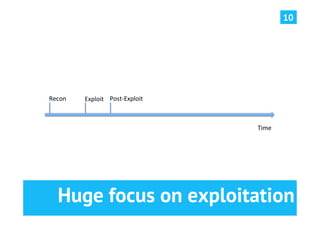
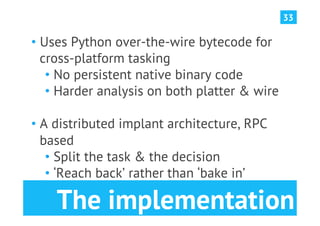
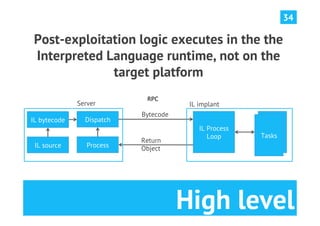
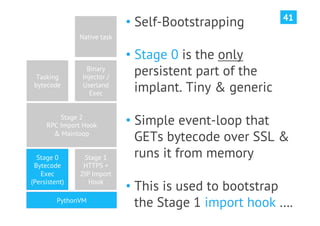
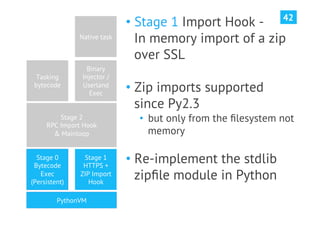
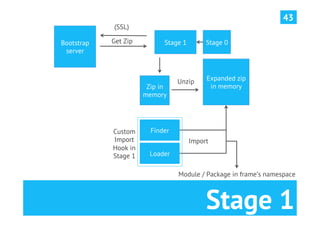
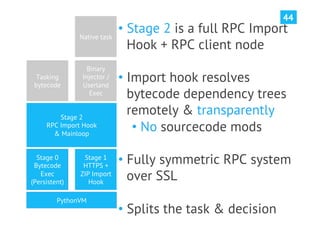
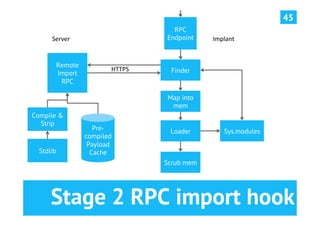
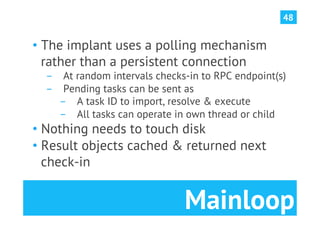
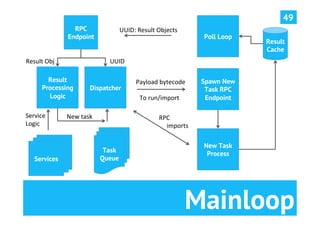
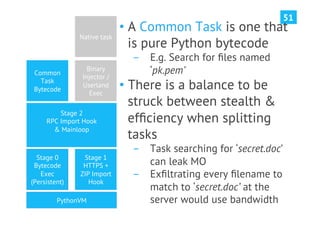
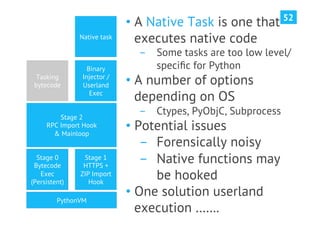
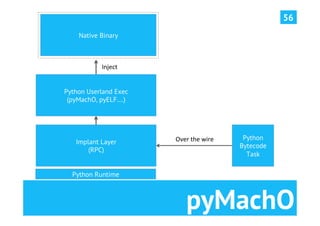
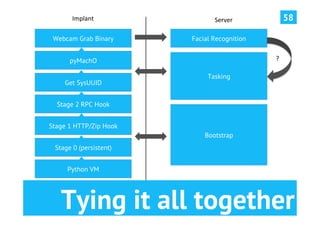
The document discusses advanced post-exploitation strategies for managing long-term, complex attack engagements, emphasizing the need for more effective tooling and methodologies. It introduces a distributed implant architecture using Python to separate actions from motivations, enhance stealth, and facilitate scalability. Key takeaways include the inadequacies of current post-exploitation frameworks and the importance of innovation in penetration testing and attack strategies.