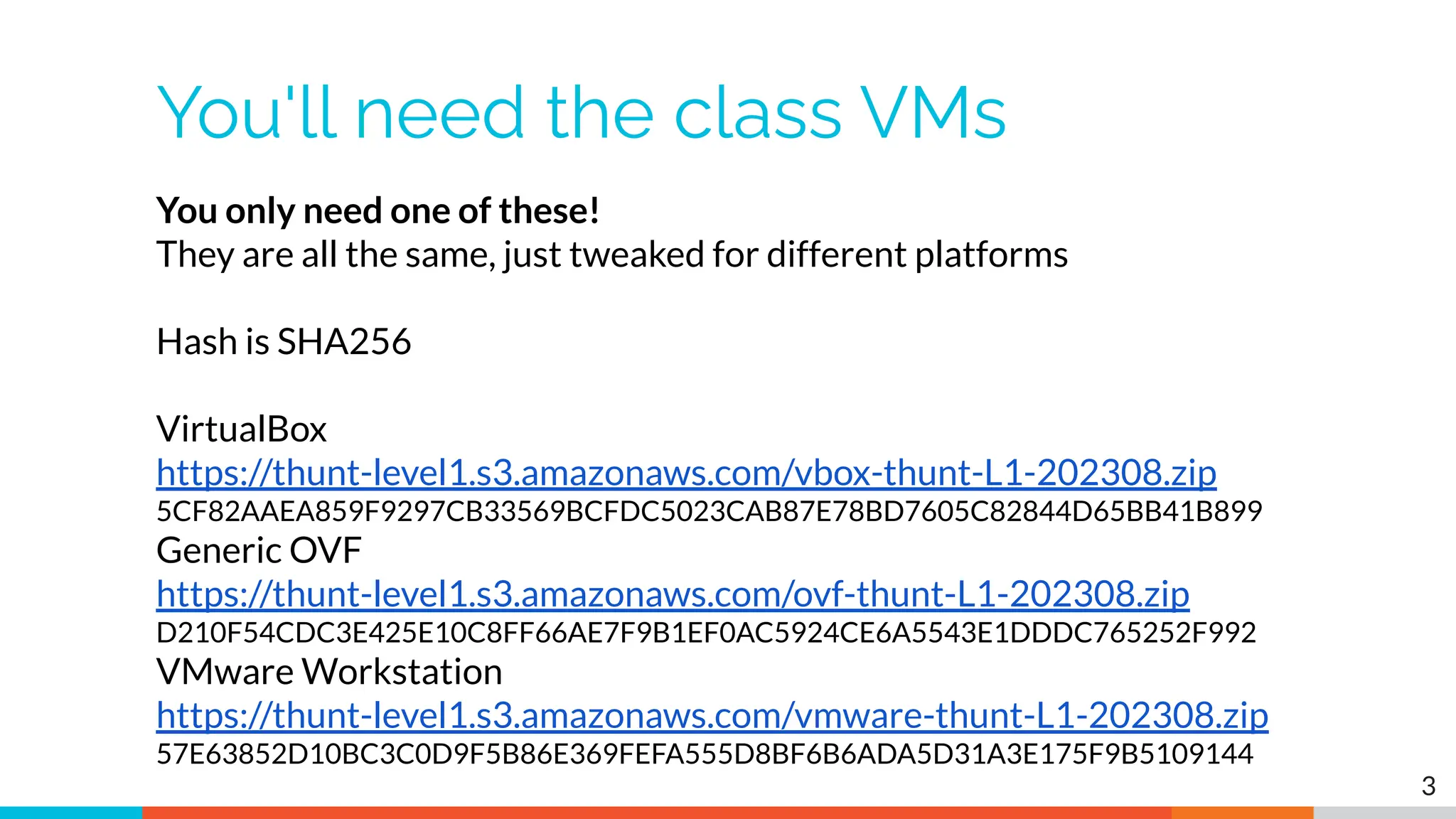
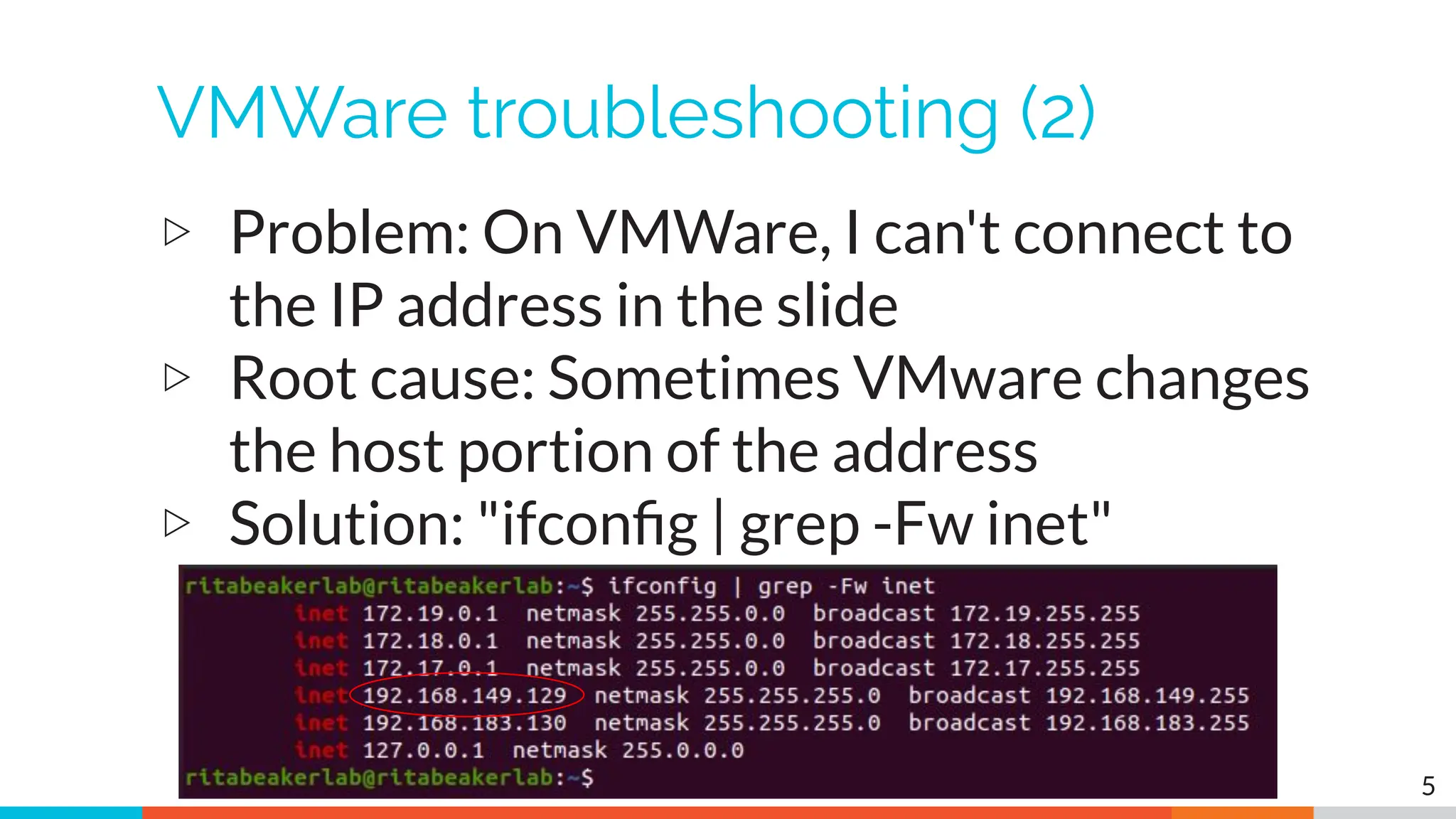
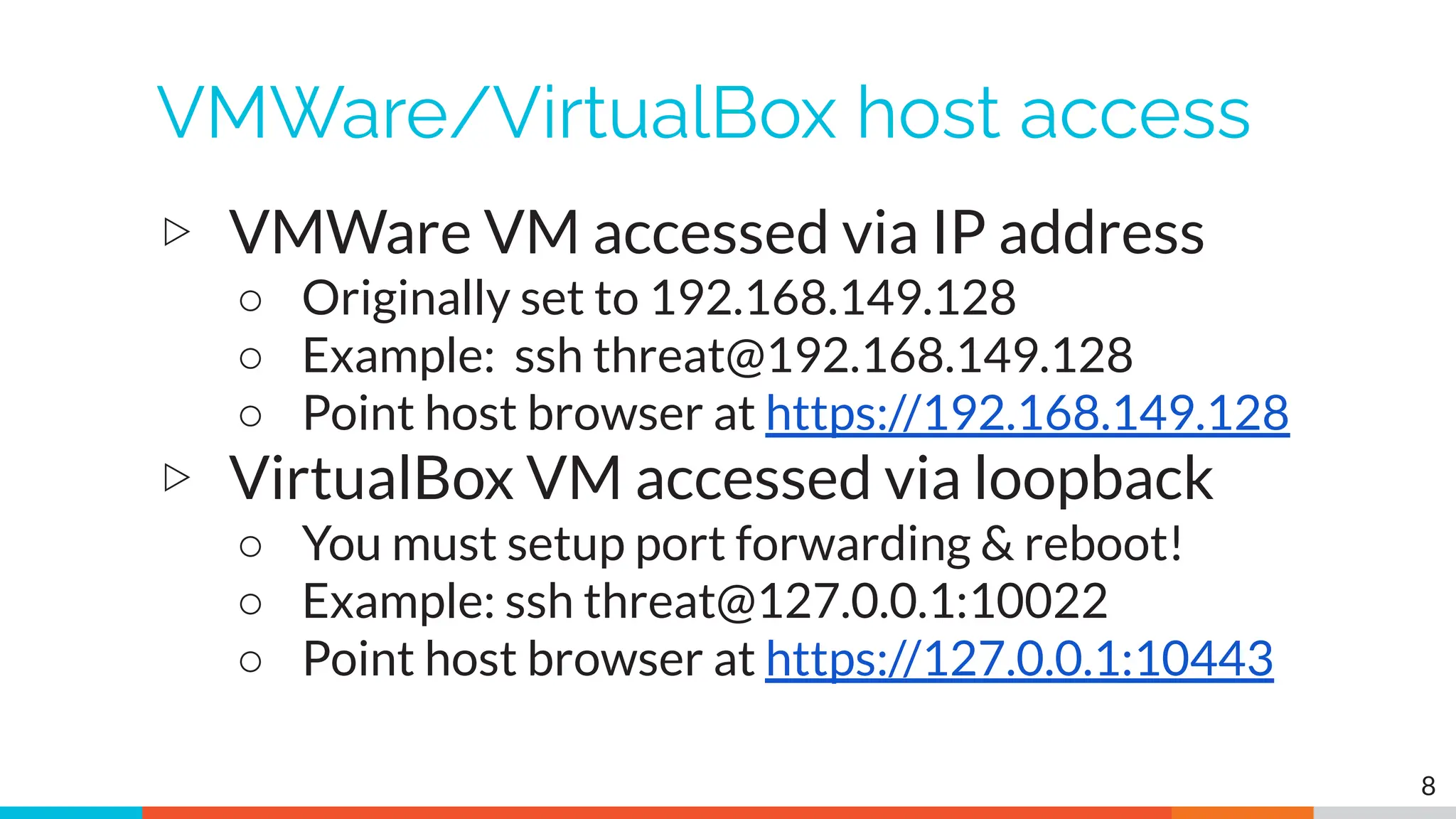
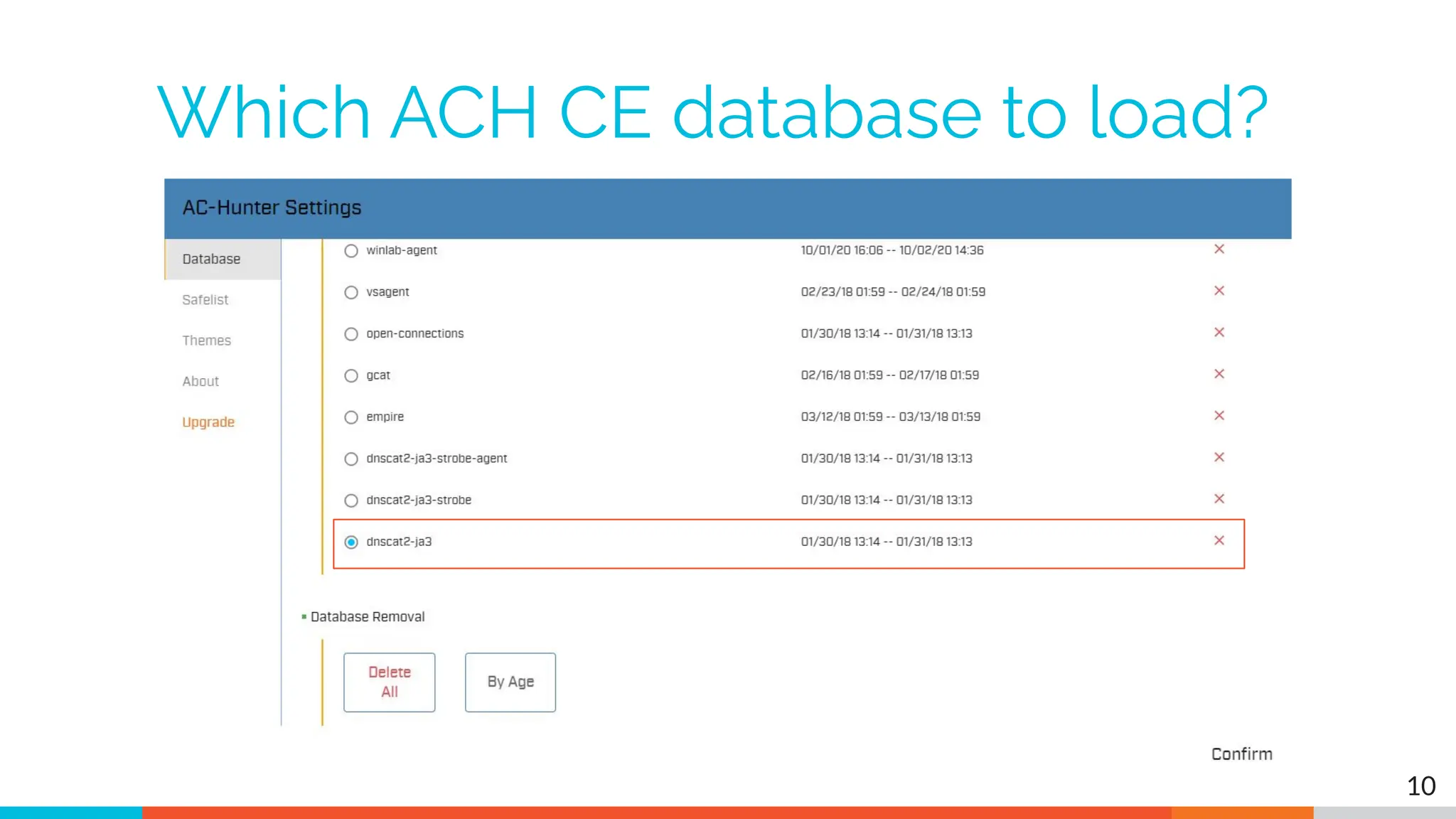
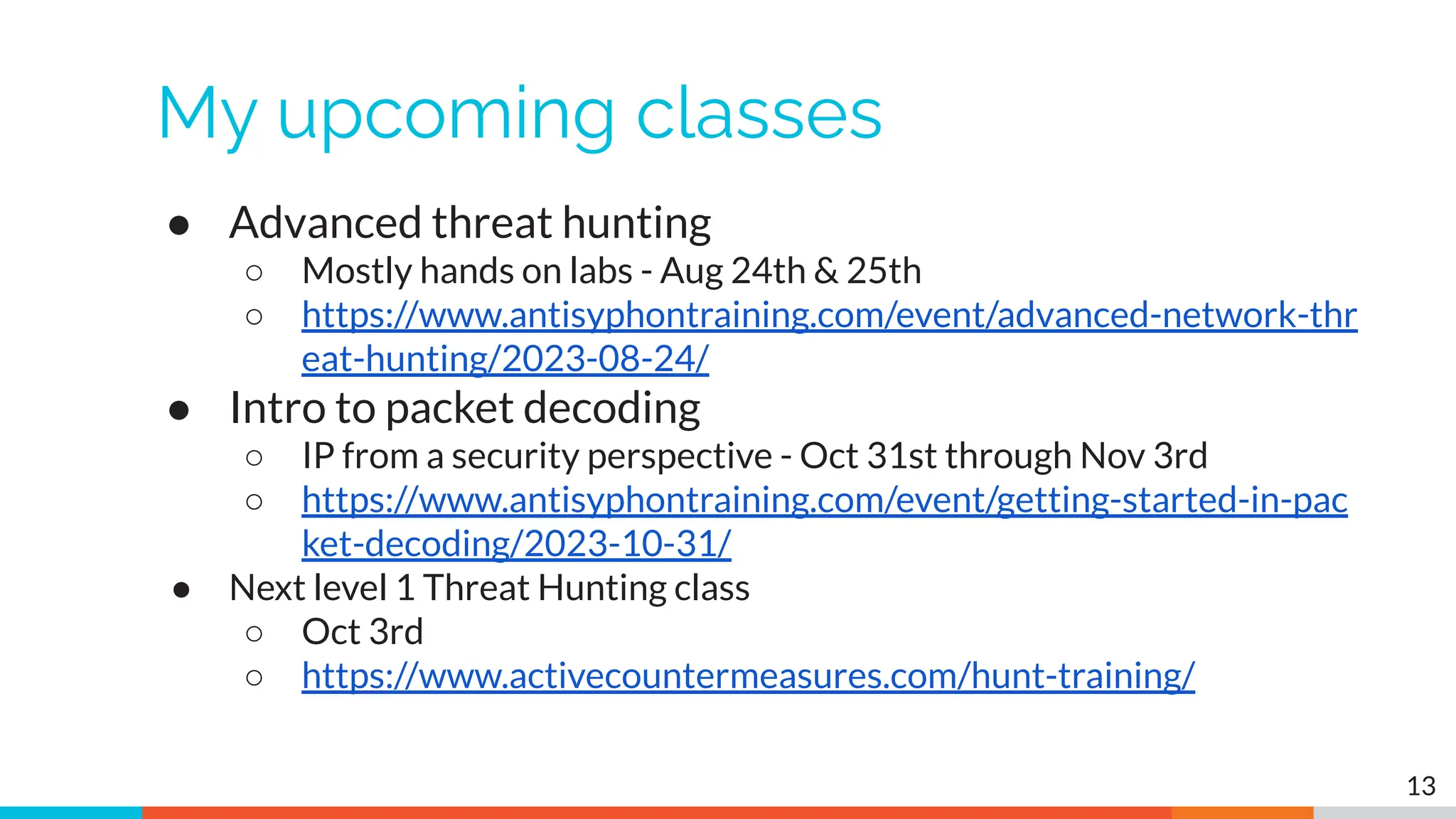
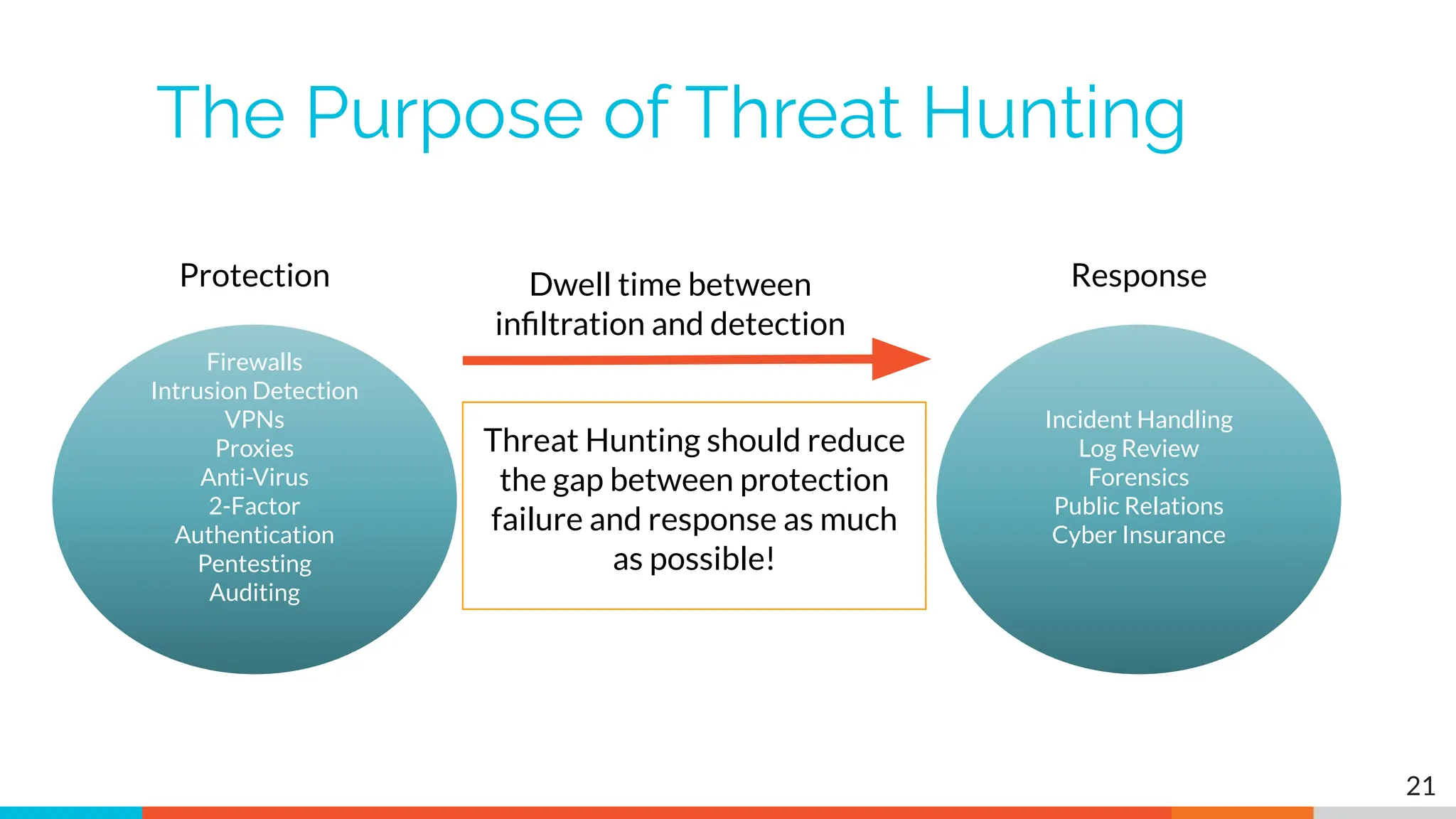
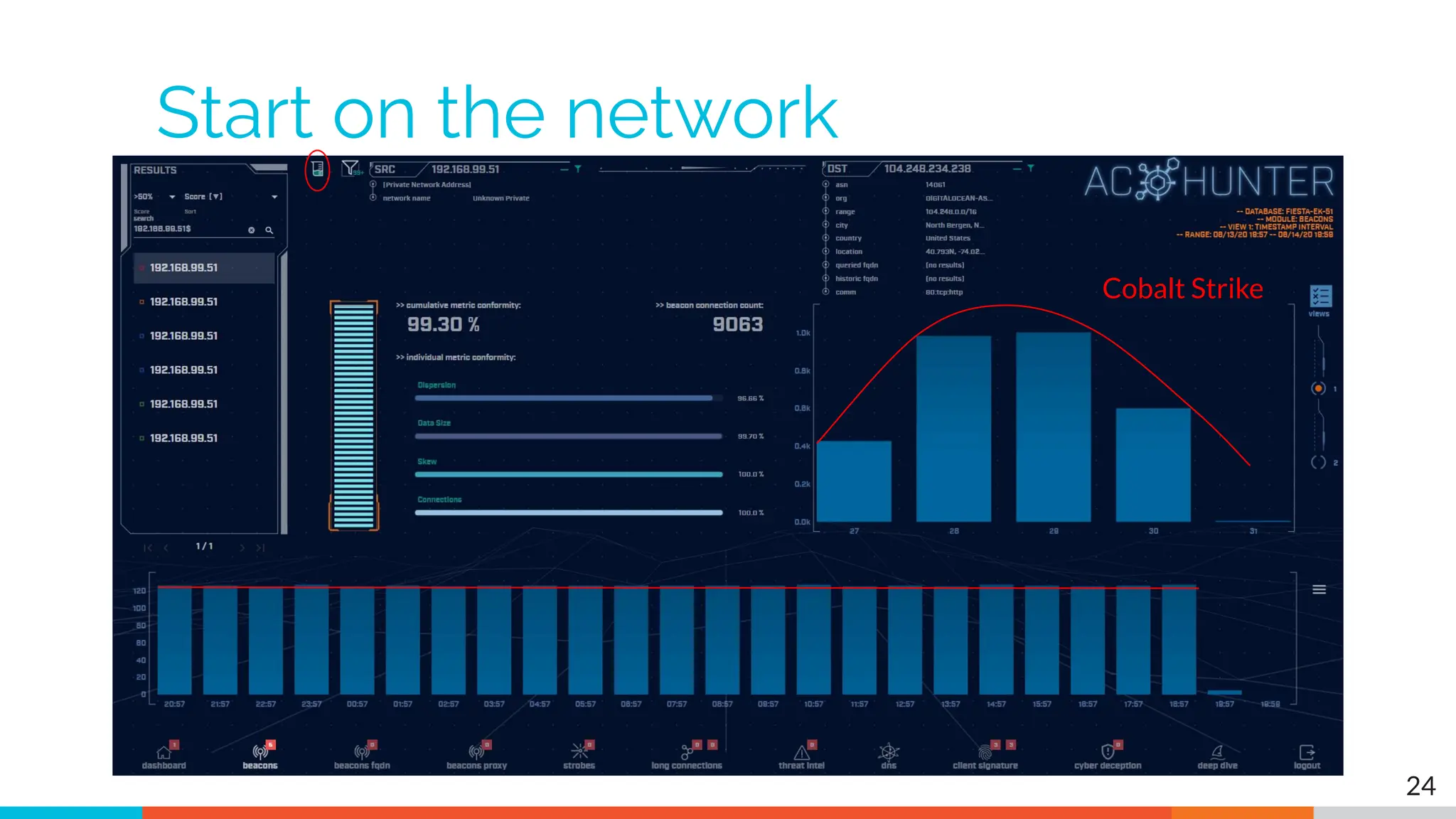
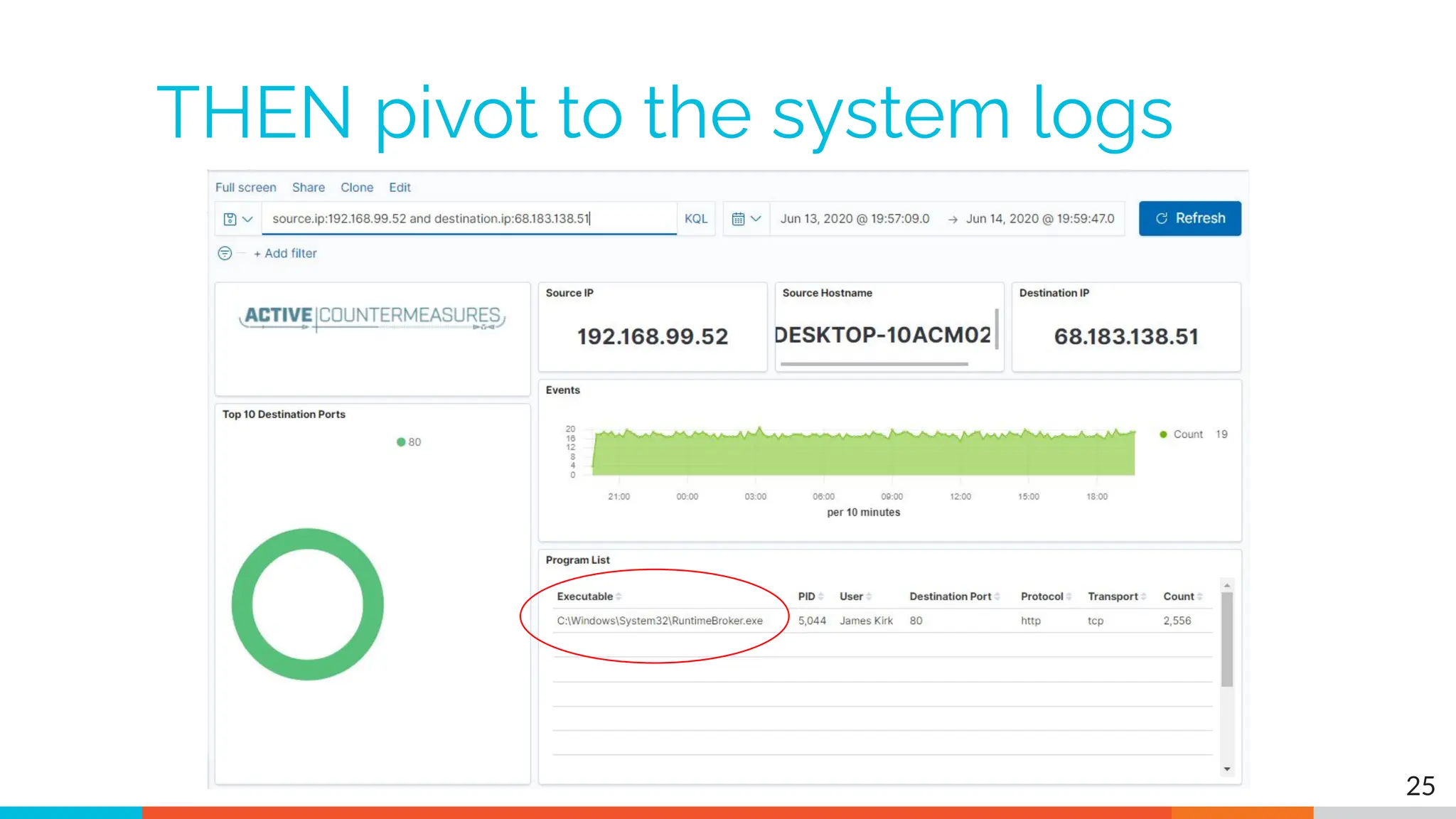
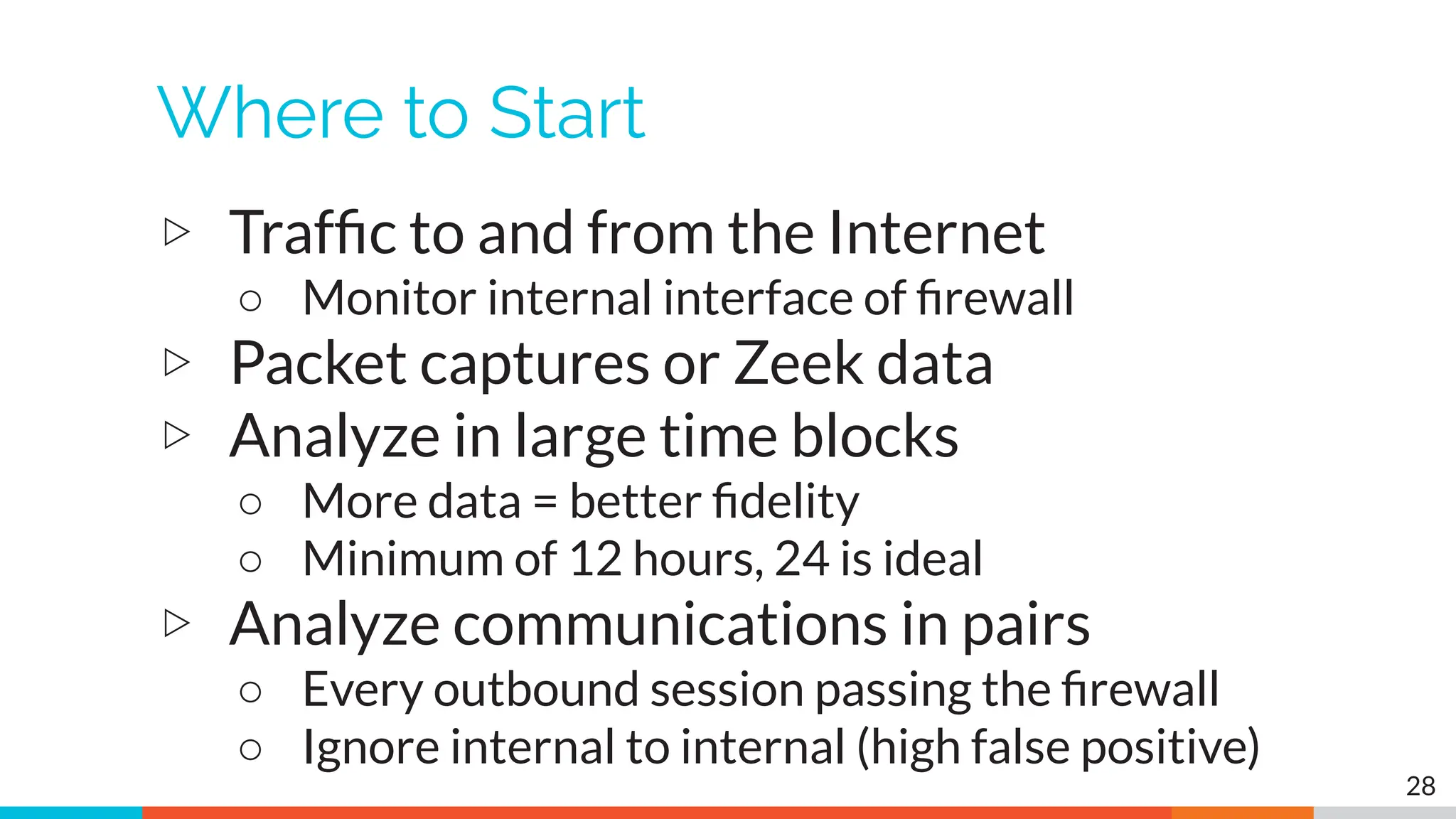
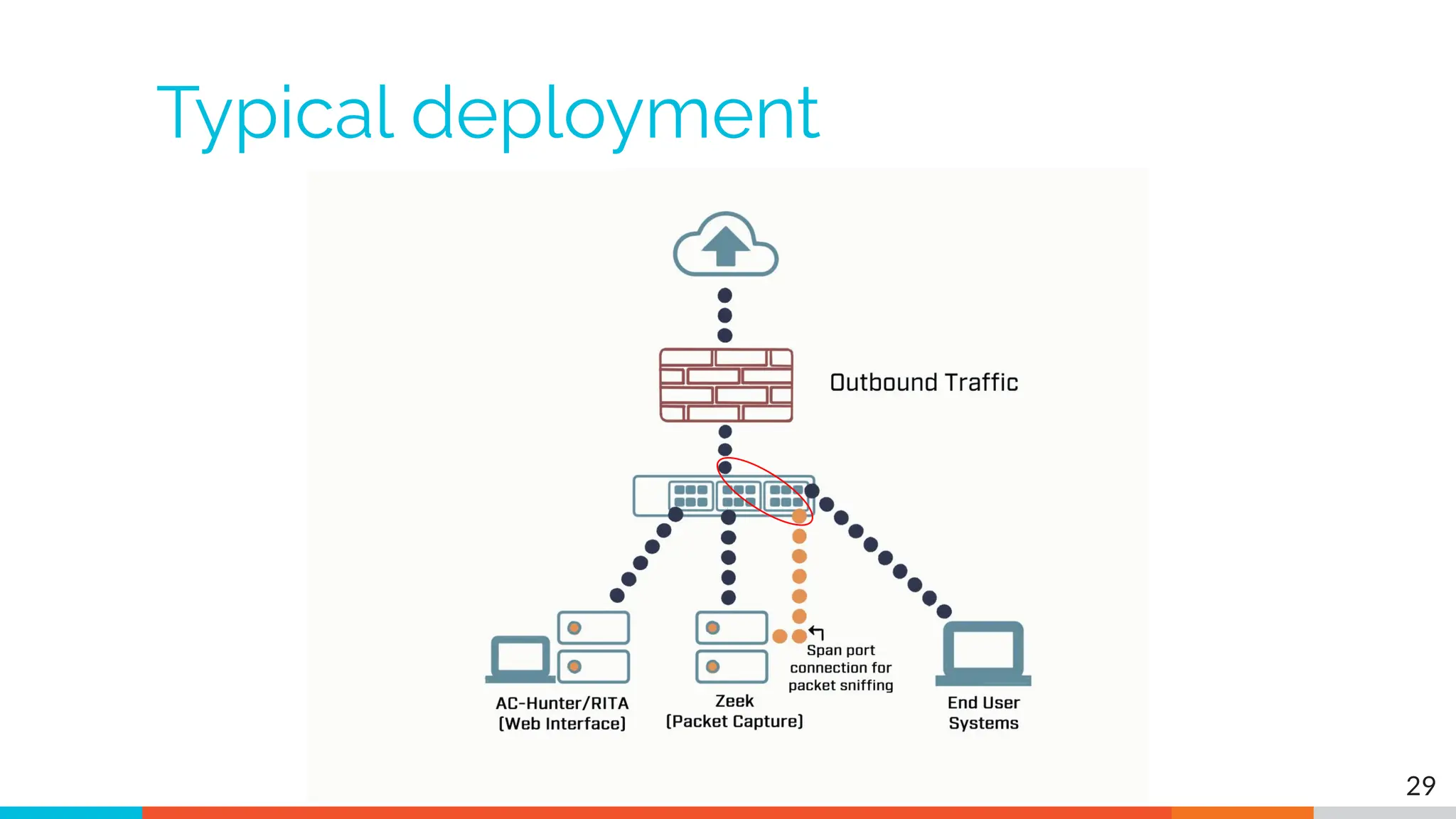
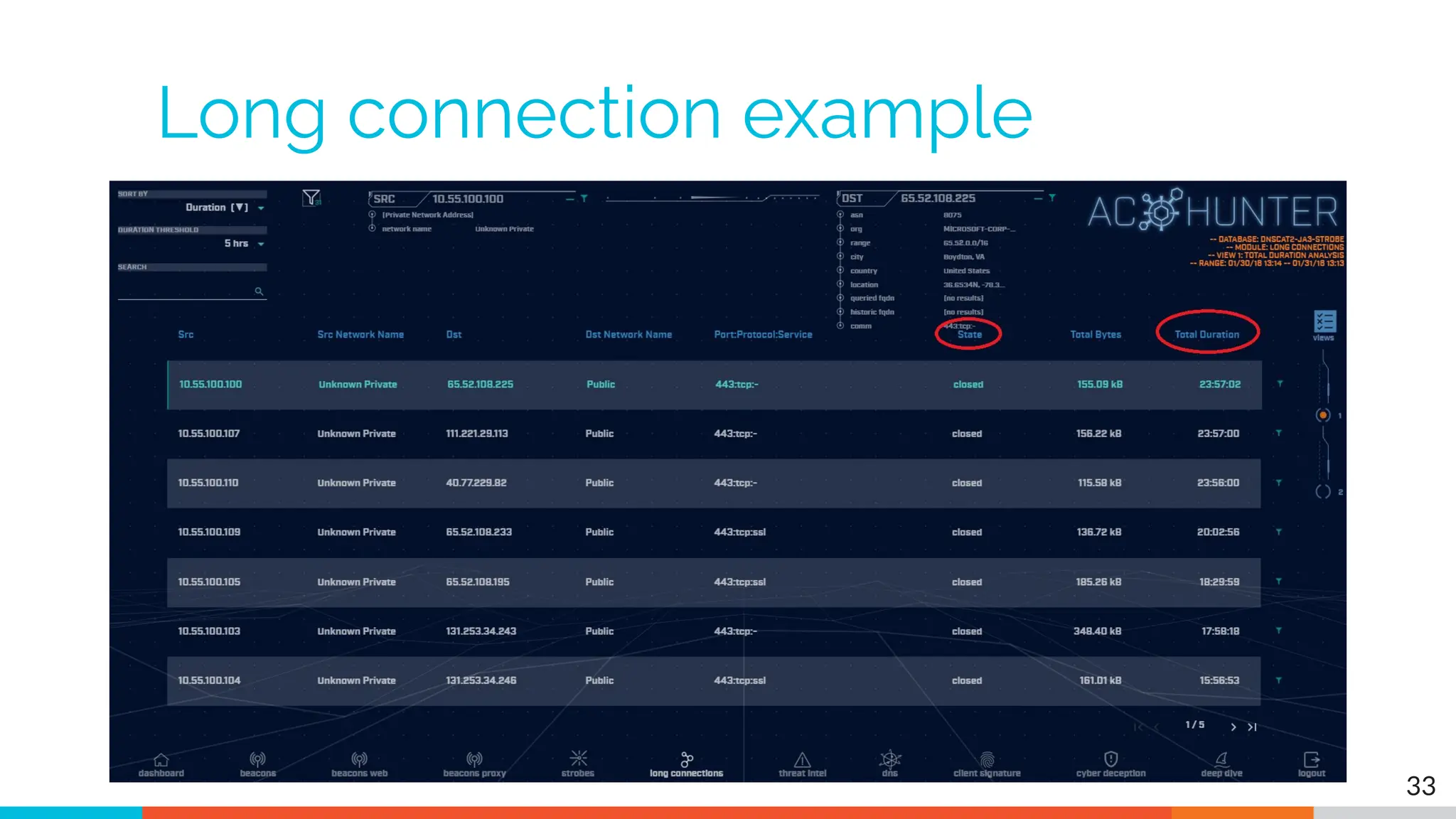
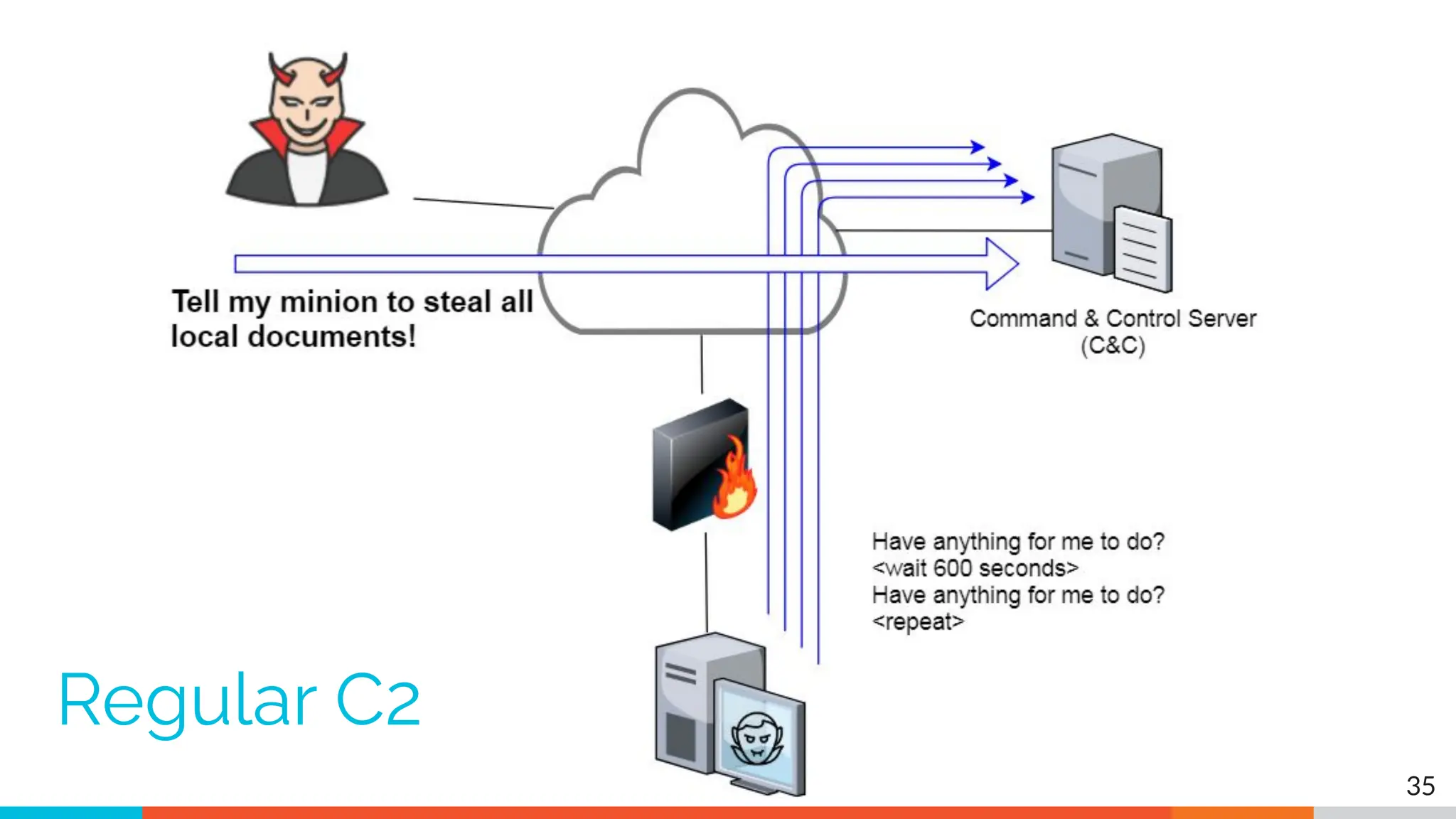
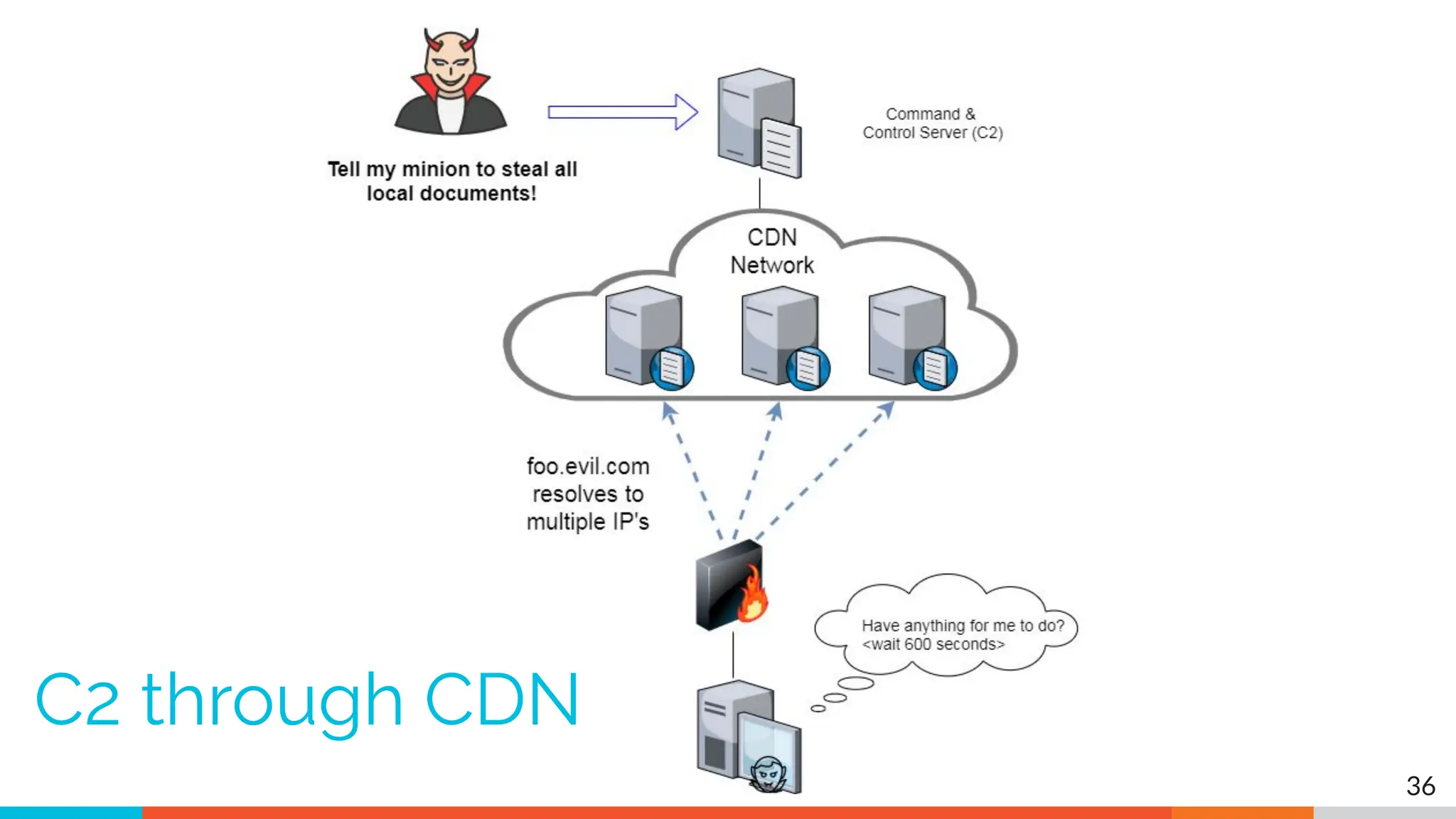
