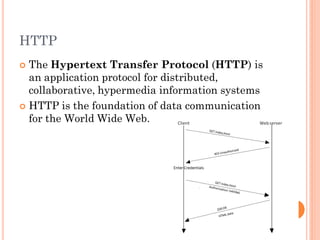
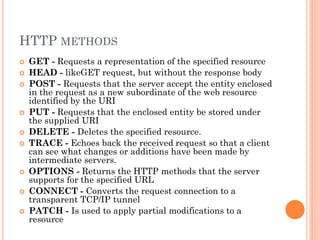
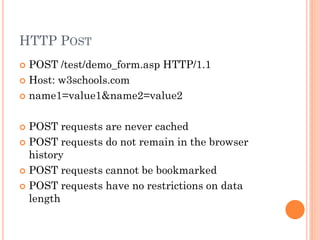
The document discusses HTTP and security topics related to web applications. It provides an overview of HTTP basics including methods like GET and POST. It then covers security threats like cross-site scripting (XSS), SQL injection, sensitive data exposure, and cross-site request forgery (CSRF). The document recommends approaches to protect against these threats, such as input filtering, prepared statements, encryption, using tokens, and more. It also discusses how these security concepts apply to PHP and WordPress applications.





![PHP METHODS FOR POST AND GET
GET - $_GET variable
POST - $_POST variable
$_REQUEST for both + $_COOKIE
if (isset($_GET['user']) && isset($_GET['gen']))
{
$user = $_GET['user'];
$gen = $_GET['gen'];
echo 'User: '. $user. ' - gender: '. $gen;
}
](https://image.slidesharecdn.com/httpandsecurity-131121032627-phpapp02/85/Http-and-security-9-320.jpg)


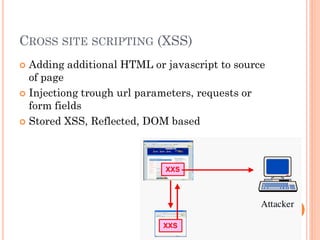
![XSS PROTECTION
Stripping tags
Transform characters like <,>,/,’,” etc to html
entities
Php functions:
string strip_tags ( string $str [, string
$allowable_tags ] )
string htmlentities ( string $string)
string htmlspecialchars( string $string)](https://image.slidesharecdn.com/httpandsecurity-131121032627-phpapp02/85/Http-and-security-13-320.jpg)

![SQL INJECTION PROTECTION
Filter user input
Way 1:
$stmt = $dbConnection->prepare('SELECT * FROM employees WHERE
name = ?');
$stmt->bind_param('s', $name);
$stmt->execute();
$result = $stmt->get_result();
while ($row = $result->fetch_assoc())
{ // do something with $row }
Way2:
$unsafe_variable = $_POST["user-input"] ;
$safe_variable = mysql_real_escape_string($unsafe_variable);
mysql_query("INSERT INTO table (column) VALUES ('" .
$safe_variable . "')");
](https://image.slidesharecdn.com/httpandsecurity-131121032627-phpapp02/85/Http-and-security-16-320.jpg)





