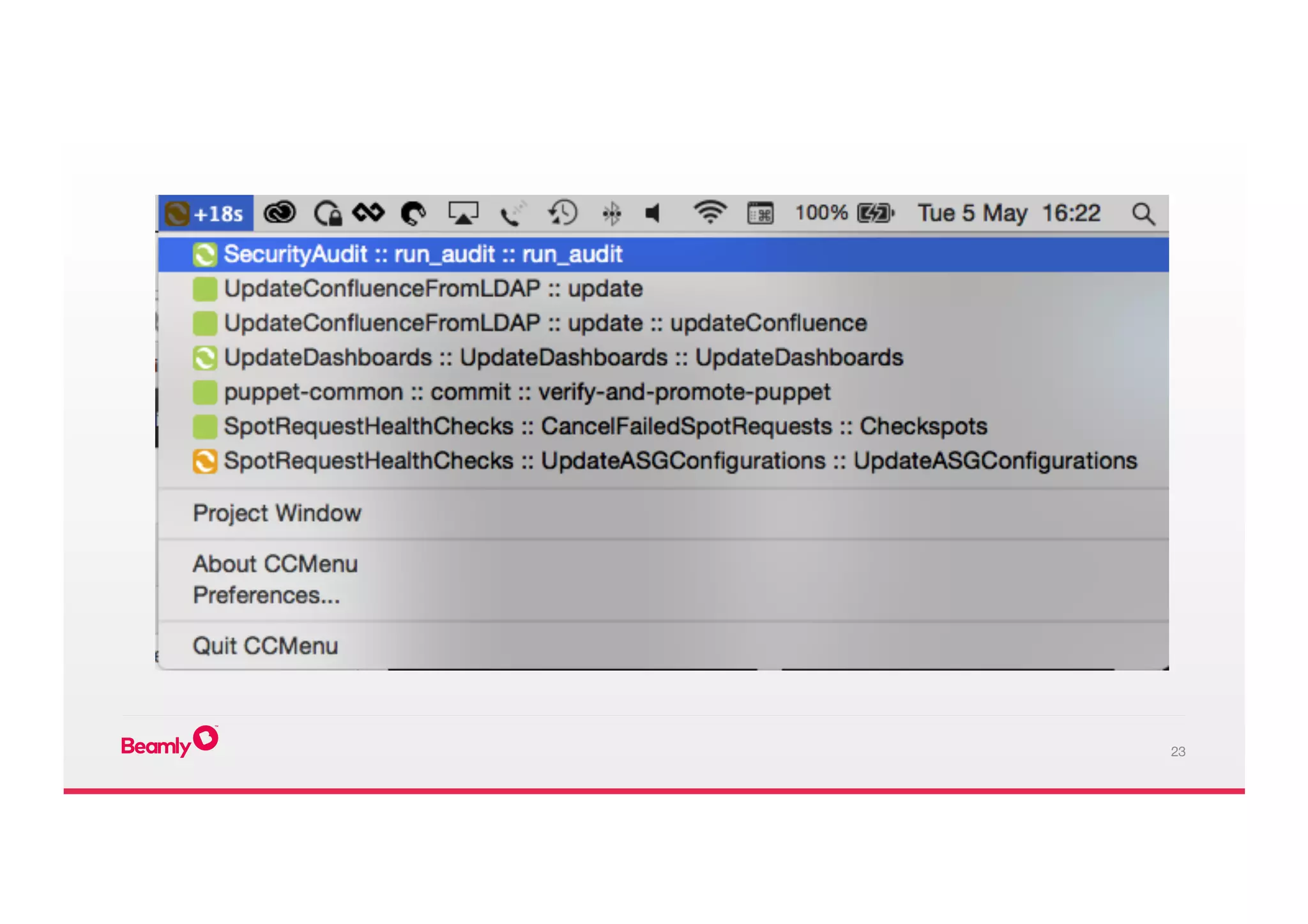
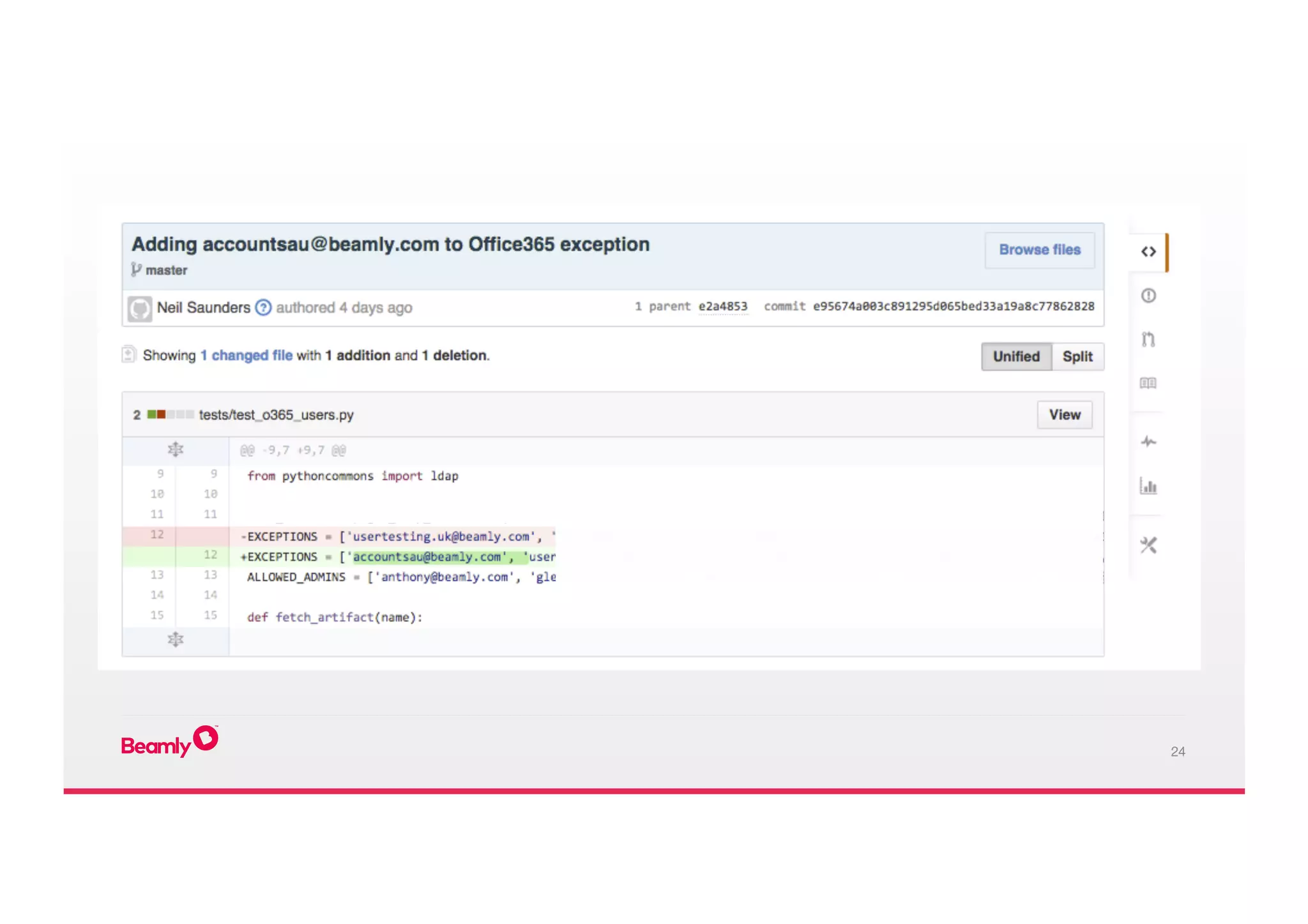
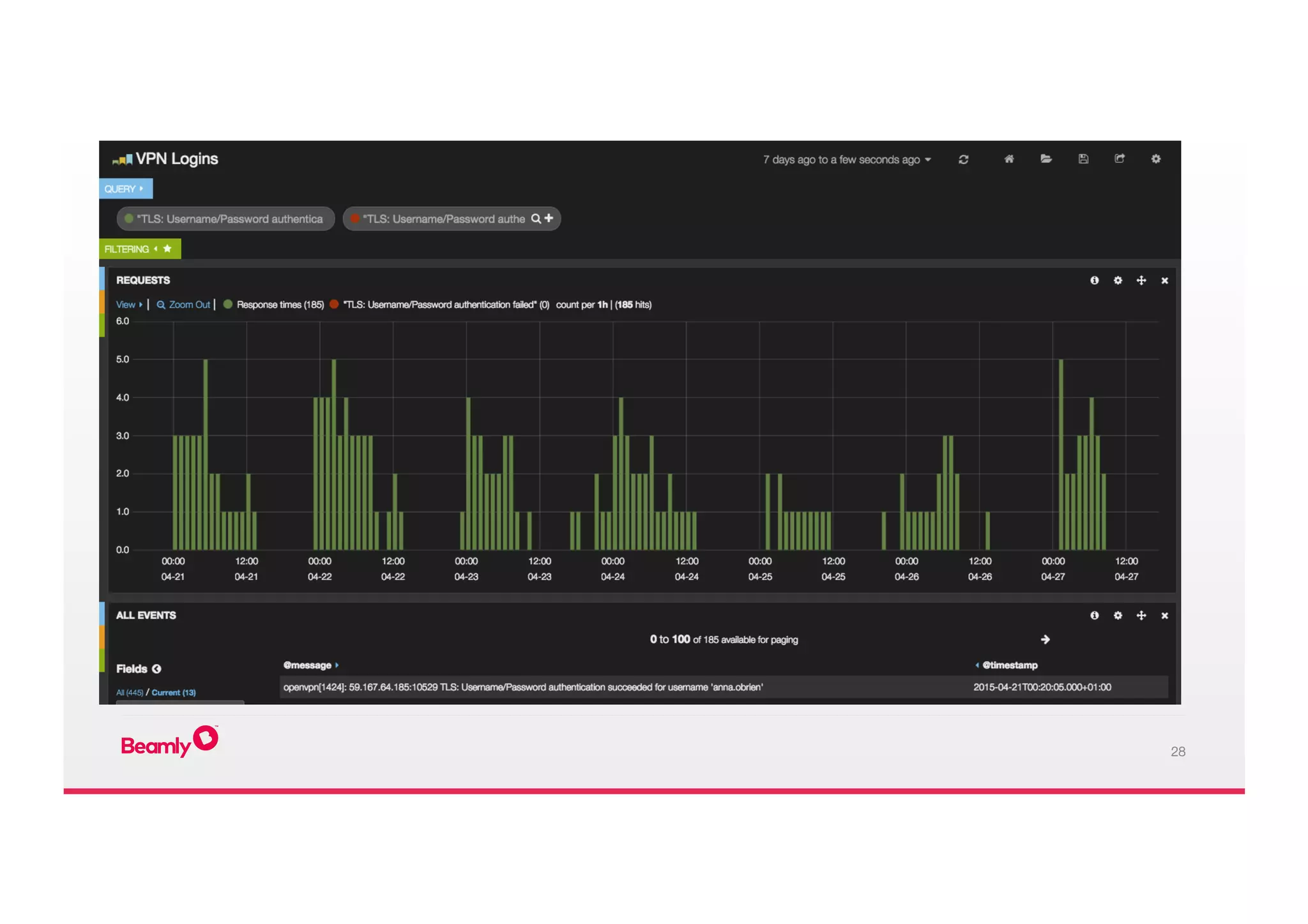
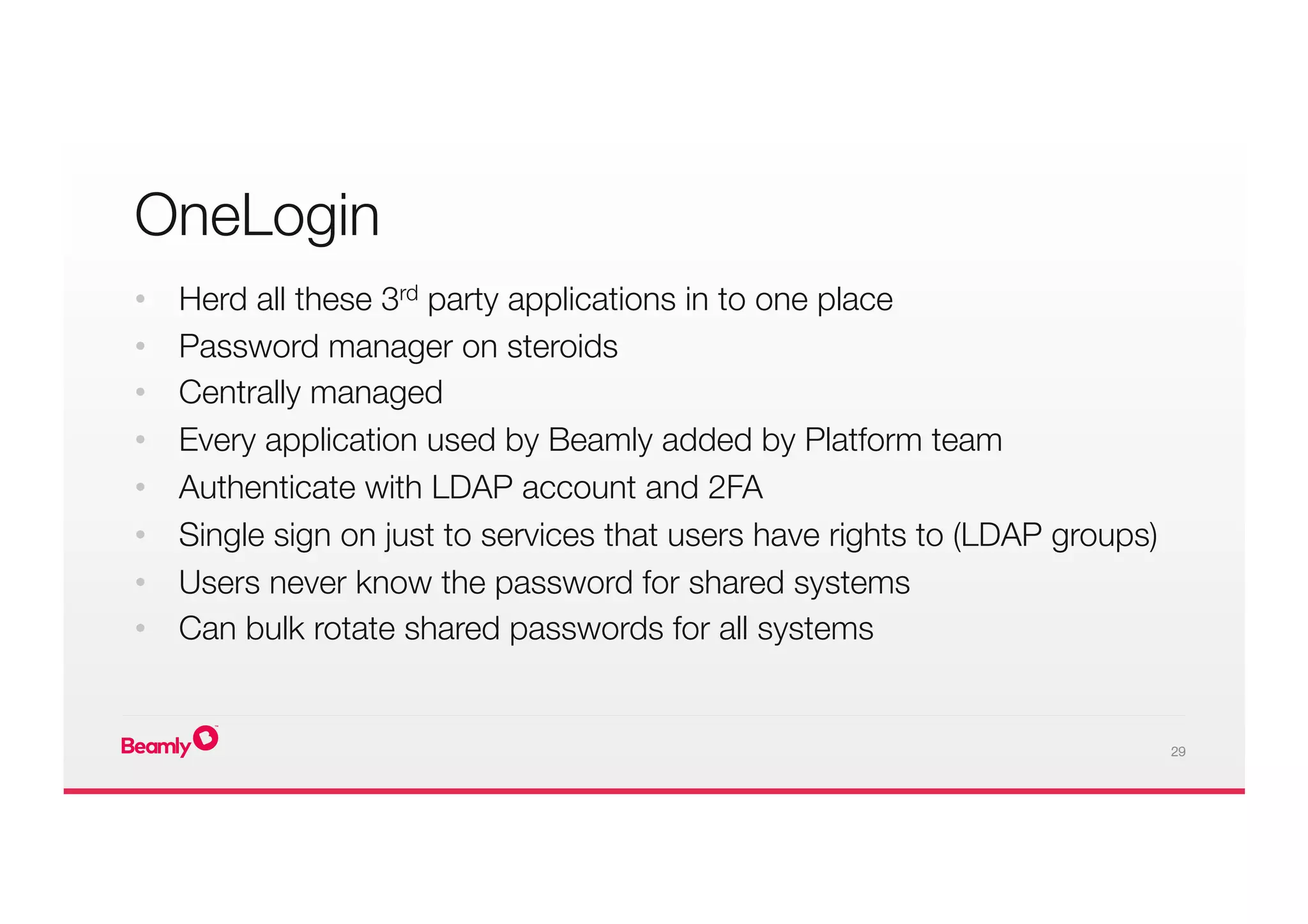
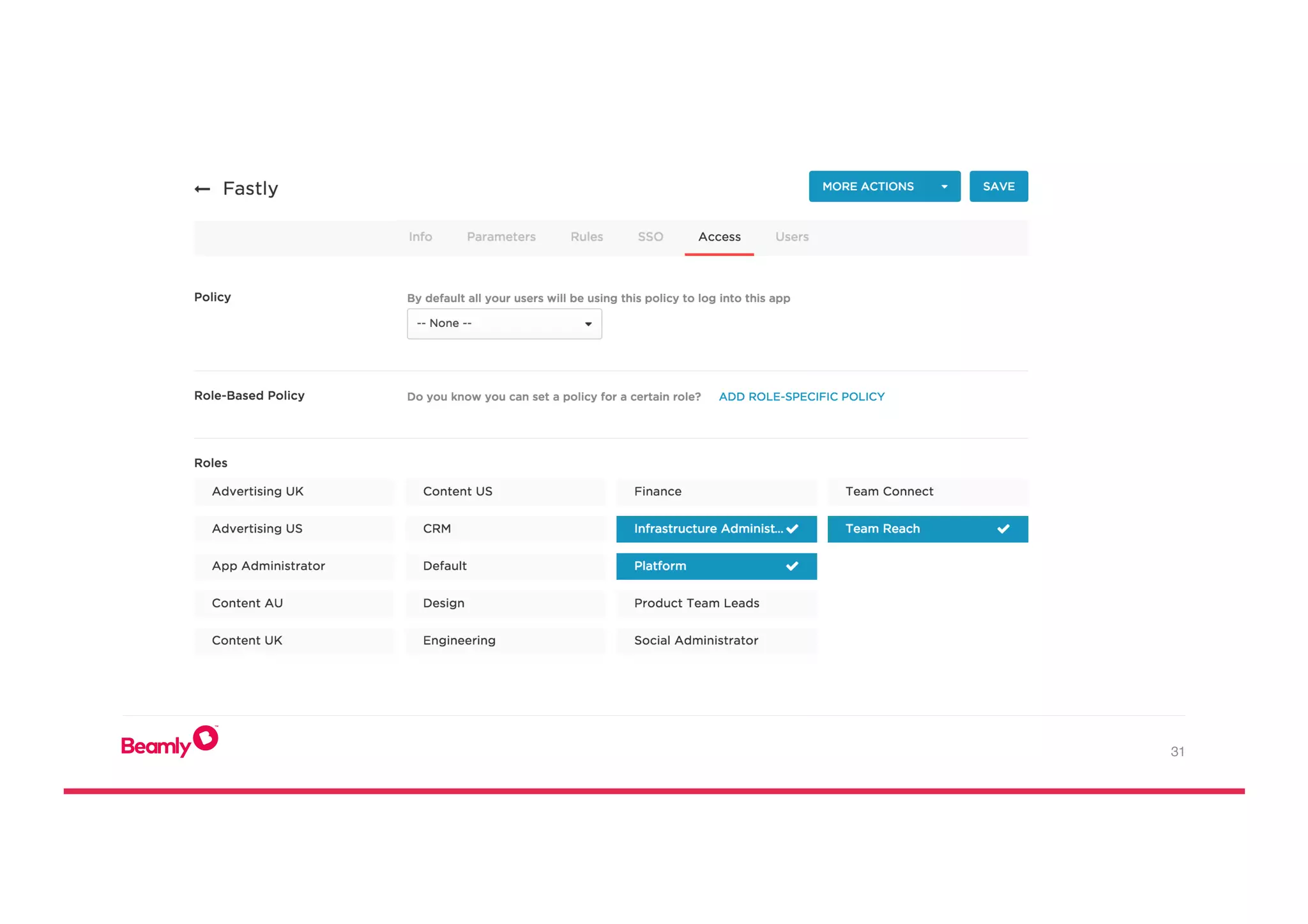
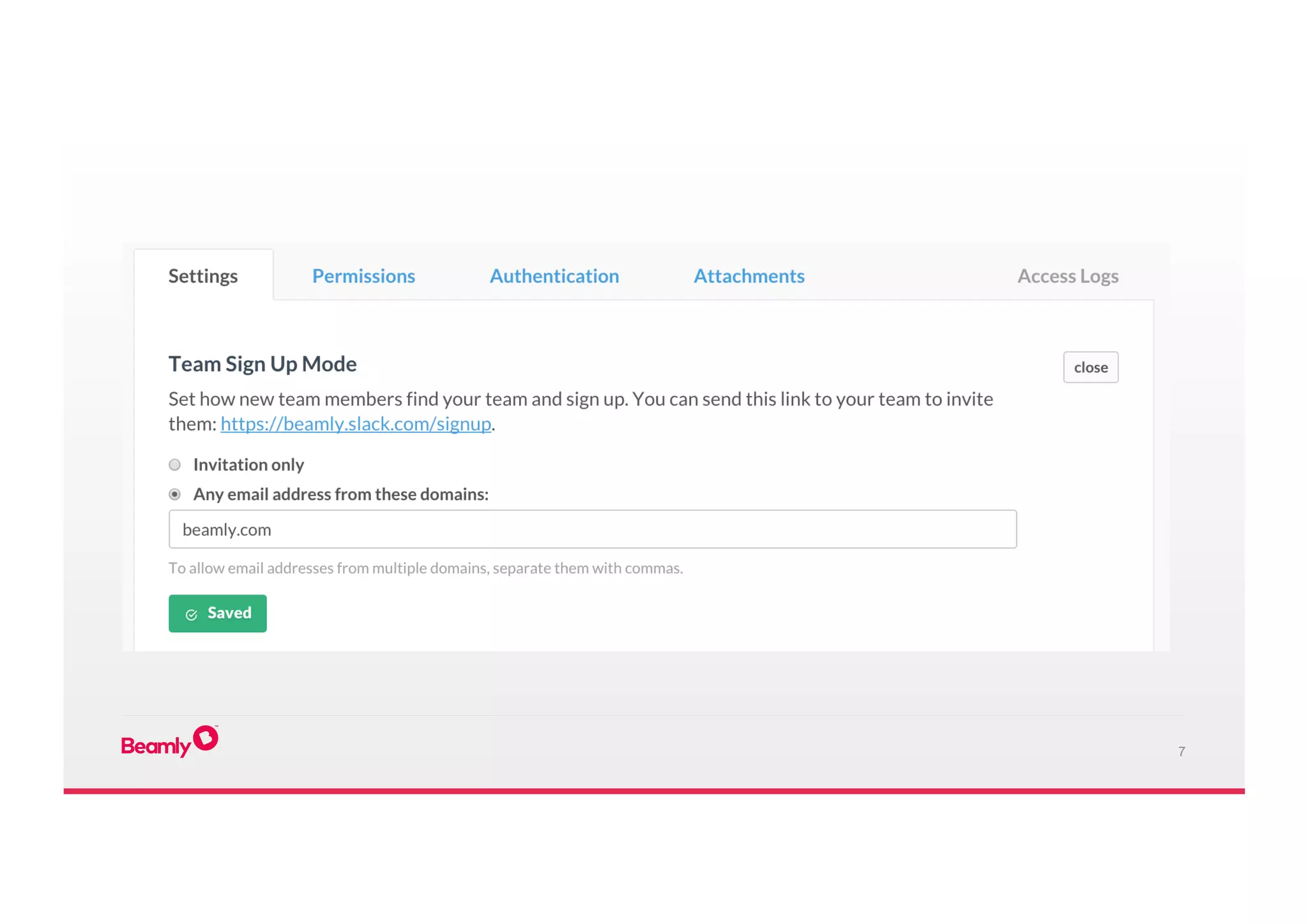
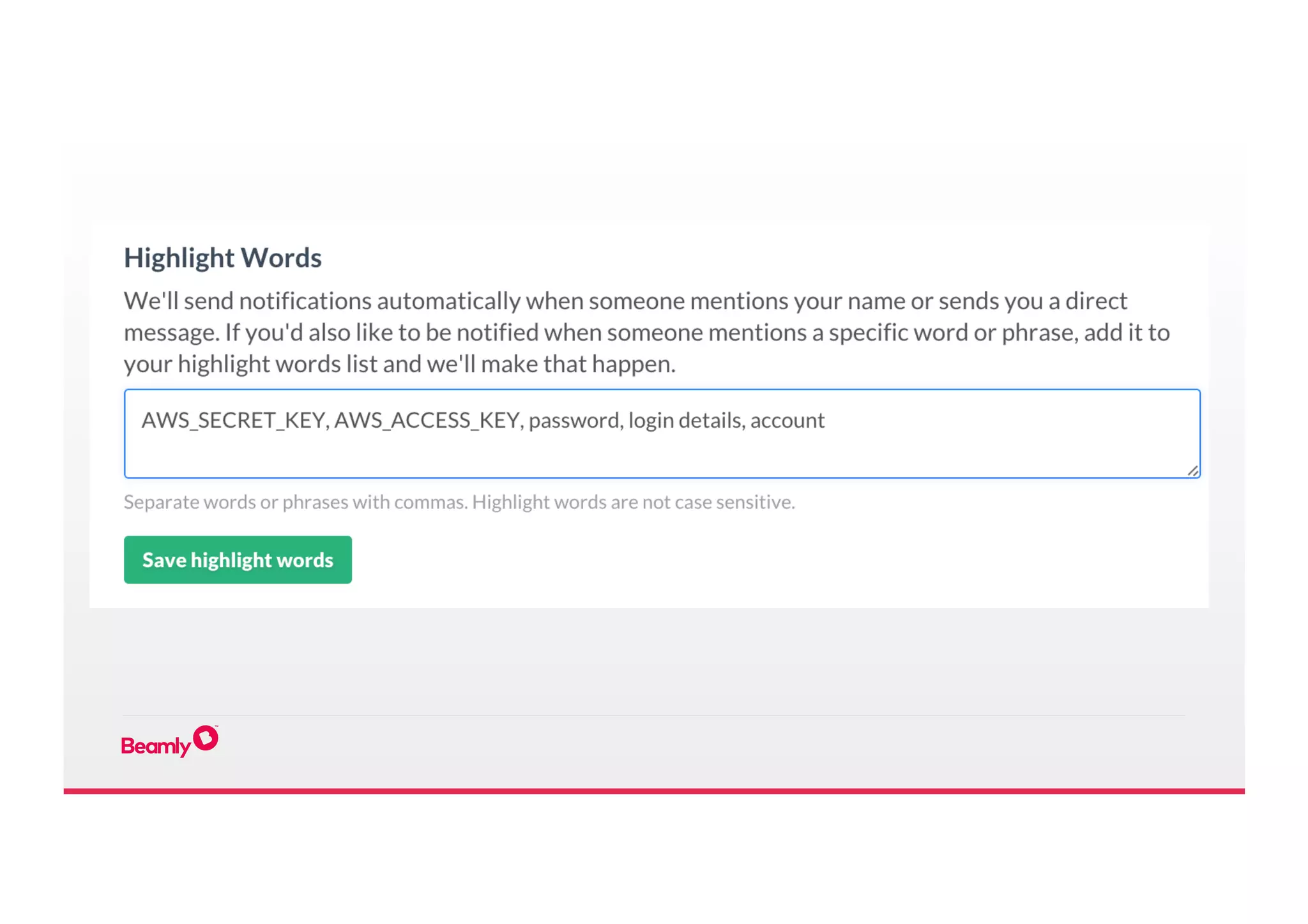
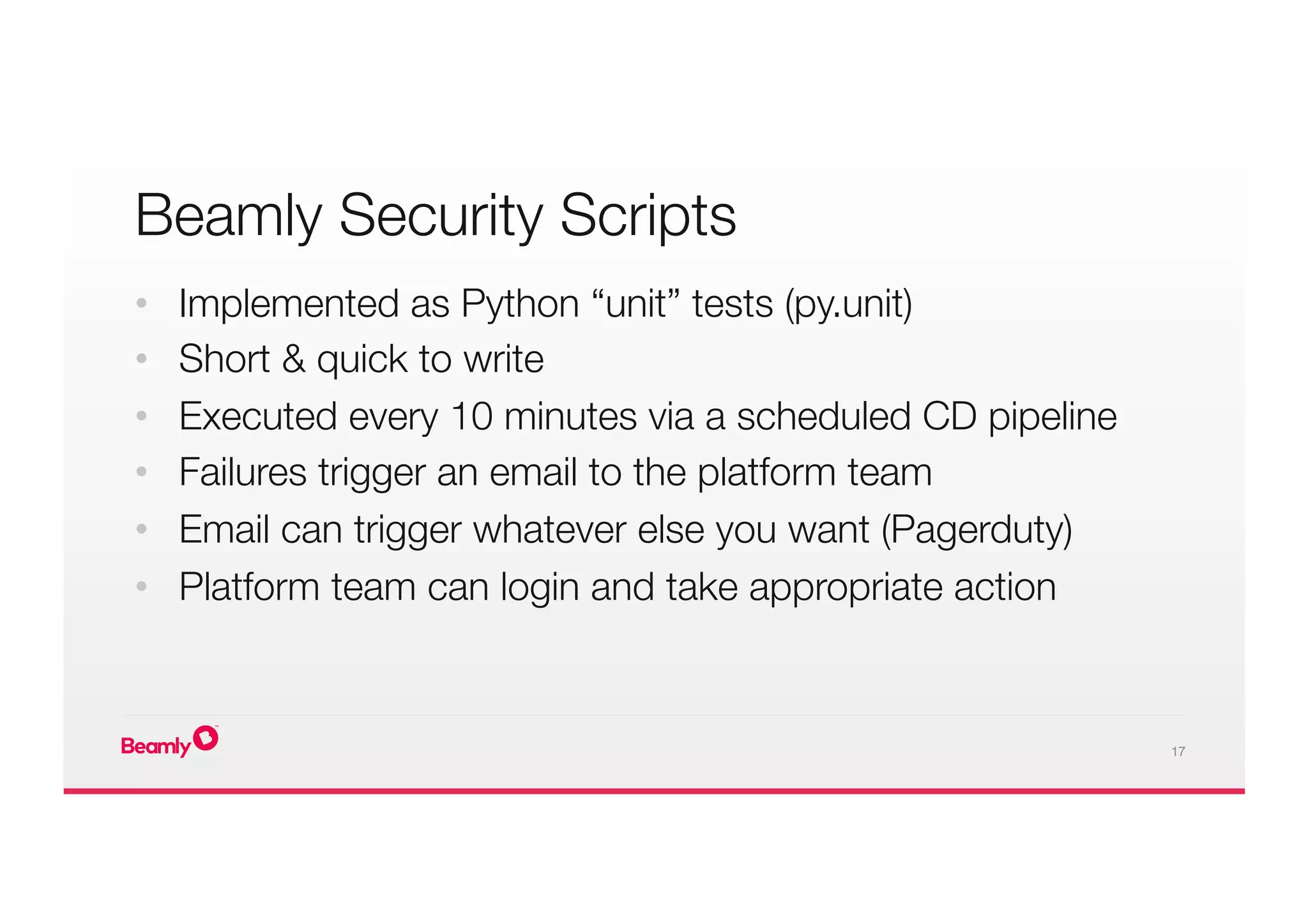
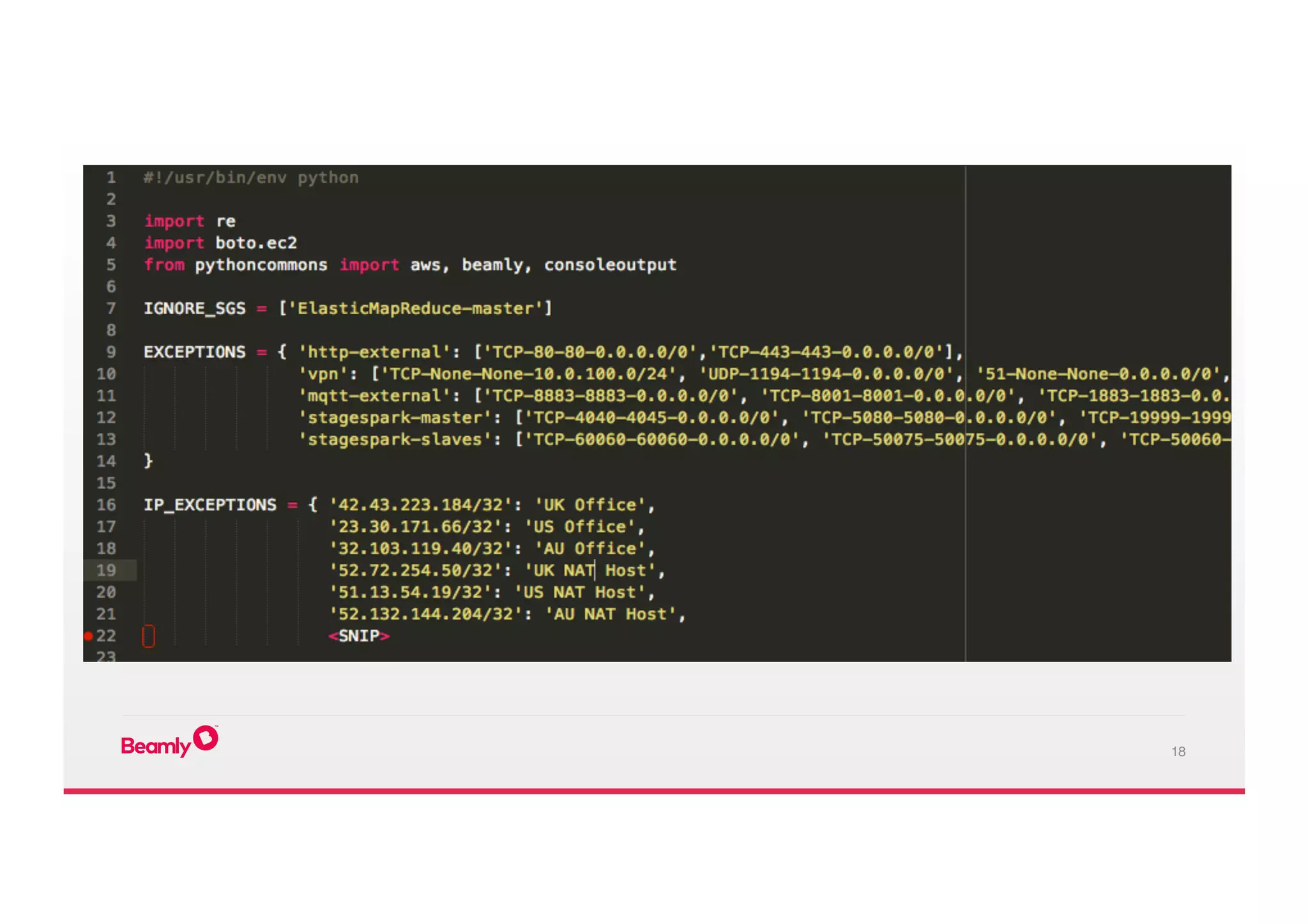
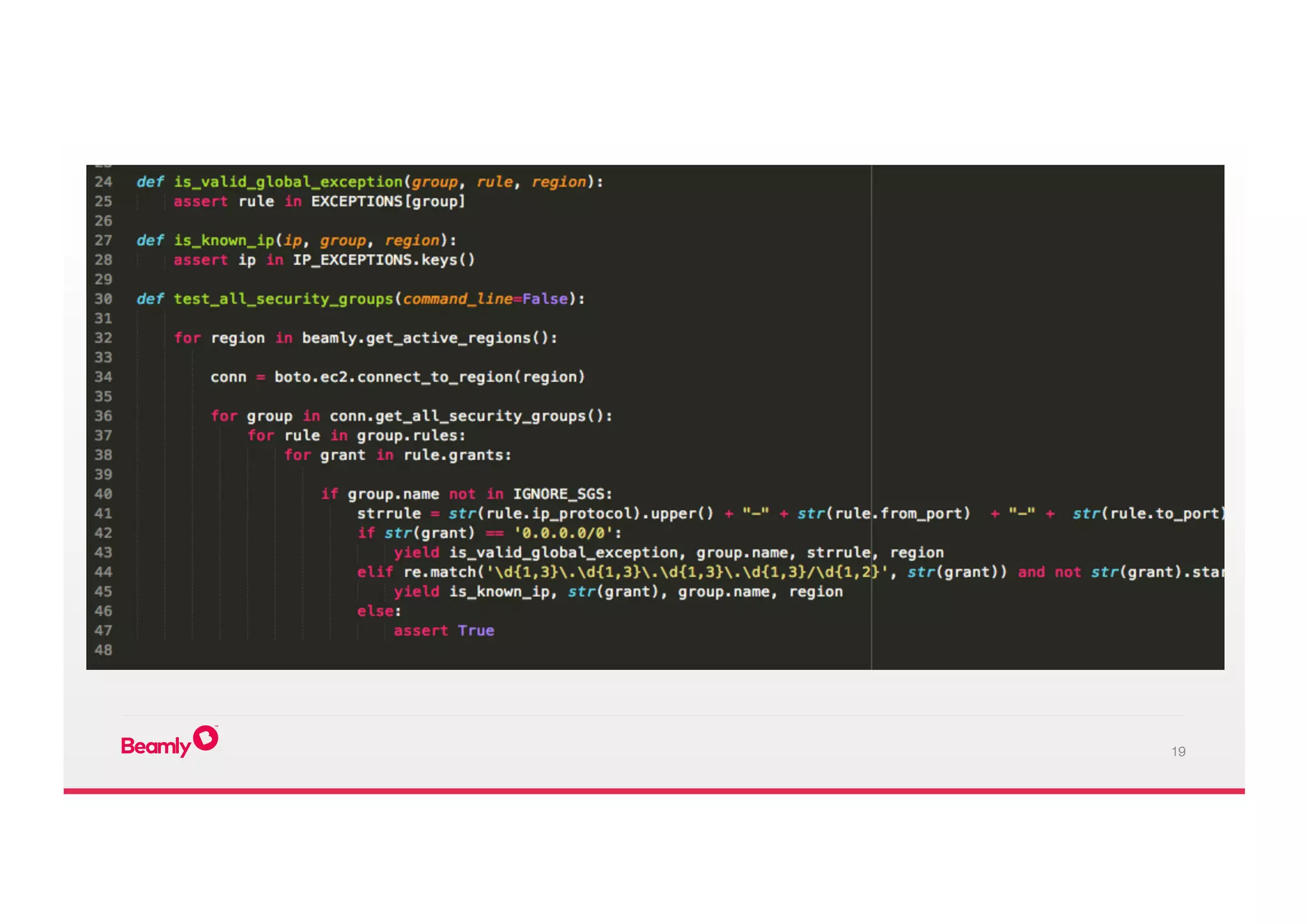