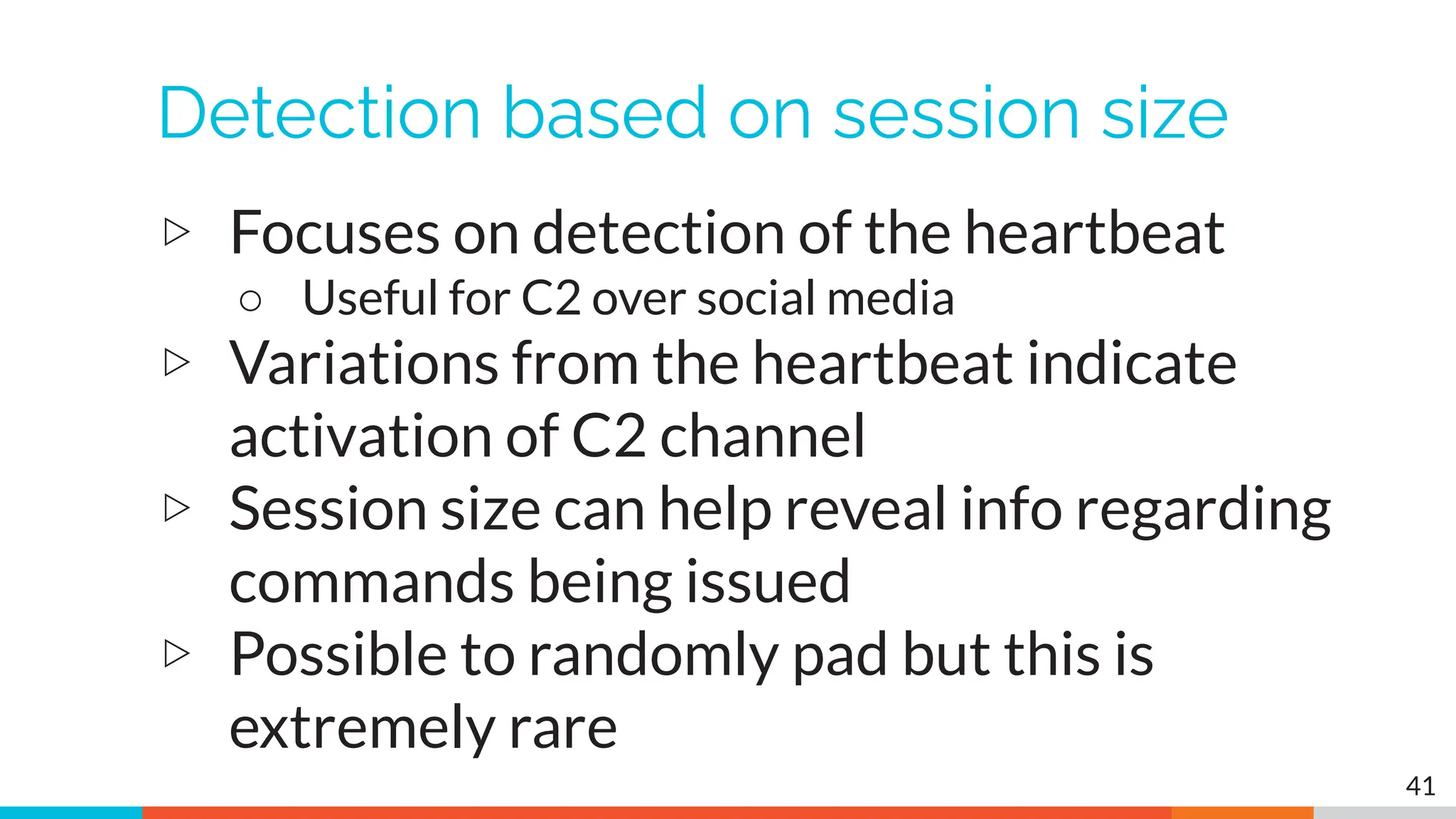
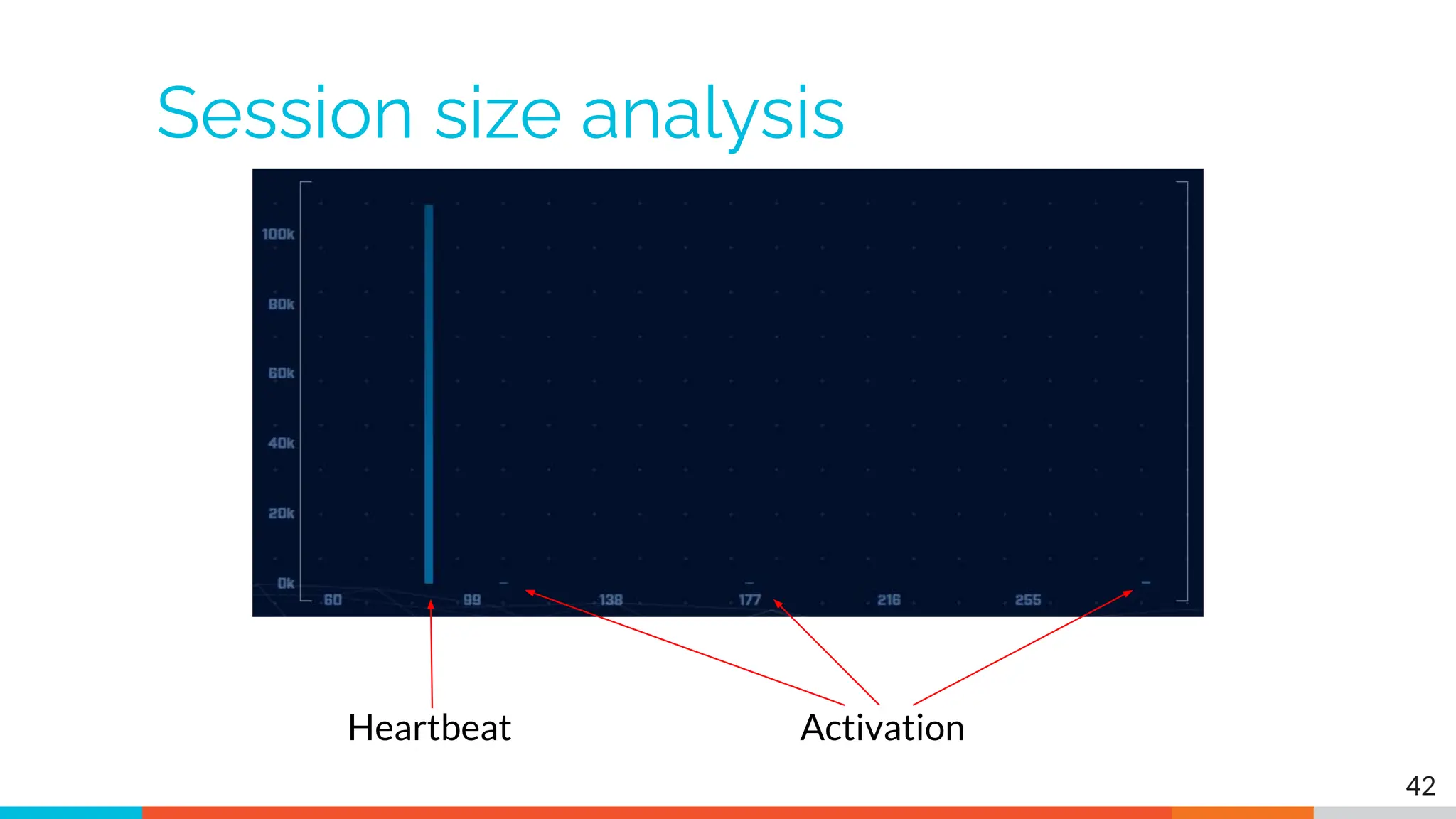
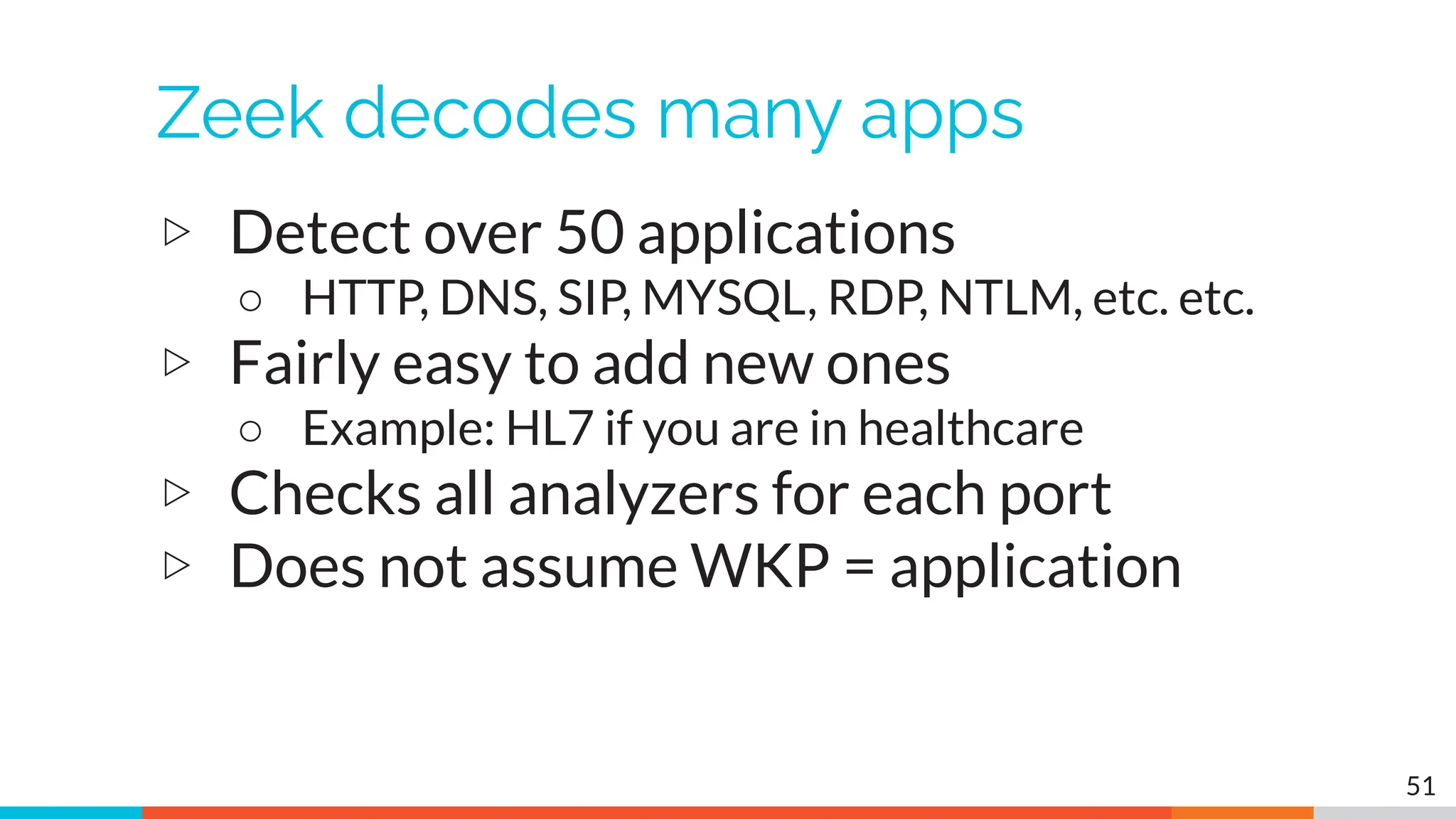
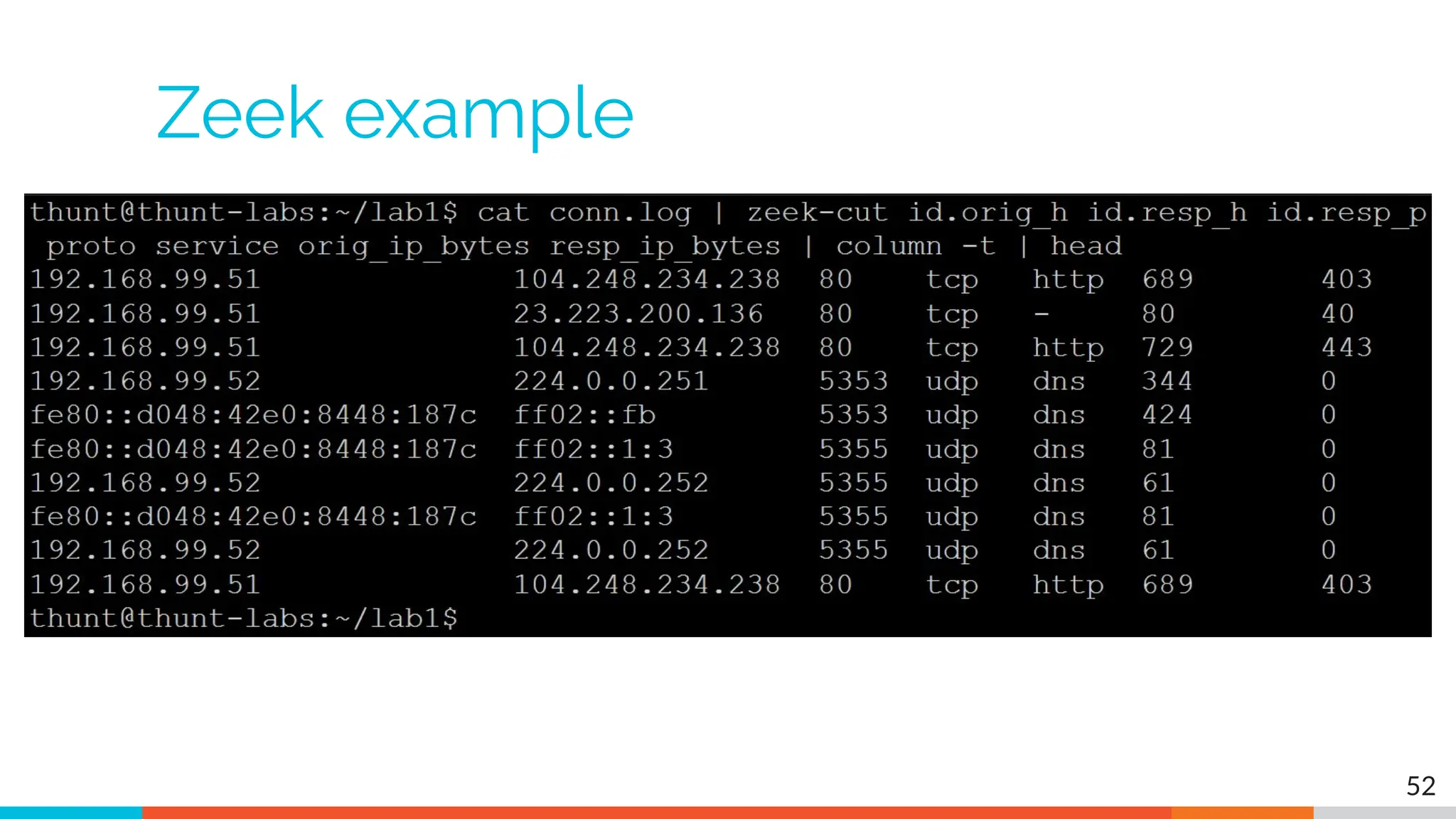
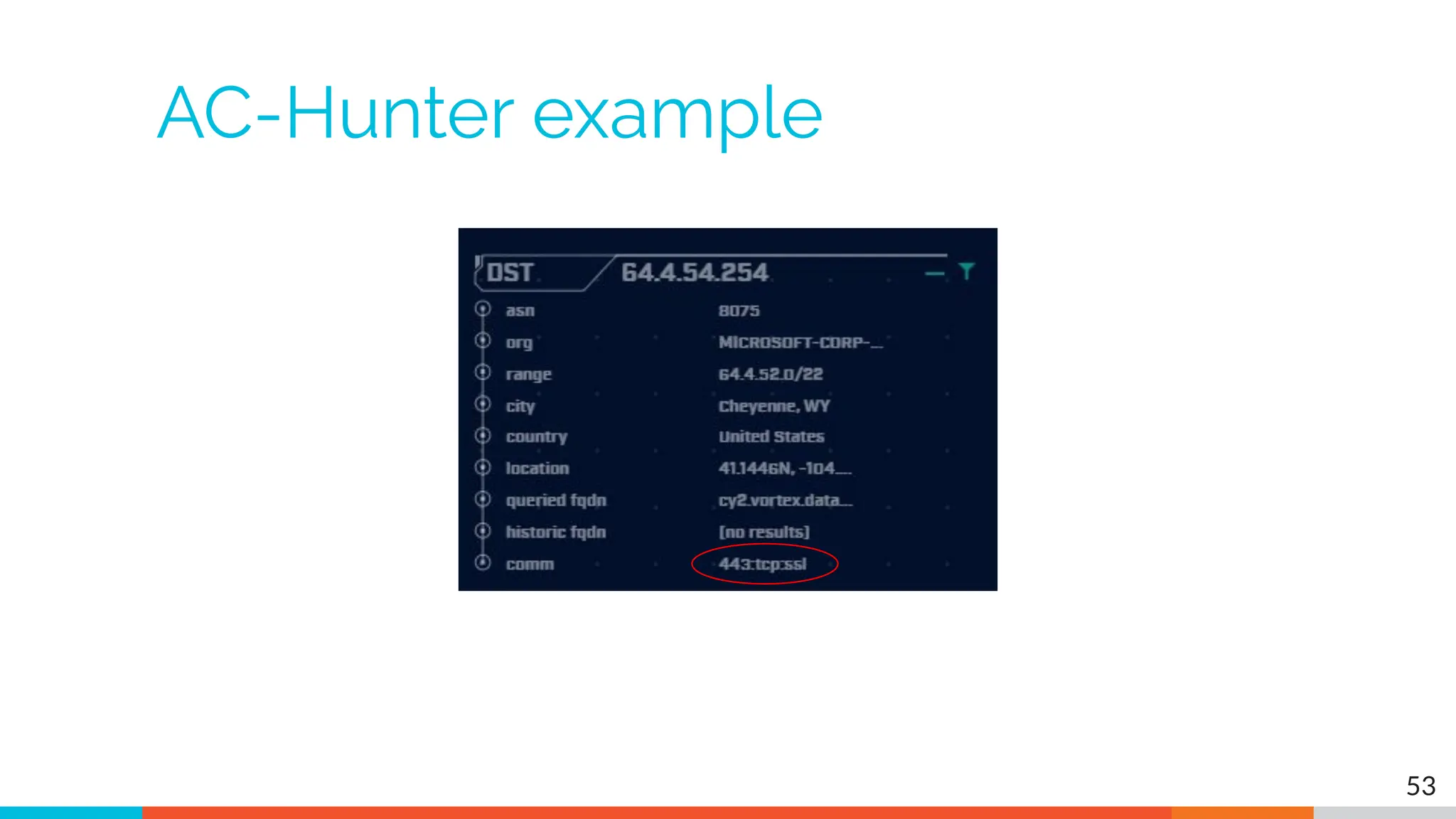
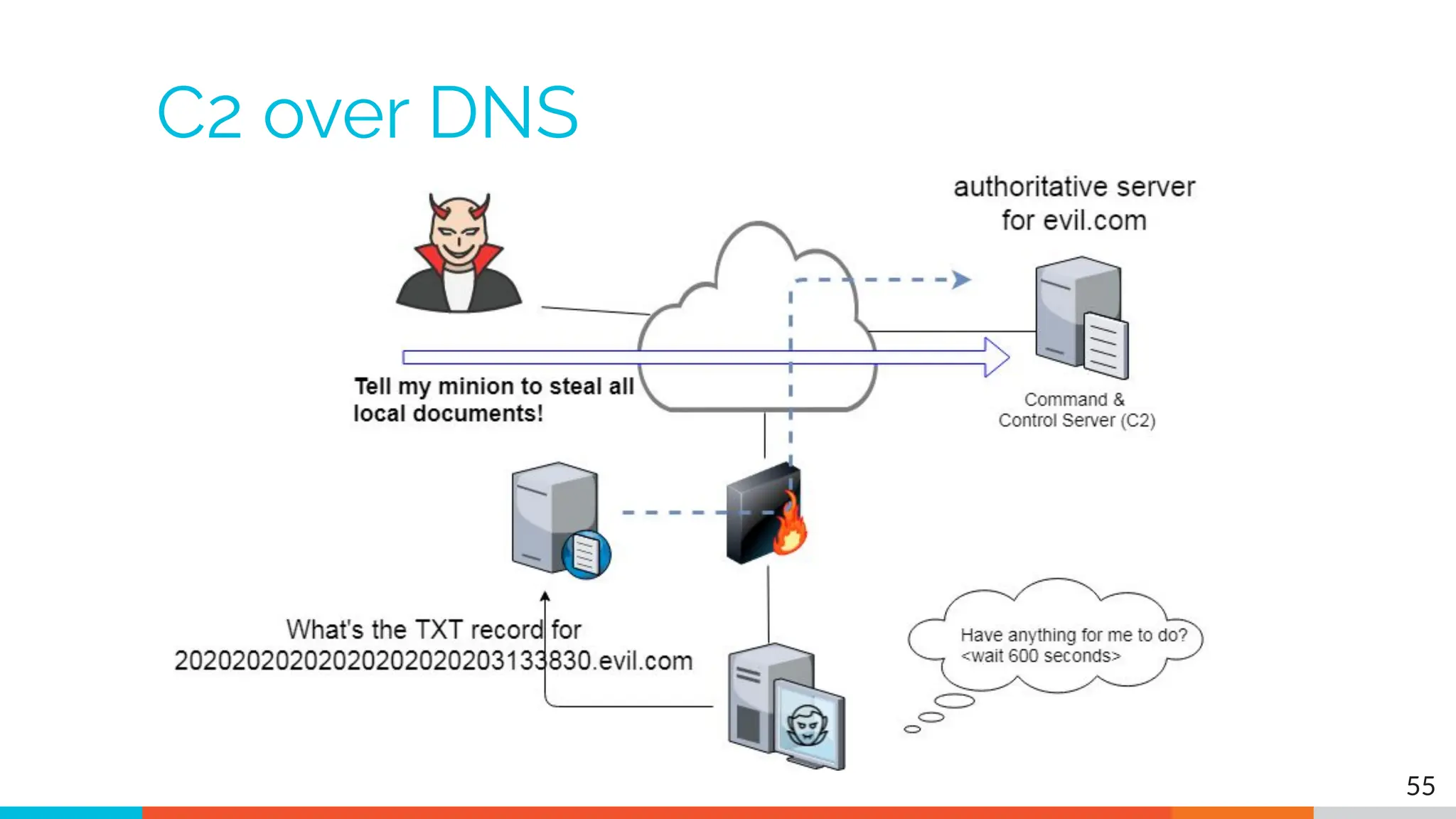
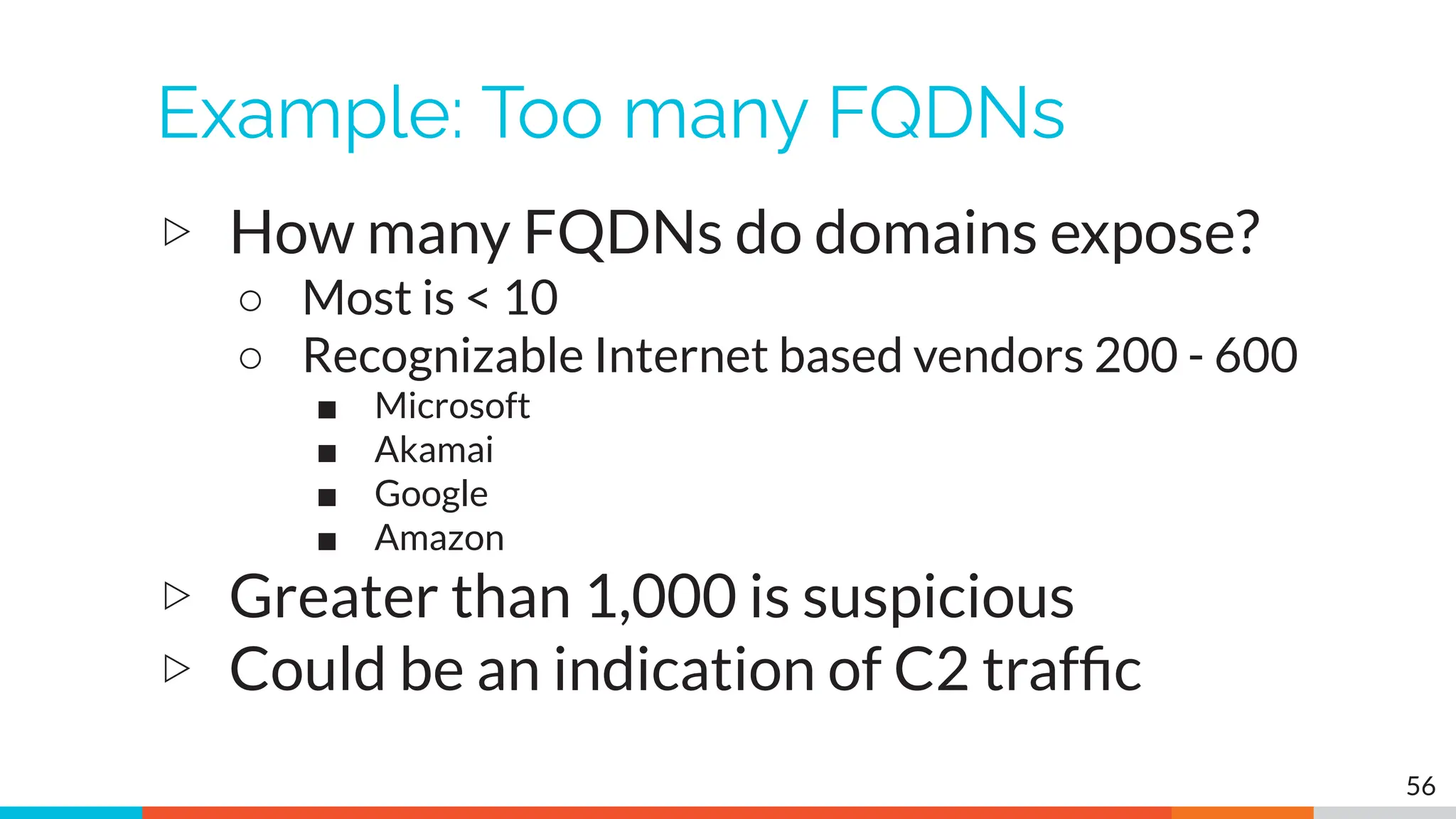
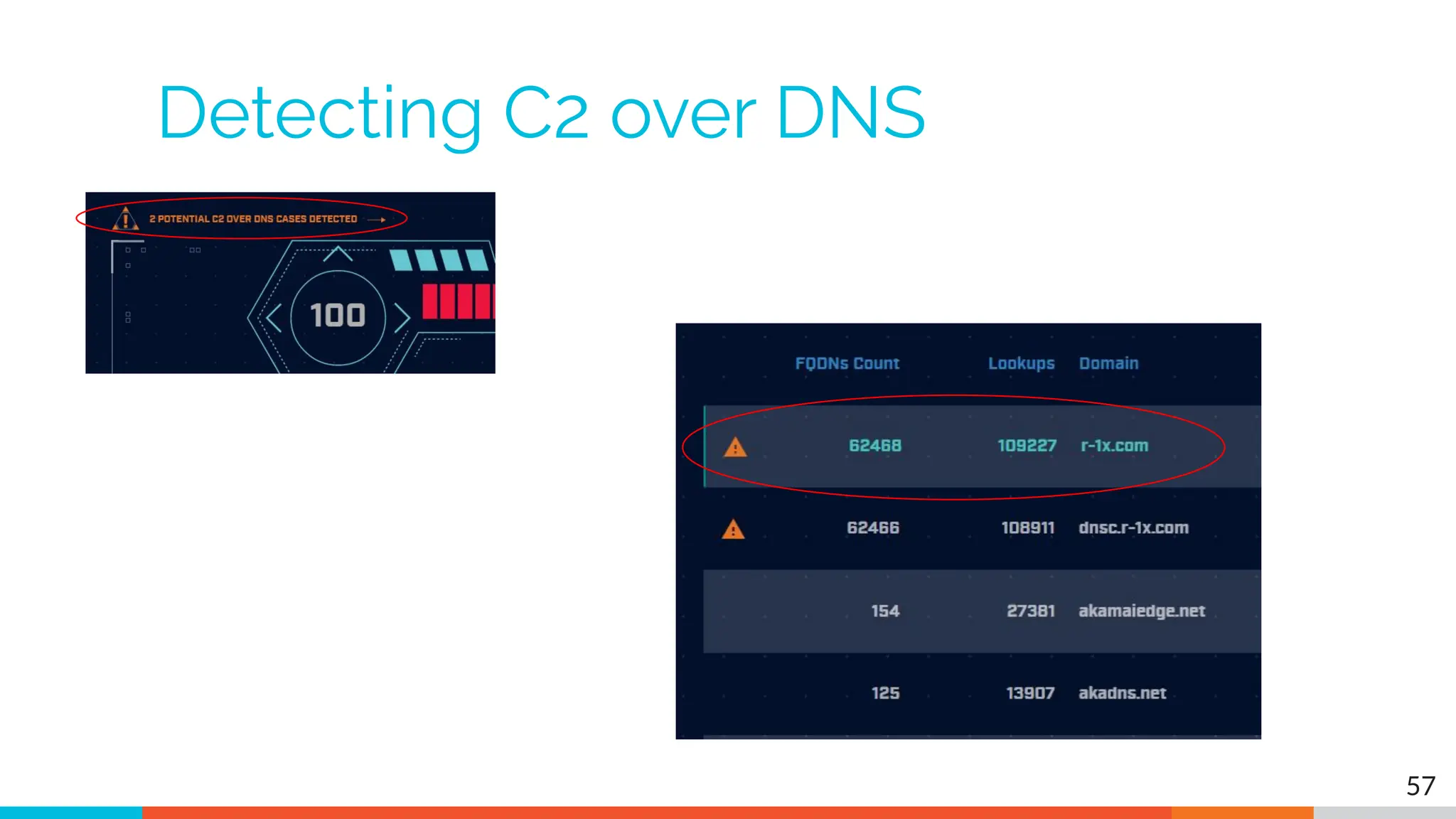
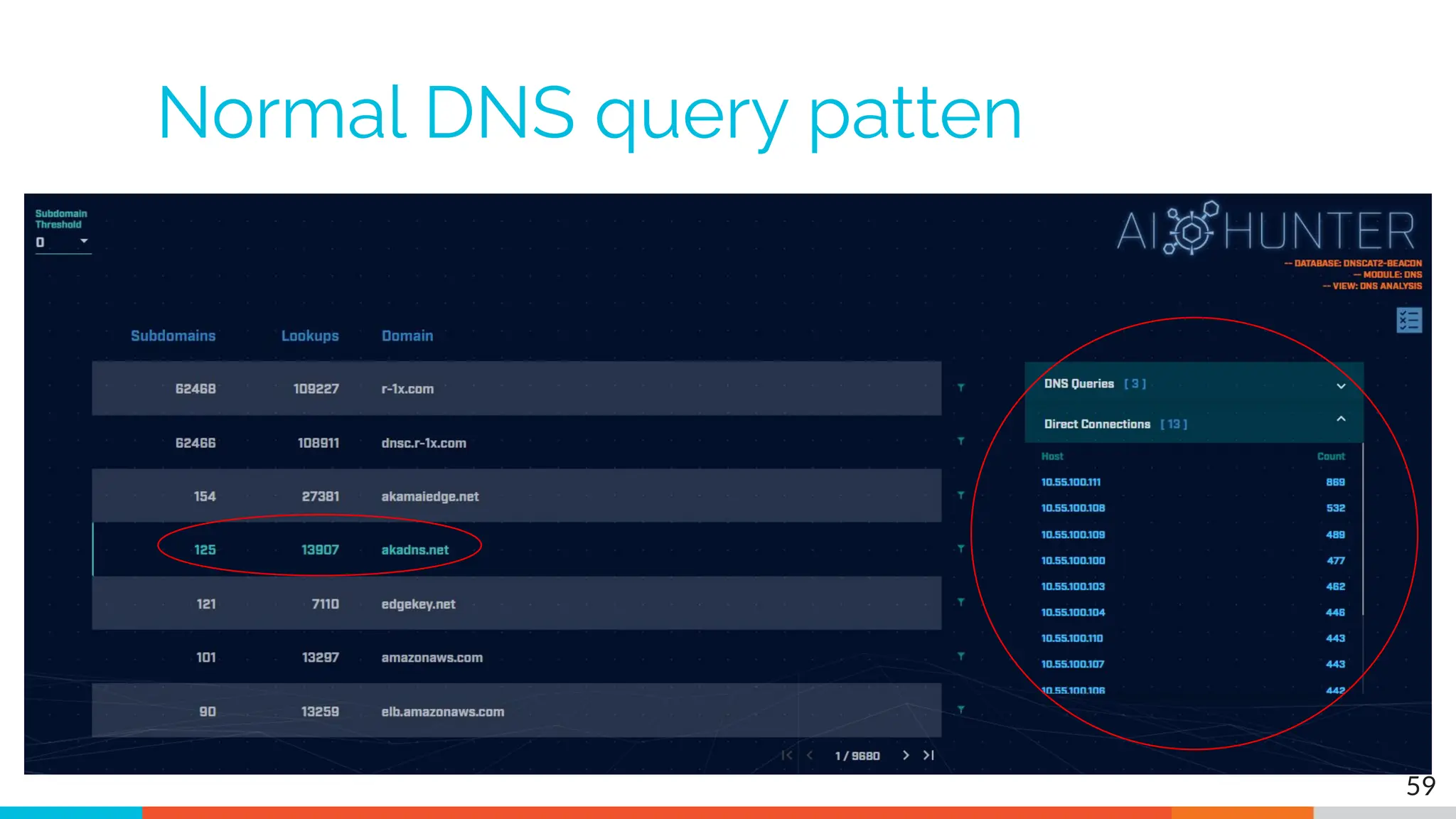
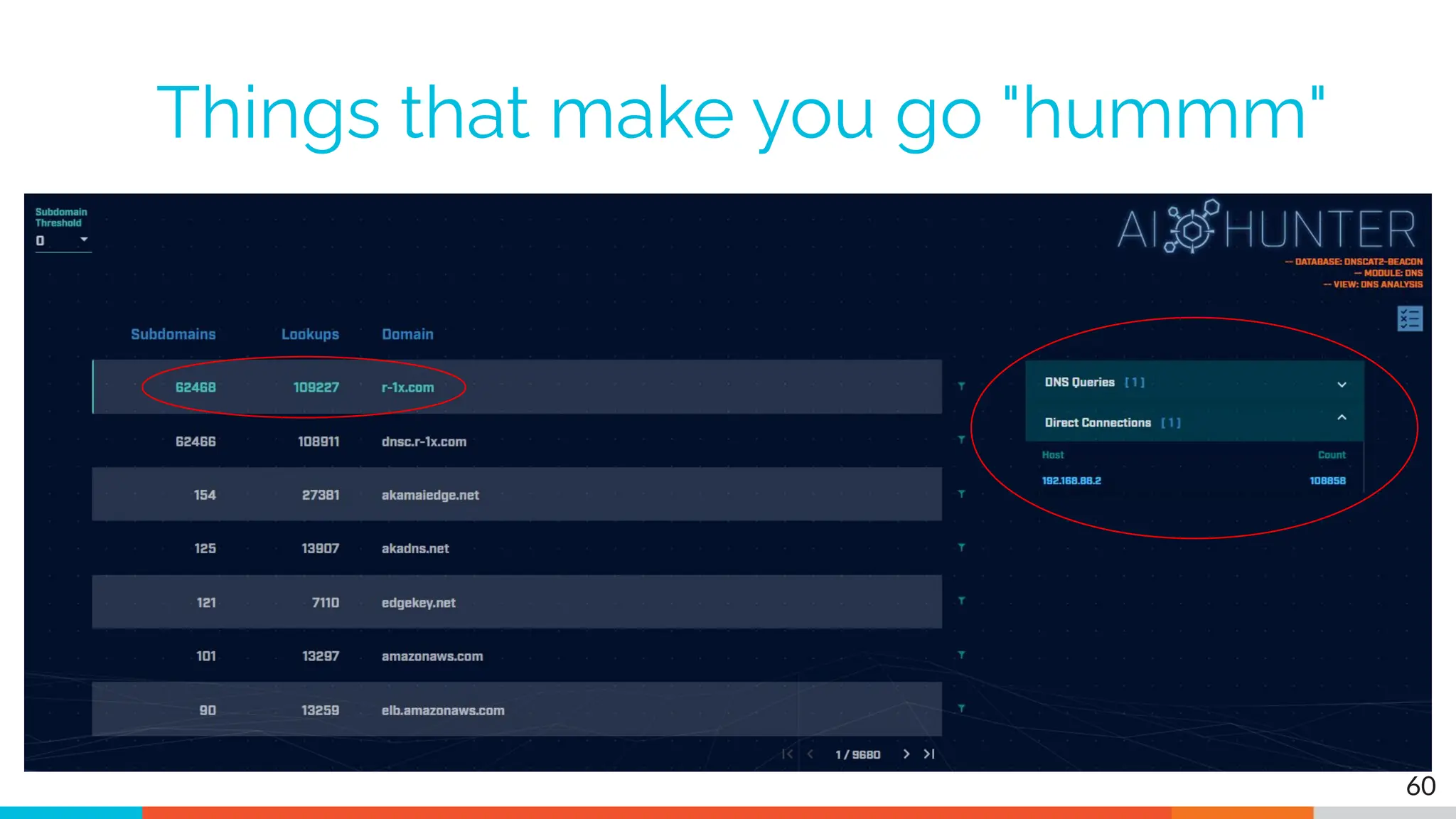
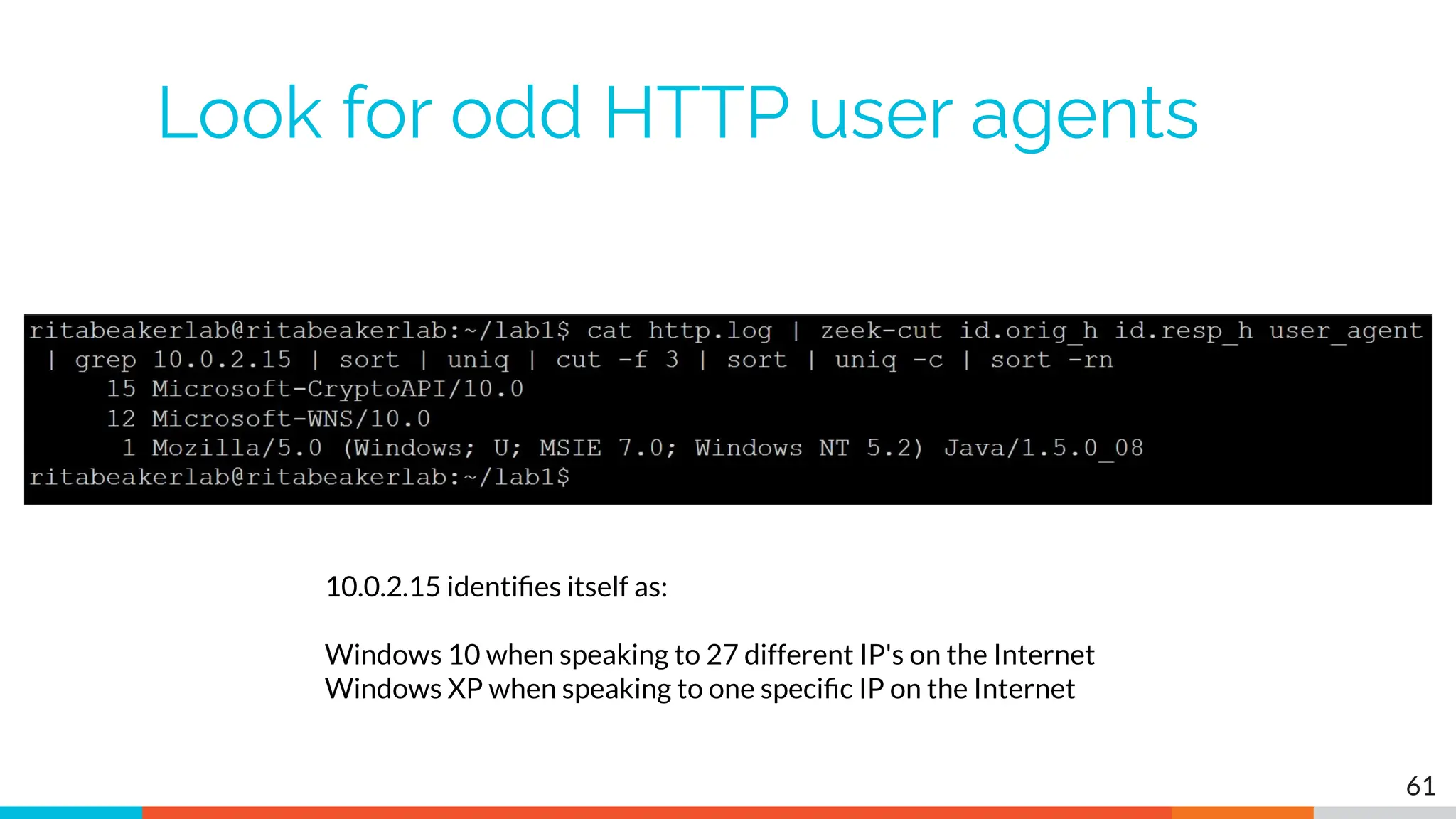
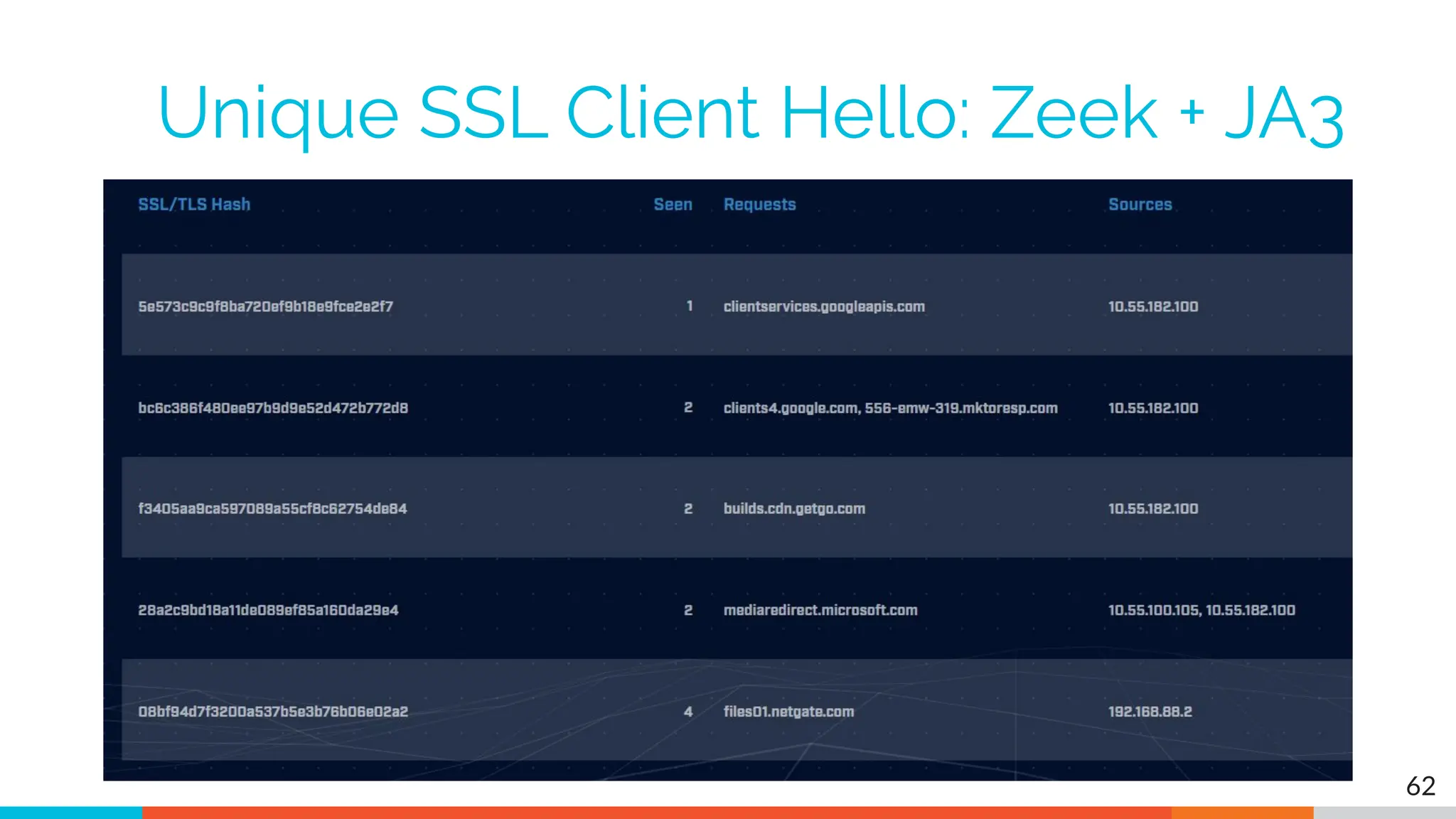
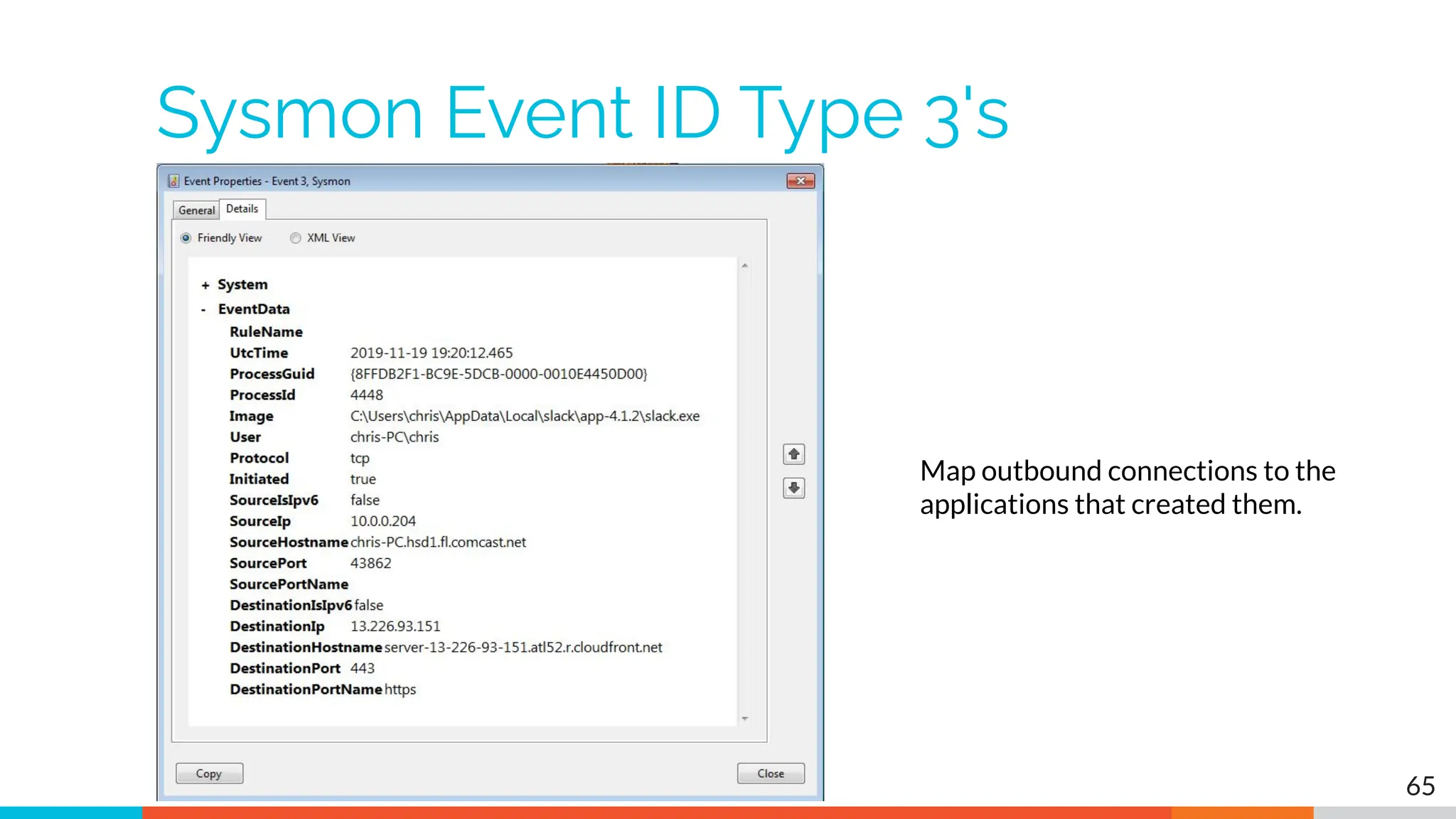
