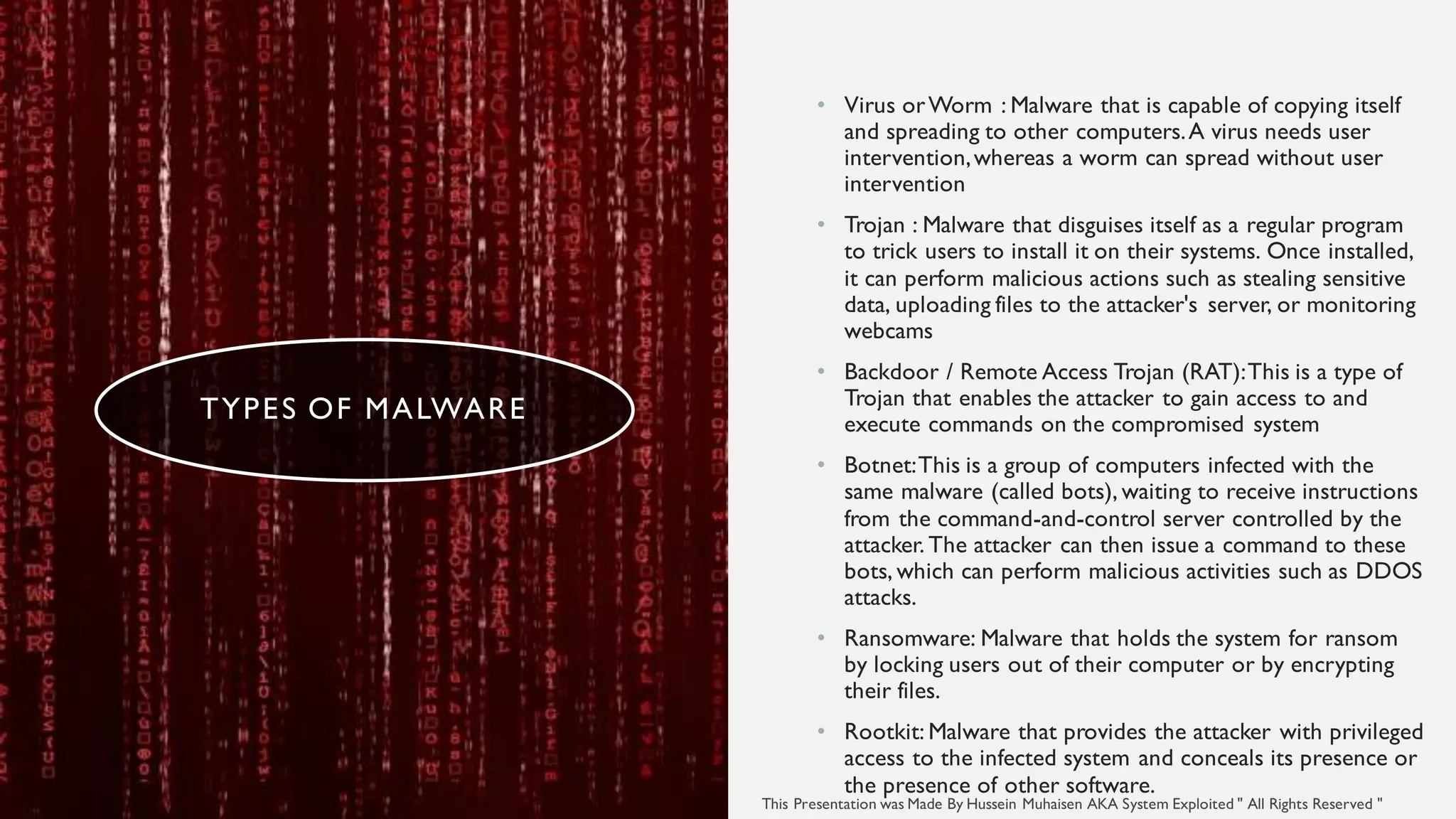
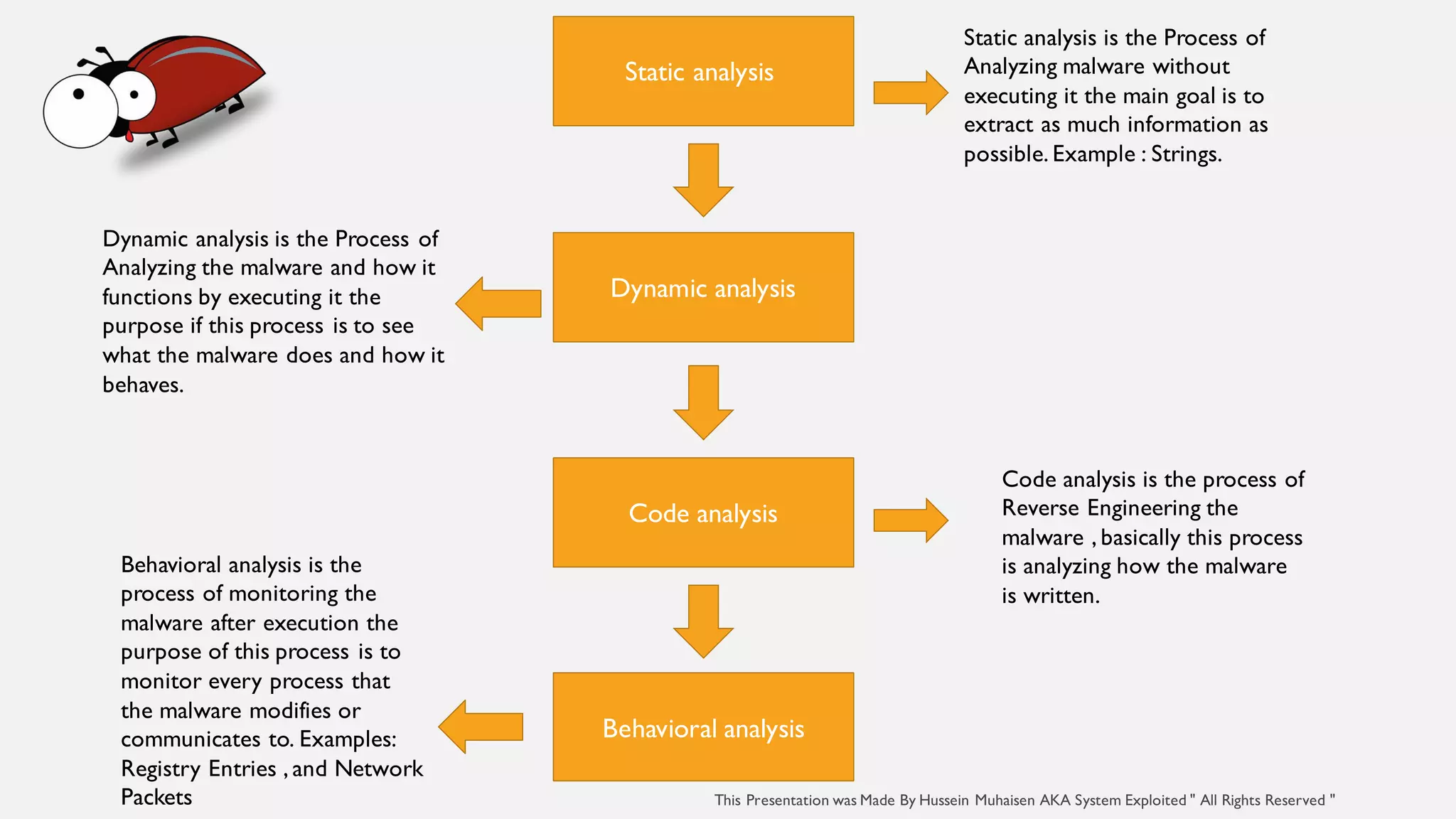
The document provides an overview of malware, defining it as malicious software used by attackers to compromise systems, with examples including viruses, trojans, ransomware, and botnets. It outlines the importance of malware analysis, which involves examining malware through different techniques like static, dynamic, code, and behavioral analysis to understand its functionality and mitigate future attacks. The document also suggests next steps for effective malware analysis, including setting up isolated environments and learning about operating systems and programming.