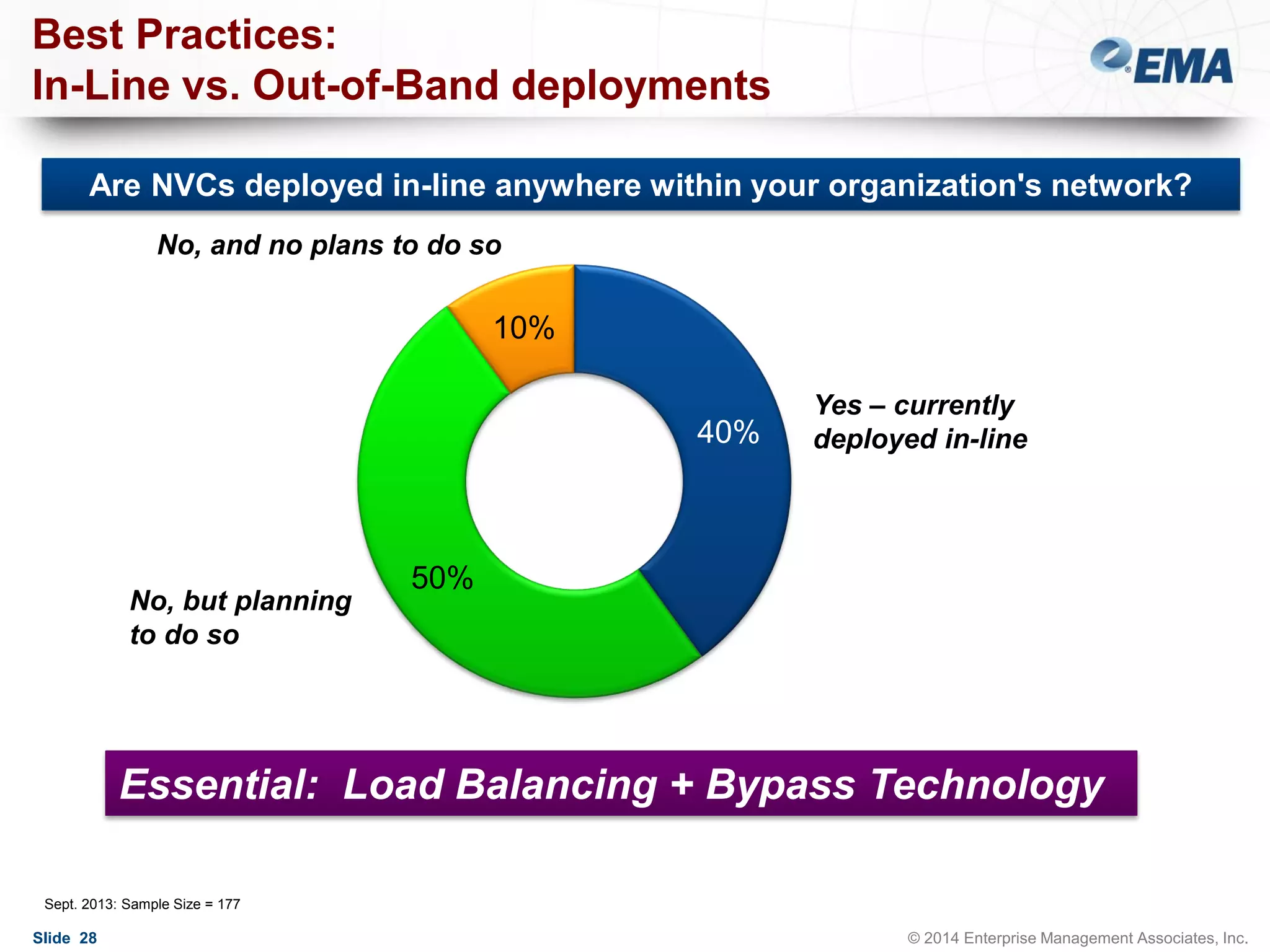
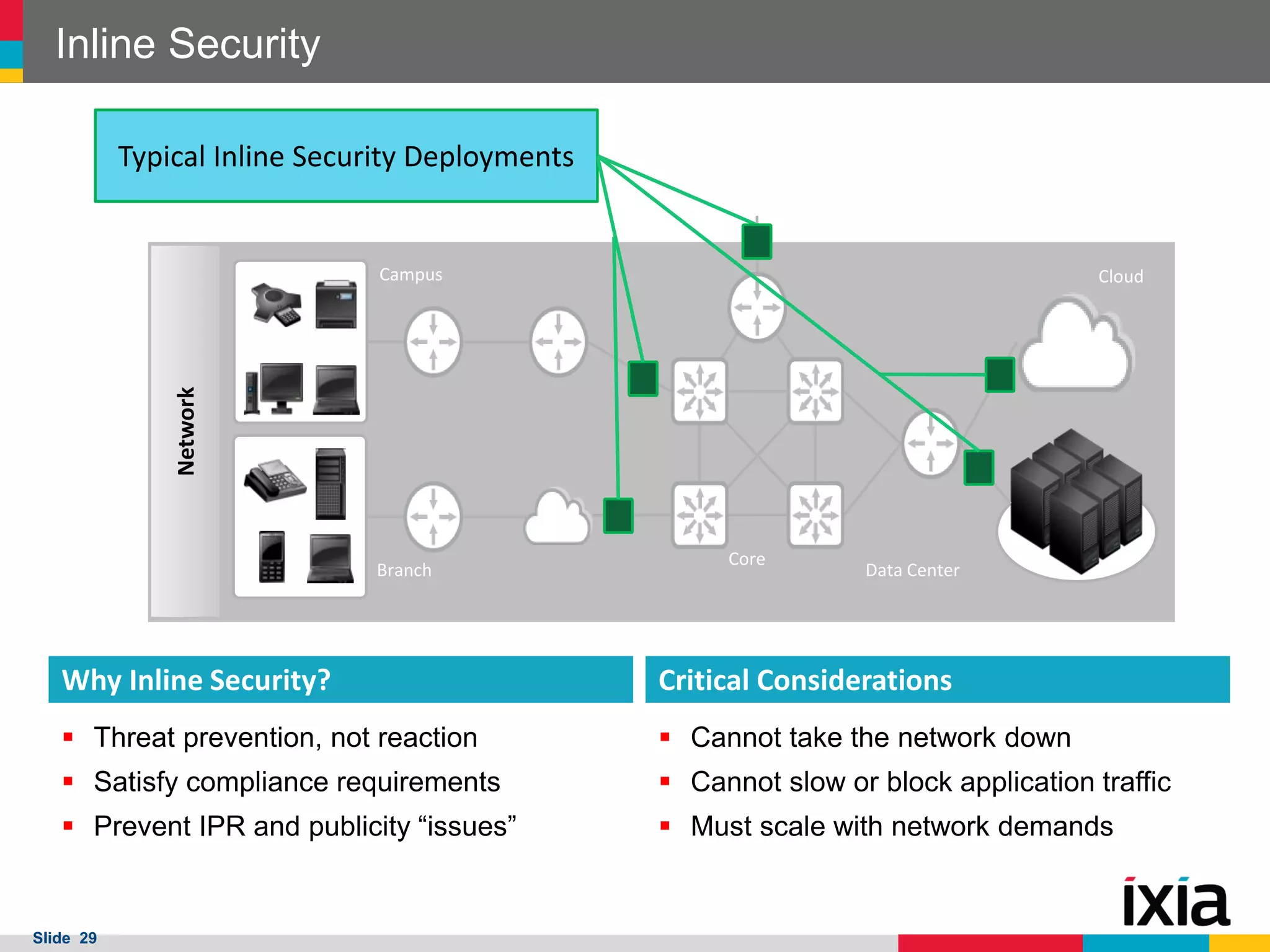
