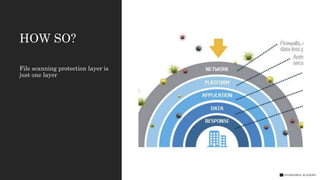
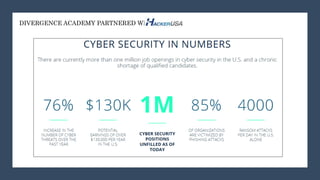
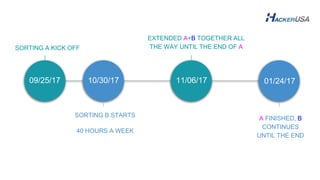
The document discusses the role of machine learning in enhancing cybersecurity, emphasizing its ability to improve data security through proactive defense measures against malware while highlighting limitations such as false positives and detection rates. It identifies that machine learning cannot serve as a standalone protection layer but can augment existing security measures. Additionally, it emphasizes the importance of integrating multiple layers of protection to tackle sophisticated threats like advanced persistent threats and various types of cyberattacks.