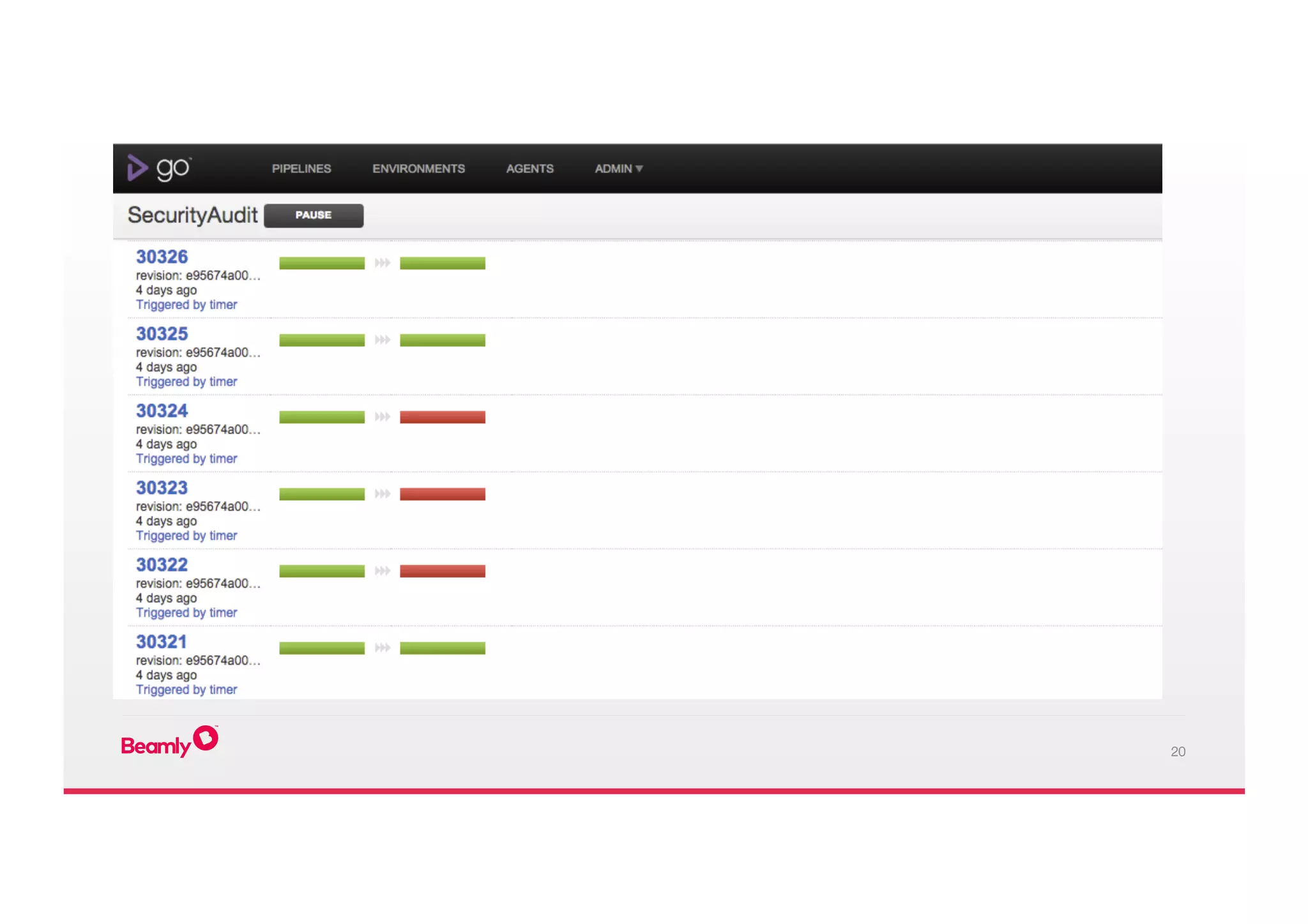
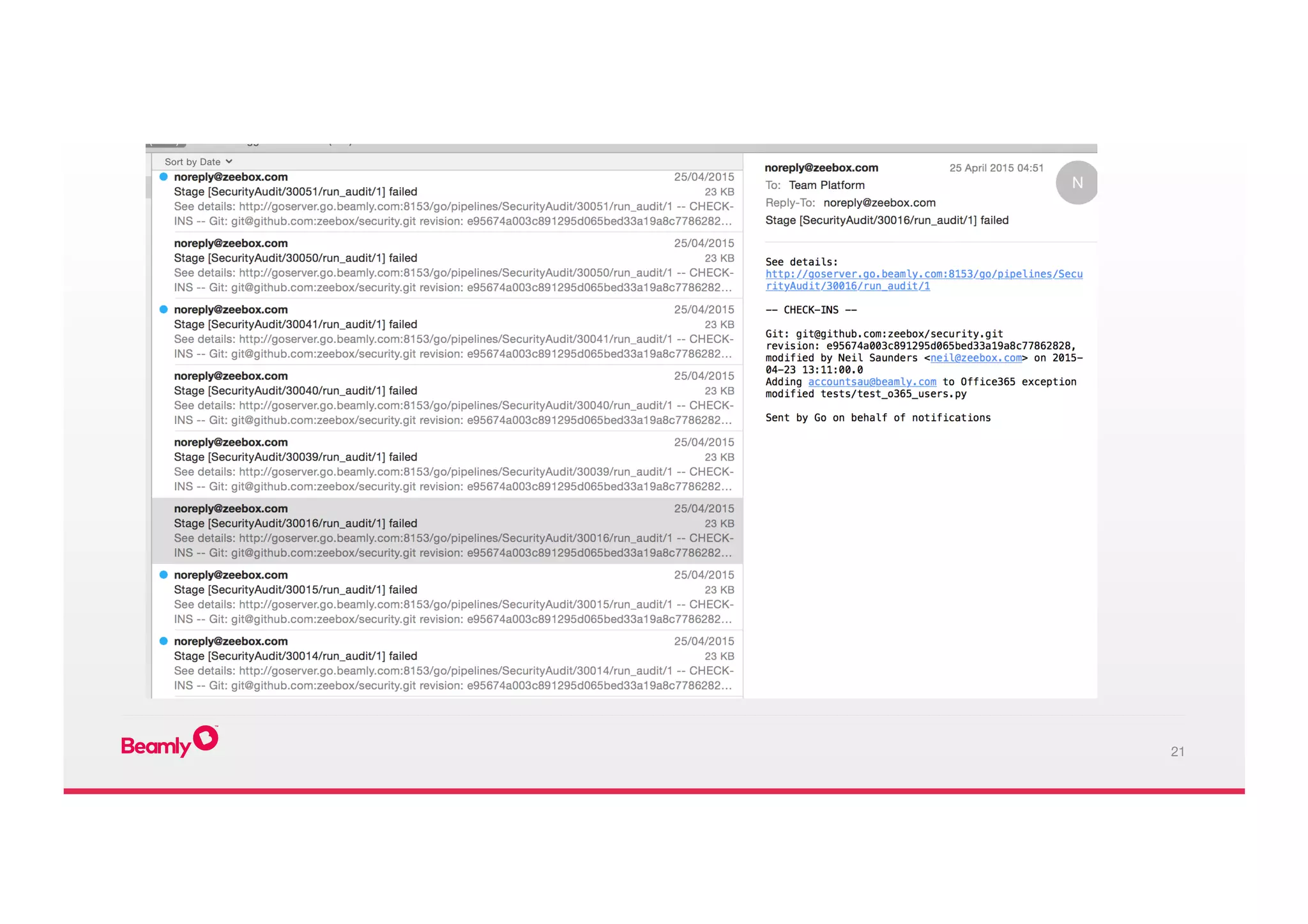
This document outlines an approach to security at a startup taken by Beamly. It involves outsourcing commodity services like hosting and monitoring to providers like AWS and Dataloop.io. It advocates setting up a single secure point of truth using LDAP to manage all user accounts and integrate with services. Beamly implemented