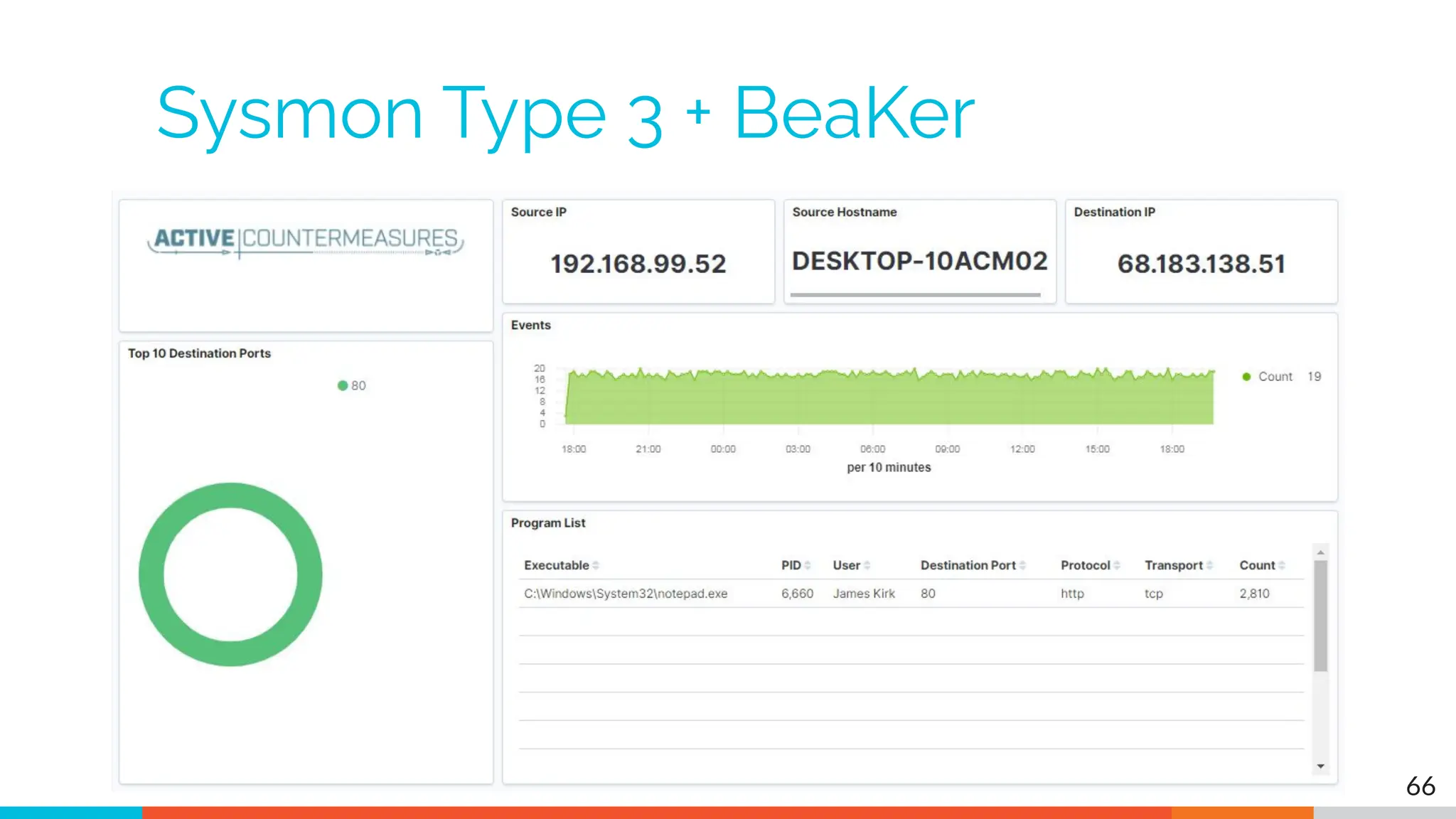
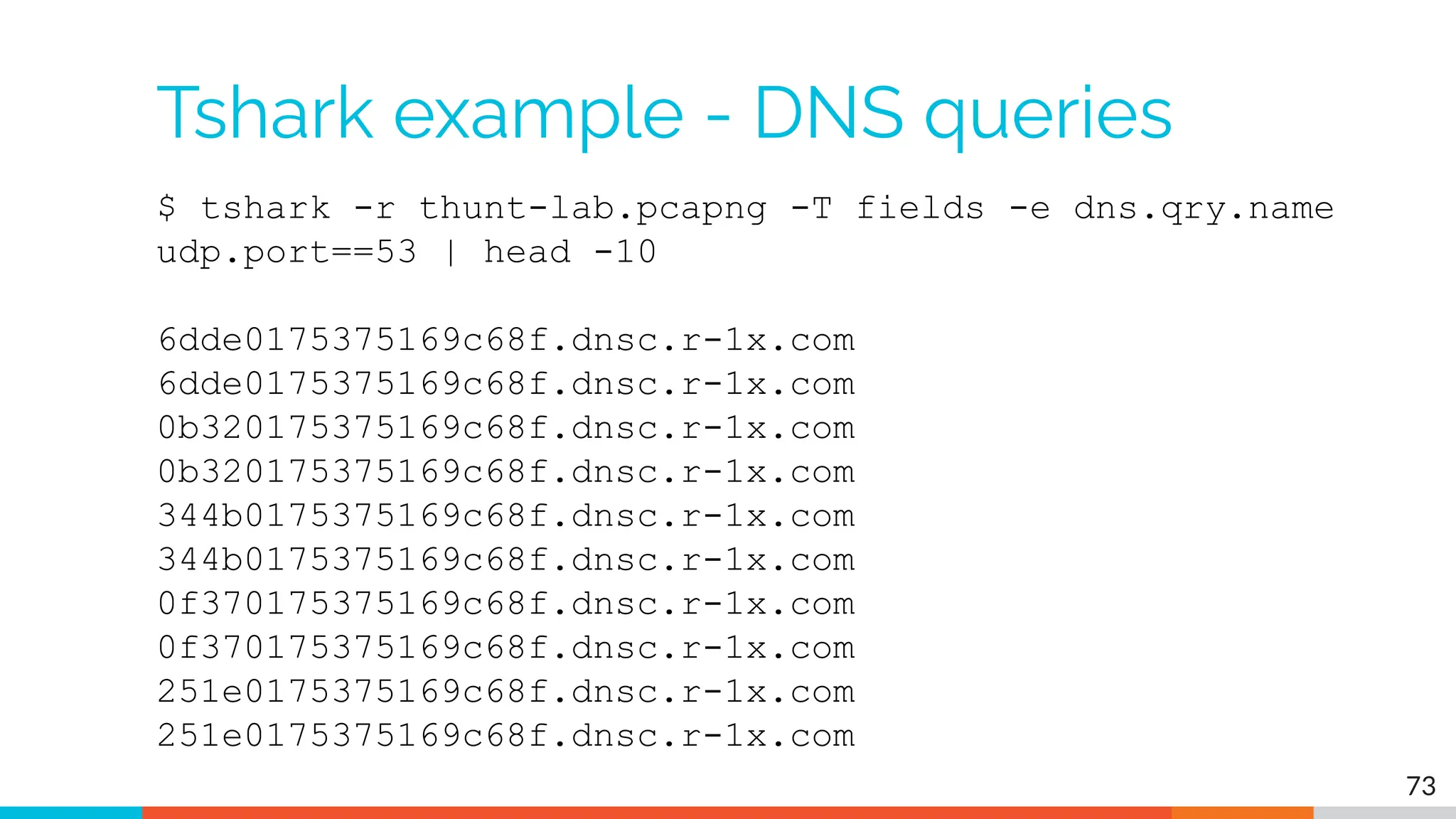
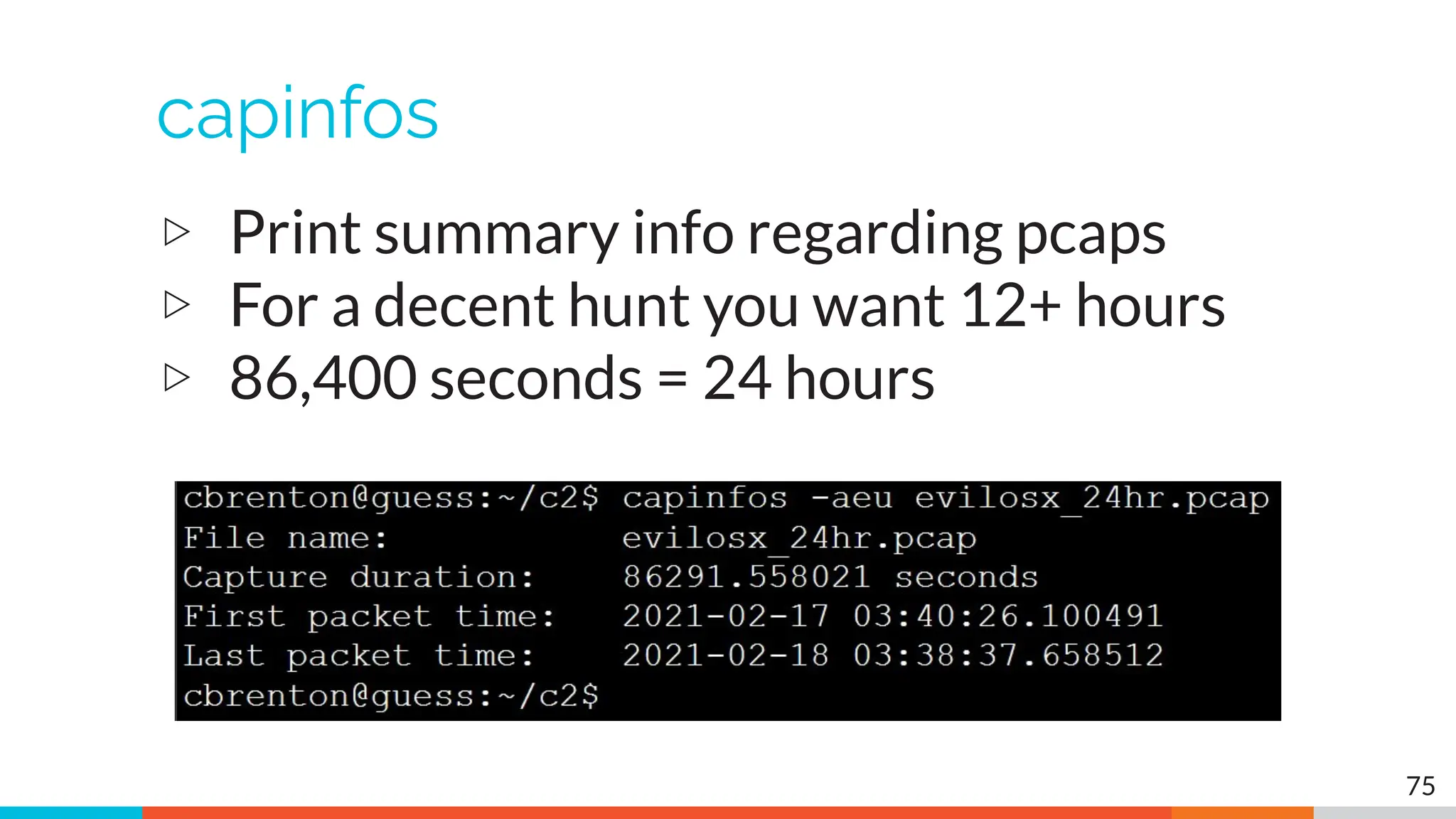
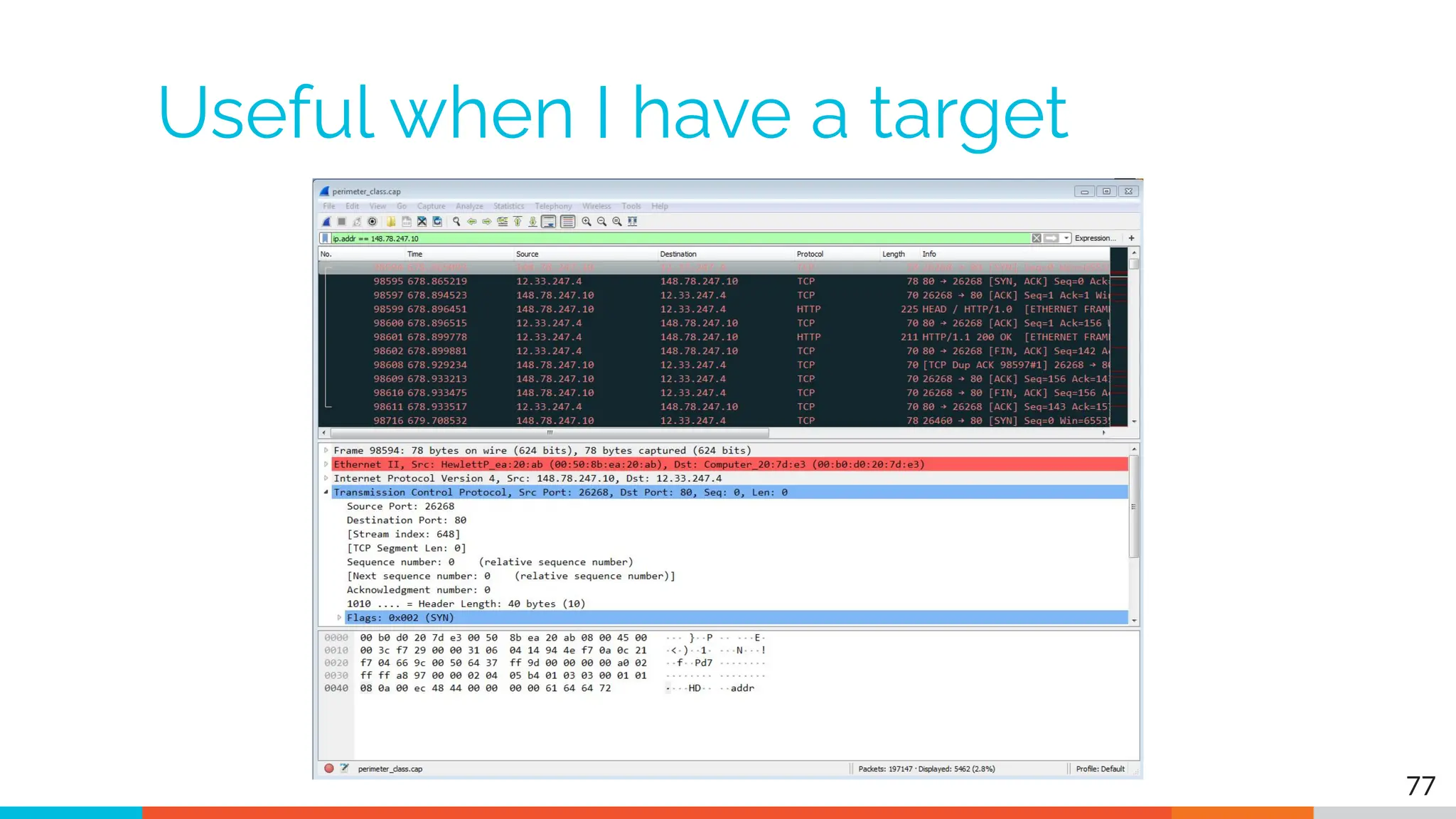
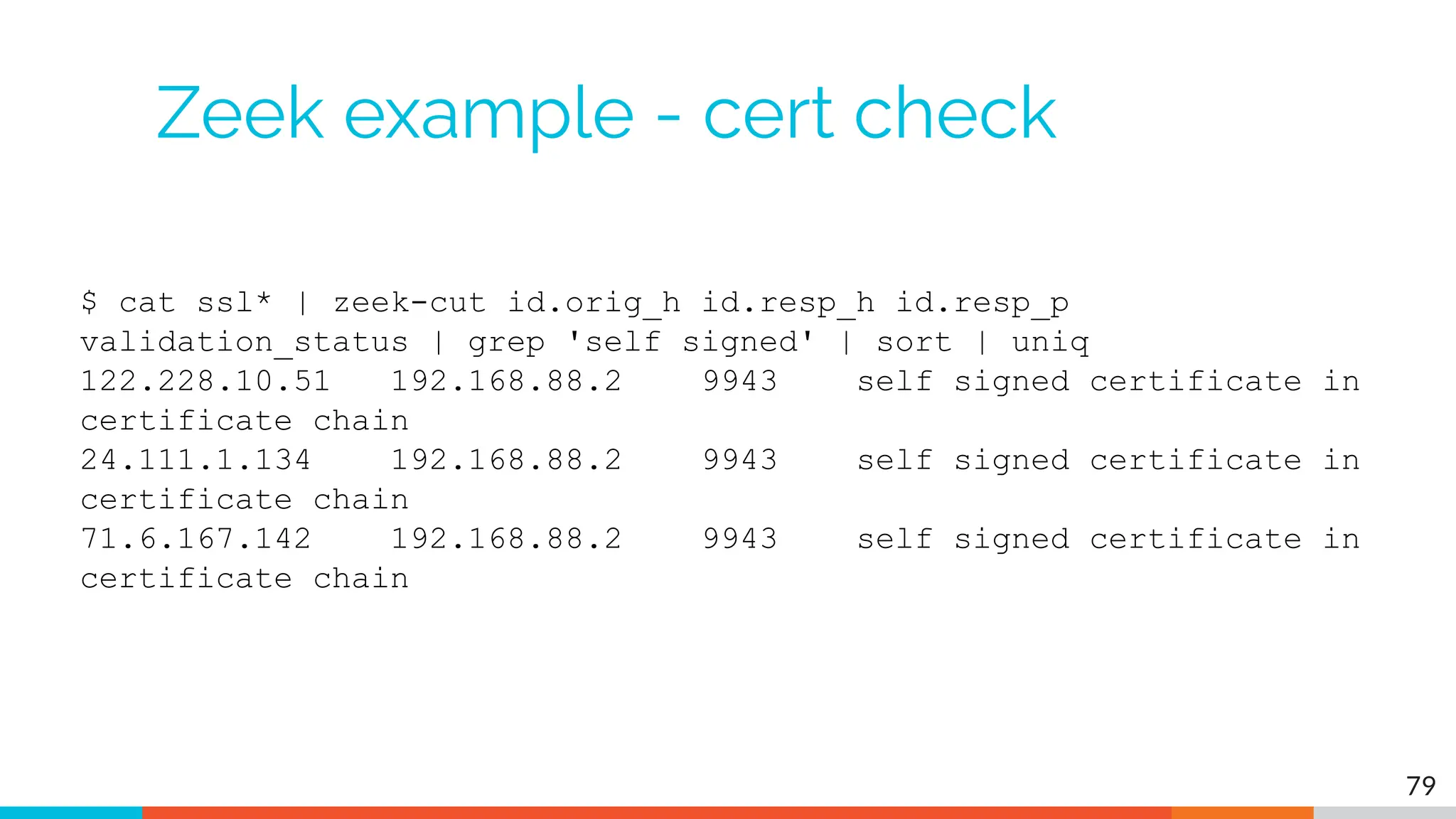
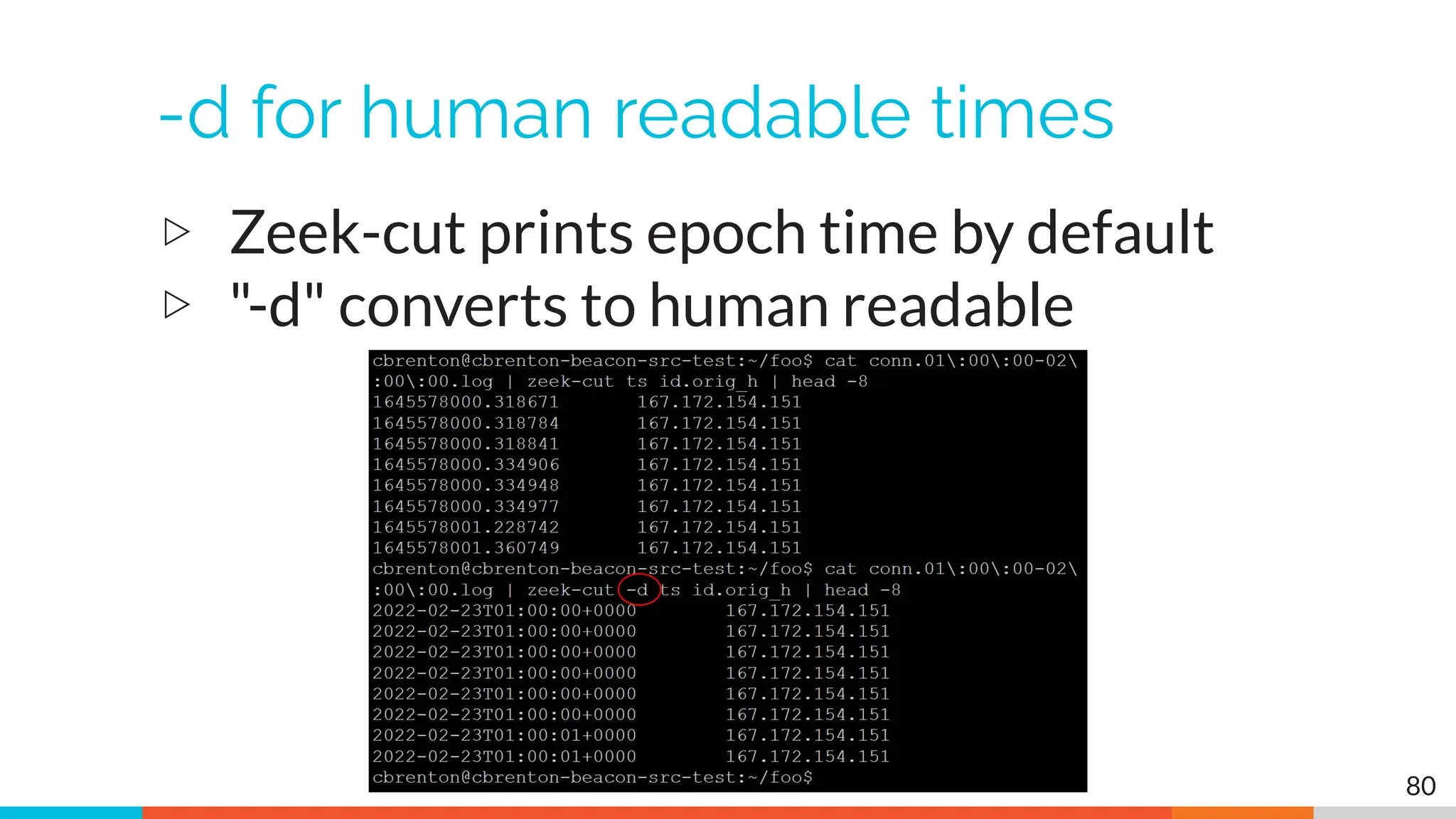
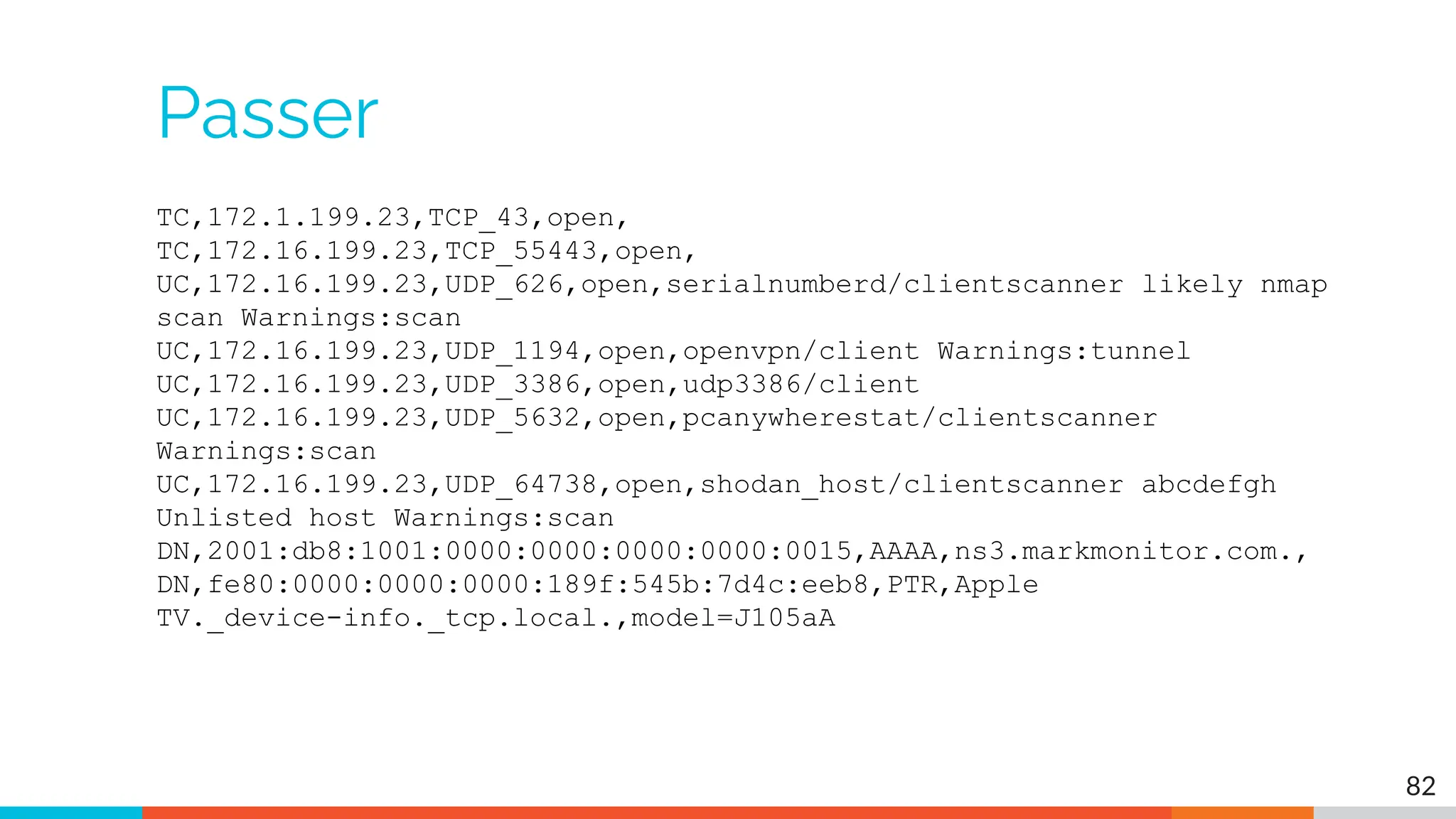
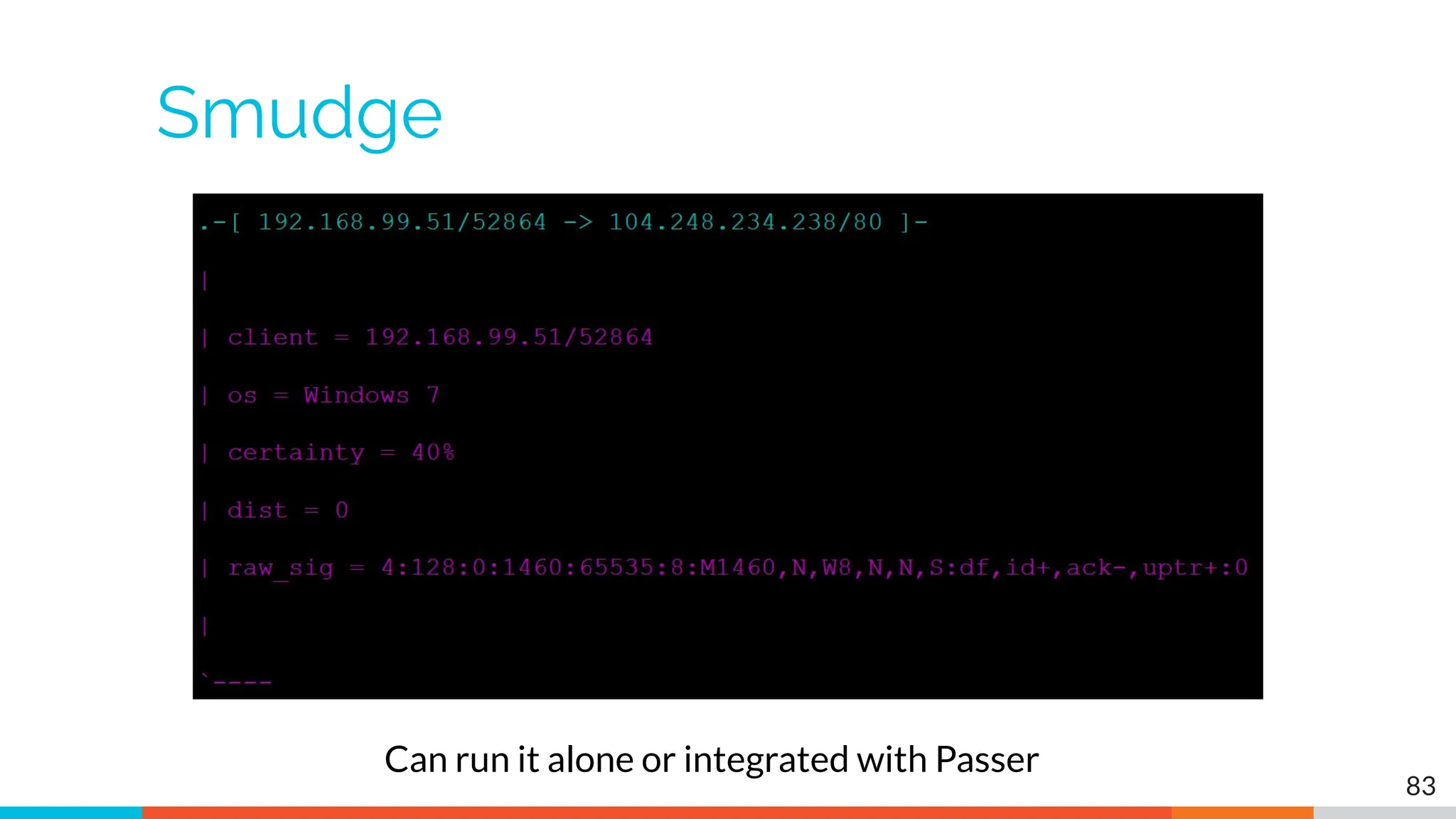
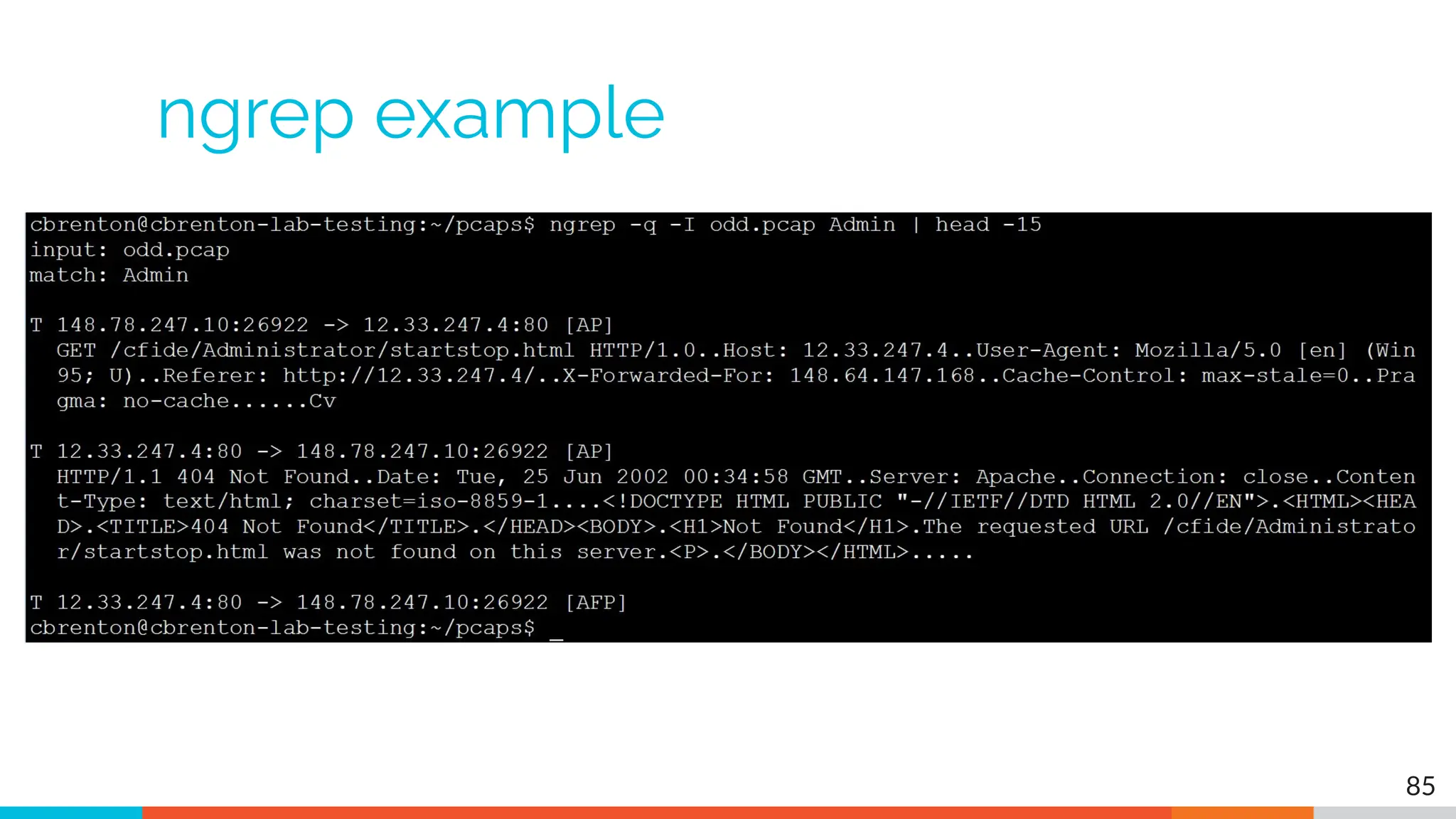
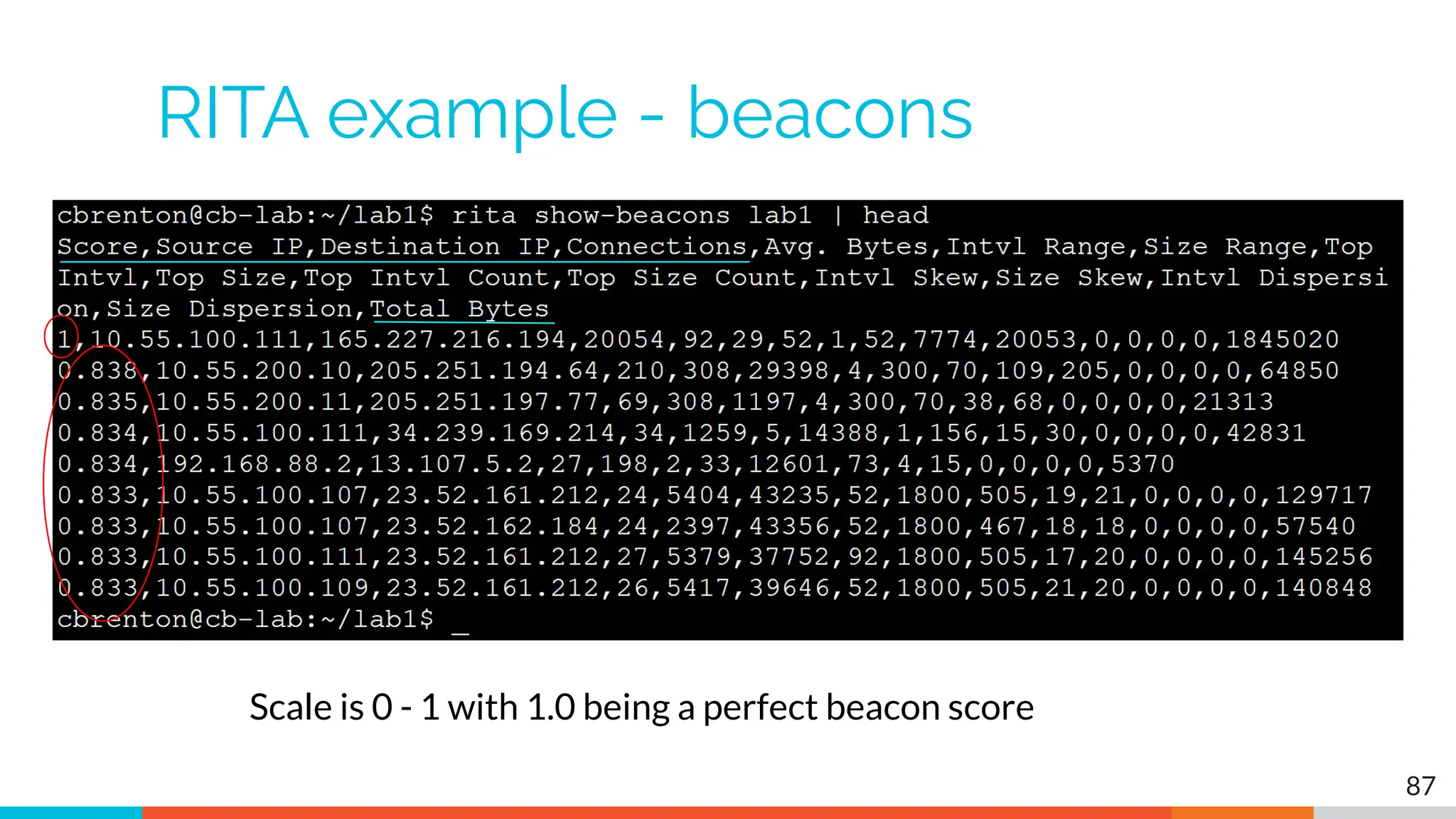
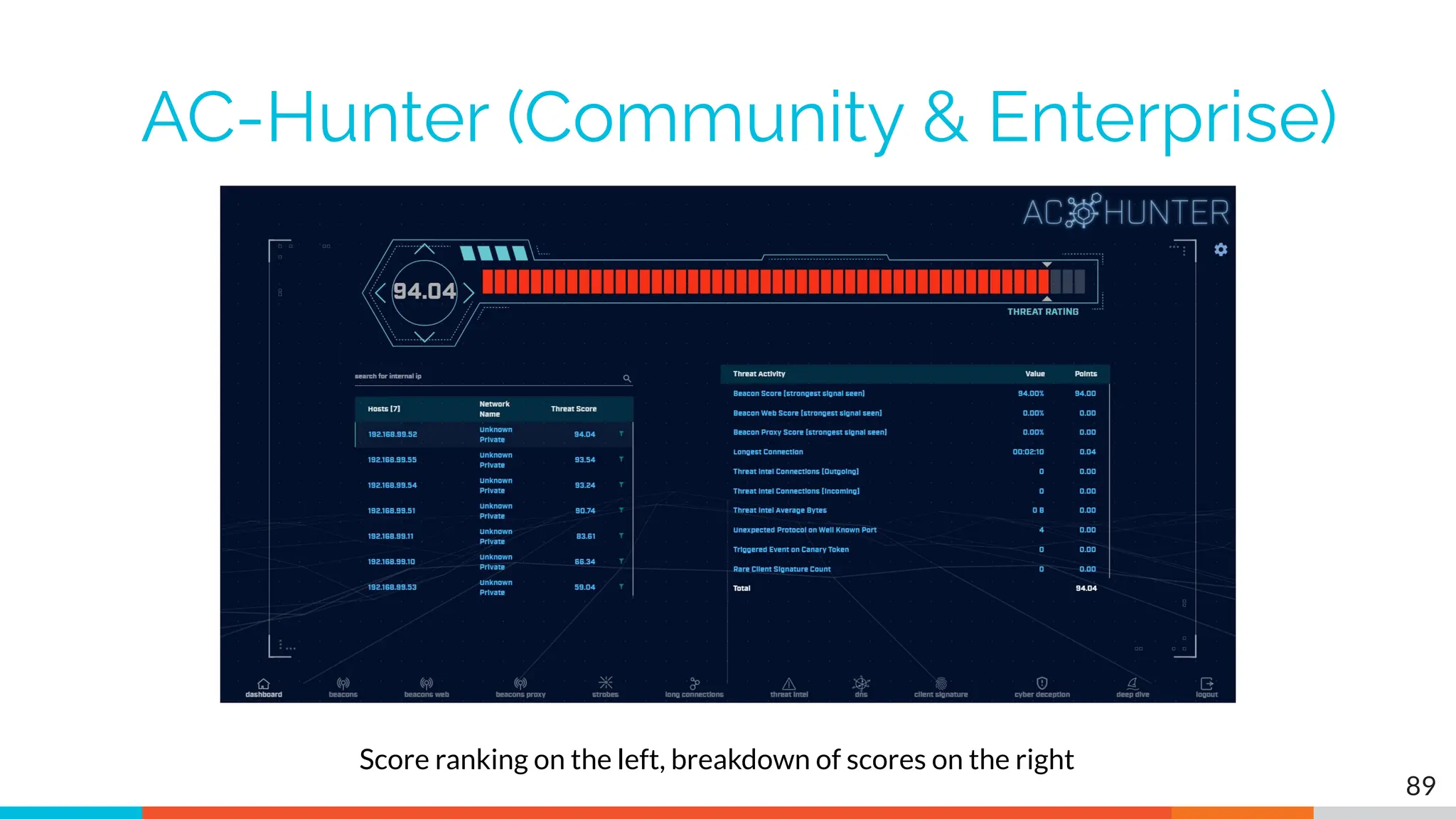
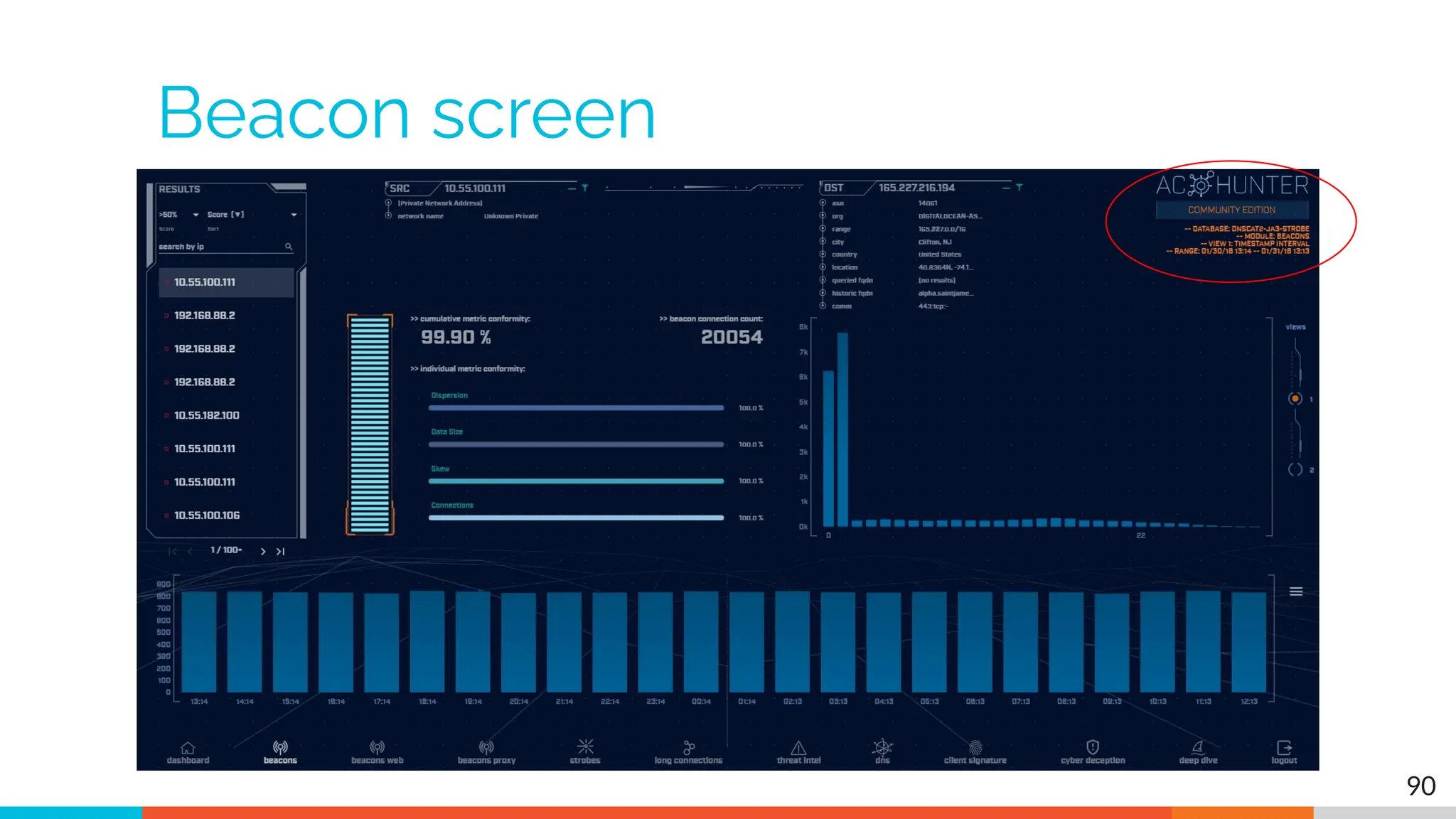
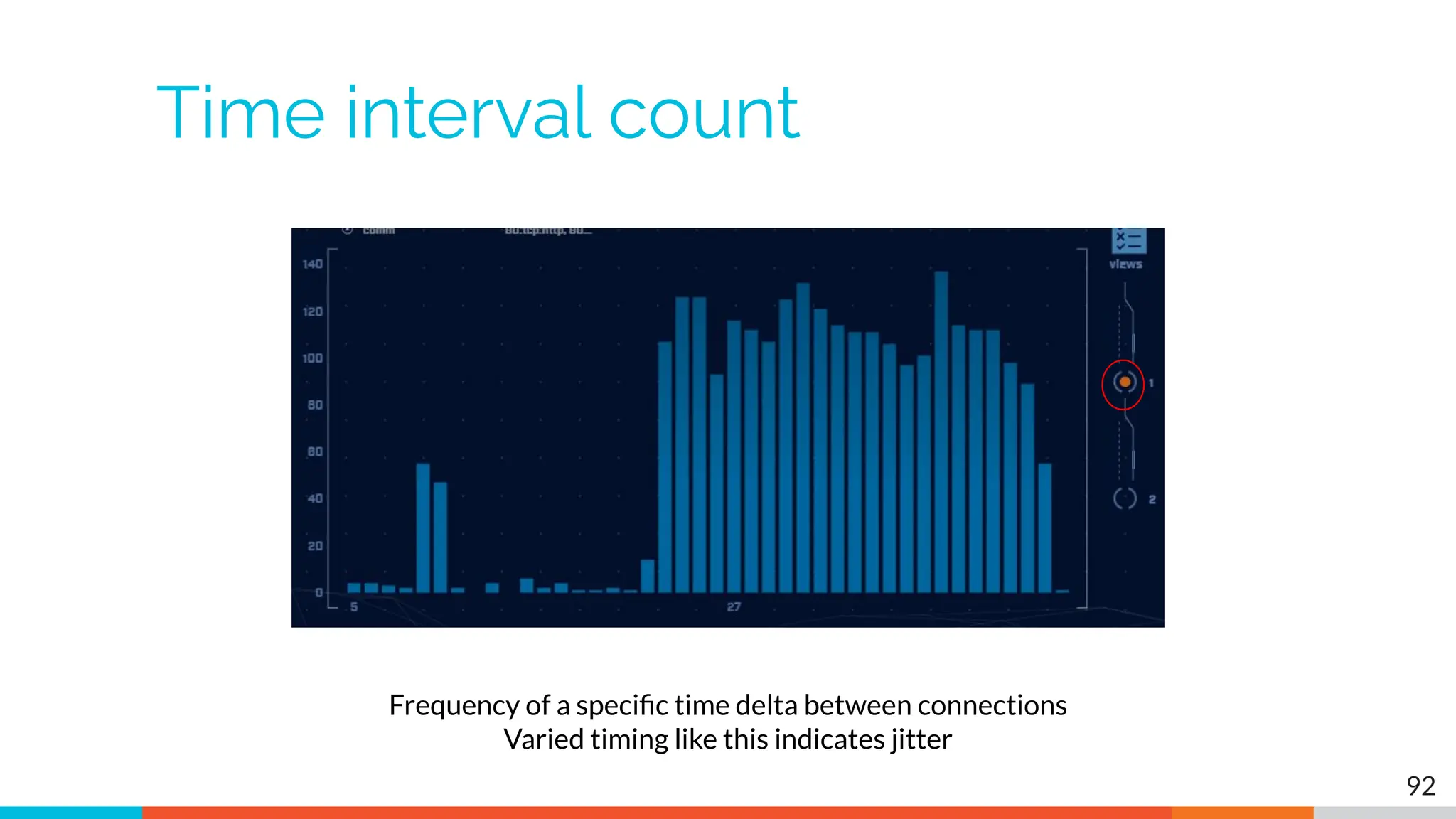
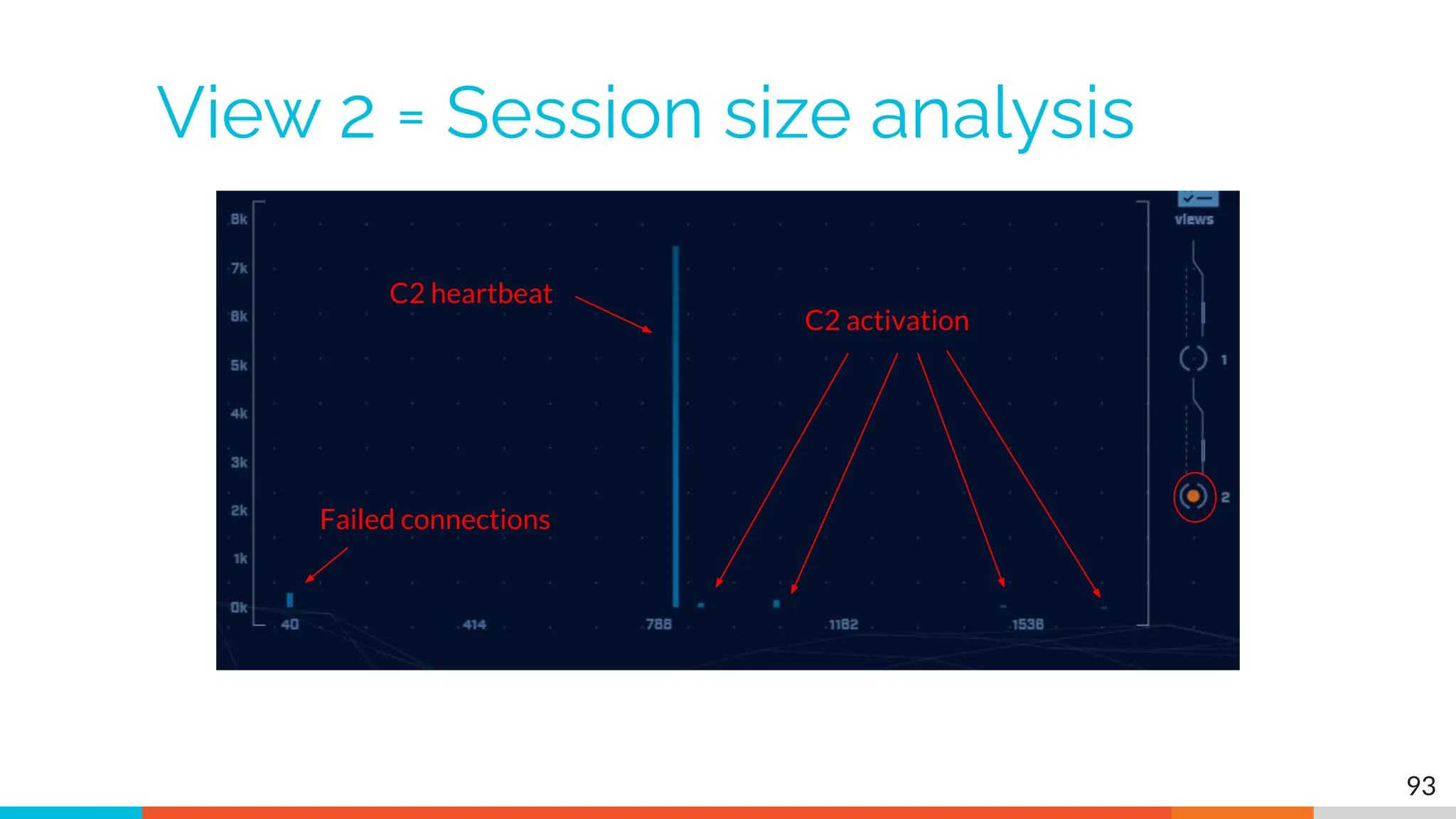