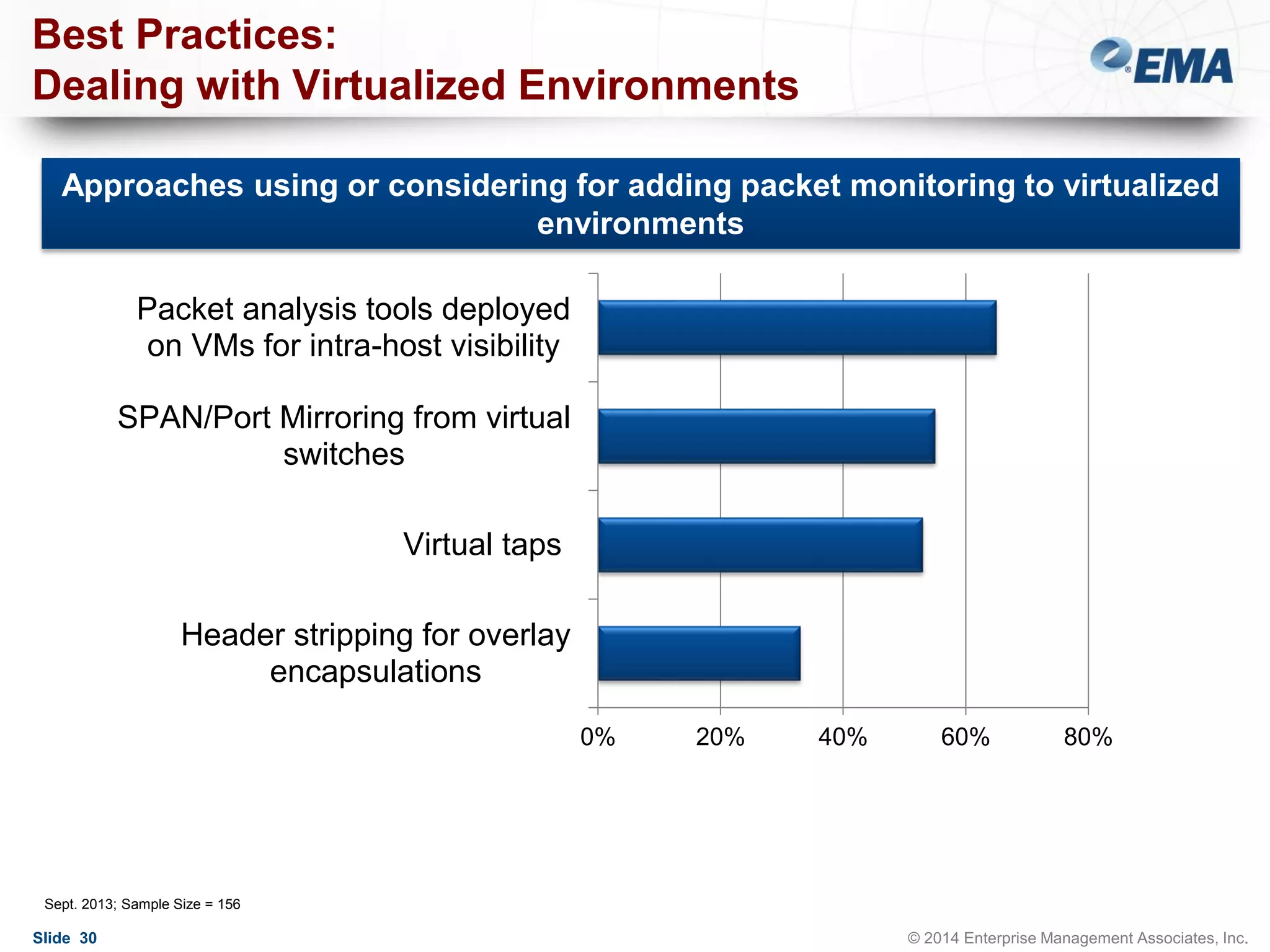
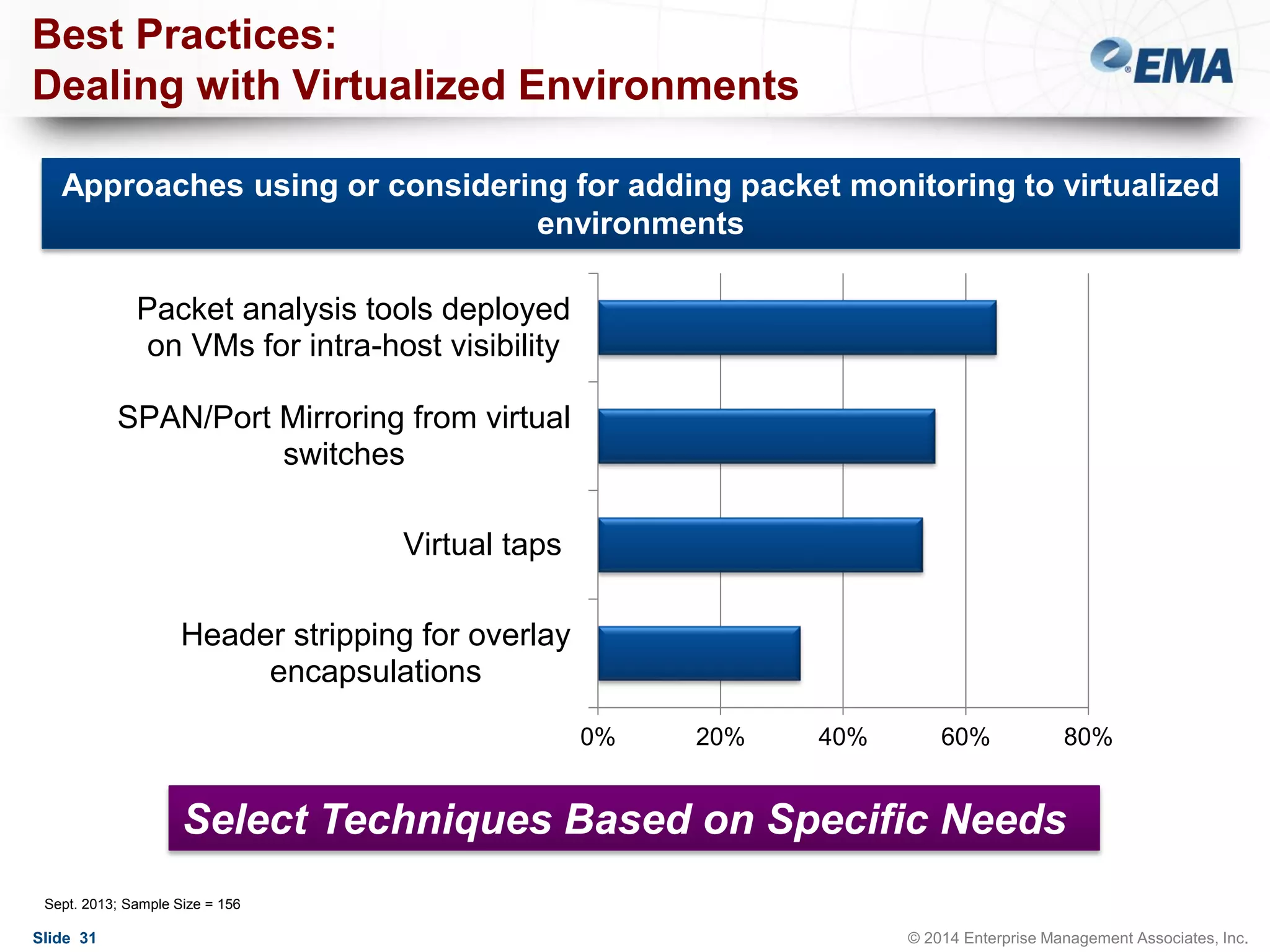
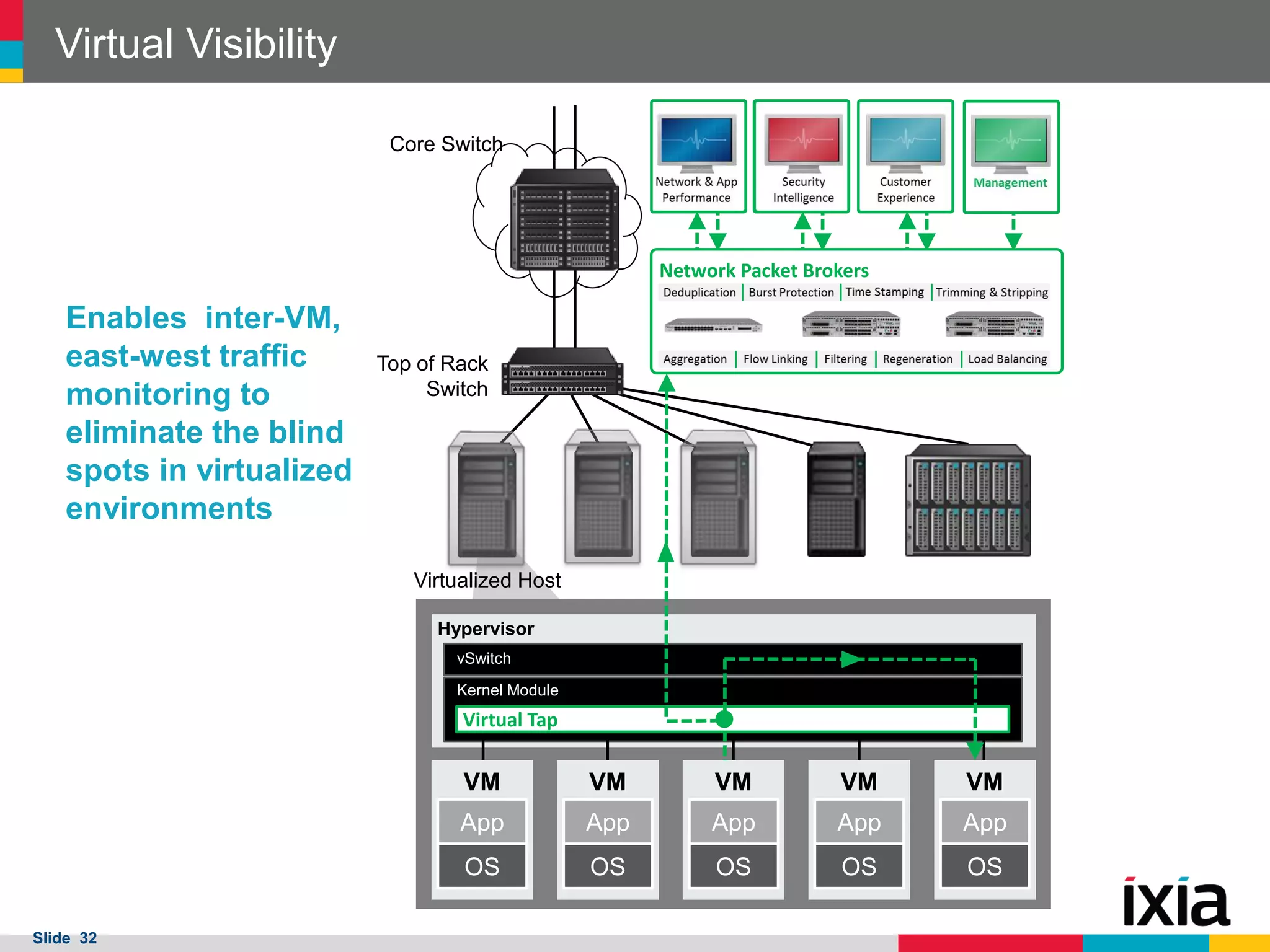
