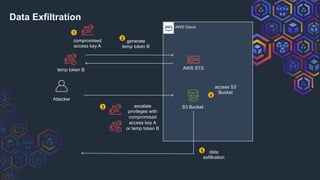
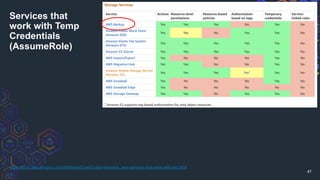
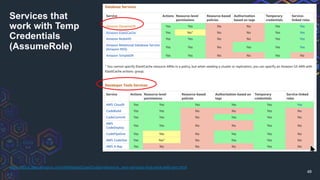
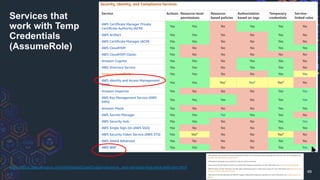
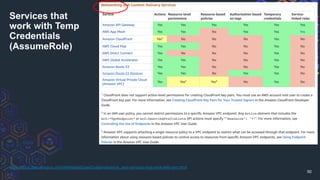
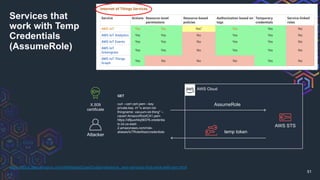
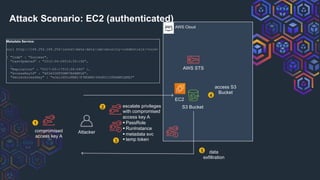
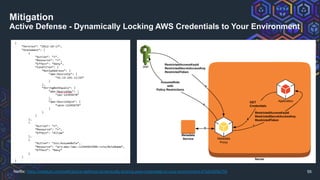
The document discusses challenges related to AWS temporary credentials, focusing on attack scenarios such as privilege escalation and data exfiltration following a compromised access key. It outlines the defender's perspective on detection, investigation, and remediation strategies, highlighting difficulties in managing and mitigating attacks using temporary tokens. The document emphasizes the need for improved monitoring, proactive measures, and updated incident response protocols for temporary credential management.