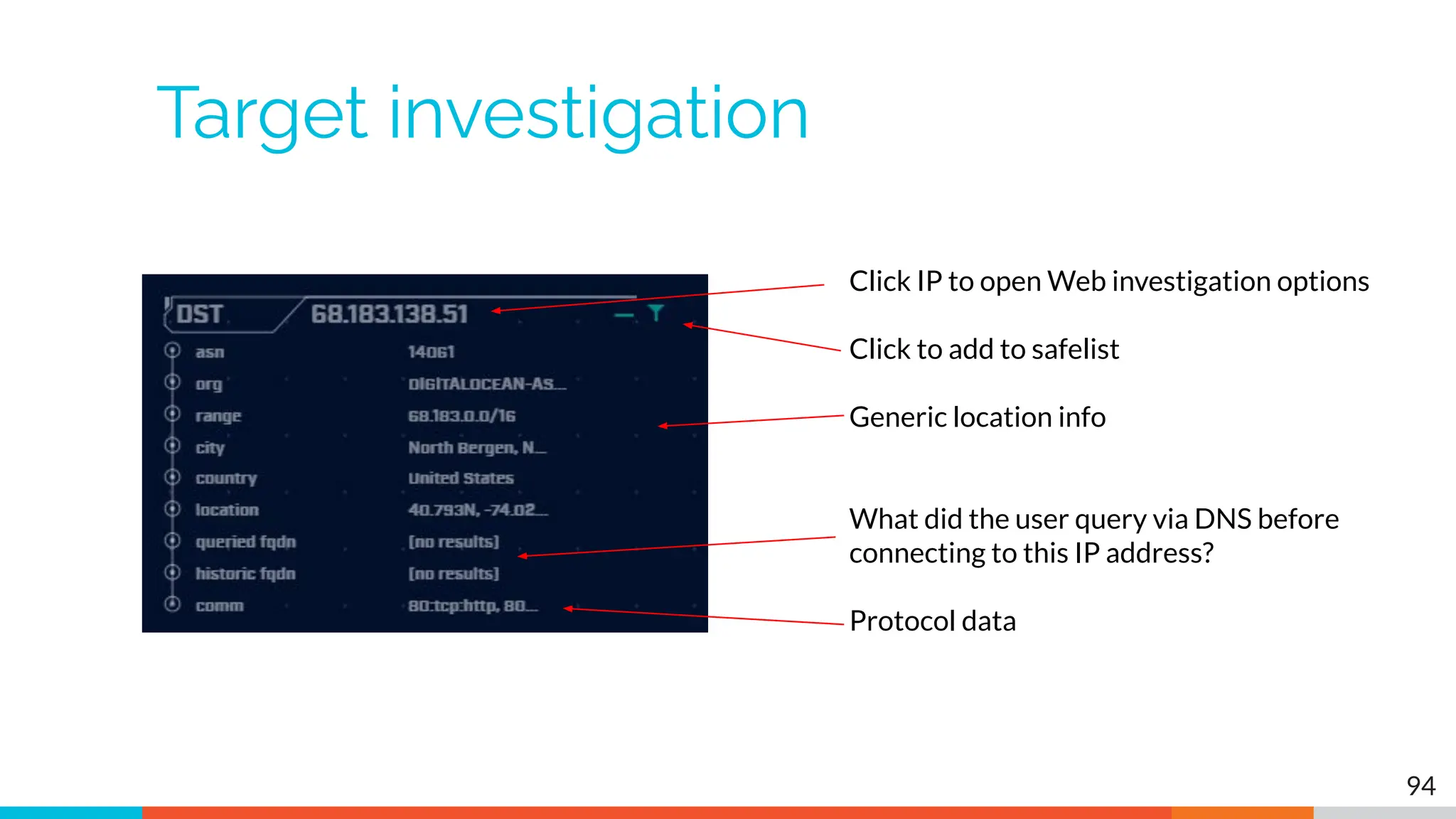
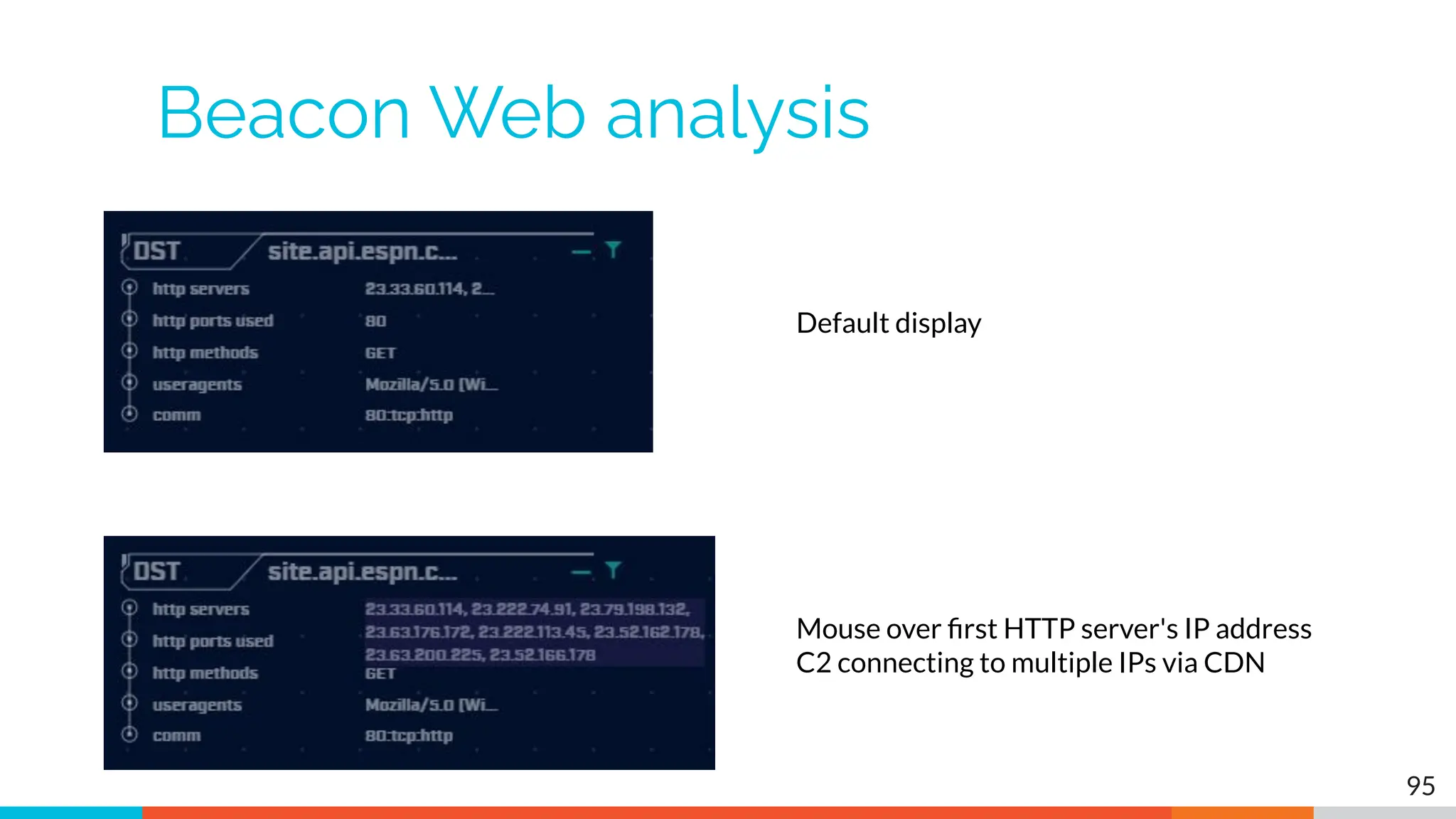
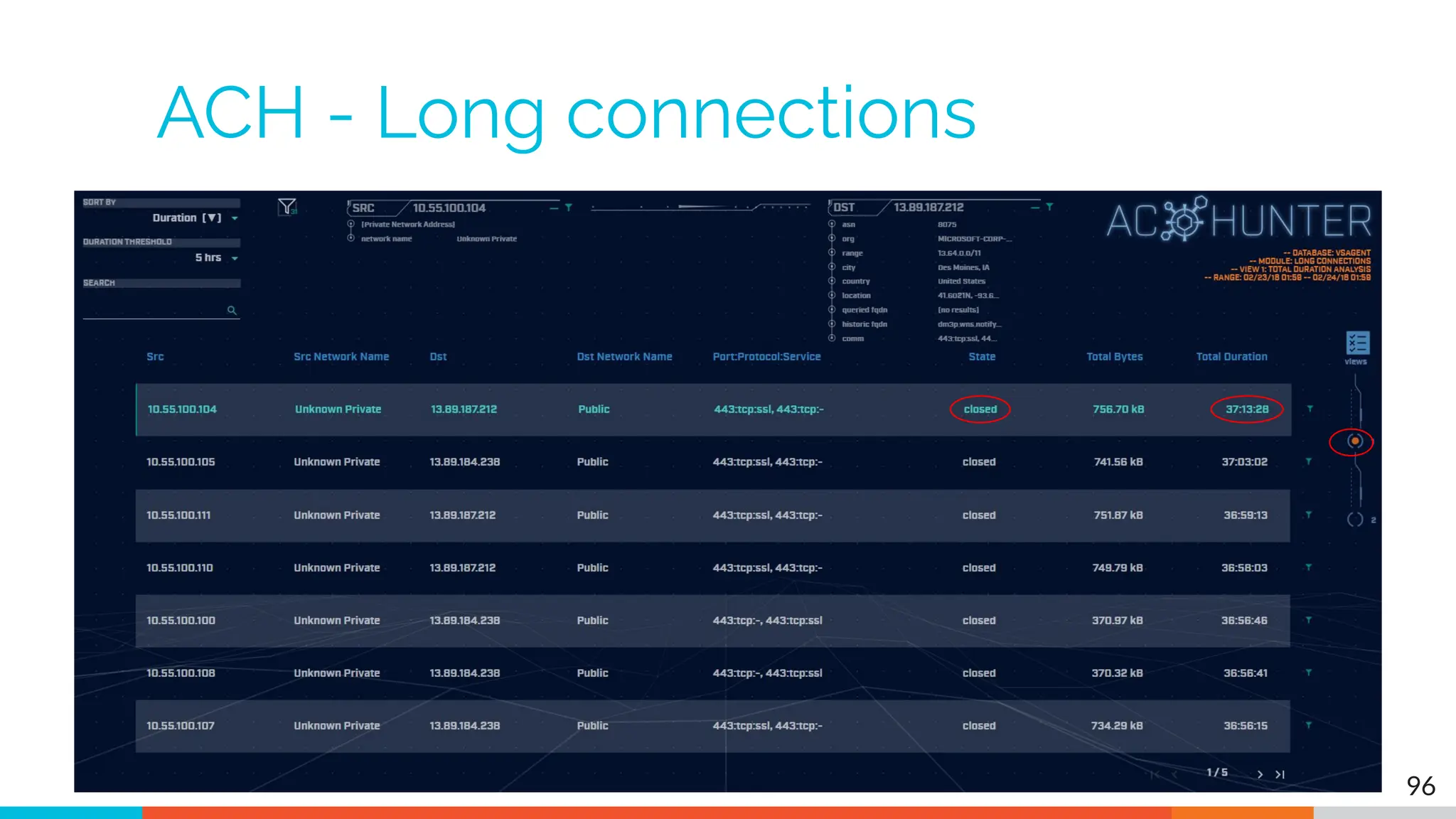
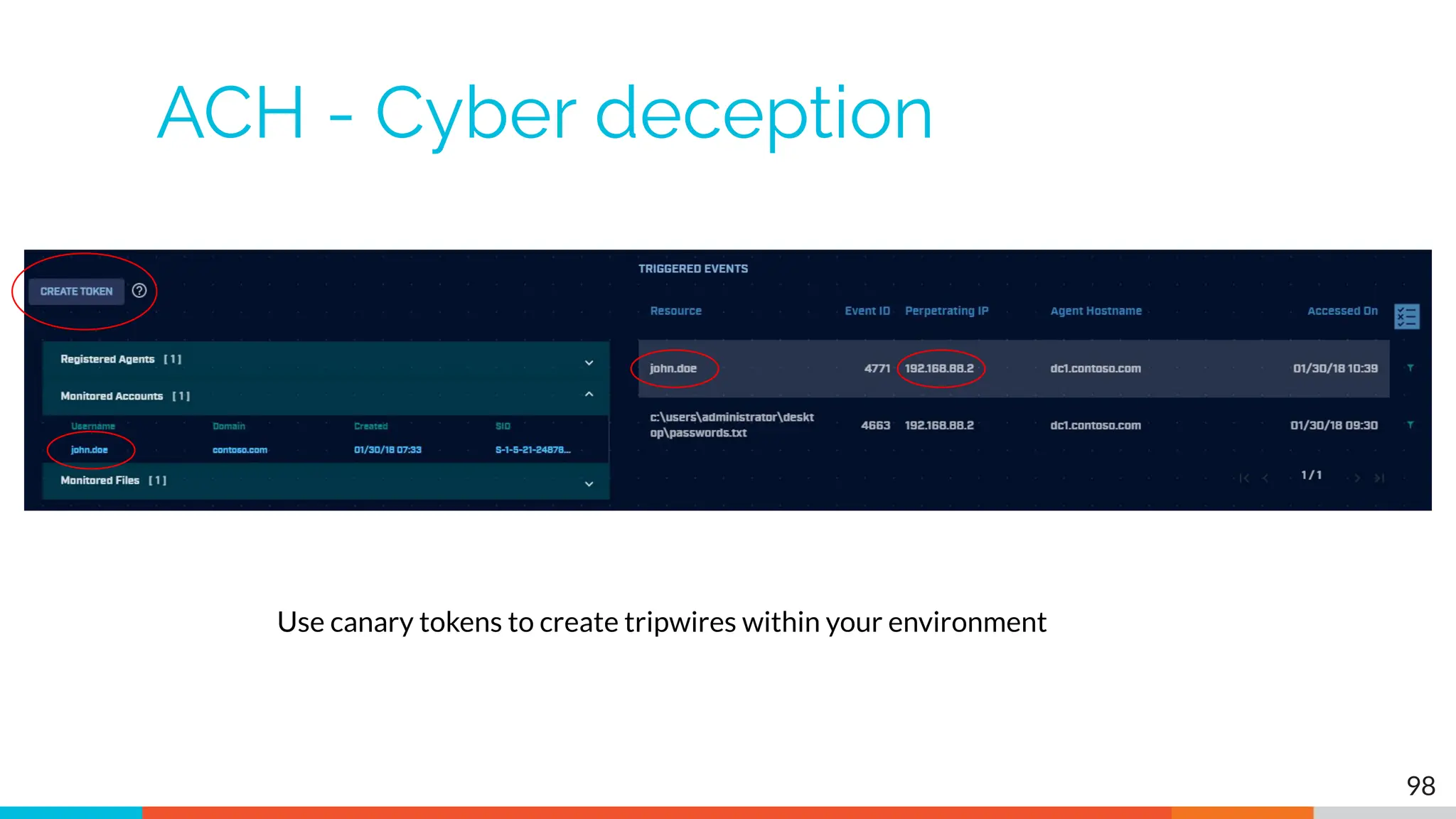
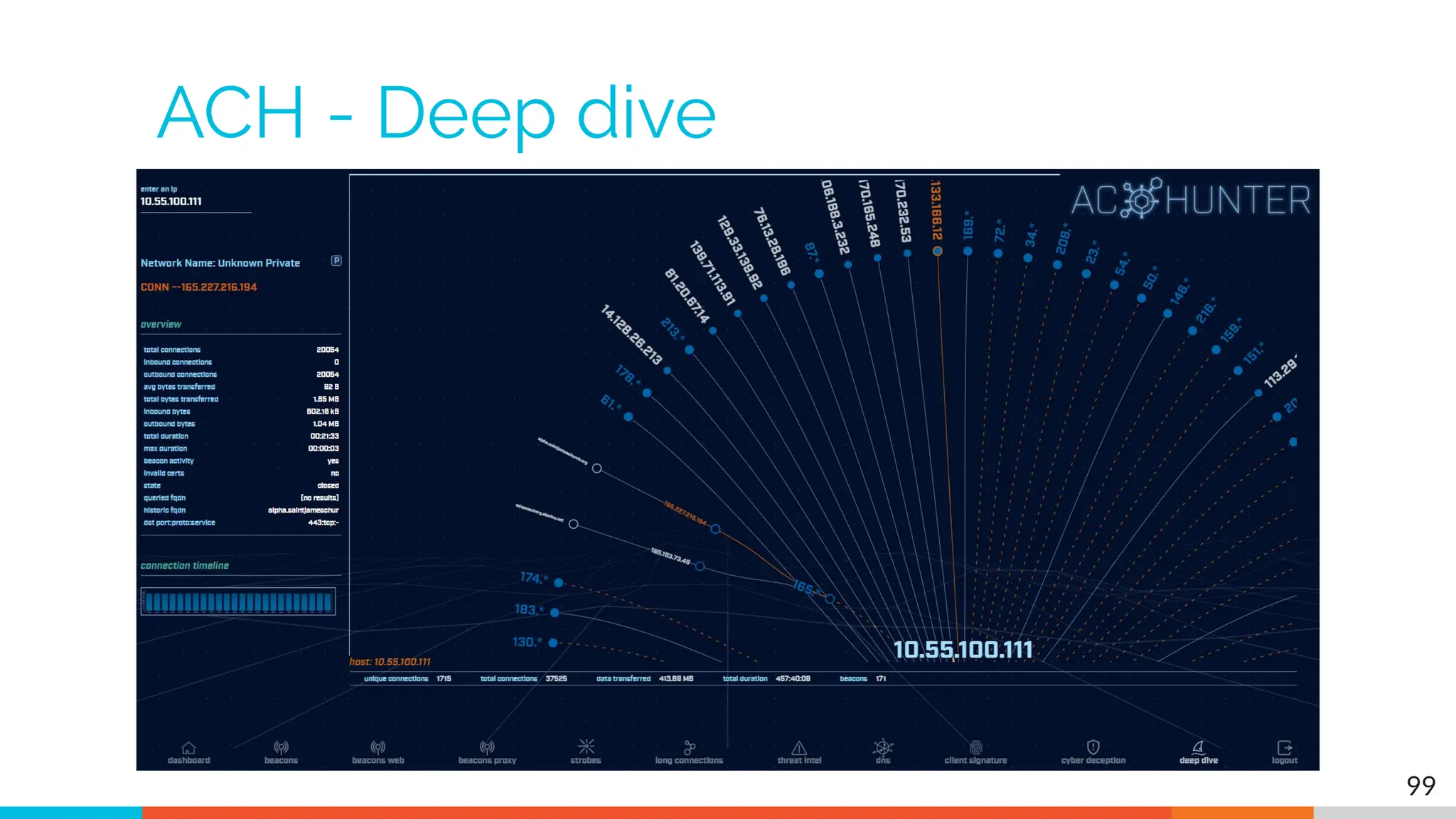
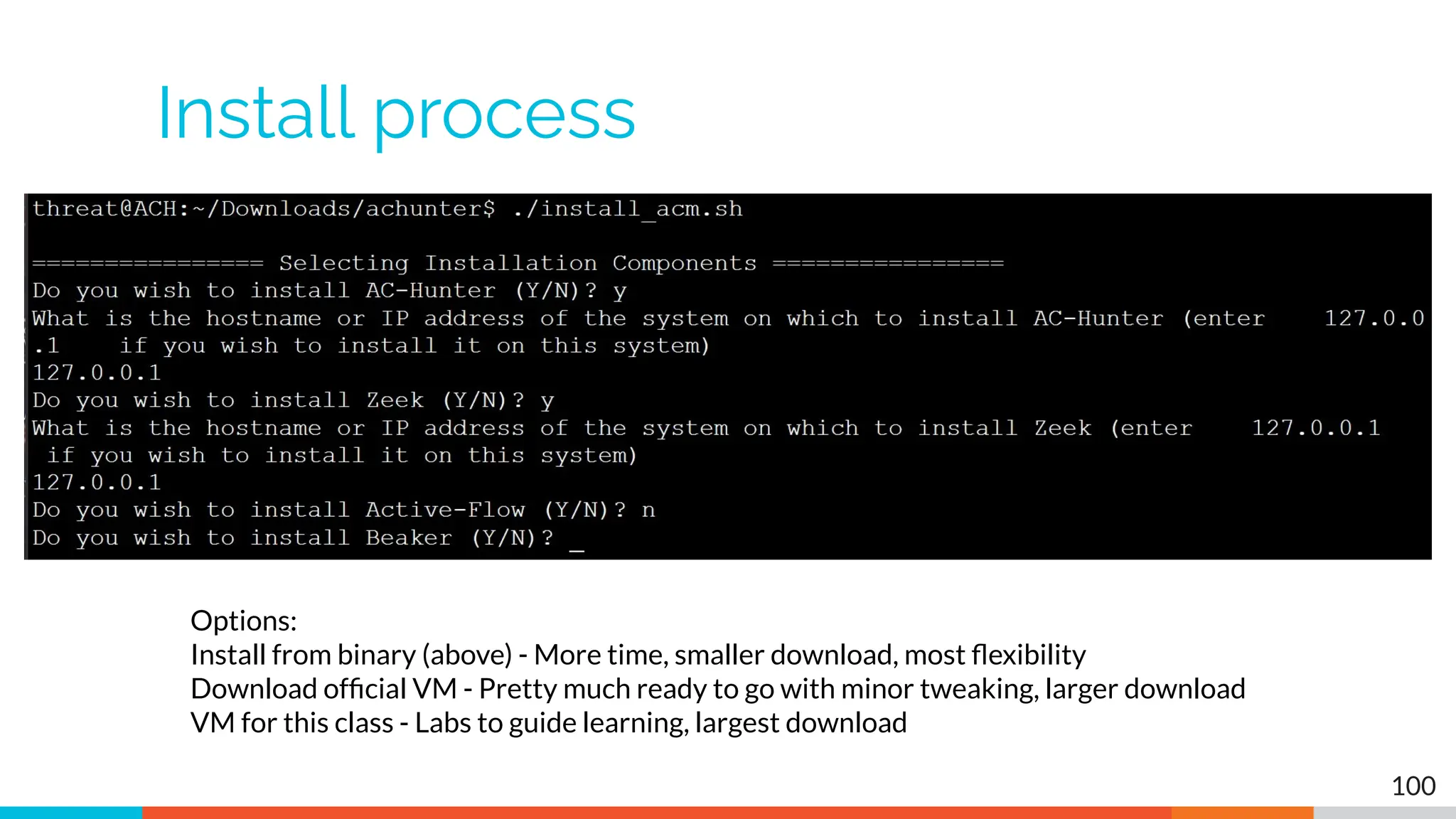
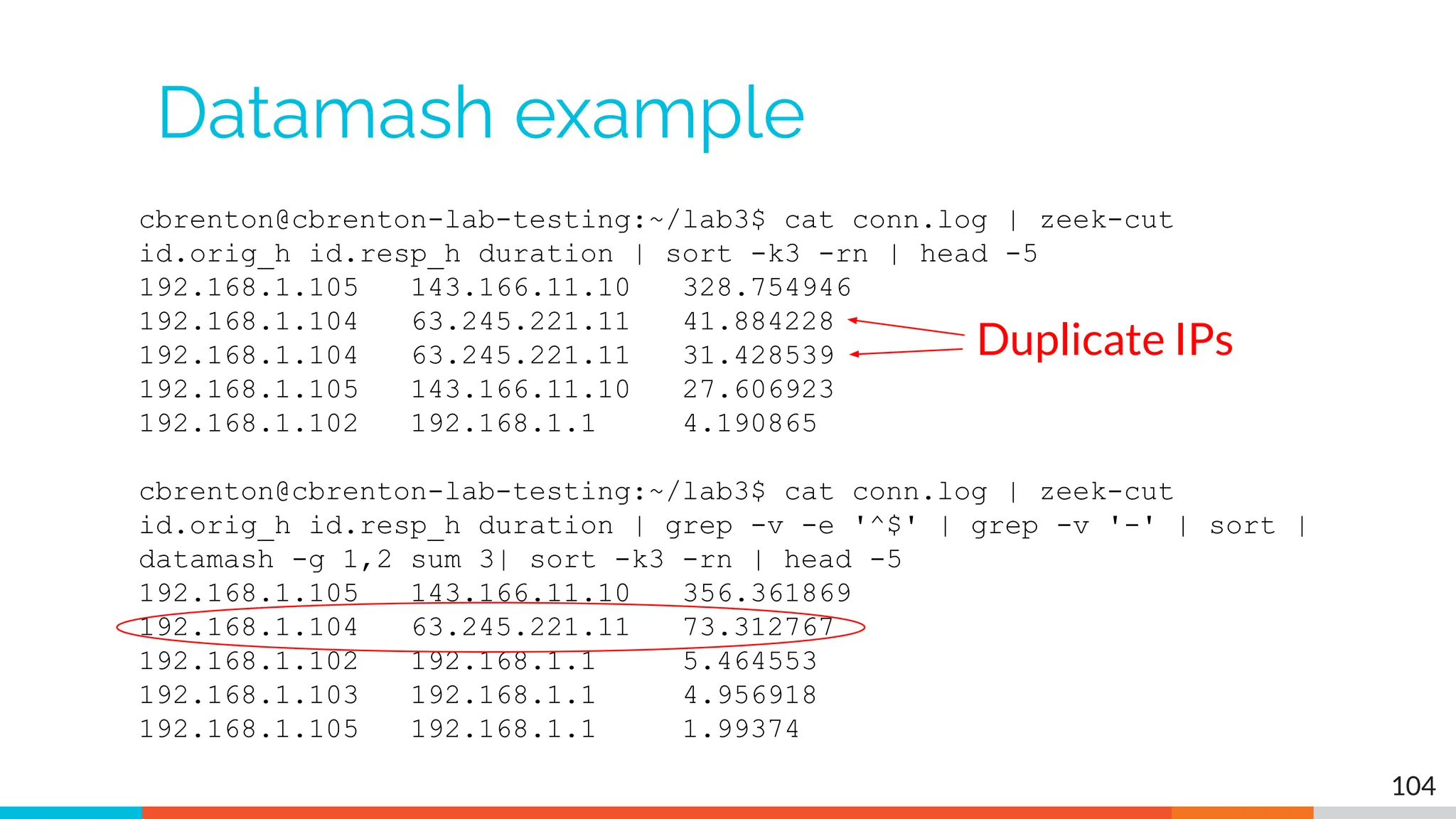
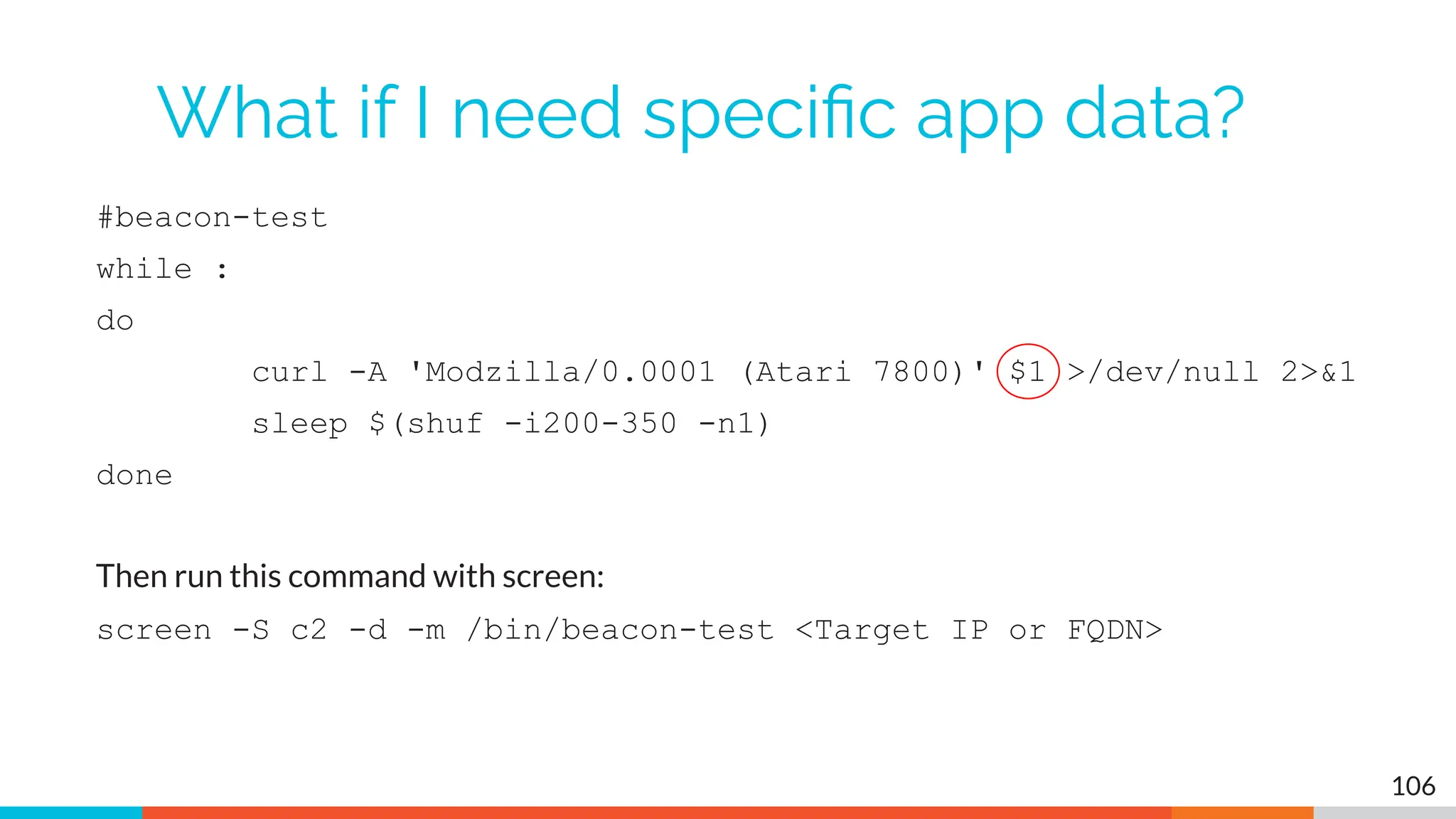
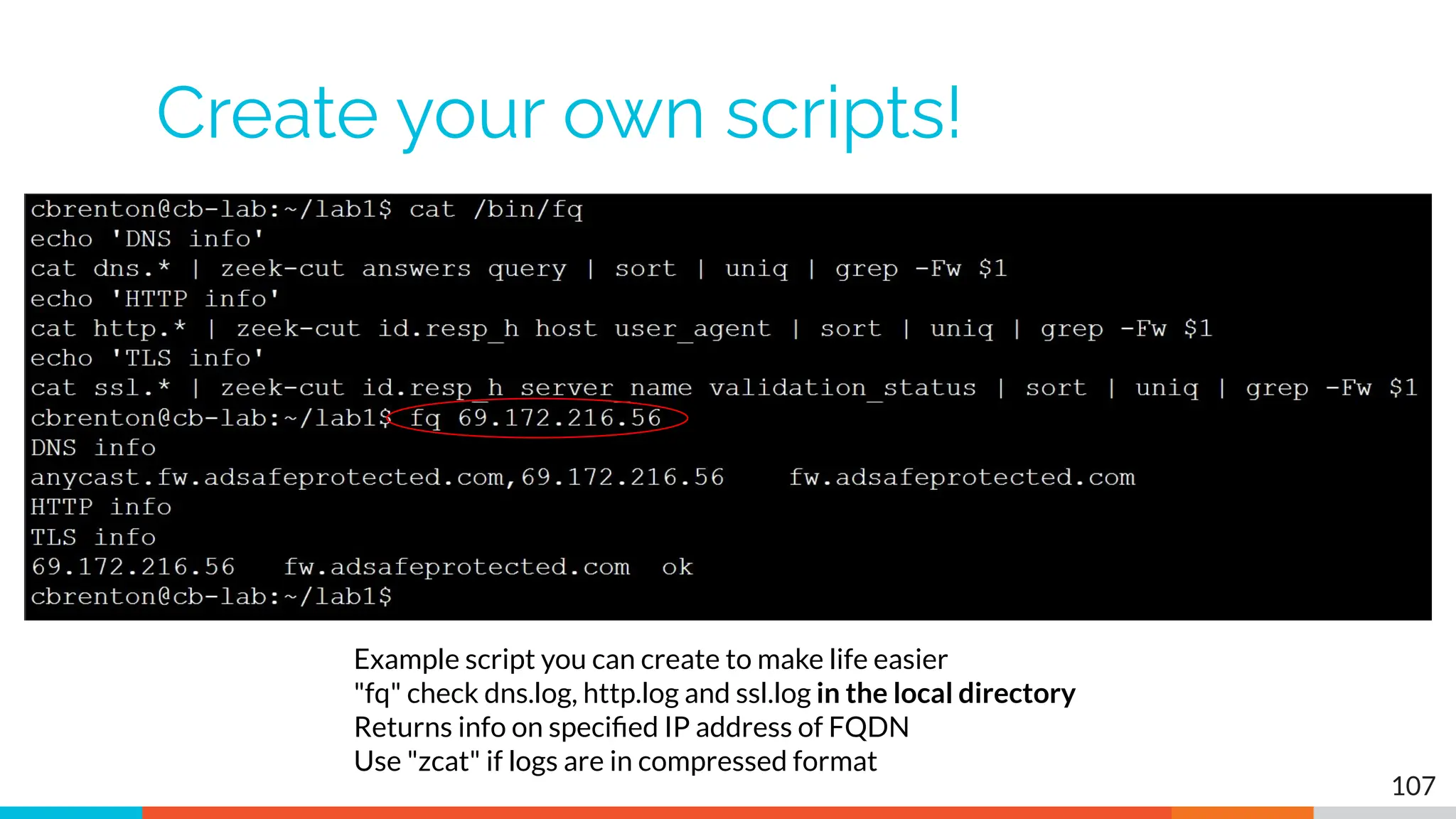
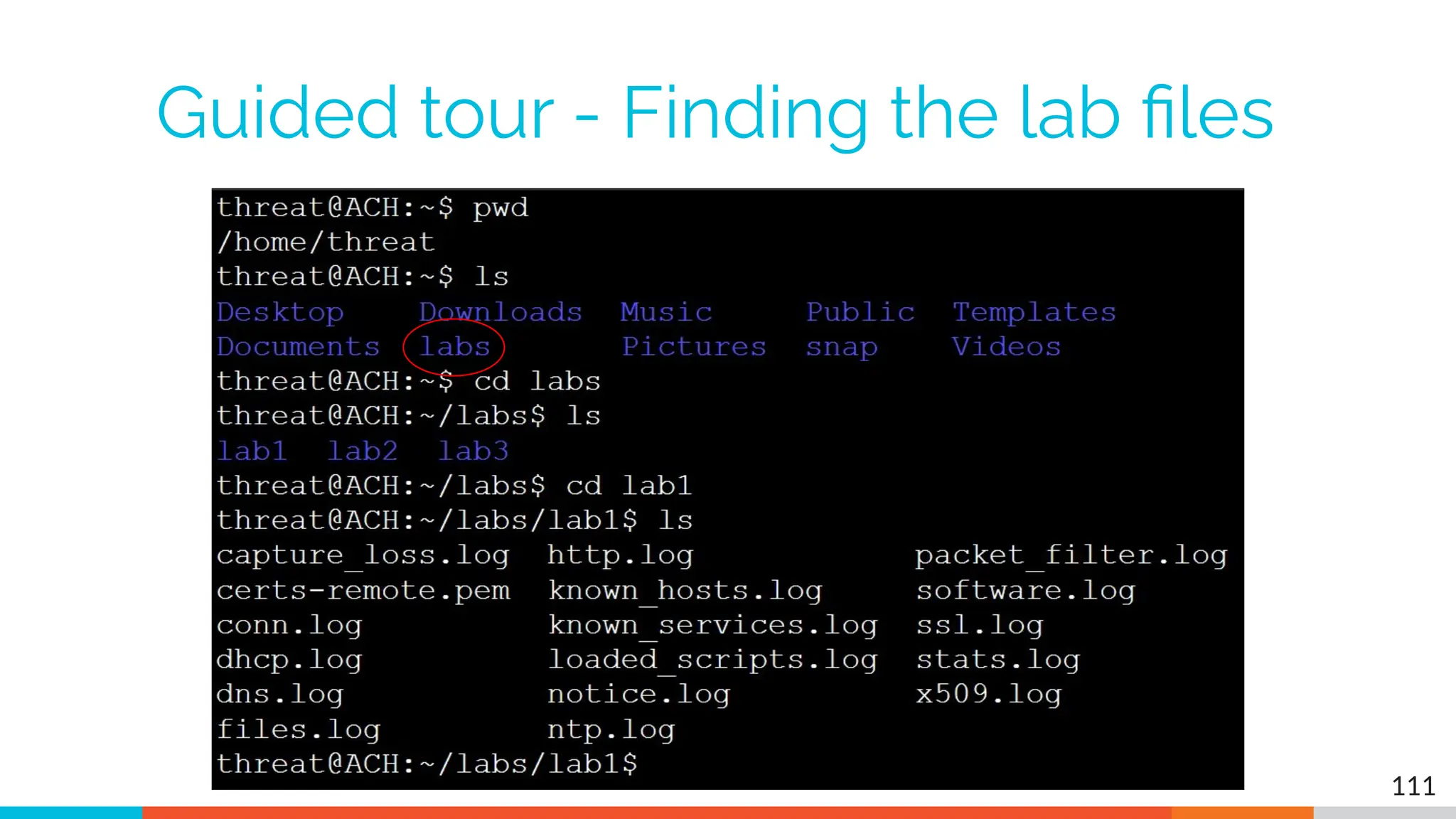
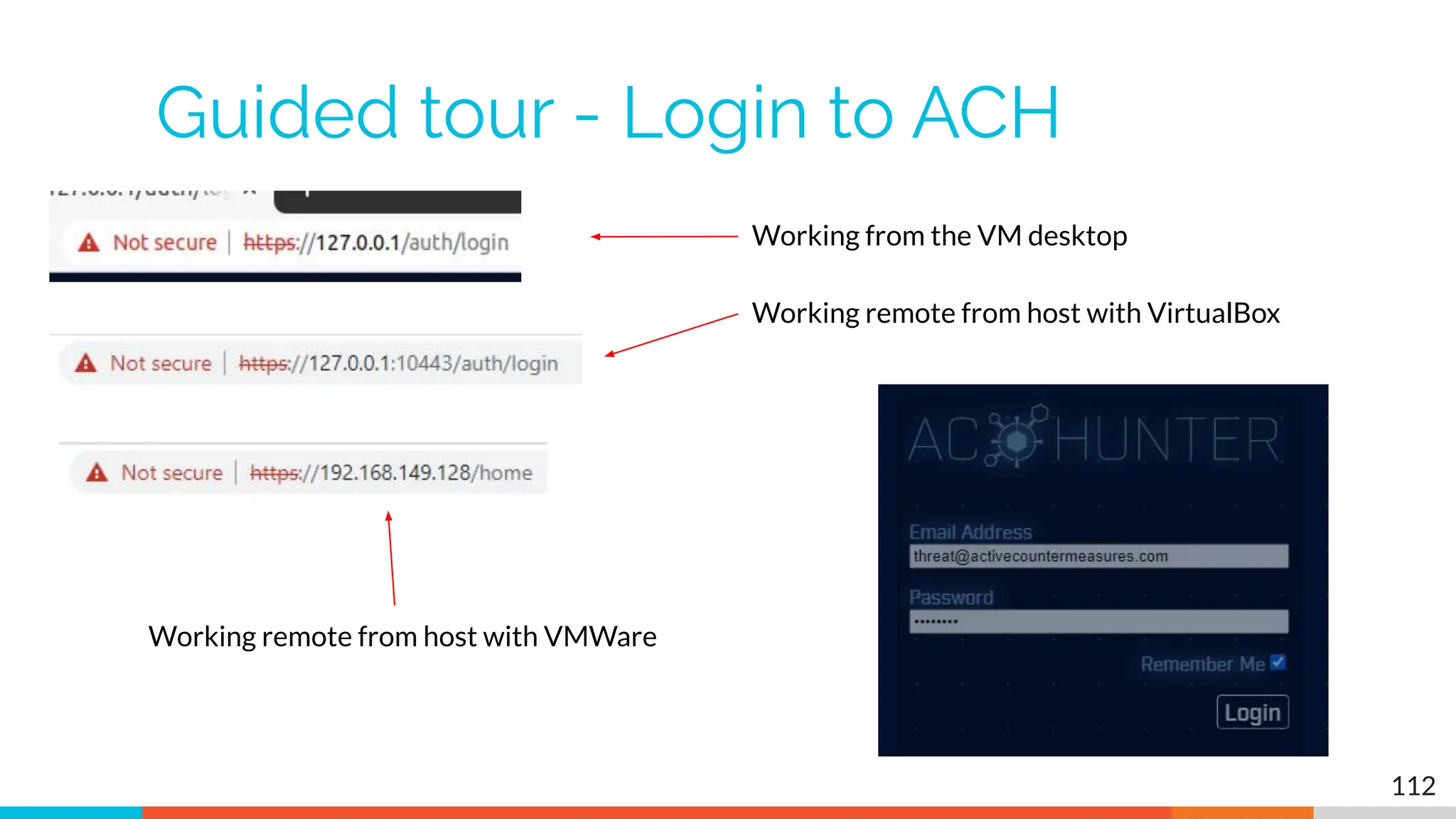
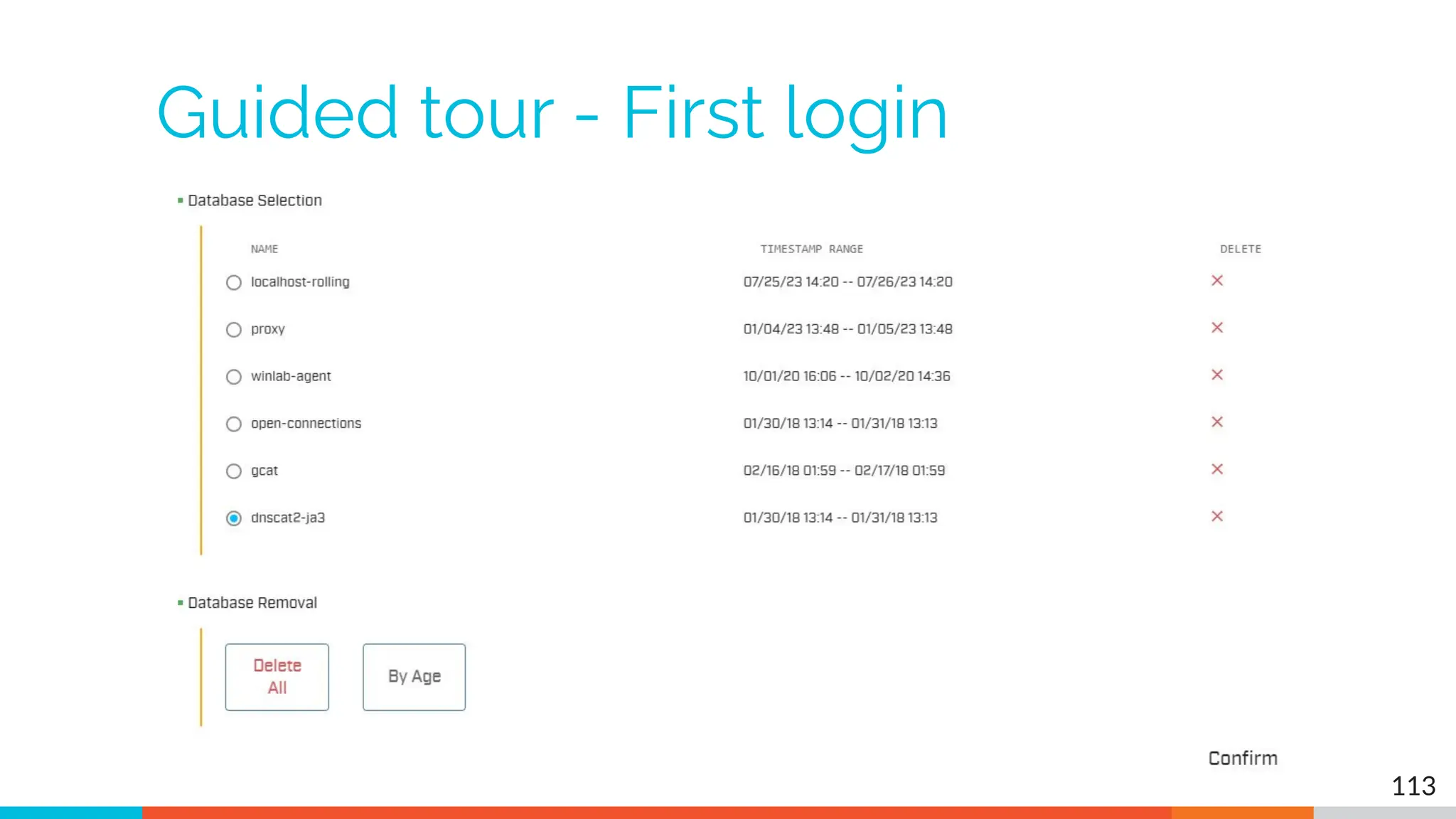
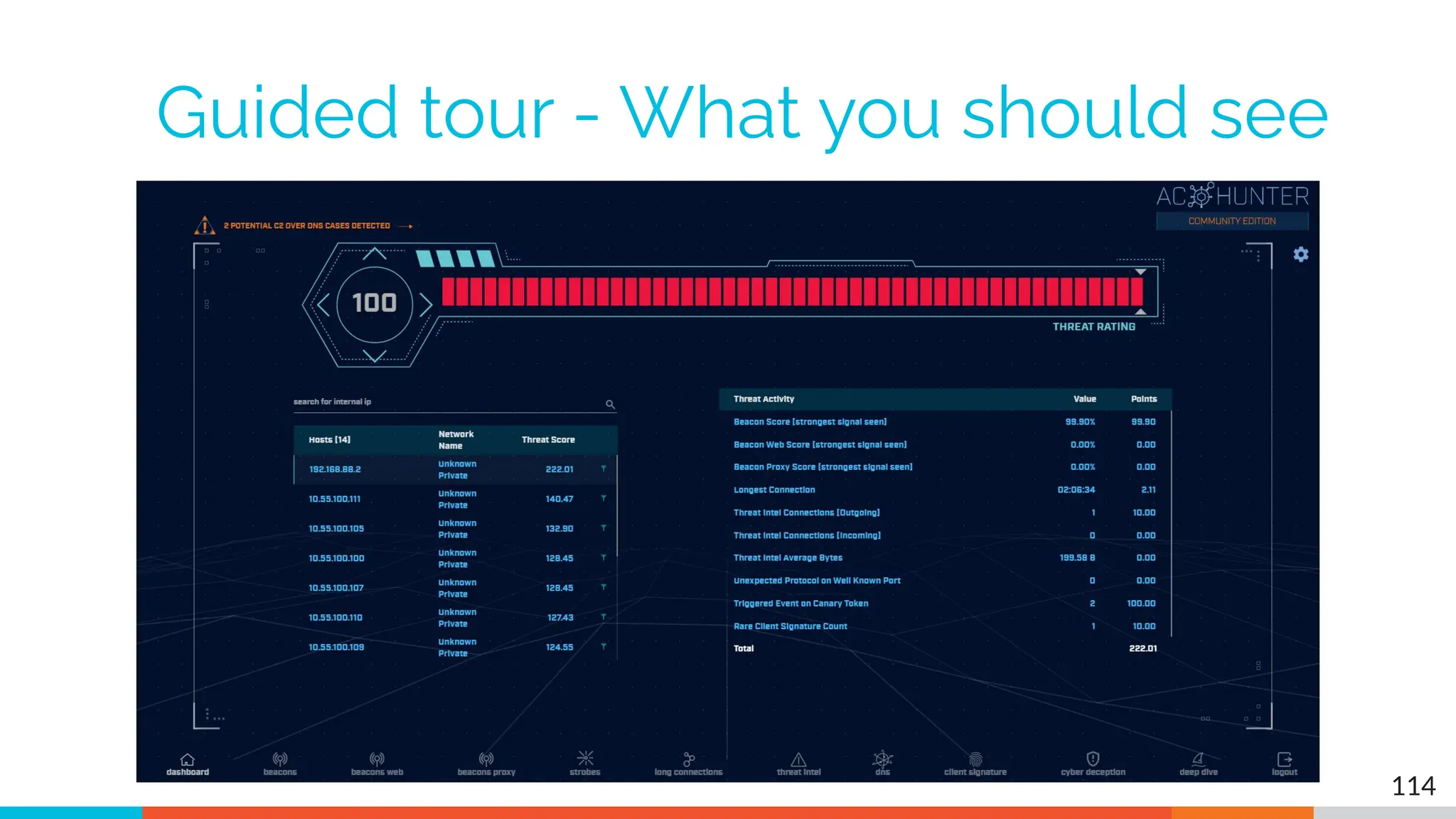