security "unit" tests as Python scripts to regularly audit third party services and alert the team of any issues. The approach emphasizes enabling two-factor authentication wherever possible and regularly backing up data and configurations.









![22
collected
1280
items
test_all_github_hooks_are_known.py
......................................................................................................
.........................................................................................................................................
..................................................................................................................................
test_aws_iam_users_with_passwords_have_2fa.py
.....................................................................................
test_aws_security_groups.py
.............................................................................................................
.................................................................................
test_github_users_and_in_ldap_and_2fa.py
.............................................................
test_jira_users_not_in_ldap.py
..........................................................................................................
........................................................................
test_o365_users.py
...........................................................................................................
test_onelogin_users_are_in_ldap.py
...........................................................................................
test_pagerduty_users_not_in_ldap.py
........................
test_slack_users_not_in_ldap_and_2fa.py
............................................................F....................................
.....................................................
===================================
FAILURES
===================================
_________________________
test_unknown_slack_users[60]
_________________________
realname
=
’New
Joiner',
two_factor_enabled
=
False
def
two_factor_enabled(realname,
two_factor_enabled):
>
assert
two_factor_enabled
E
assert
False
test_slack_users_not_in_ldap_and_2fa.py:42:
AssertionError
===================
1
failed,
1279
passed
in
145.26
seconds
====================](https://image.slidesharecdn.com/londondevops-securityatastartup-150513141632-lva1-app6891/75/London-Devops-9-Security-at-a-startup-23-2048.jpg)