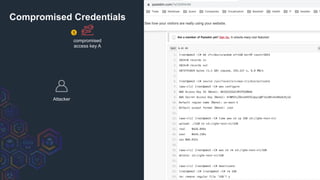
















![Defensive Viewpoint: Temp Tokens
33
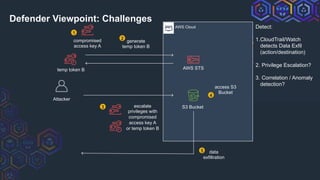
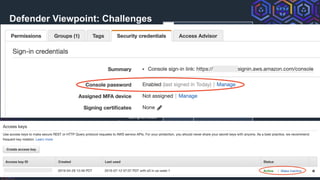
Detect
Update CloudWatch/SIEM
filters to detect
• Creation:
GetSessionToken
AssumeRole actions
• Usage: accessKeyId =~
ASIA*[1]
[1]https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html#Using_access-keys-audit](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-33-320.jpg)
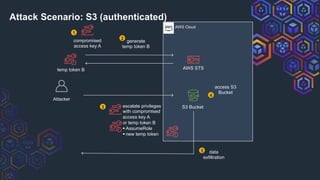
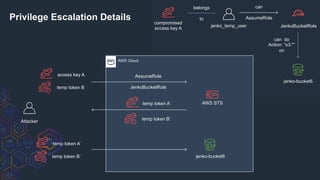
![AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
2
4
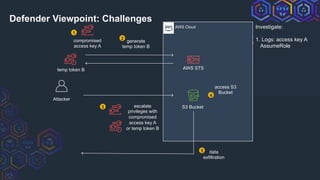
Defender Viewpoint: Temp Tokens
Mitigate/Remediate:
1. Can’t delete temp
token
2. a) Restrict Role[1]
b) Delete User[2]
3. Update Remediation
Playbook
4. Revoke Active Session
for Role[3]
AssumeRole
JenkoBucketRole
temp token B’
1
belongs
to
all keys/tokens jenko_temp_user
2
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html#Using_access-keys-audit
[2] https://aws.amazon.com/premiumsupport/knowledge-center/potential-account-compromise/
[3] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_revoke-sessions.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-34-320.jpg)
![[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html#Using_access-keys-audit
[2] https://aws.amazon.com/premiumsupport/knowledge-center/potential-account-compromise/
[3] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_revoke-sessions.html
AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
2
4
Defender Viewpoint: Temp Tokens
Mitigate/Remediate:
1. Can’t delete temp
token
2. a) Restrict Role
b) Delete User
3. Update Remediation
Playbook
4. Revoke Active Session
for Role
AssumeRole
JenkoBucketRole
temp token B’
1
belongs
to
all keys/tokens jenko_temp_user
2](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-35-320.jpg)
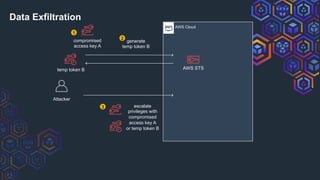
![AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
Defender Viewpoint: Temp Tokens
Prevention:
GetSessionToken
1. Can’t prevent[1]
AssumeRole
JenkoBucketRole
temp token B’
generated
from
all keys/tokens jenko_temp_user[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_control-access_enable-create.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-36-320.jpg)
![Prevention:
GetSessionToken
1. Can’t prevent[1]
AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
AssumeRole
JenkoBucketRole
temp token B’
generated
from
all keys/tokens jenko_temp_user
Defender Viewpoint: Temp Tokens
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_control-access_enable-create.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-37-320.jpg)
![AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
Prevention:
GetSessionToken
1. Can’t prevent[1]
2. Can’t MFA-protect
3. Can’t use IAM
permissions boundaries
AssumeRole
JenkoBucketRole
temp token B’
2
3
generated
from
all keys/tokens jenko_temp_user
max perms
Defender Viewpoint: Temp Tokens
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_control-access_enable-create.html
[2] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_revoke-sessions.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-38-320.jpg)
![AWS Cloud
Attacker
generate
temp token B
temp token B AWS STS
sessions
temp token B’ S3 Bucket
1
4
Prevention:
GetSessionToken
1. Can’t prevent[1]
2. Can’t MFA-protect
3. Can’t use IAM
permissions boundaries
AssumeRole
4. Can restrict
5. Can Revoke active
sessions for Role[2]
AssumeRole
JenkoBucketRole
temp token B’
2
5
3
generated
from
all keys/tokens jenko_temp_user
max perms
Defender Viewpoint: Temp Tokens
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_control-access_enable-create.html
[2] https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_revoke-sessions.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-39-320.jpg)
![BLUE
• Plan ASAP
• manage temp token usage especially remediation/recovery
• Prevention
• lockdown access keys (aws:sourceIp/aws:sourceVpc[1]/MFA)
• isolate temp token usage in separate accounts
• service-only IAMUsers in separate accounts
• minimal privileges for AssumeRole and PassRole
• Detection
• alert on GetSessionToken
• alert on temp tokens (ASIA*)
• harden CloudTrail/CloudWatch/SIEM
• AWS Config (IAM,Lambda)
41
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_condition-keys.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-41-320.jpg)
![BLUE
• Mitigation/Remediation
• review/revise remediation playbook
• do not use GetSessionToken, use AssumeRole
• maybe don’t use temp tokens at all…permanent access keys
• use revoke active sessions for role(aws:TokenIssueTime[1])
• create/test a recovery plan from compromised temp tokens
• AWS Config (IAM,Lambda)
• Provisioning/Inventory
• track temp tokens that are created in a datastore
• use wrapper code for custom apps that need temp tokens
• for AWS-generated tokens (IoT, AssumeRole) have to parse logs
42
[1] https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_condition-keys.html](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-42-320.jpg)







![Generalized Approach
57
ATTACKER
Tactics
[1]
Initial
Access
Execution Persistence Privilege
Escalation
Defense
Evasion
Credential
Access
Discovery Lateral
Movement
Collection C2 Exfiltration Impact
Techniques Stolen
Credentials in
Cloud (e.g.
github,
Pastebin)
GetSession
Token
AssumeRole
<elevated
role>
Use Temp
Tokens
Copy
temporary
credentials
from Privilege
Escalation
<many> AssumeRole
<any role>
Bucket
Object Copy
/ Replication
Destroy
Buckets
or Objects
DEFENDER
Prevent • IP/VPC
whitelist
• MFA
n/a IP/VPC
whitelist role
policy
conditions
• IP/VPC
whitelist role
policy
conditions
• metadata
proxy with
secret
header
MFA MFA
Detect Filter on
failed auth
Filter on
GetSession
Token
Anomaly
Detection /
UBA?
Filter on
“ASIA*”
and
GetToken
• Filter on
API calls
• Correlate
• UBA
Anomaly
Detection /
UBA?
Anomaly
Detection /
UBA?
Mitigate /
Remediate
Delete and
recreate user
using CFT
Delete and
recreate
user using
CFT
Revoke Role
Sessions
Conditions
Revoke Role
Sessions
Conditions
[1] Mitre Att&ck: https://attack.mitre.org](https://image.slidesharecdn.com/awstemporarycredentials-challengesinpreventiondetectionmitigation-190919230937/85/AWS-temporary-credentials-challenges-in-prevention-detection-mitigation-57-320.jpg)