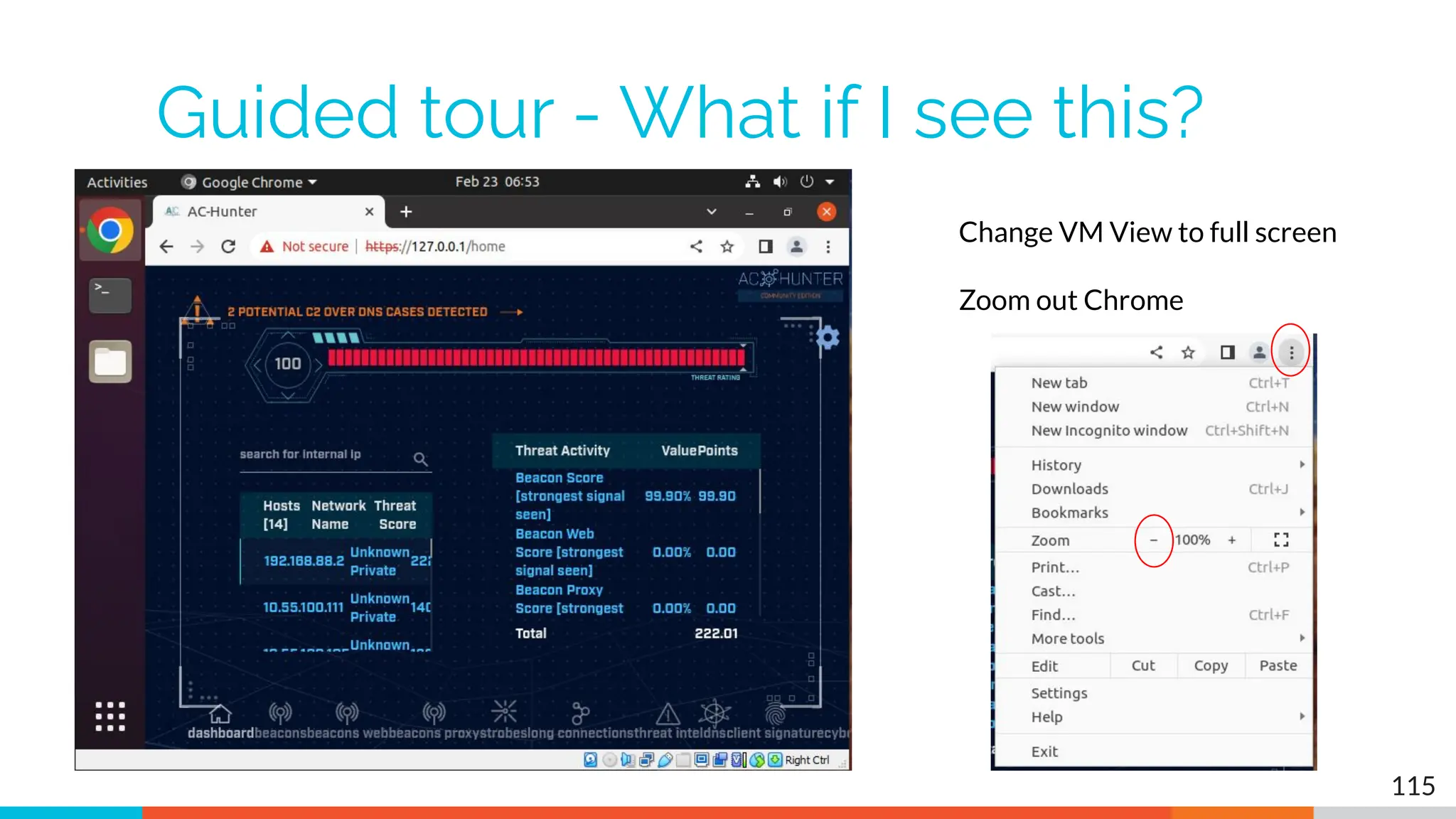
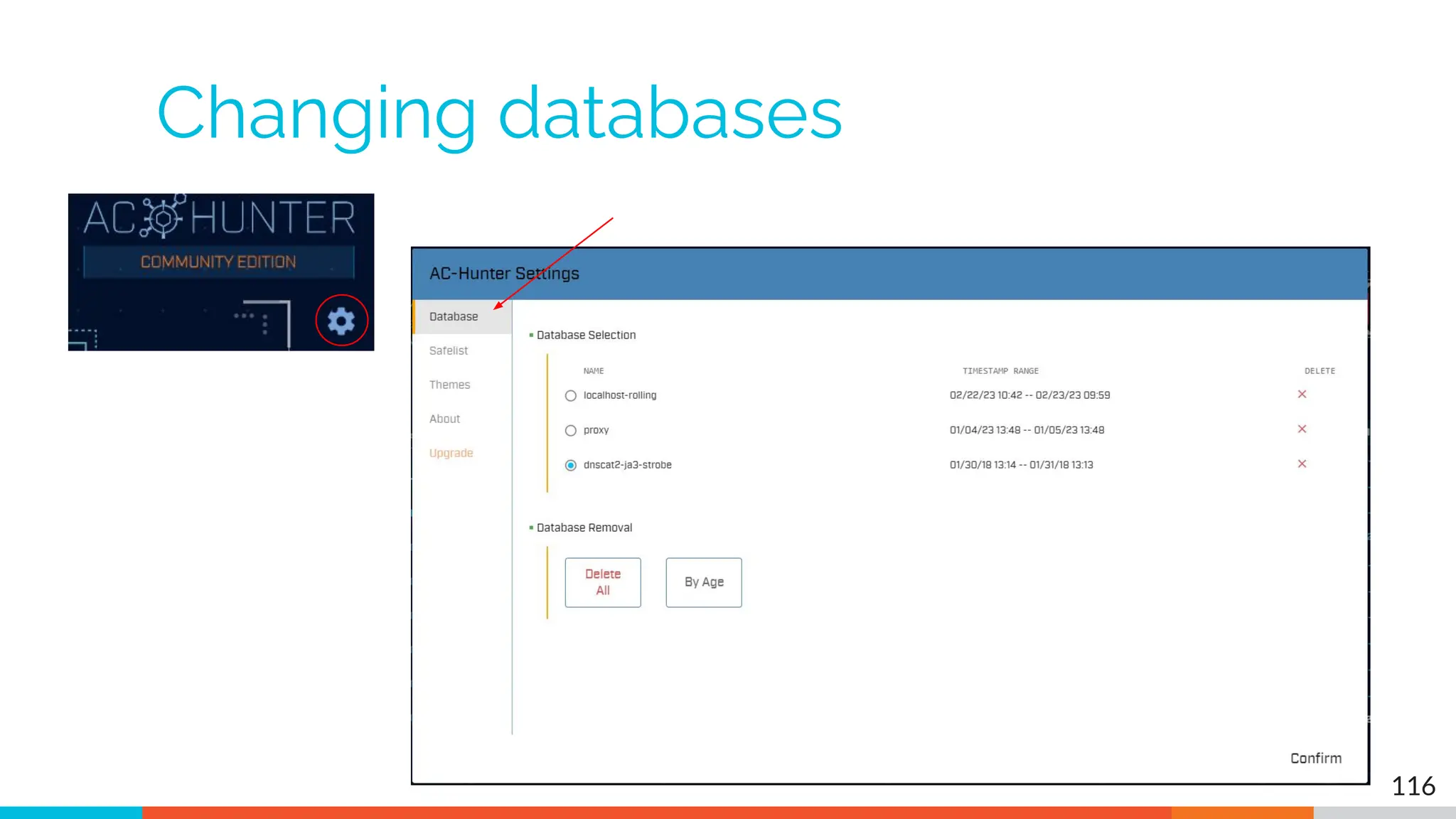
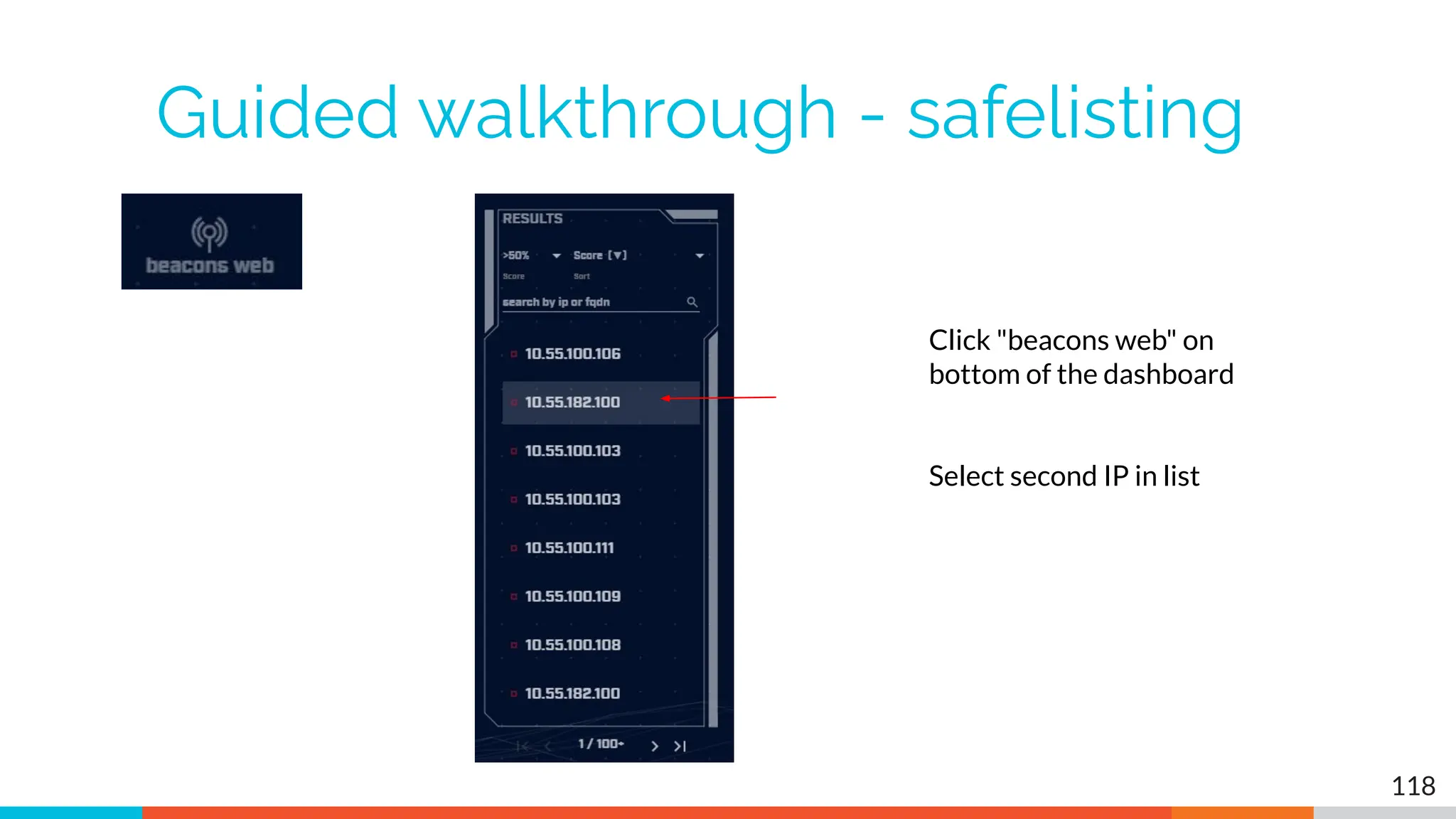
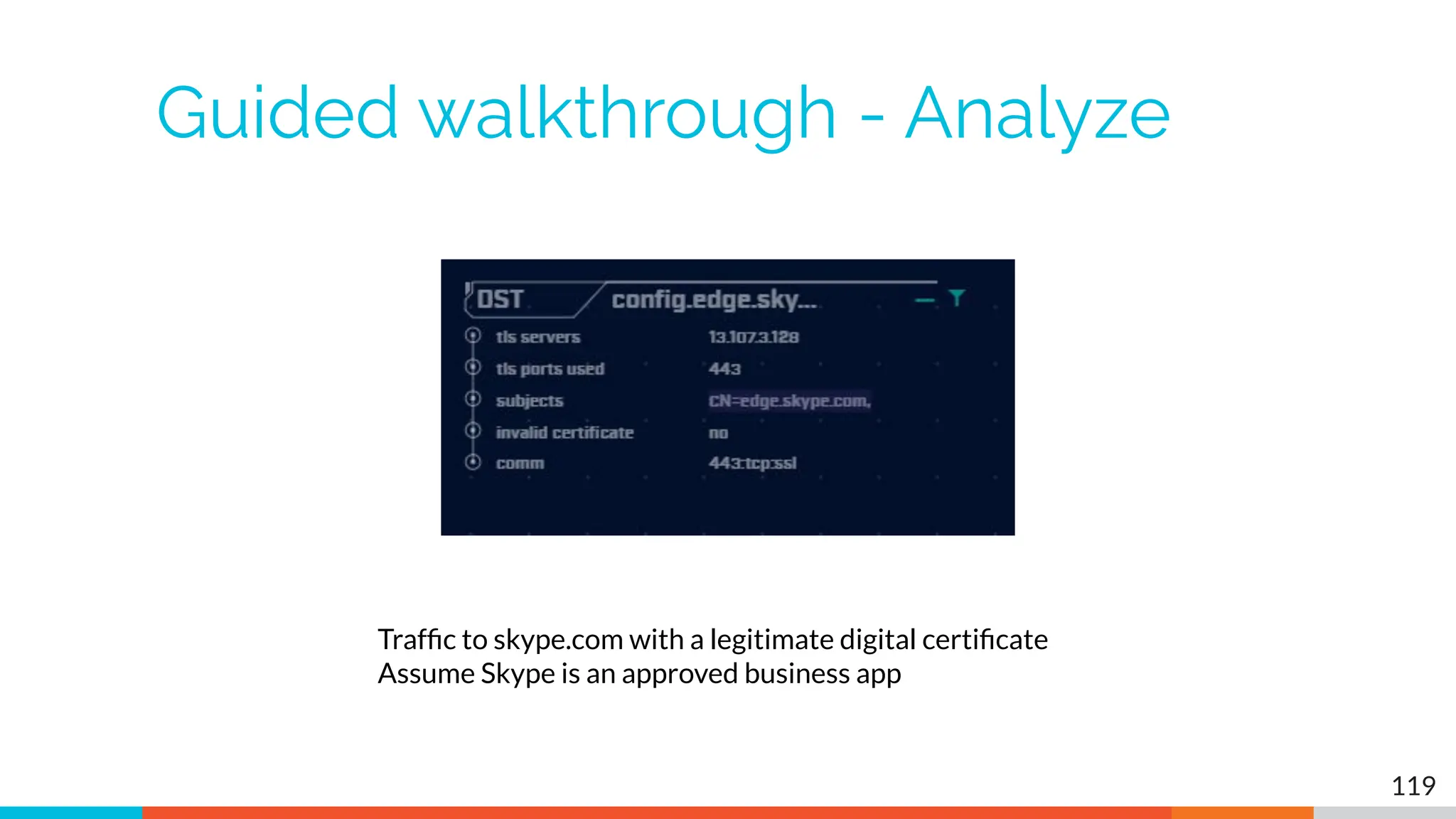
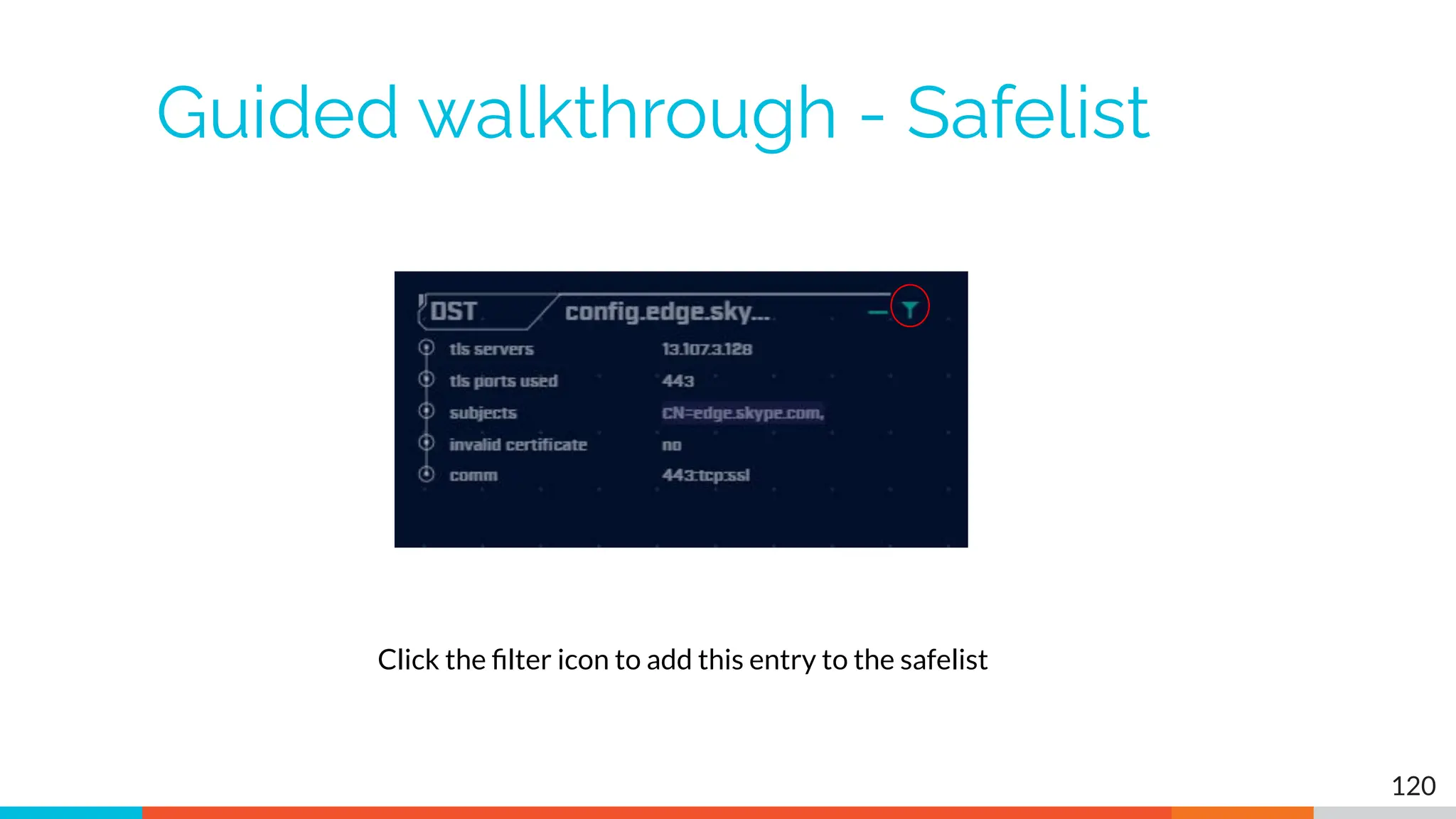
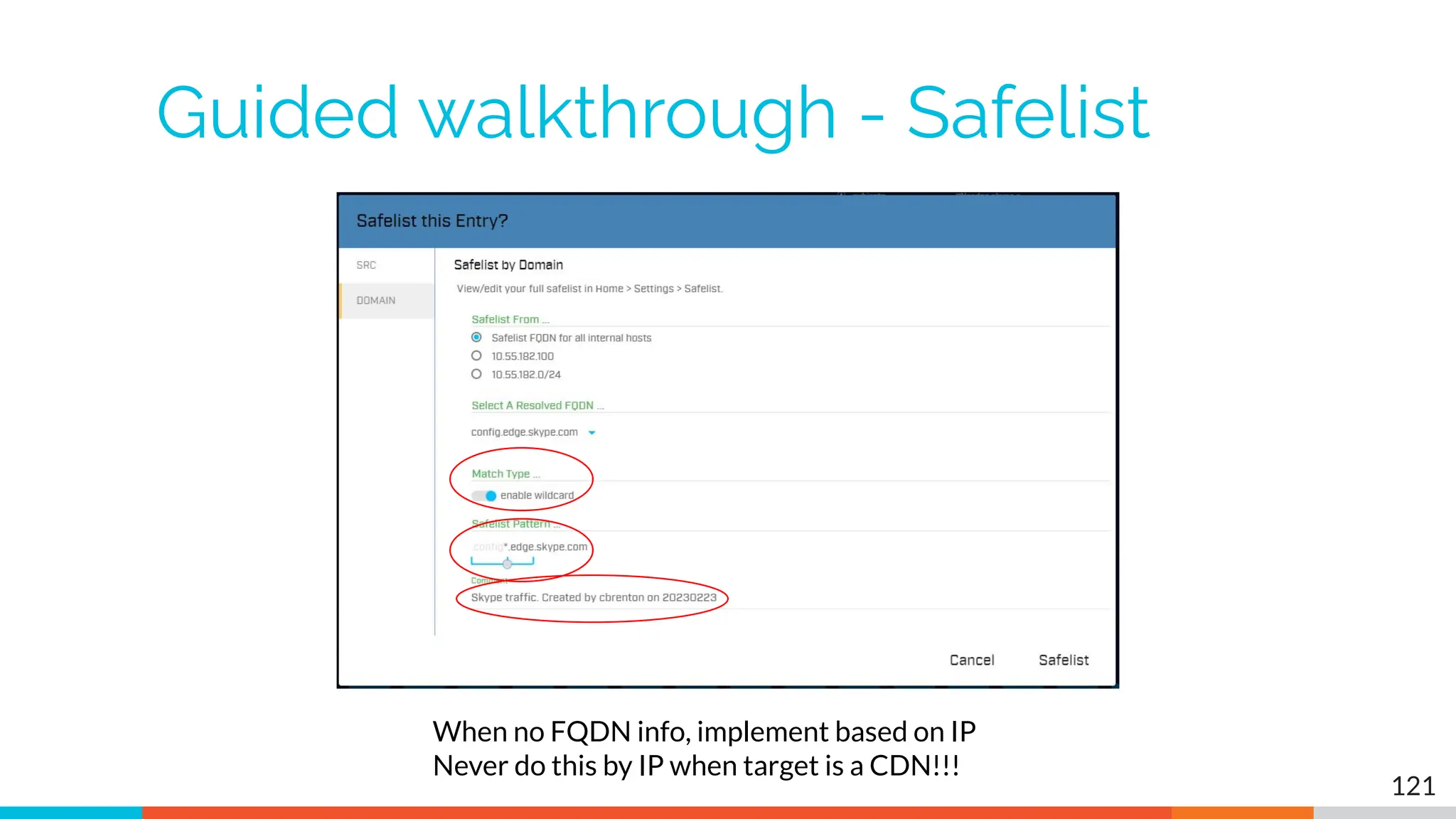
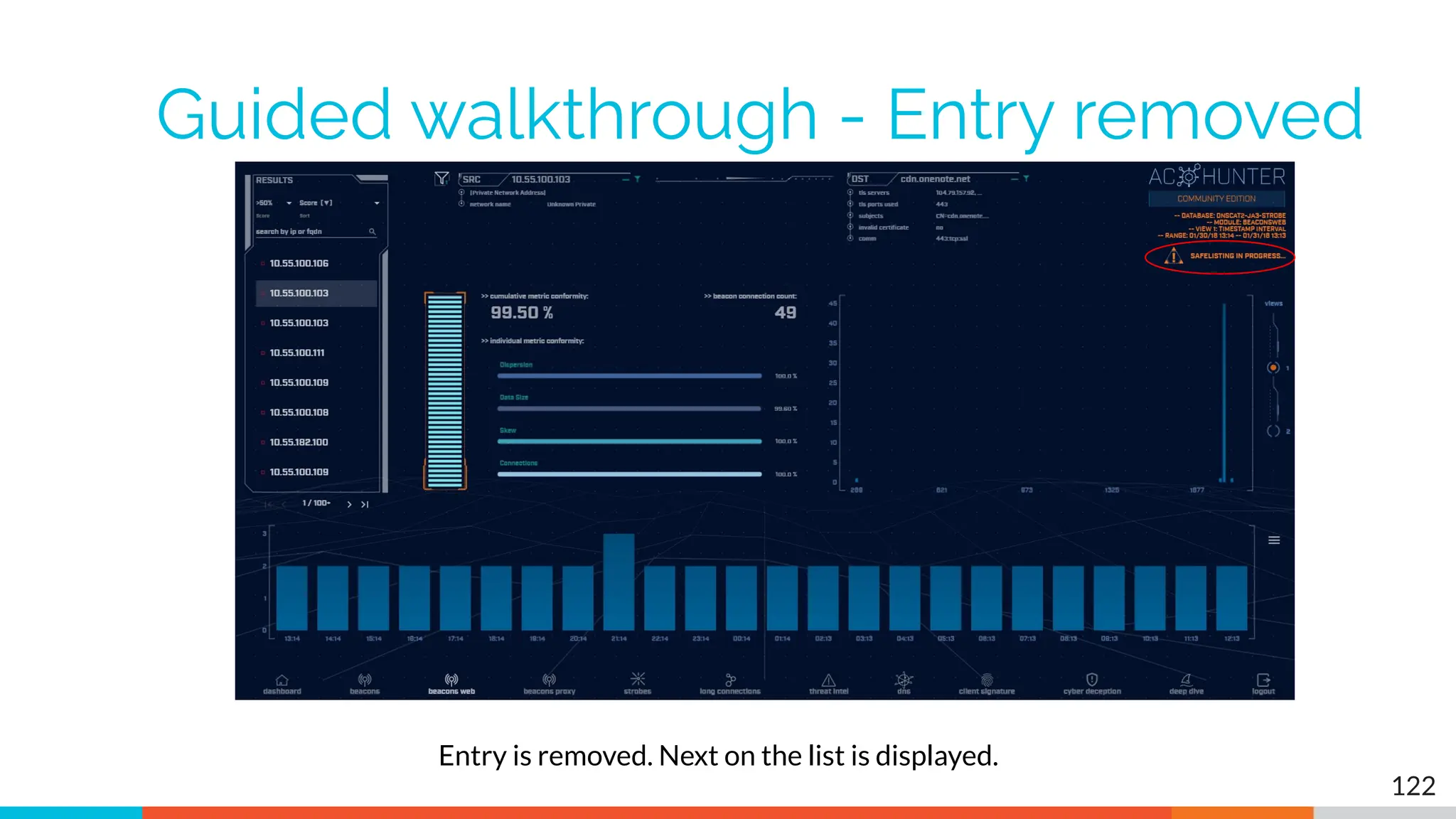
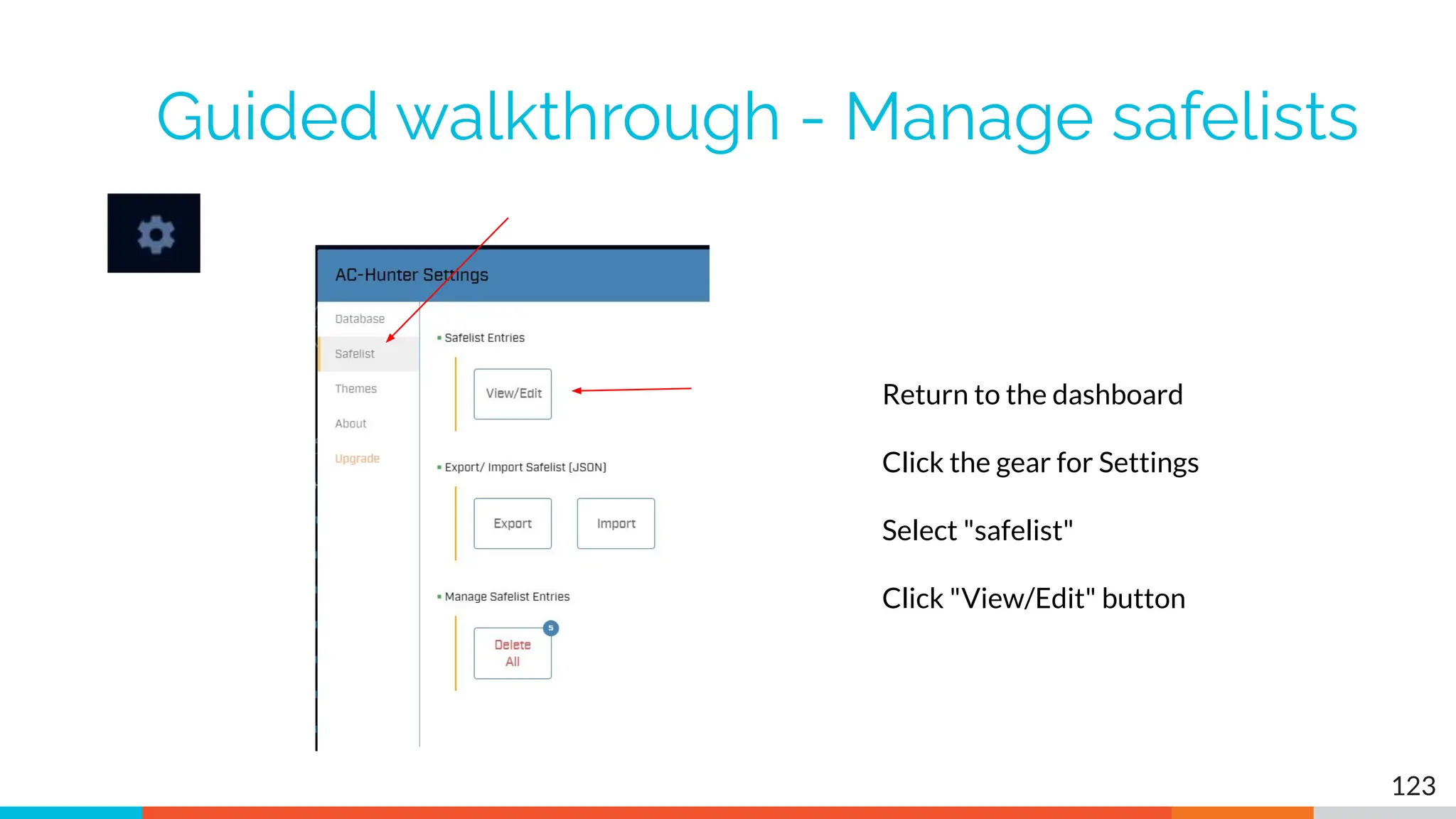
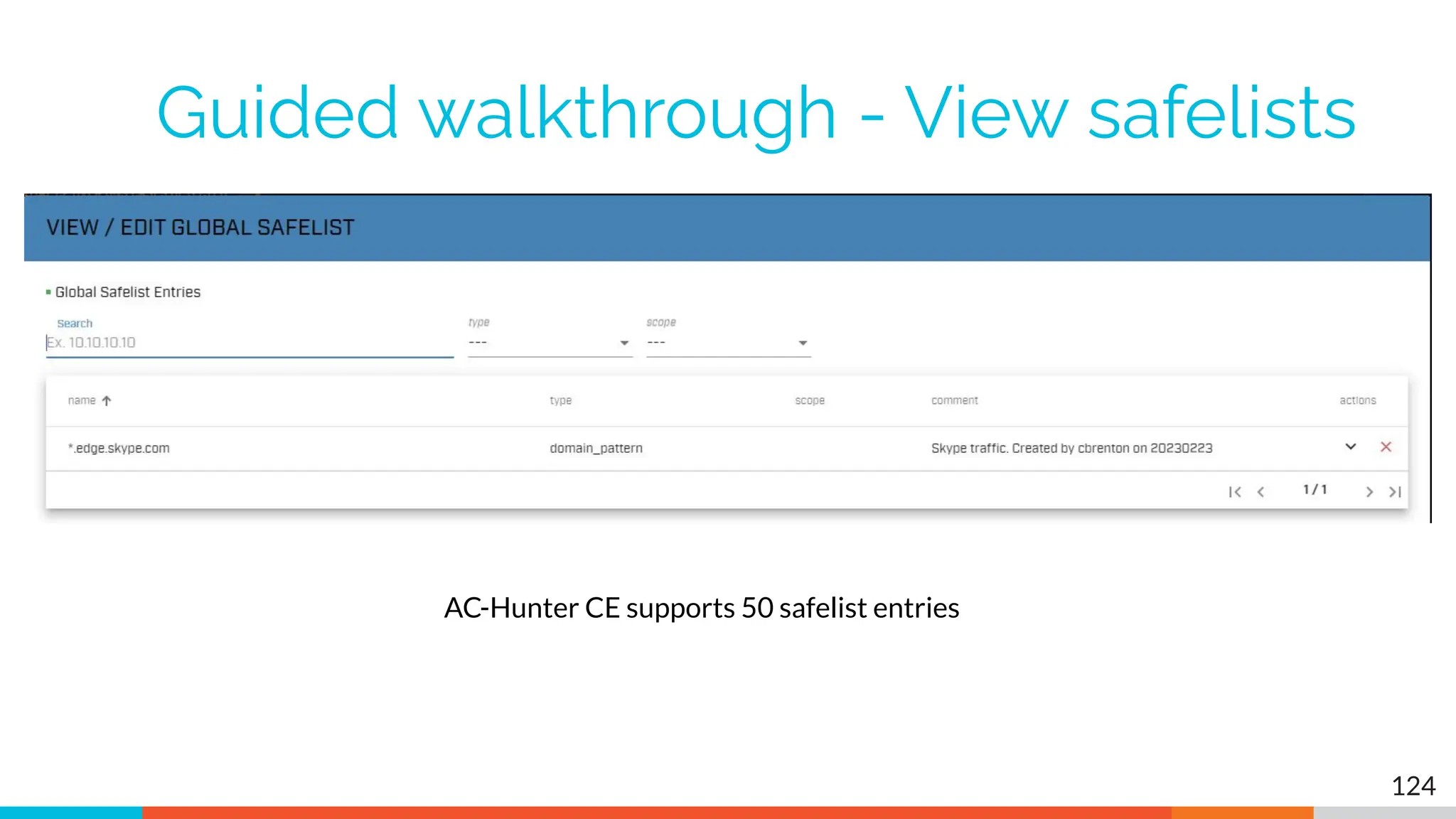
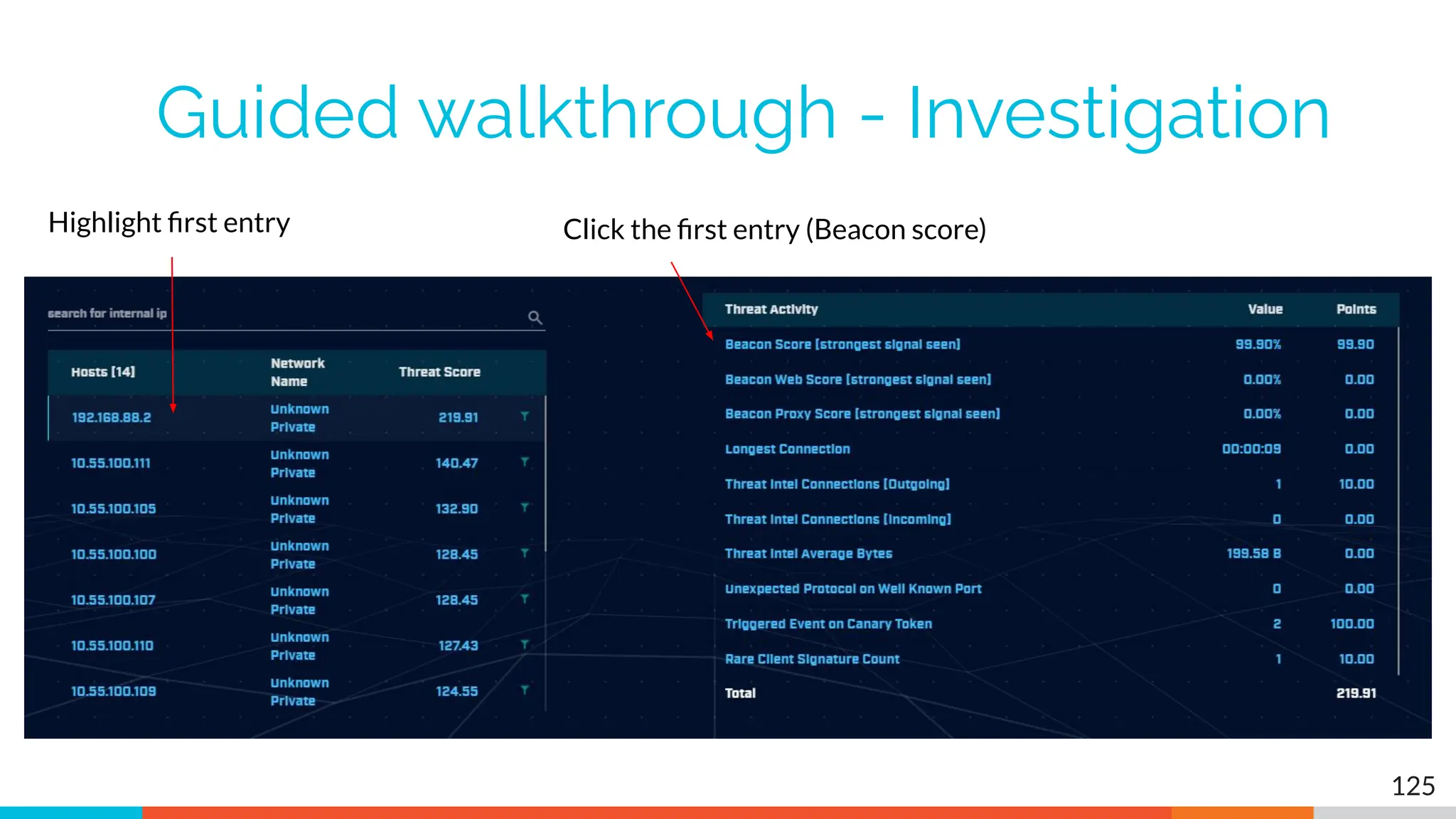
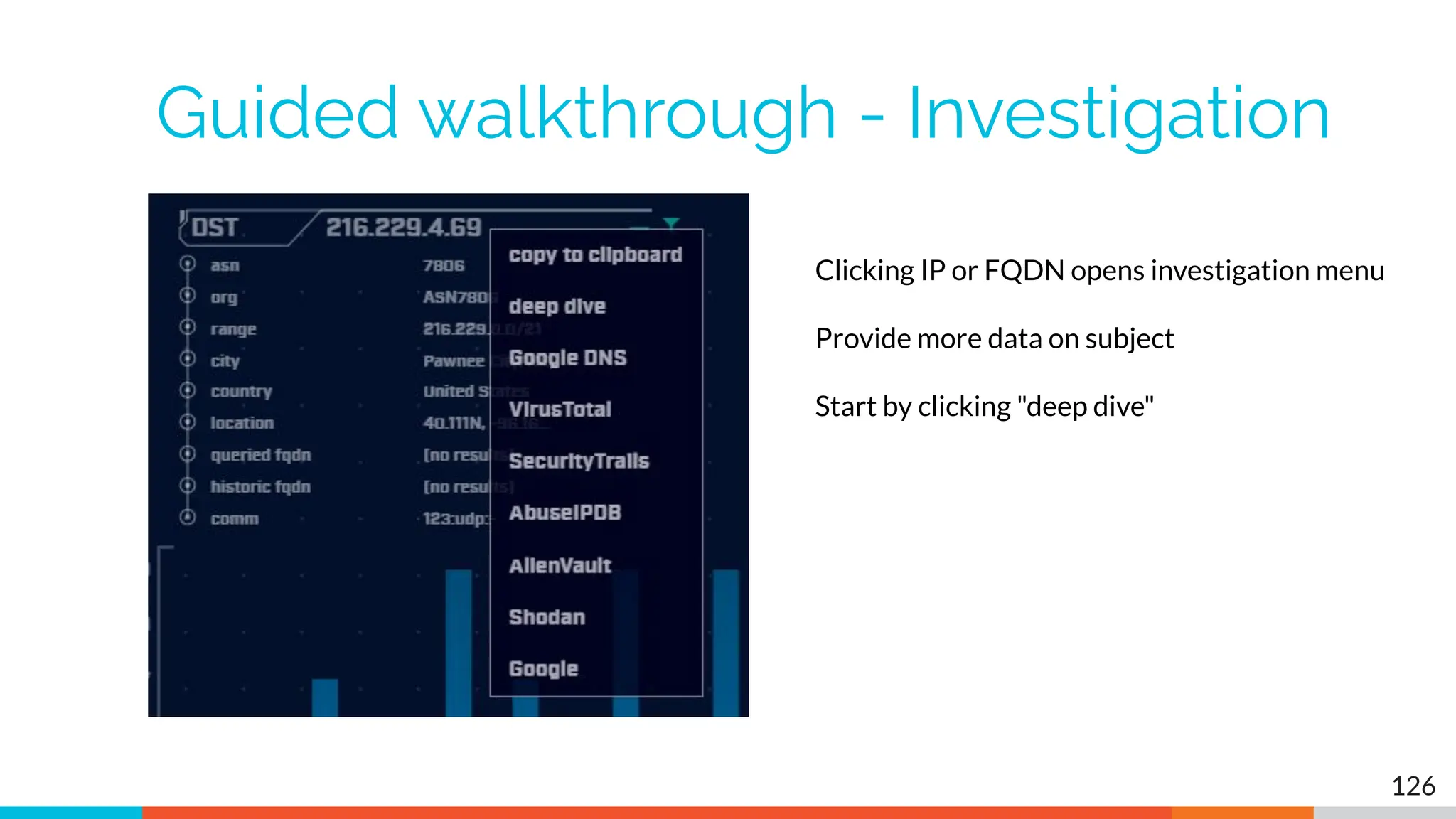
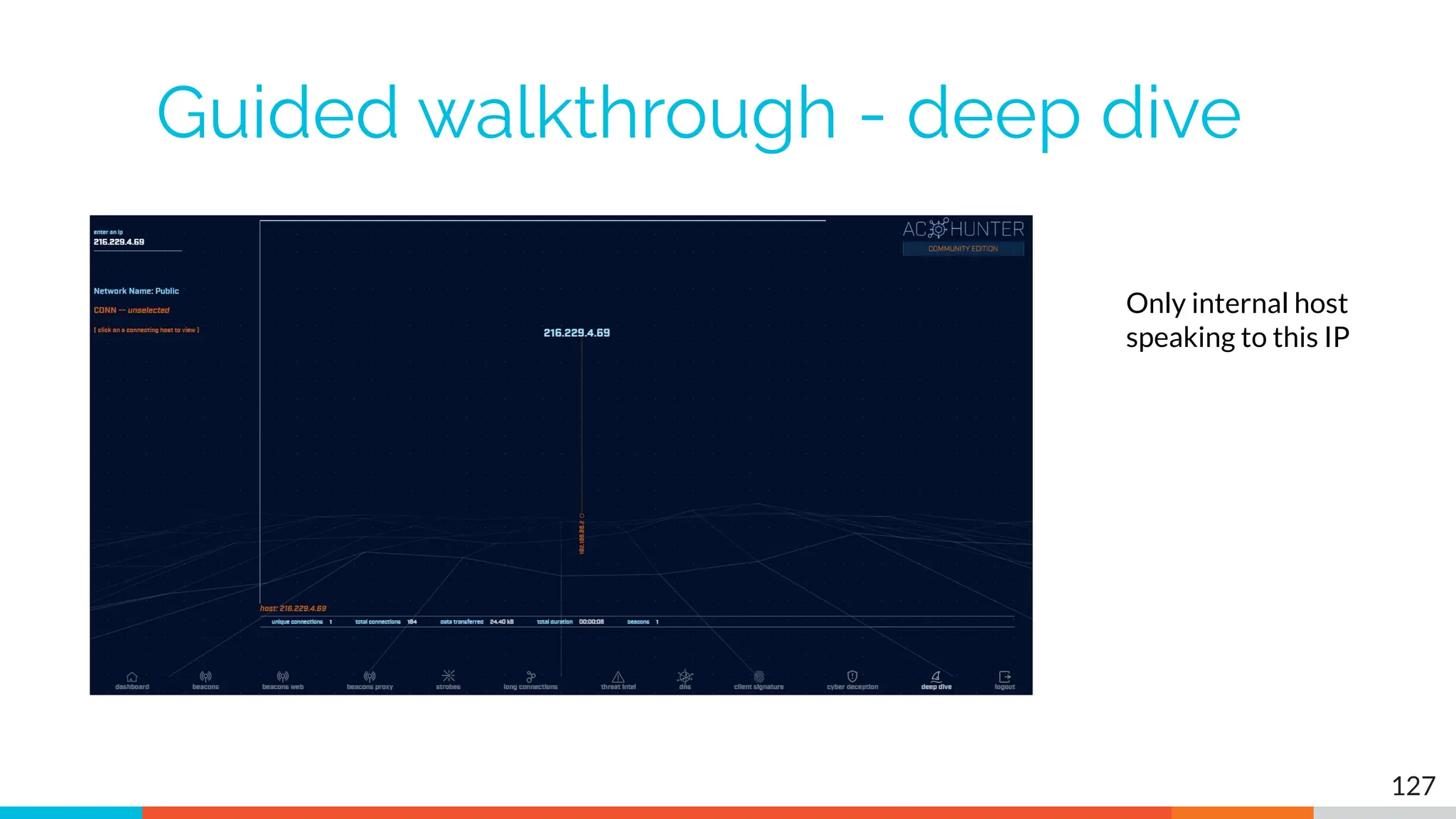
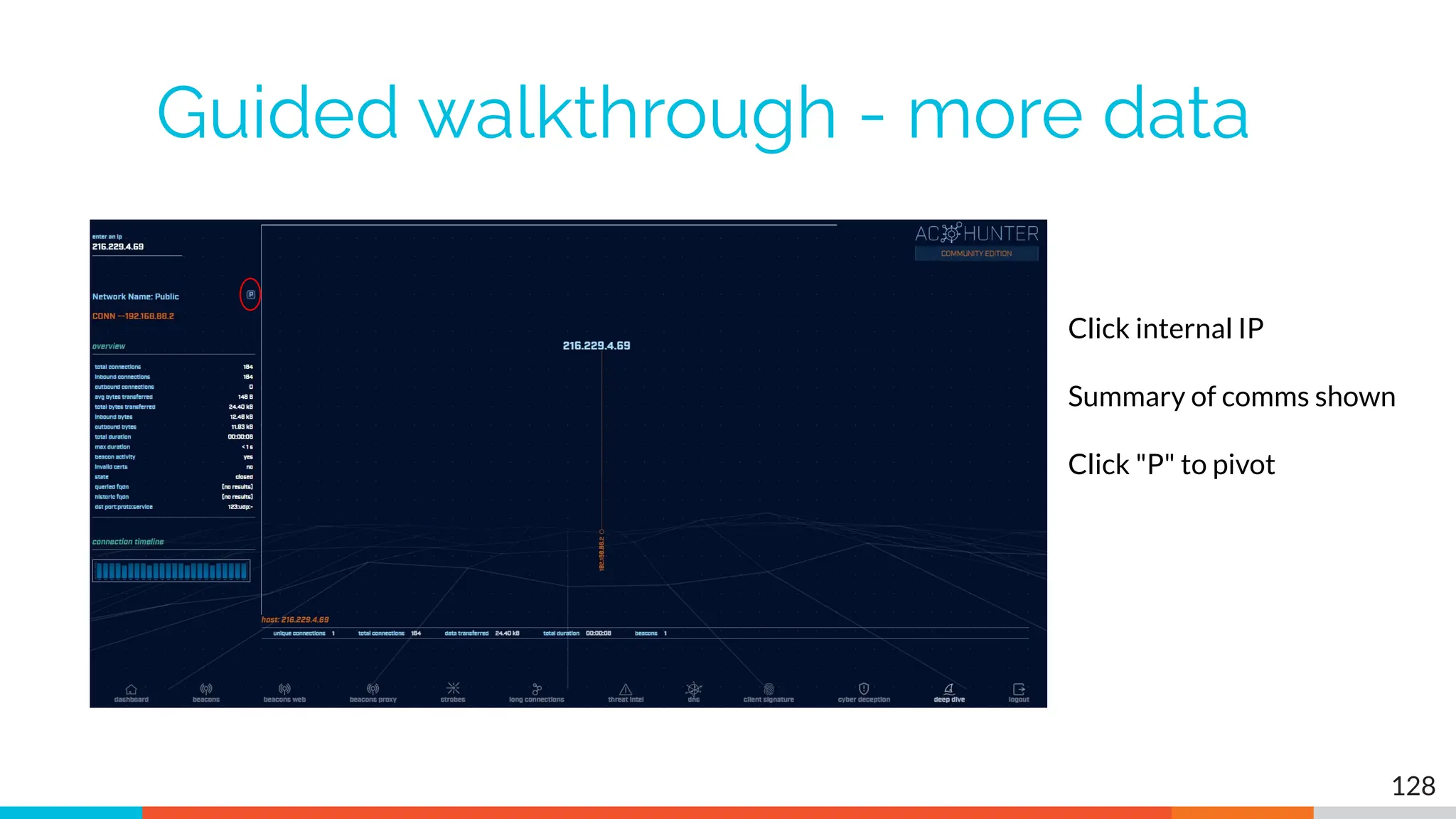