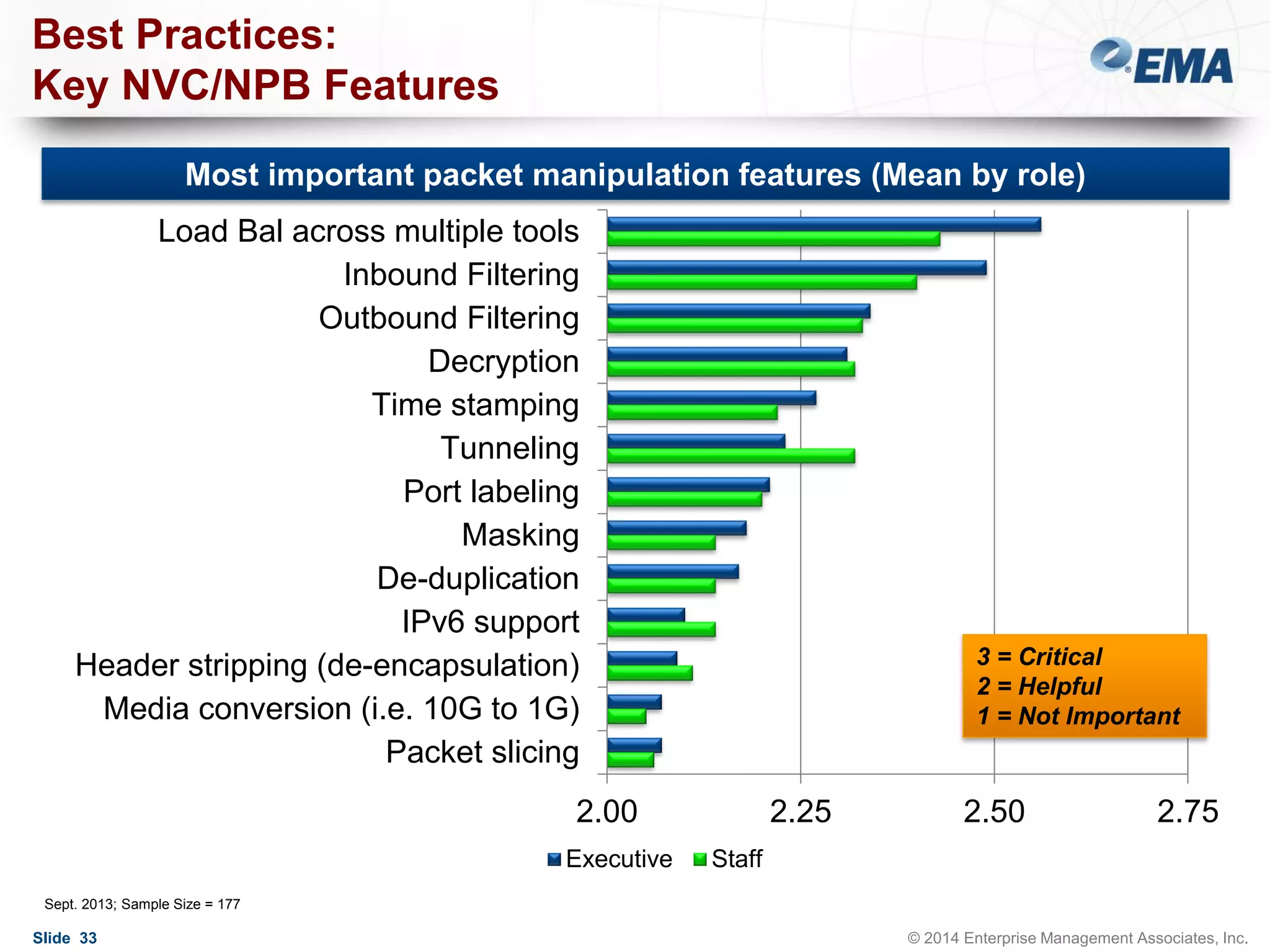
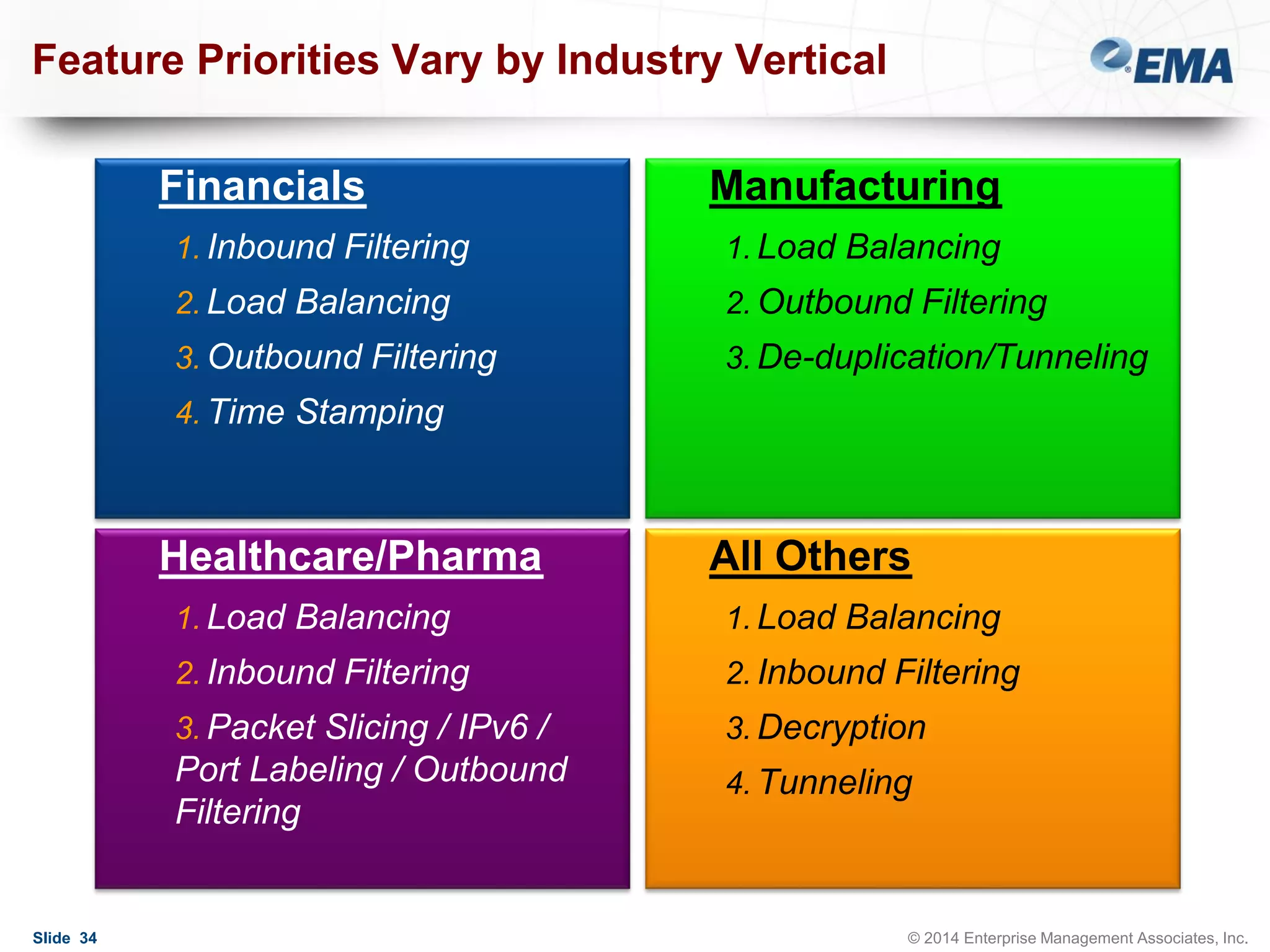
