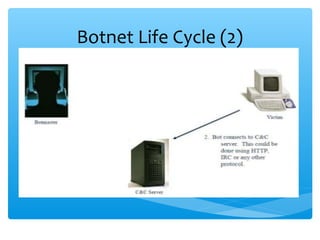
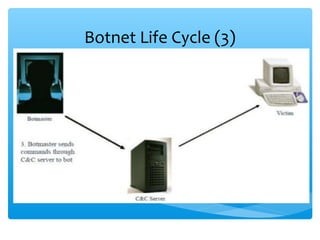
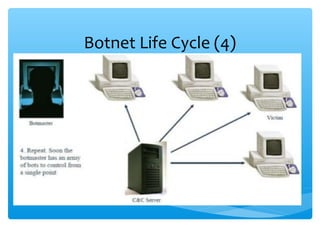
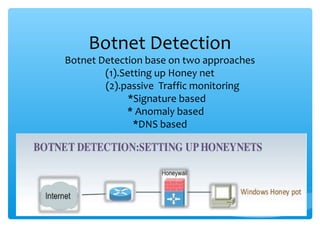
This document discusses botnets, which are networks of compromised computers controlled remotely by attackers. Botnets began as monitoring tools but are now significant contributors to criminal activities online. The document outlines botnet terminology, lifecycles, and impacts like distributing spam emails. It also discusses methods for detecting botnets through honey nets and traffic monitoring, as well as preventing infections through firewalls, antivirus software, and intrusion detection systems. The conclusion emphasizes that botnets pose a growing cybersecurity threat and detecting and mitigating botnet attacks is important for network security.