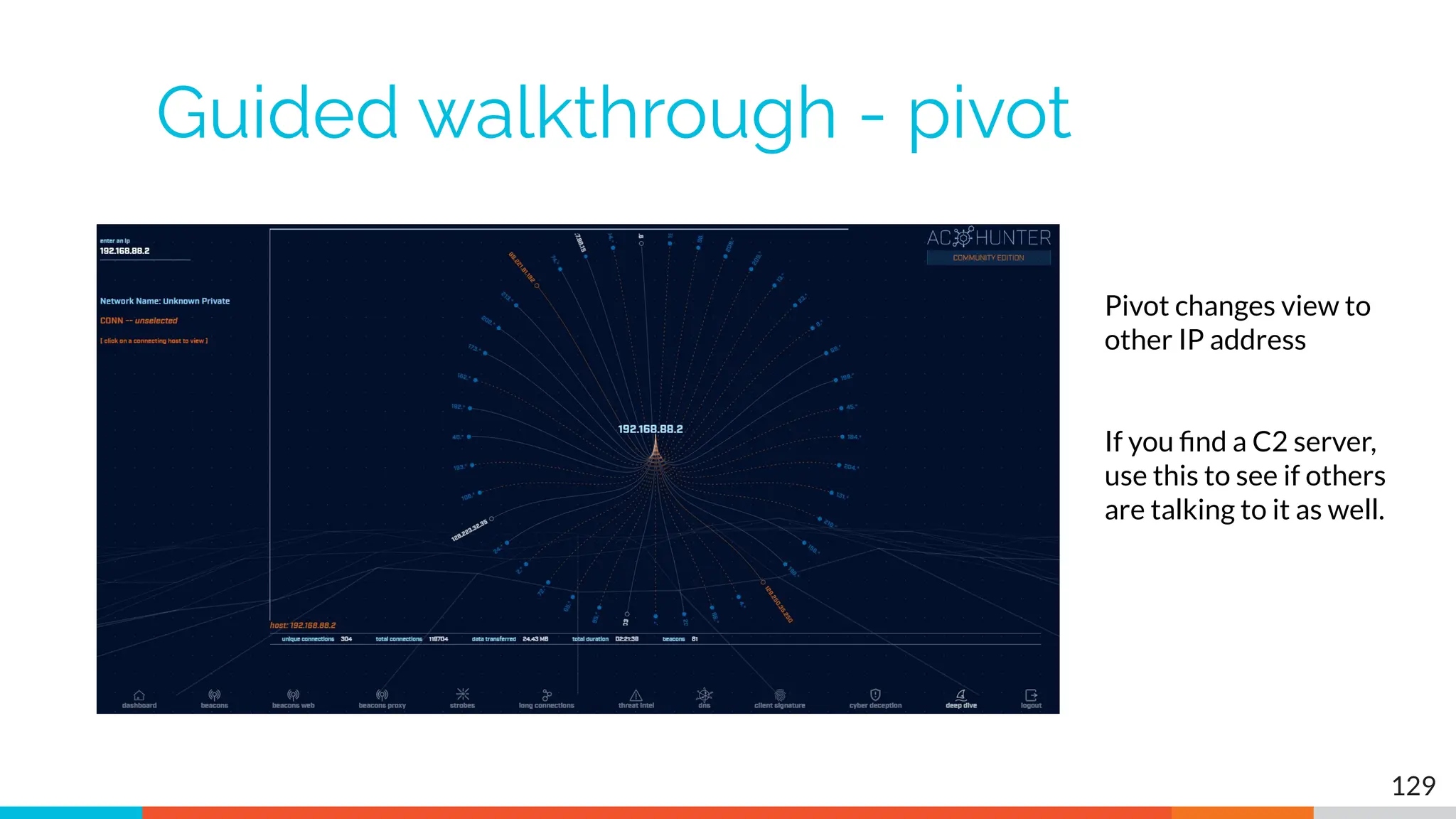
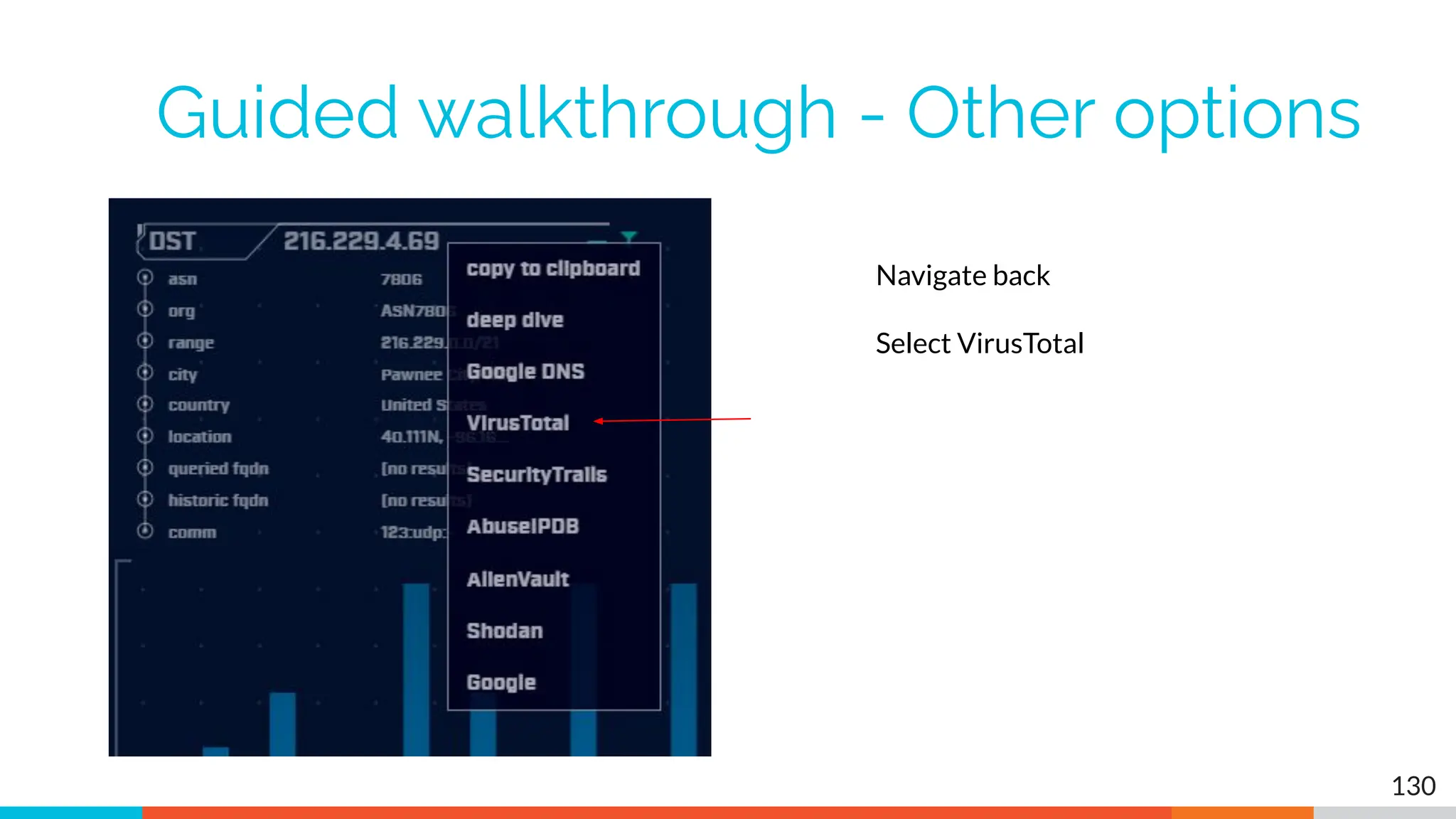
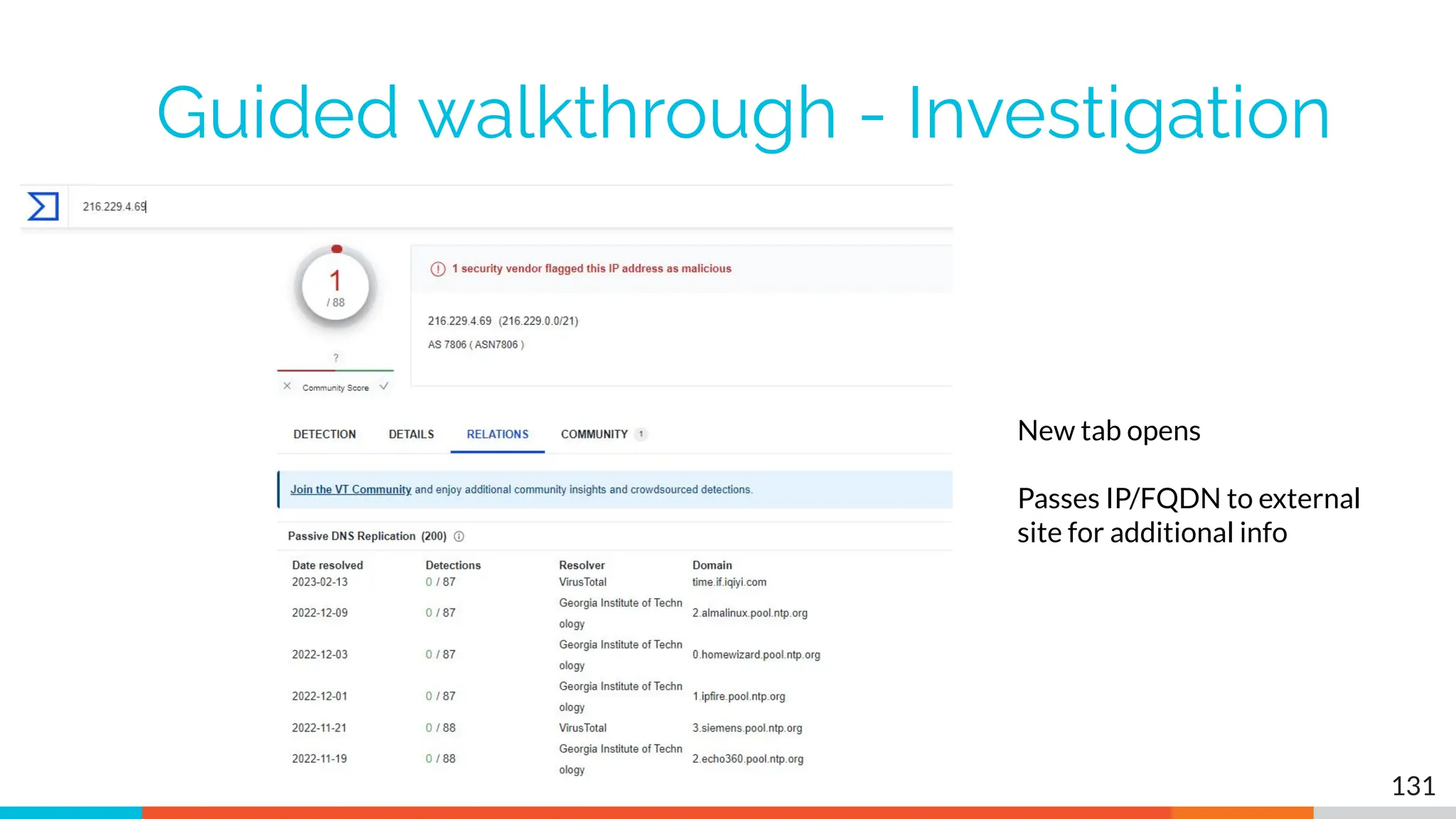
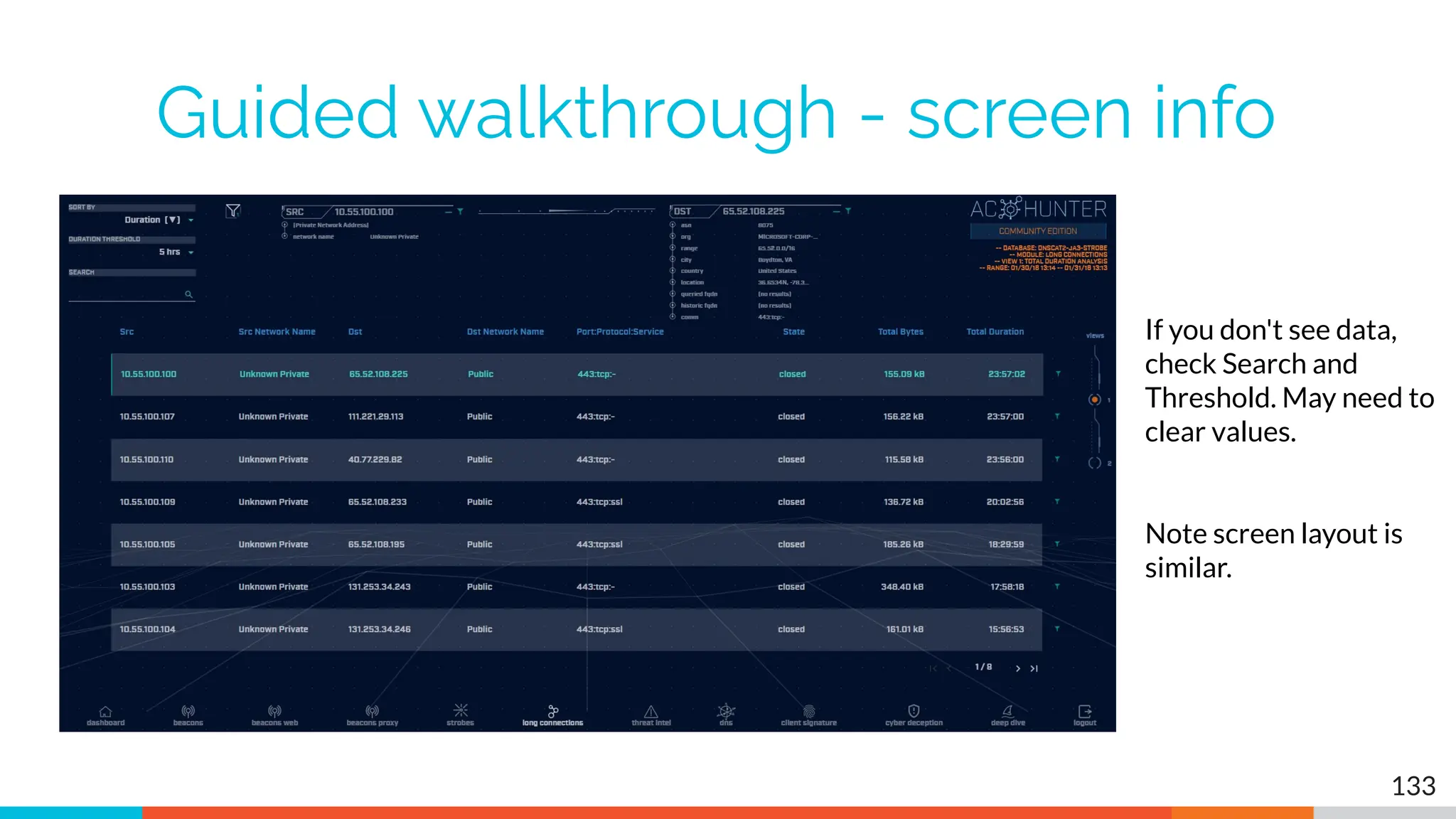
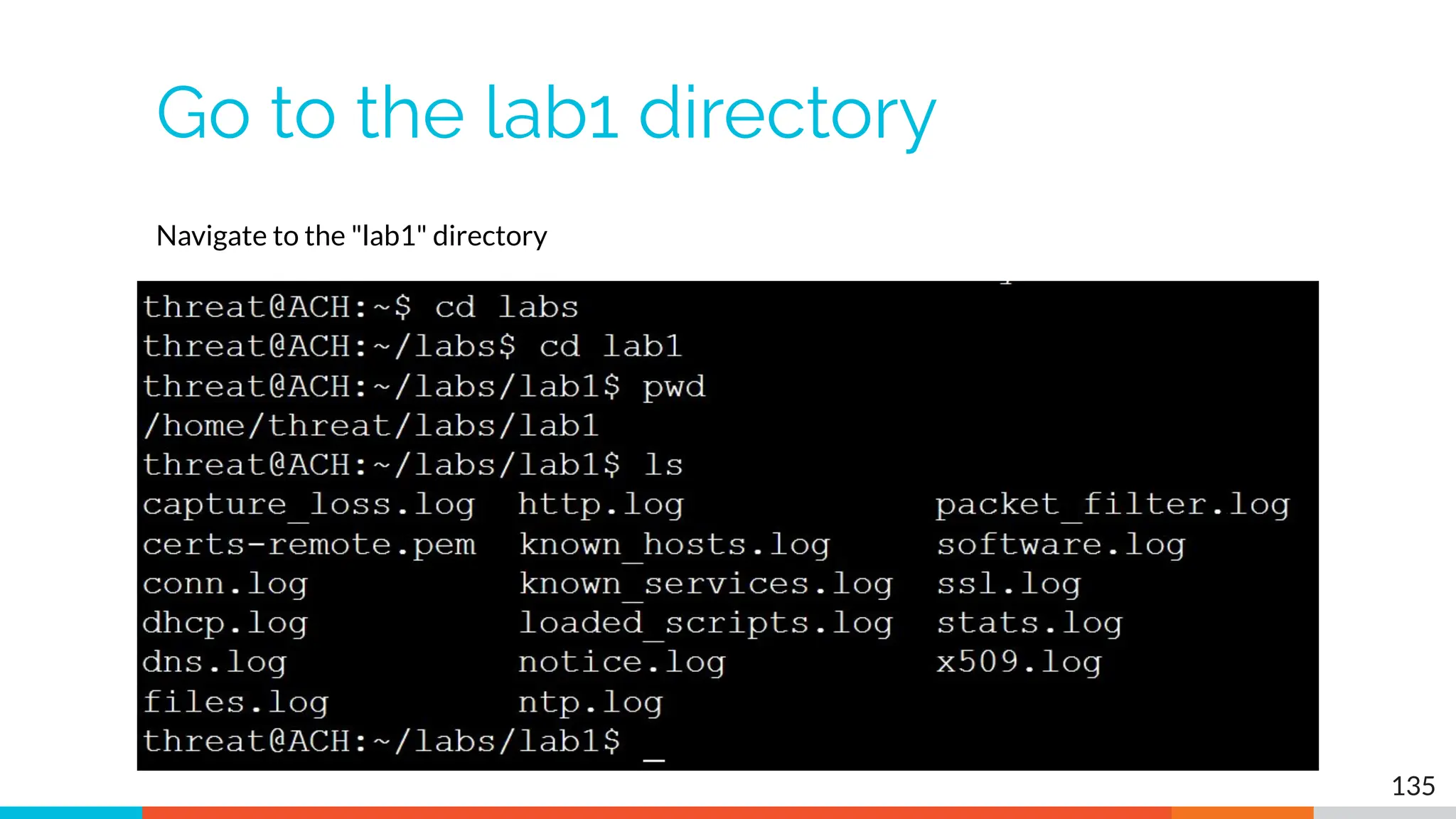
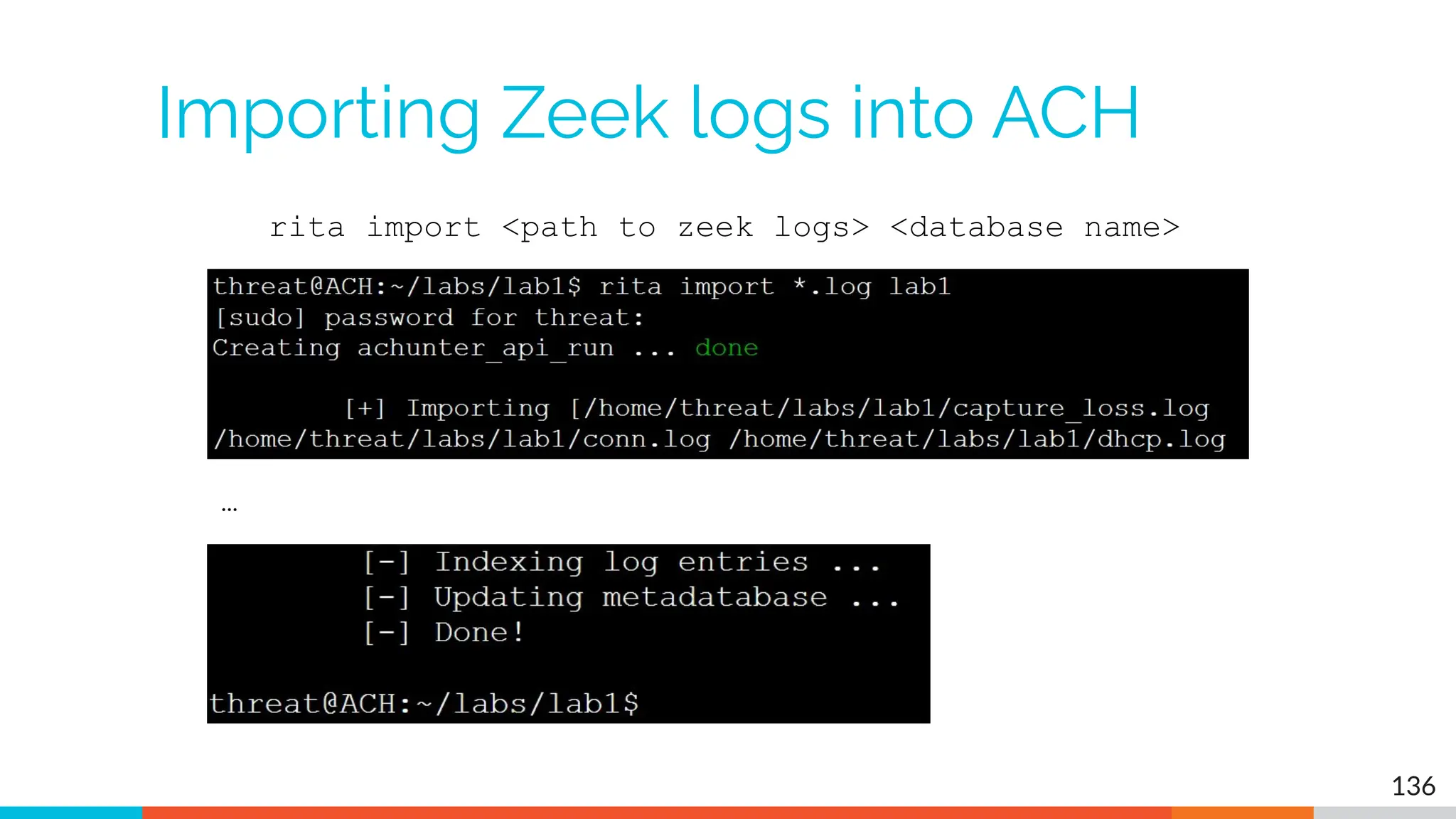
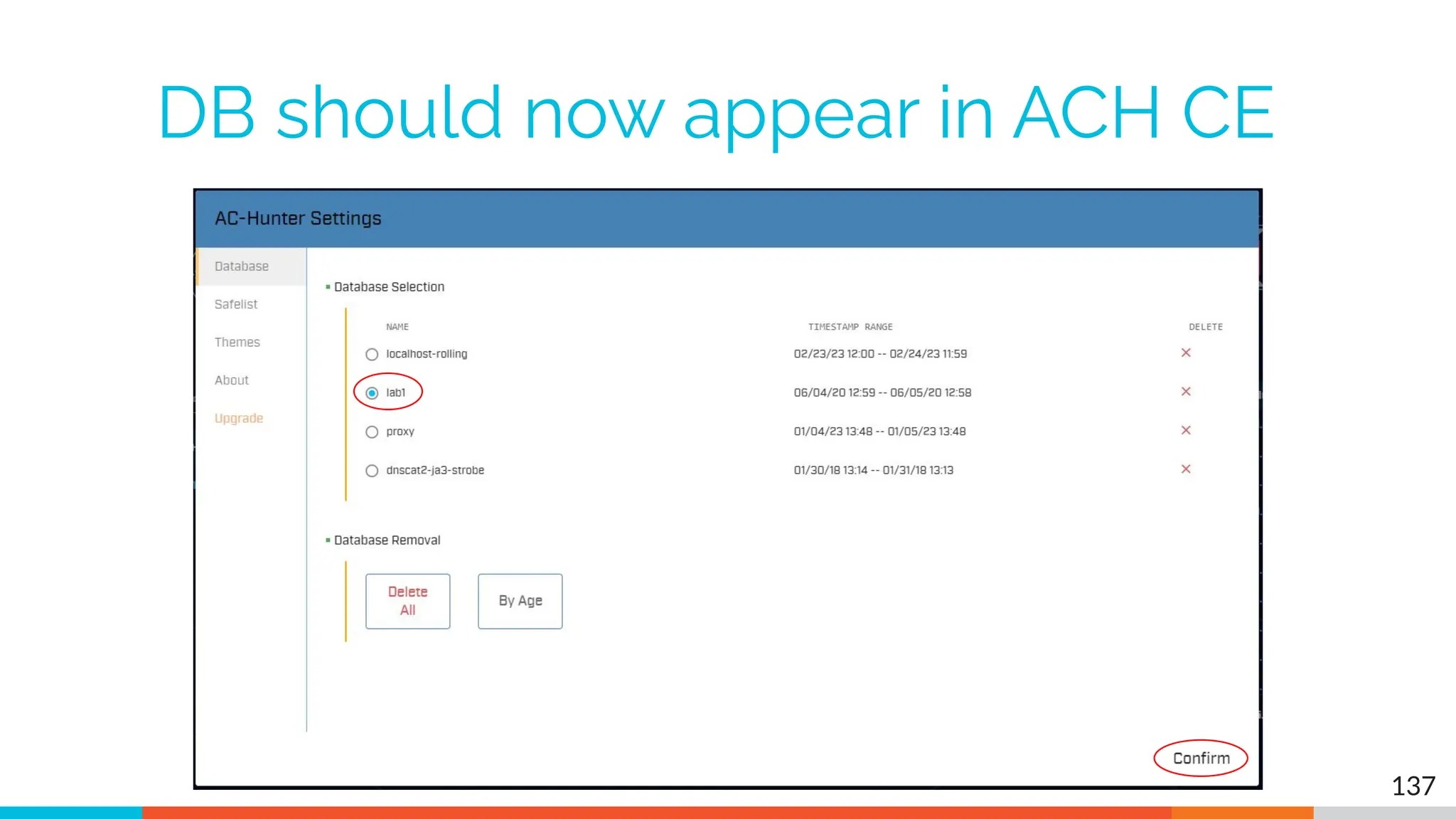
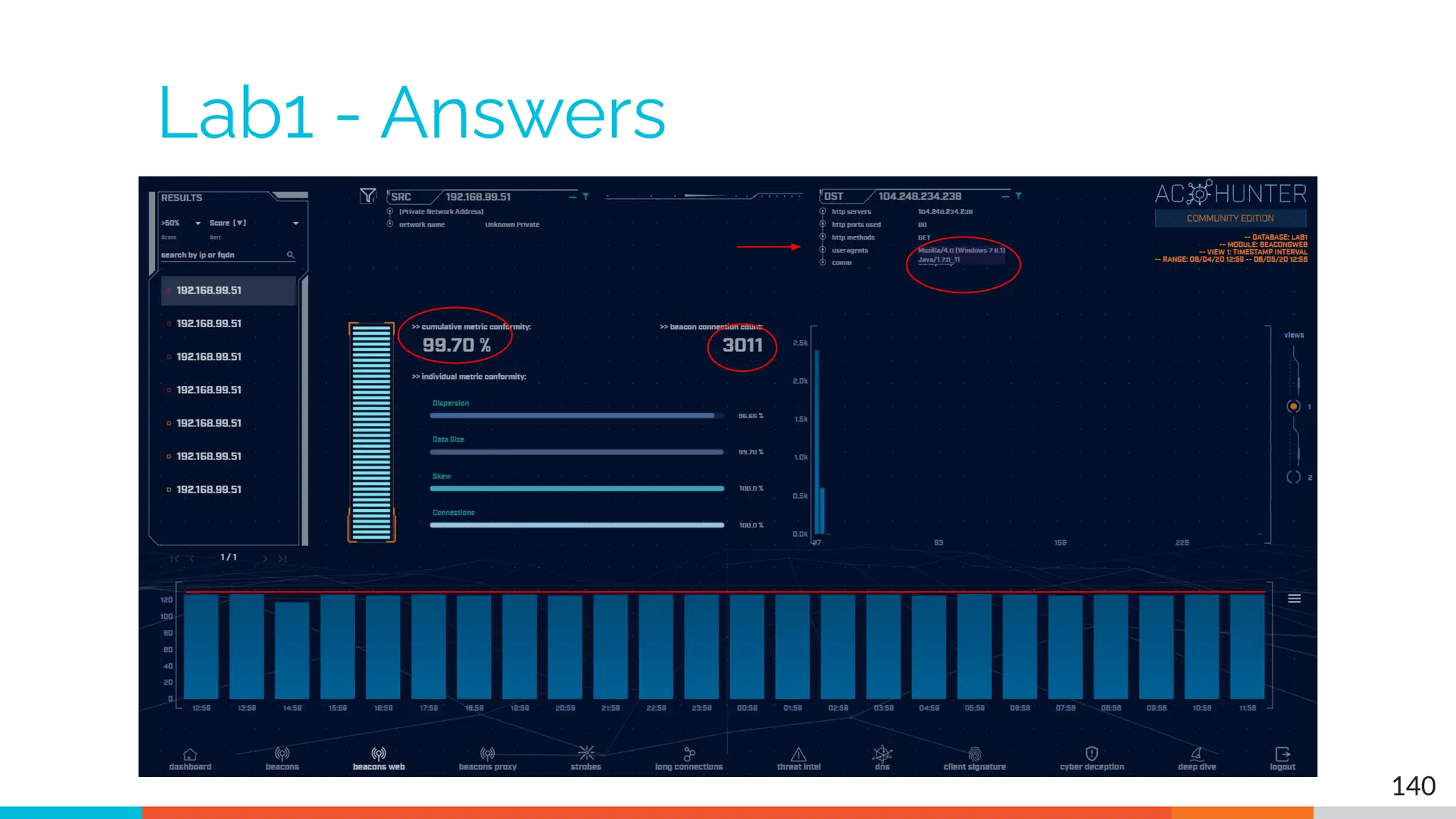
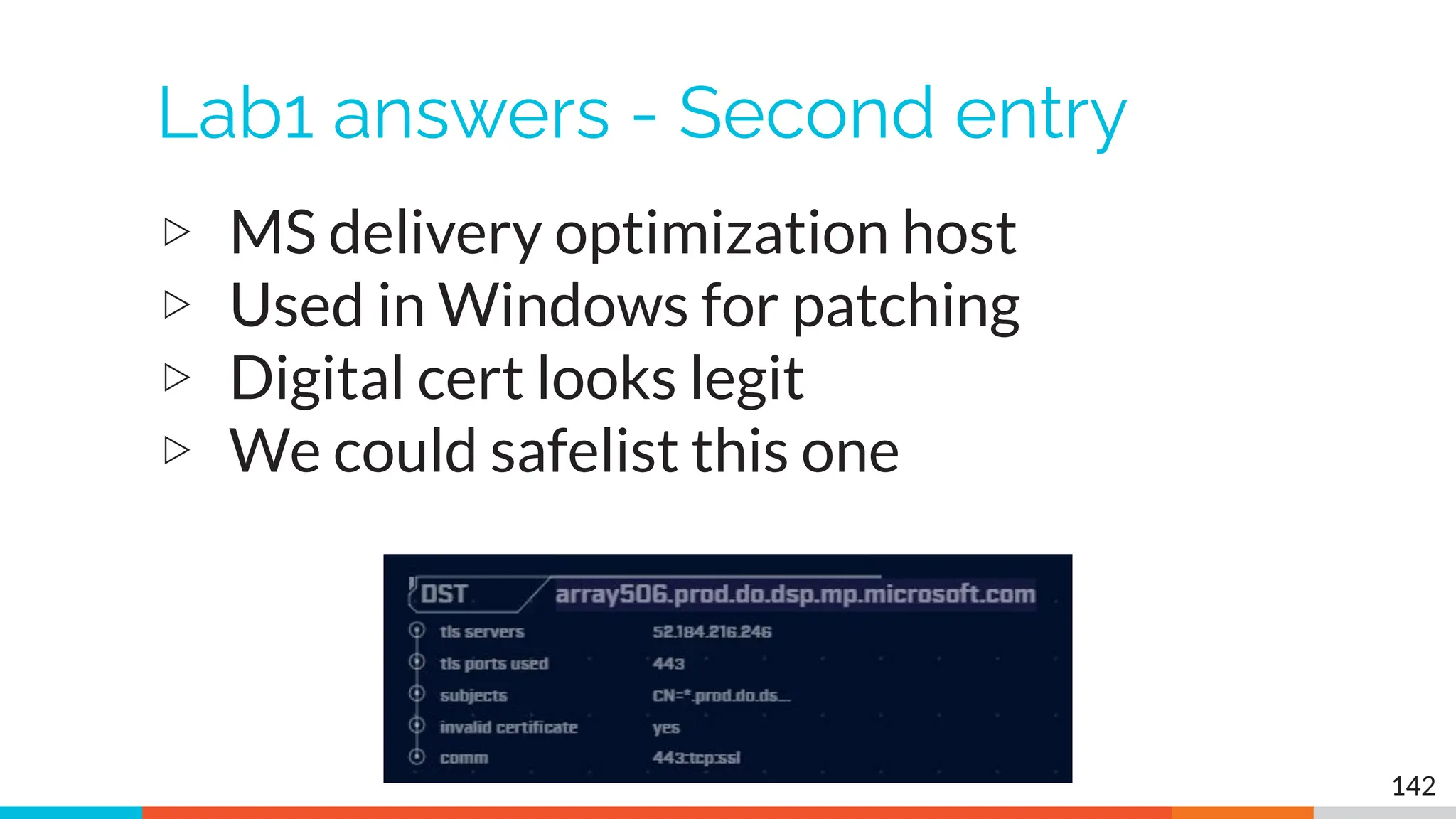
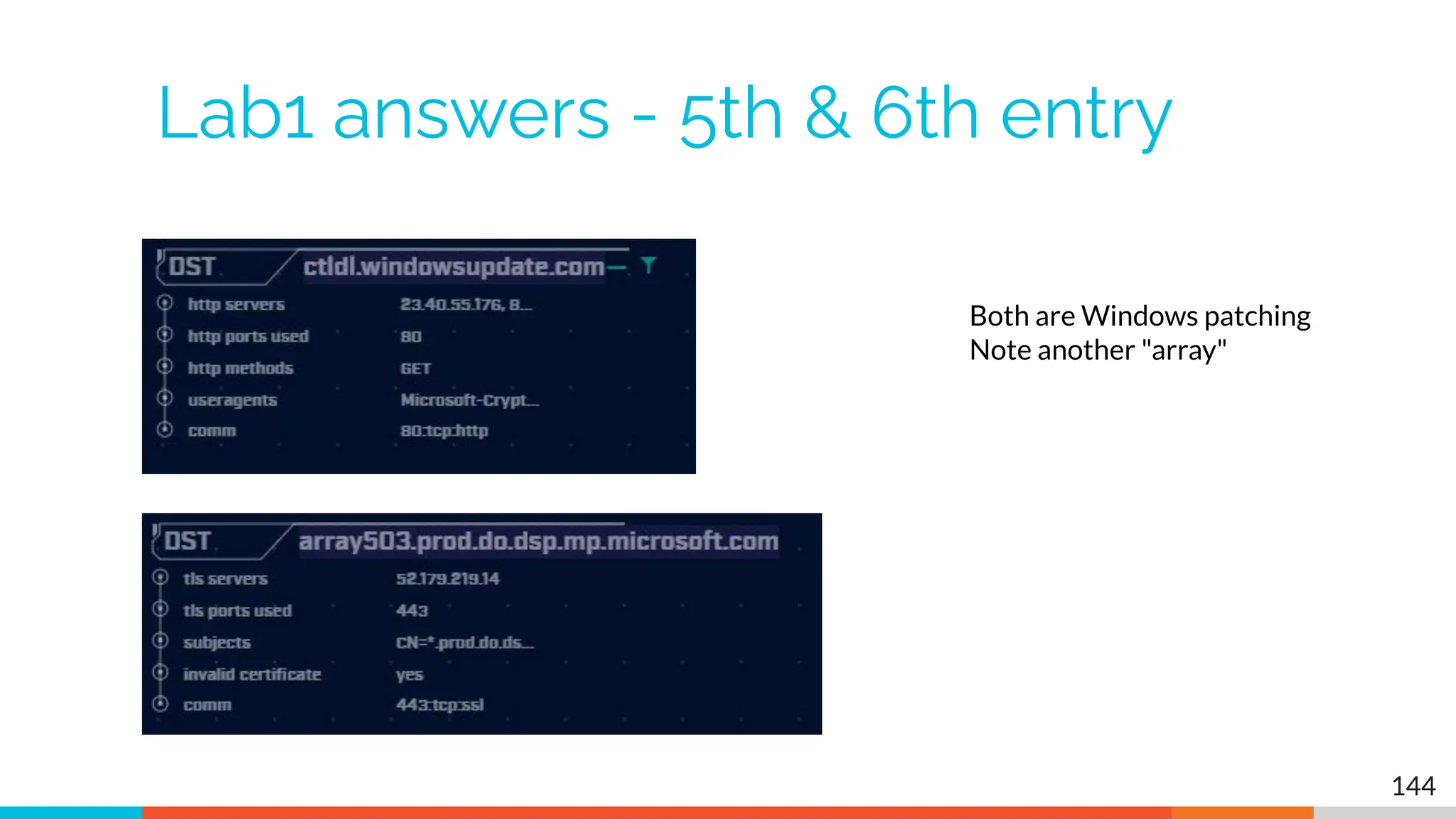
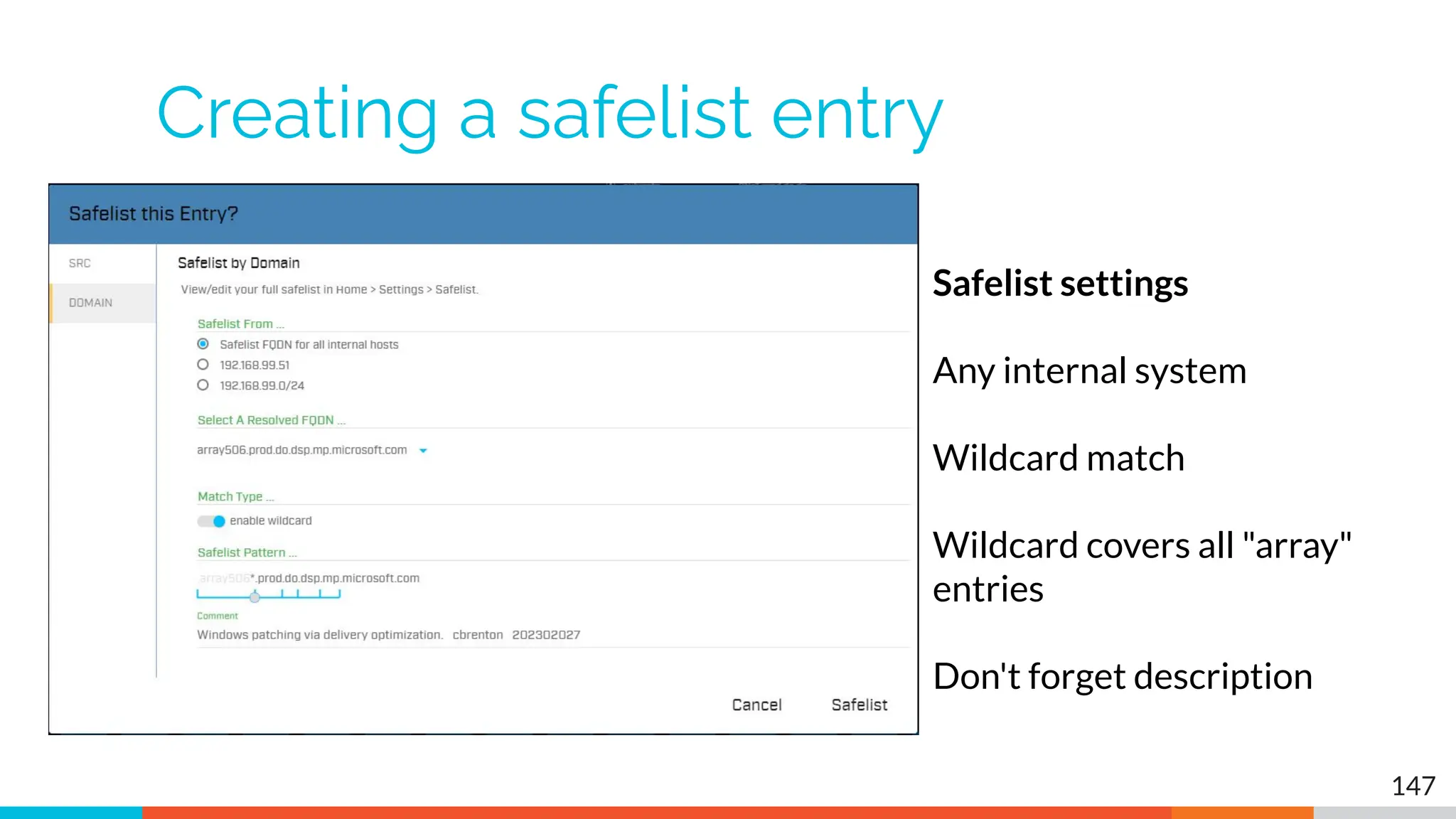
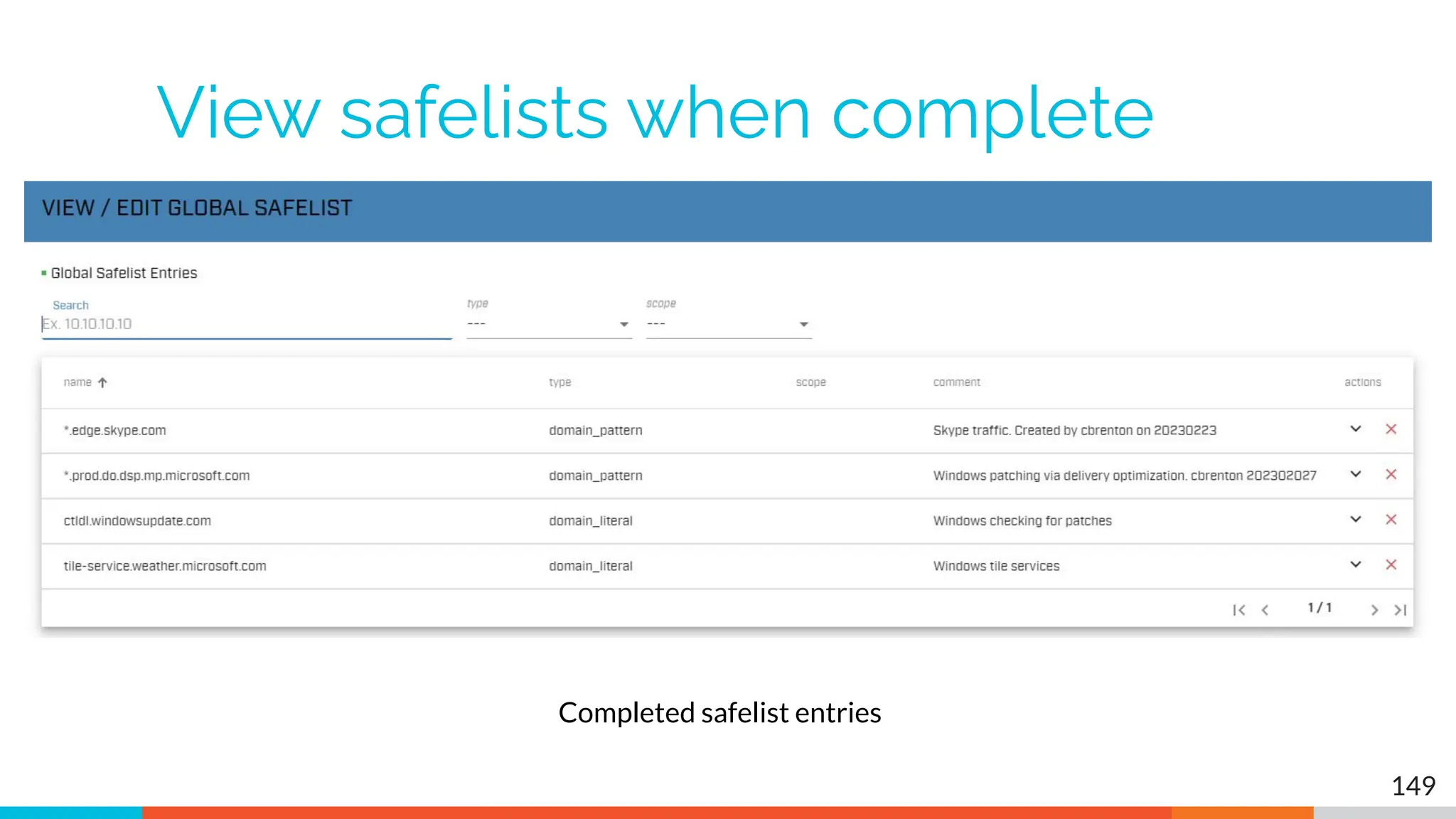
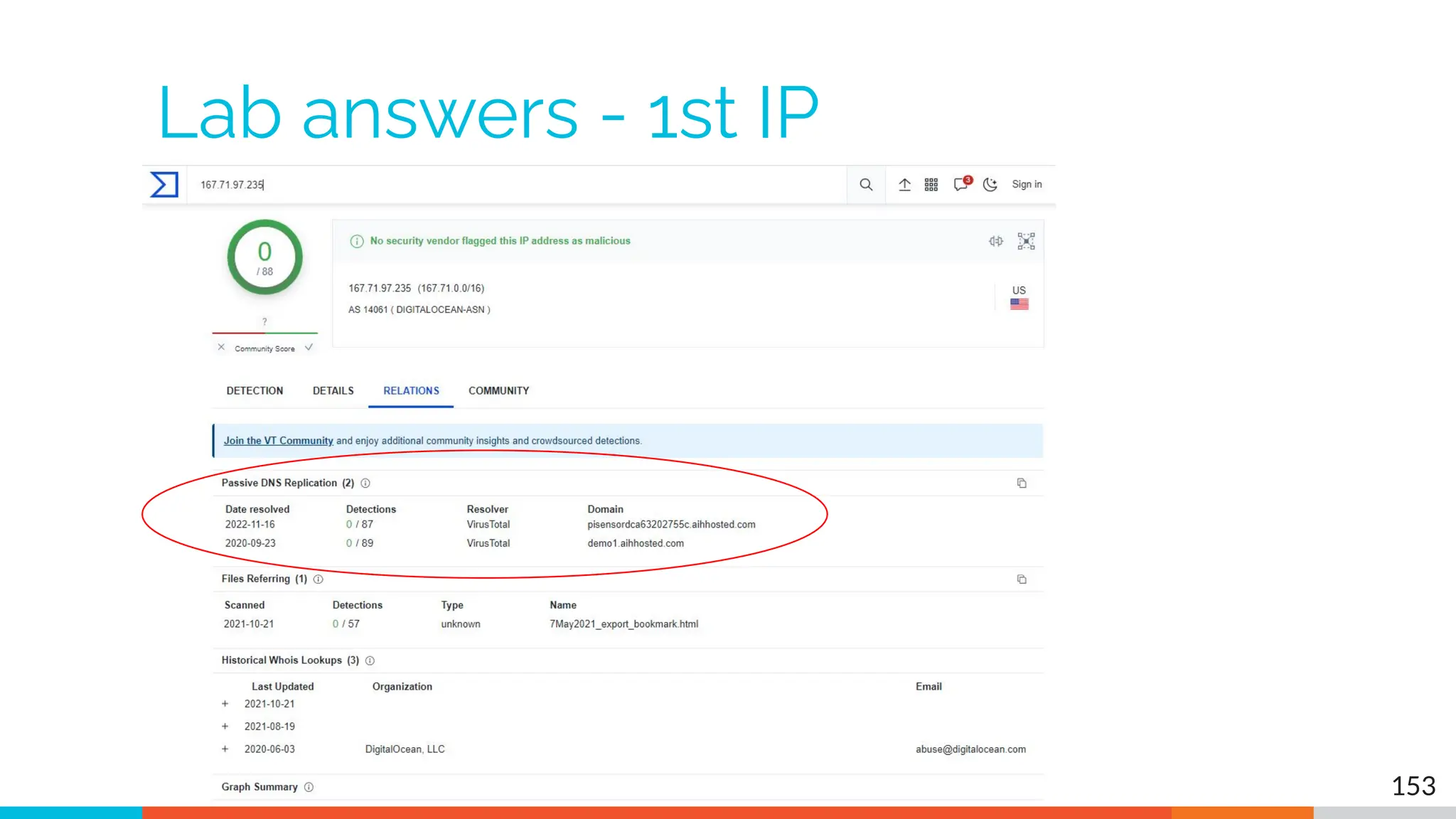