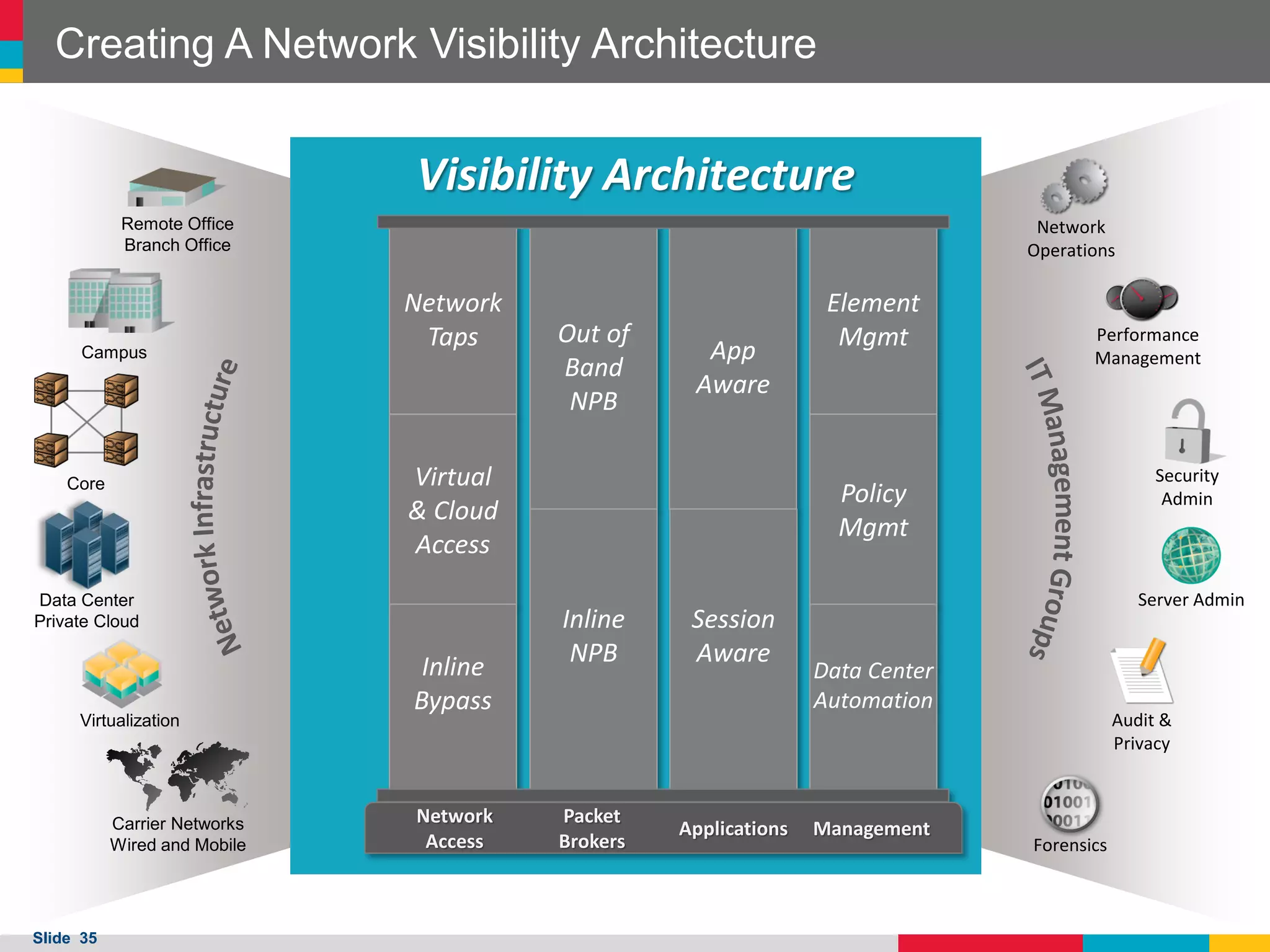
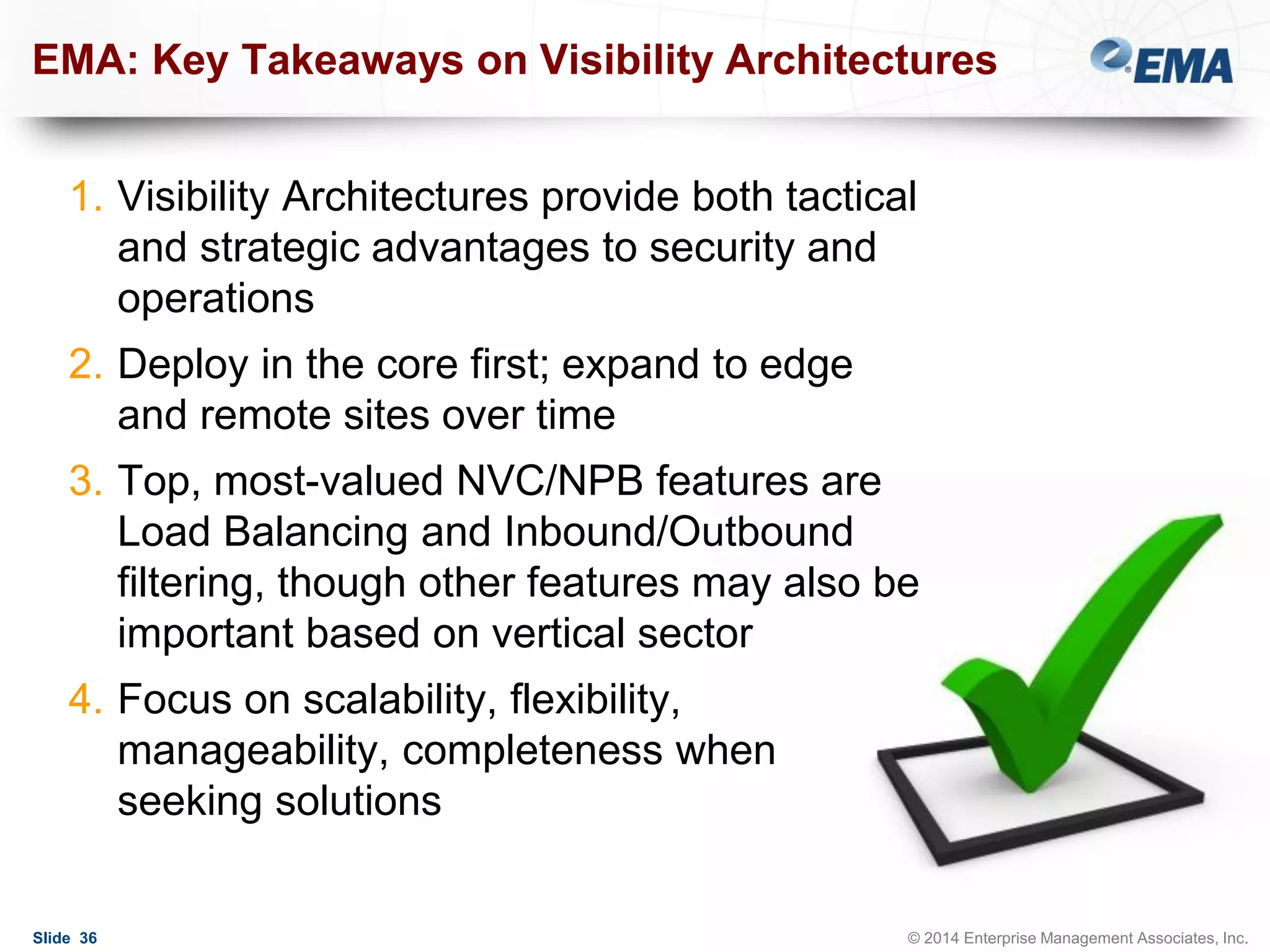
The document outlines best practices for building scalable visibility architectures, presented by experts Jim Frey and Scott Register. It covers key definitions, components, and the importance of visibility architecture in managing network traffic for performance and security operations. The webinar emphasizes the need for adaptive and resilient infrastructures due to the rapid growth of network traffic and tools.