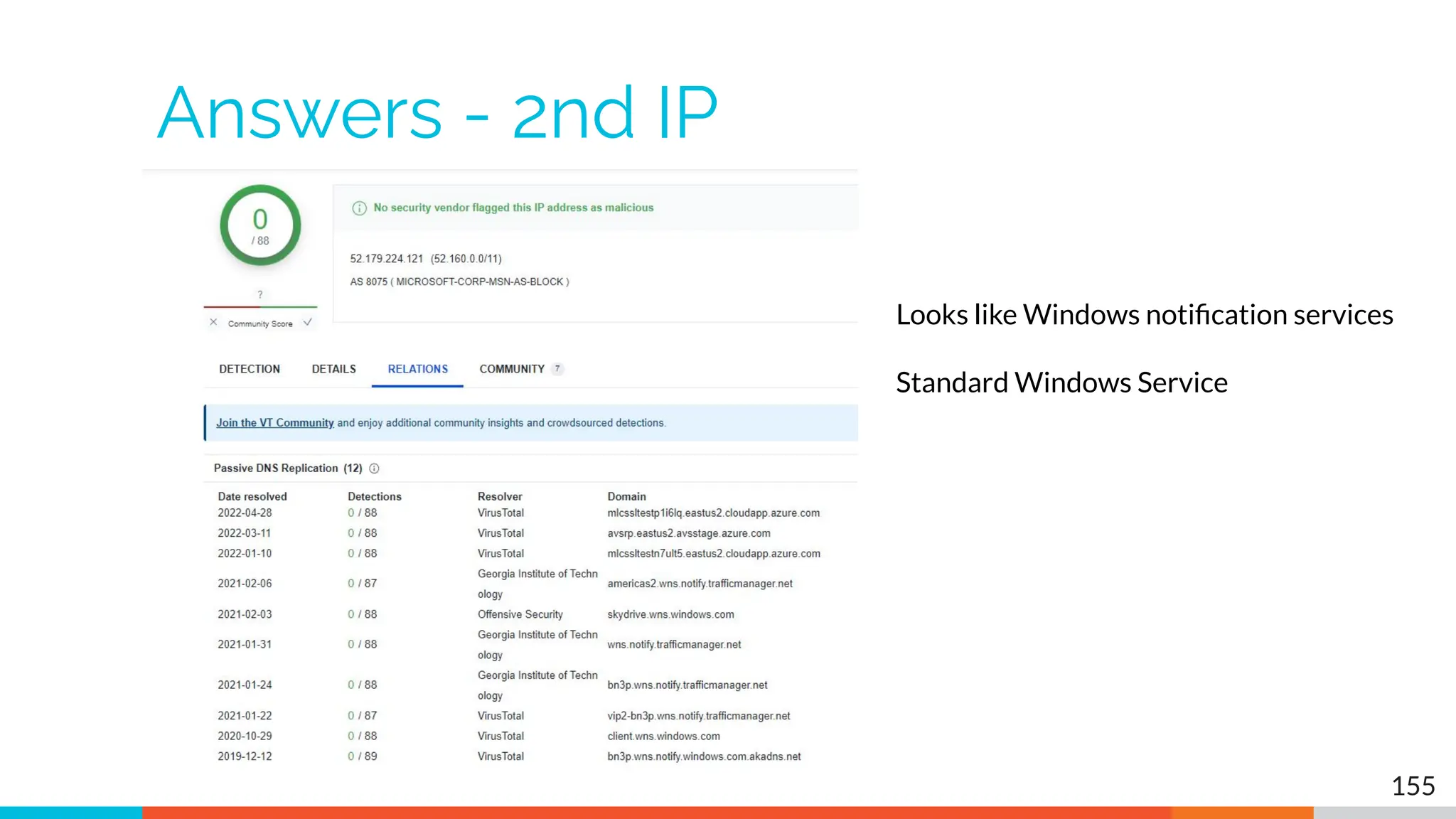
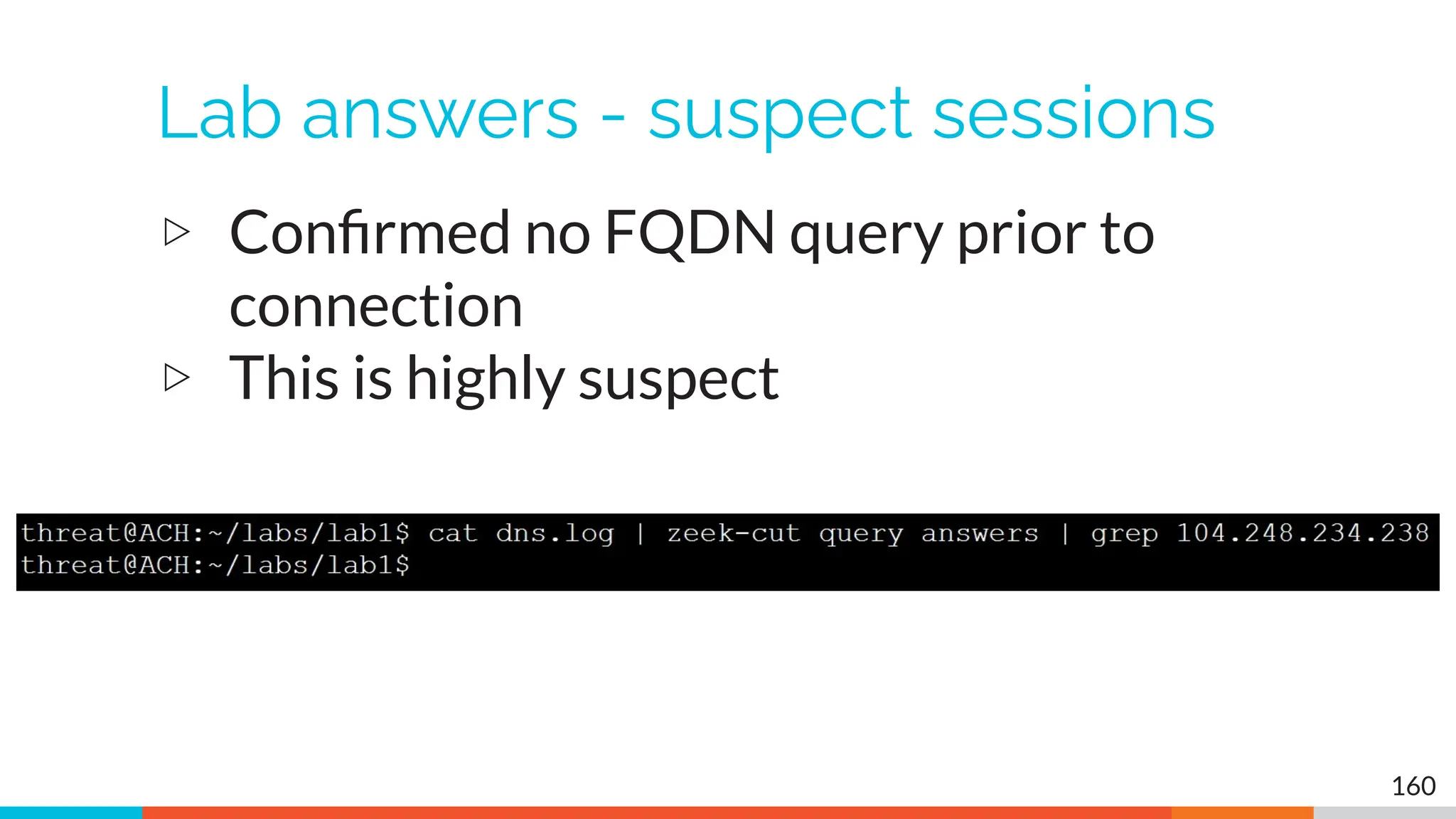
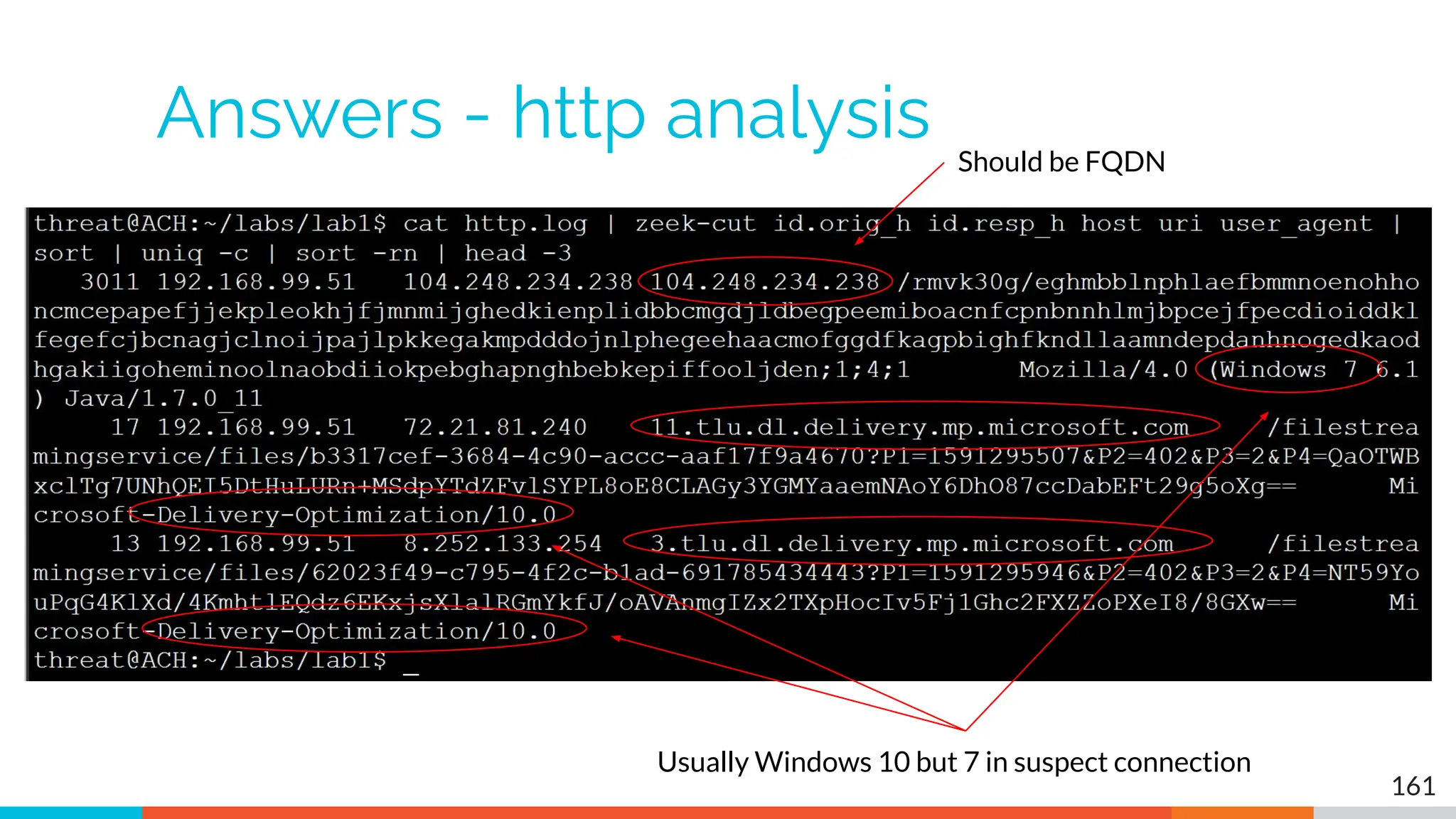
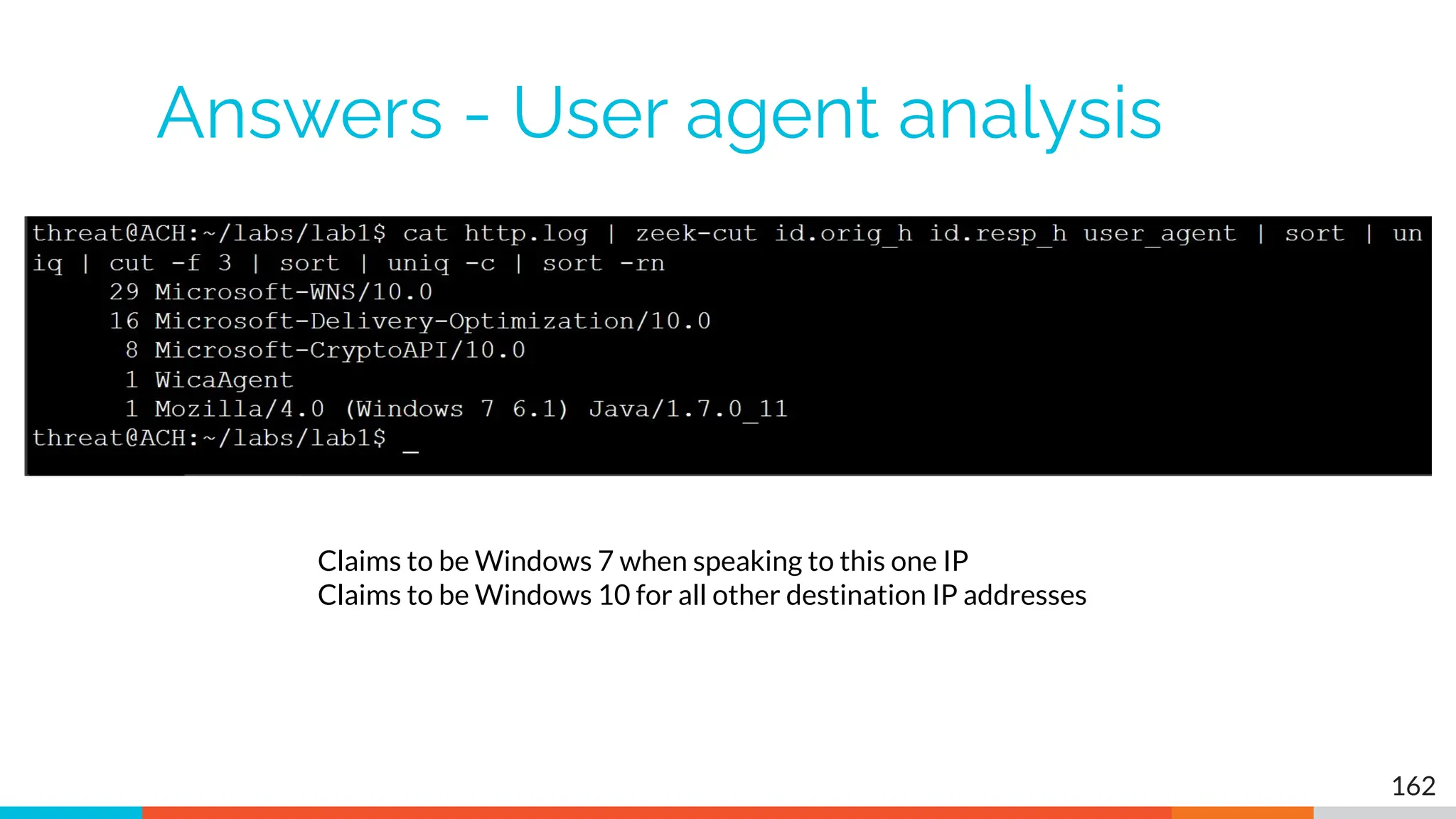
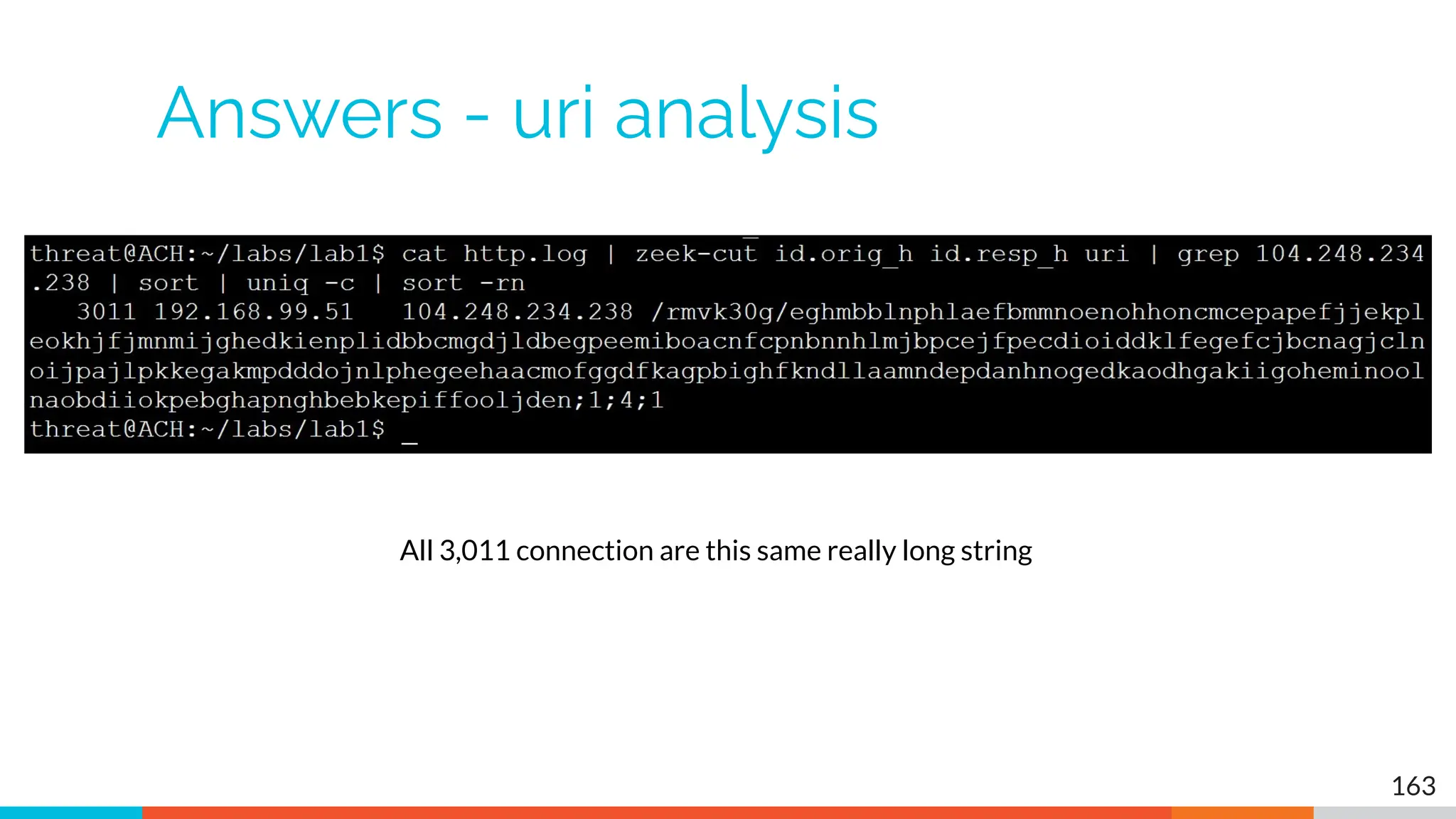
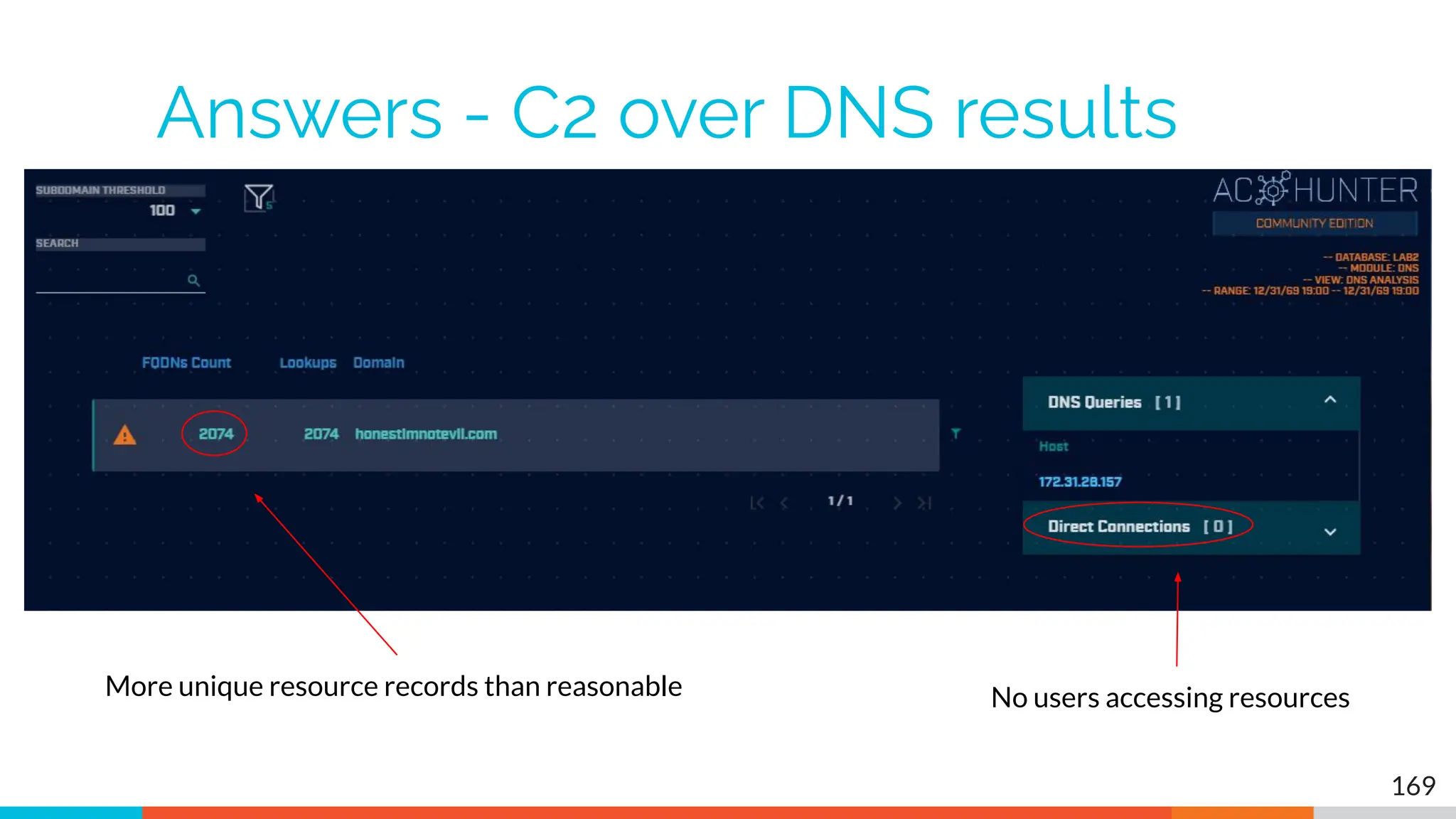
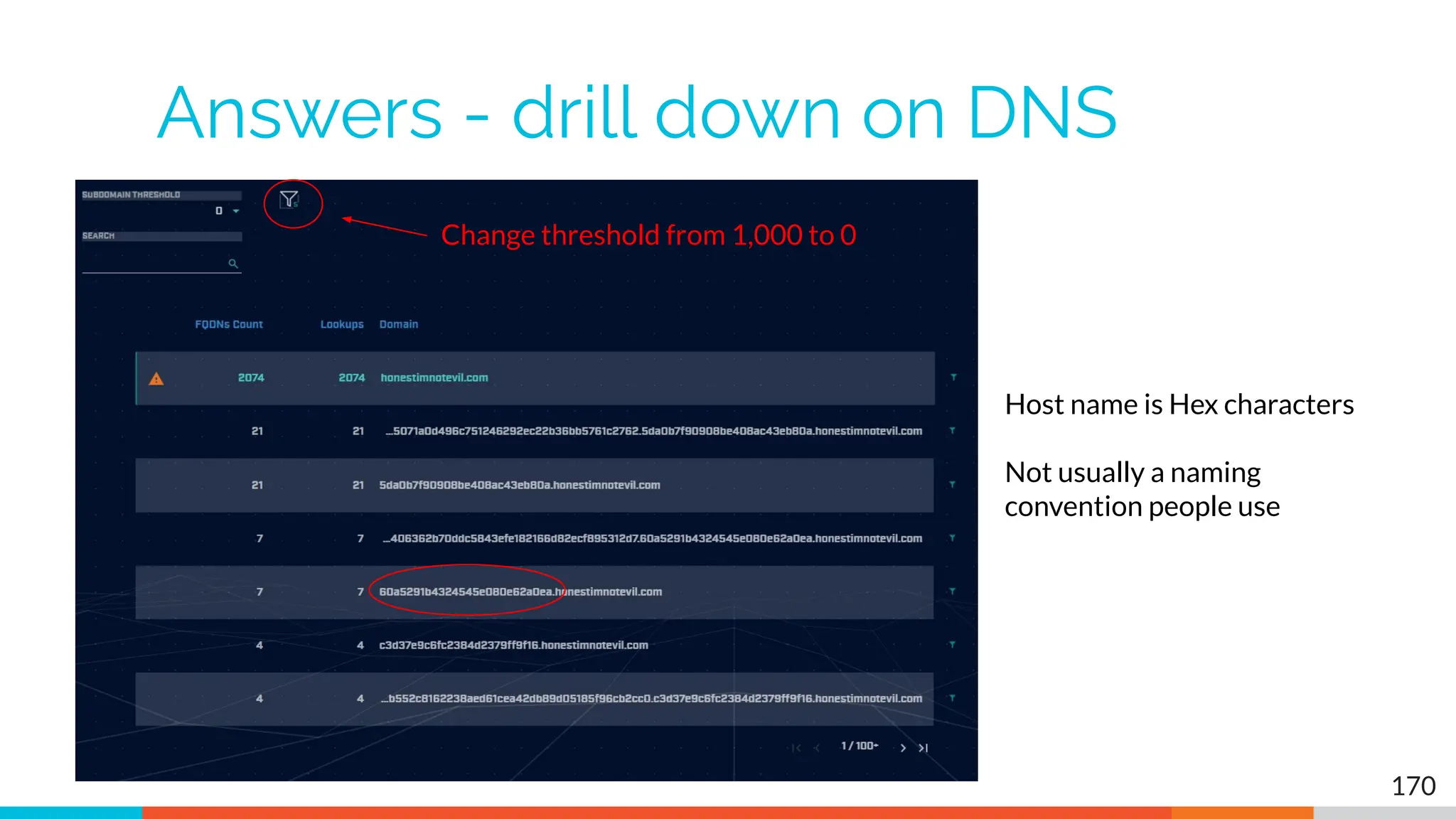
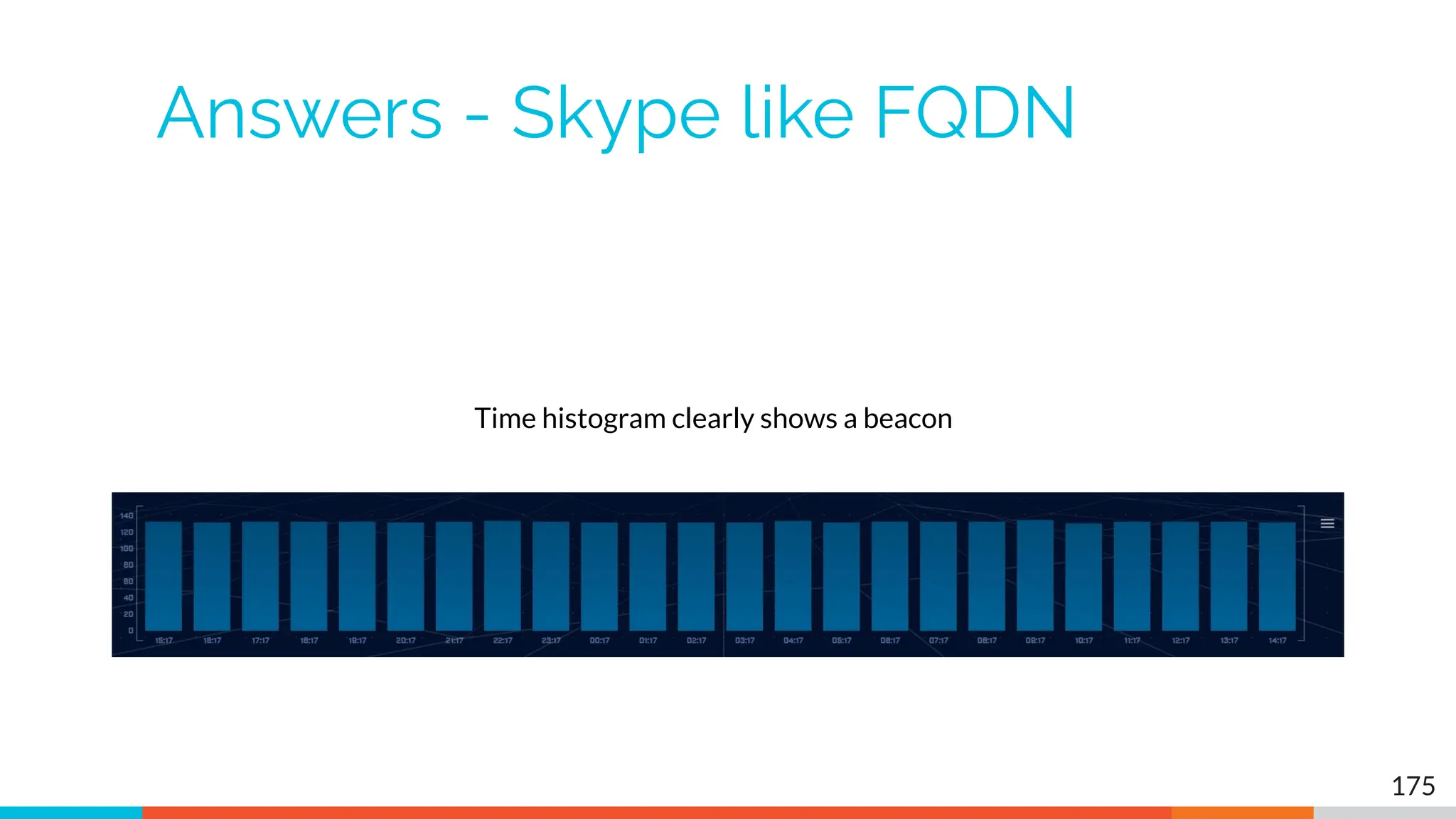
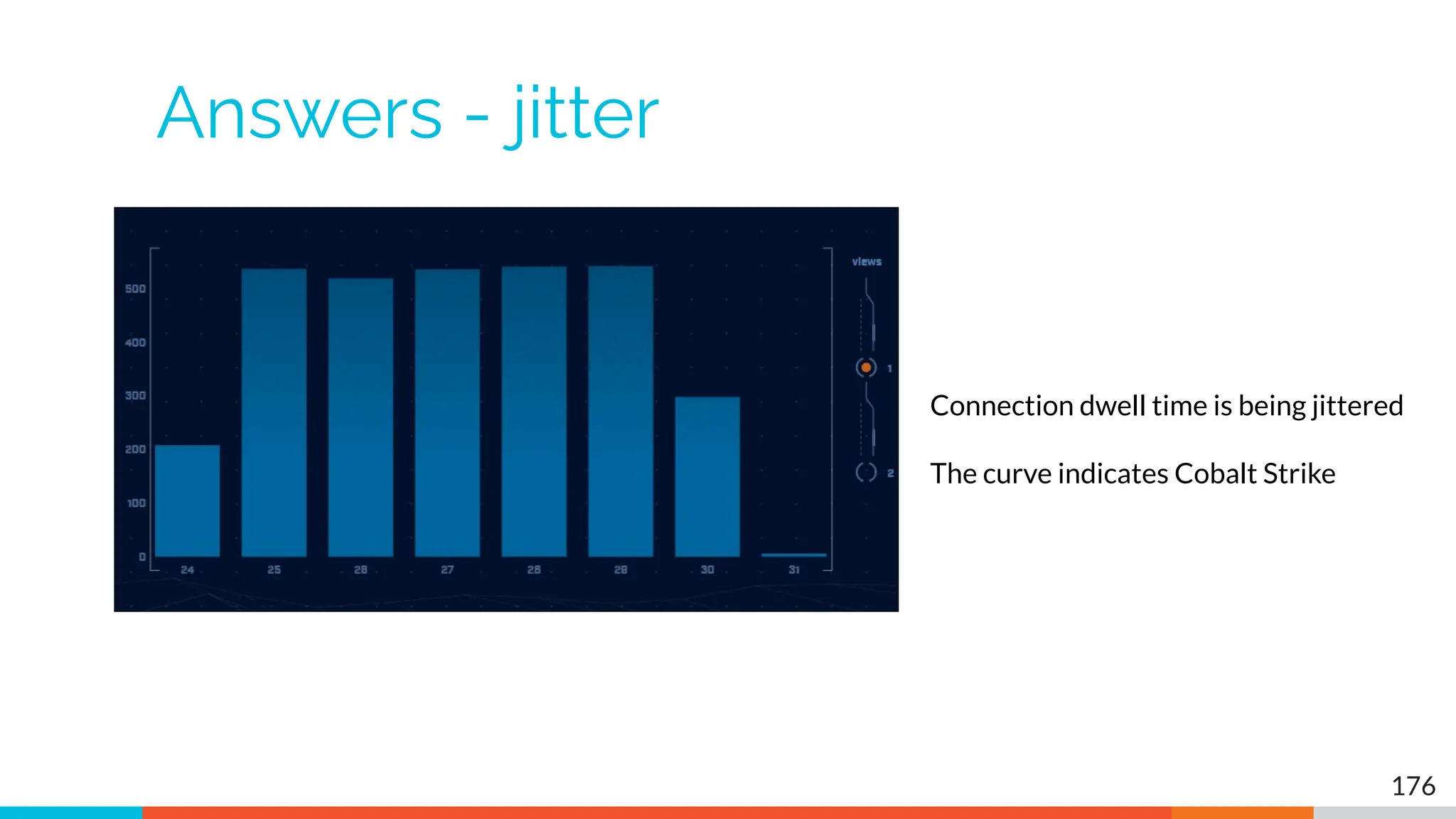
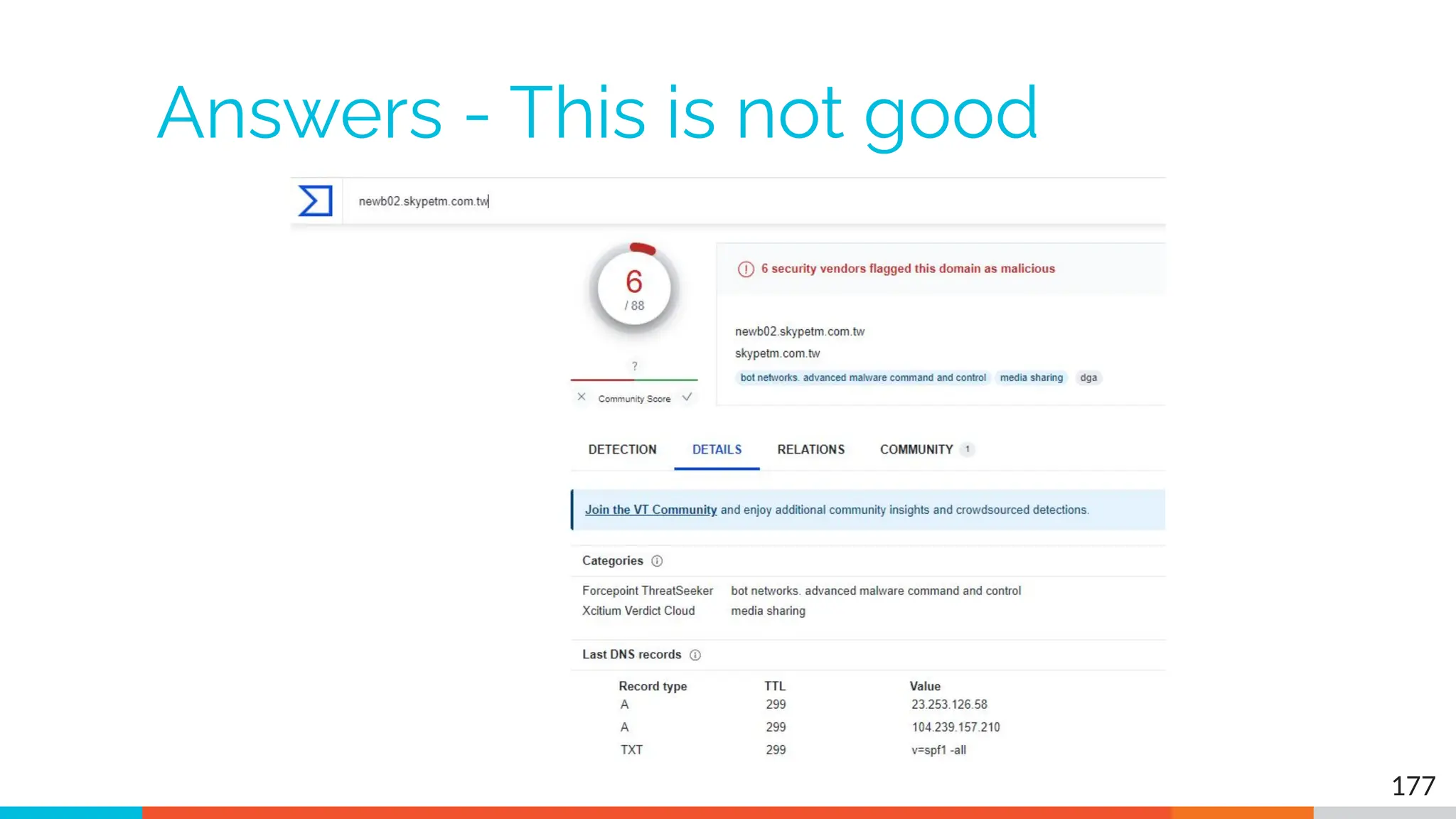
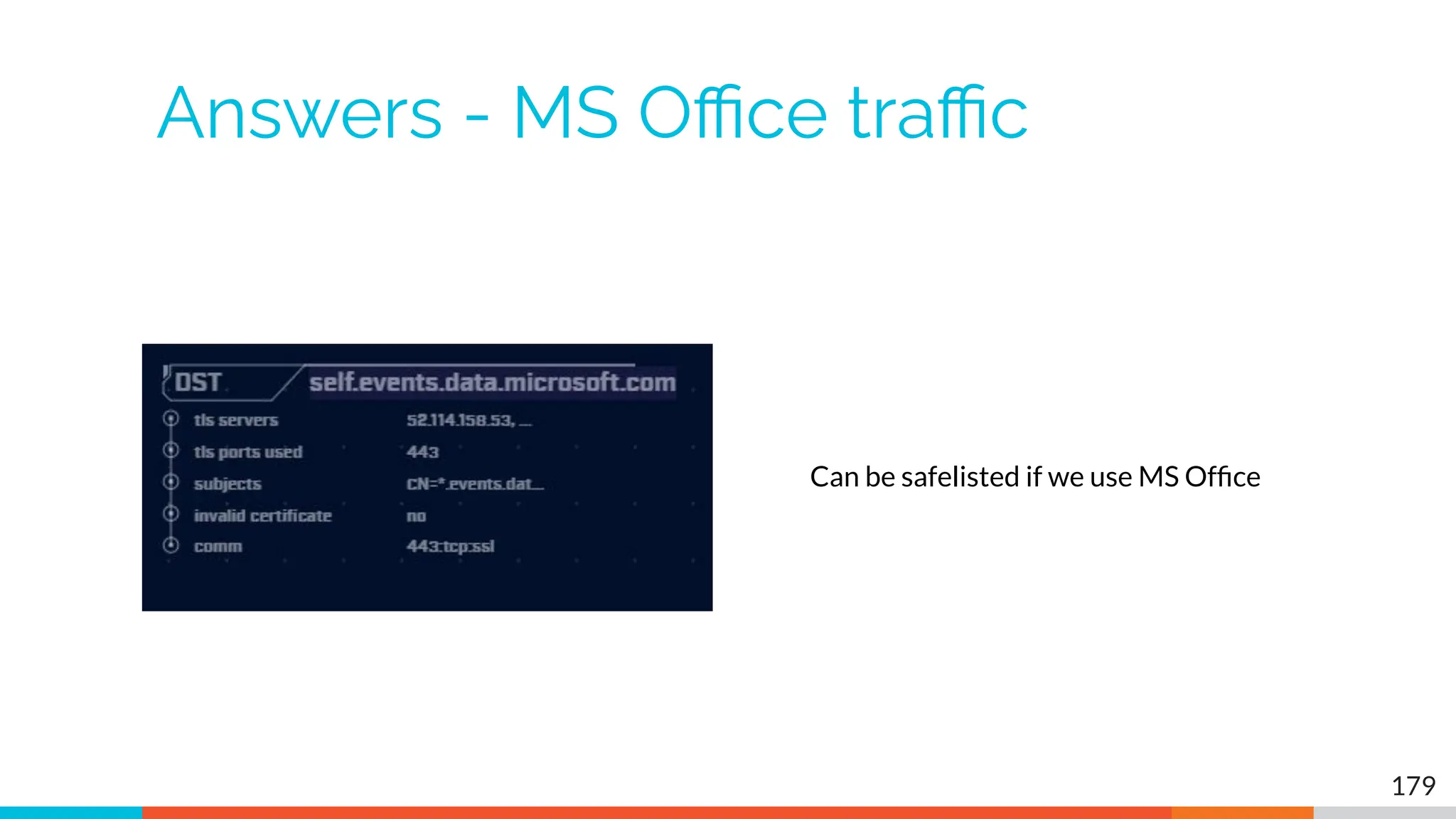
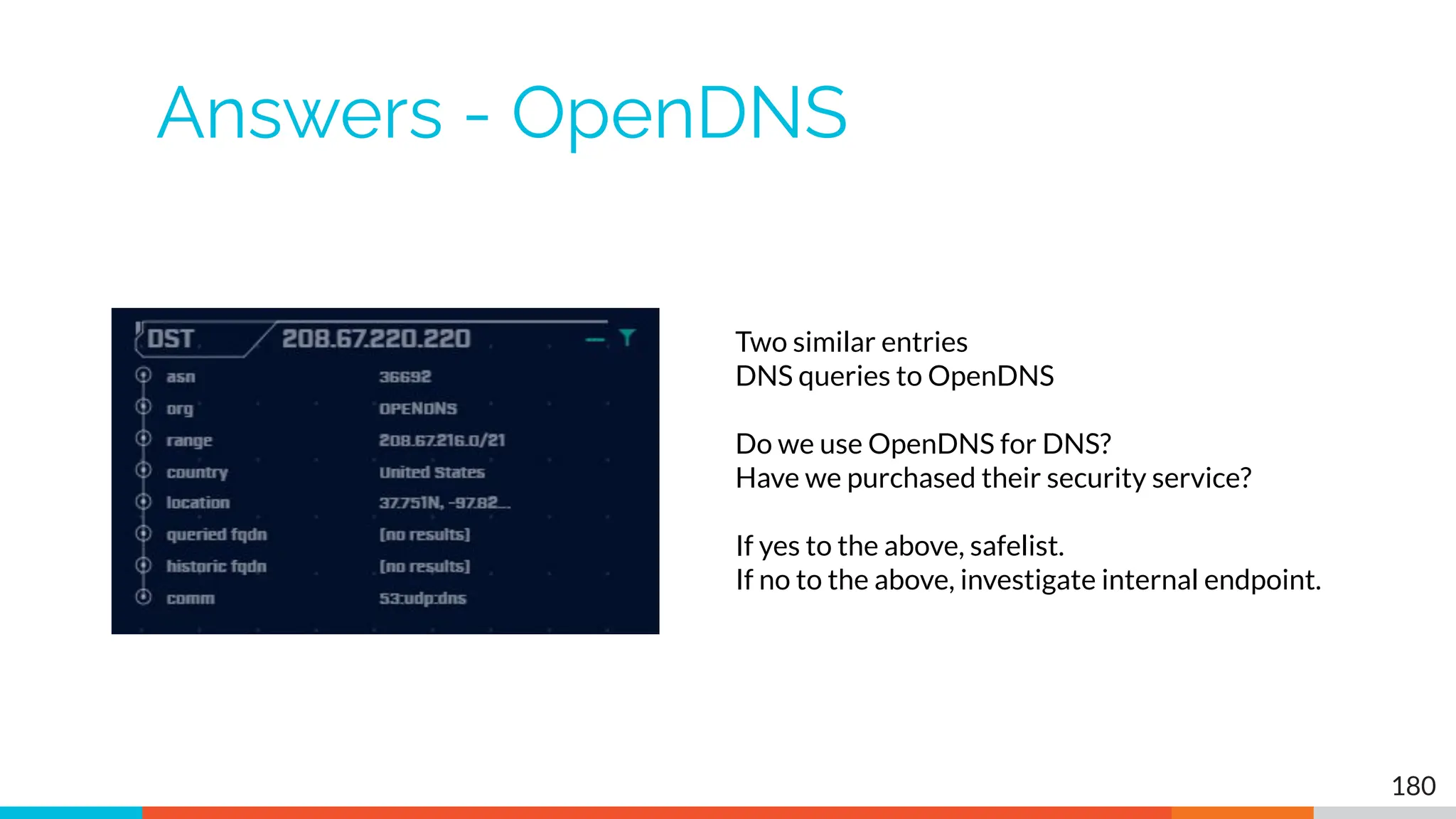
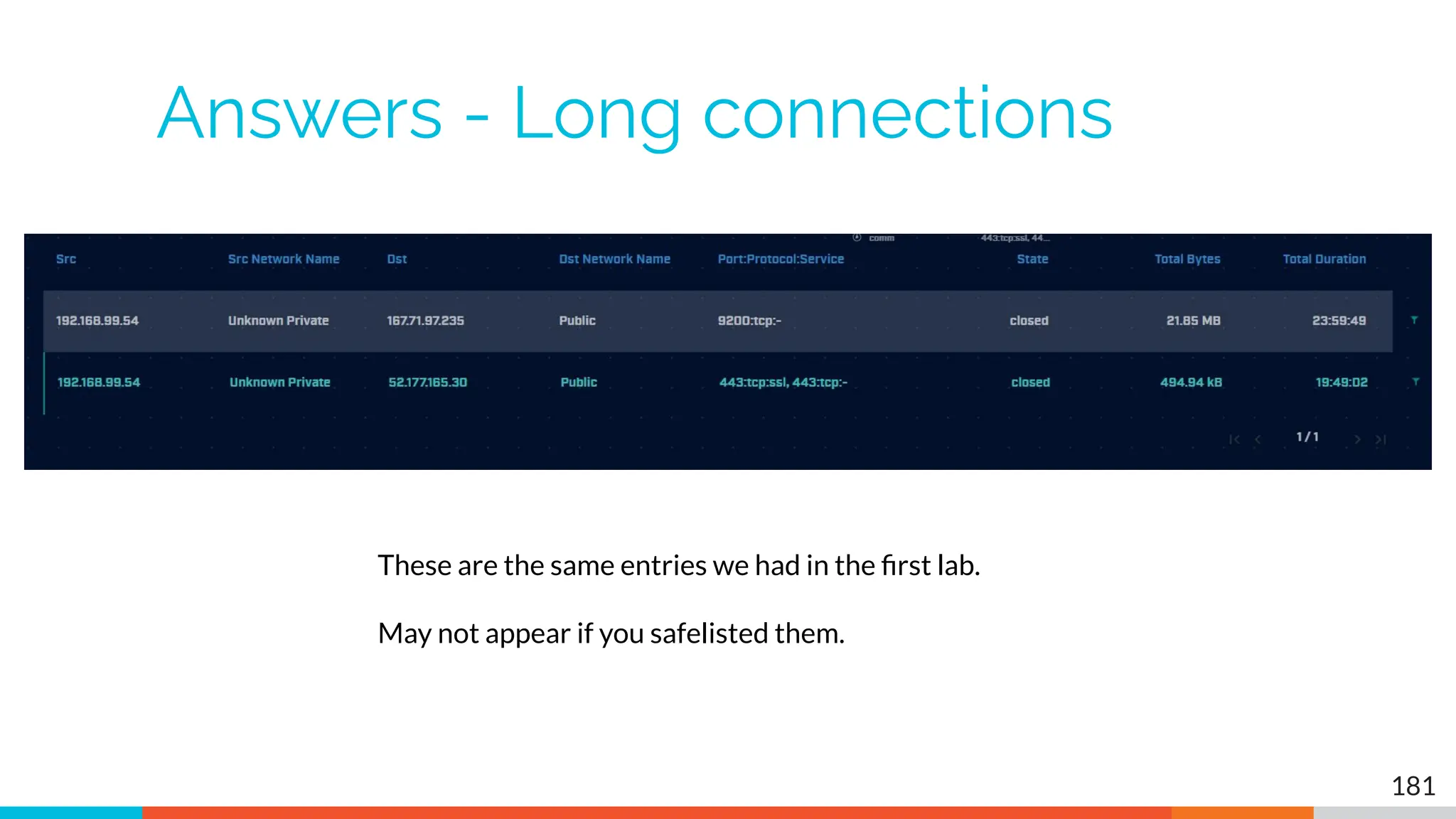
The document outlines the training and technical requirements for Level 1 network threat hunter training, includes troubleshooting techniques for VMware and VirtualBox environments, and provides resources for accessing class virtual machines. It also highlights upcoming events, classes, and goals for the course, including hands-on labs for investigating endpoints and threat hunting processes. Additionally, it discusses common issues encountered during virtual machine operation and the importance of identifying connection persistency in threat detection.