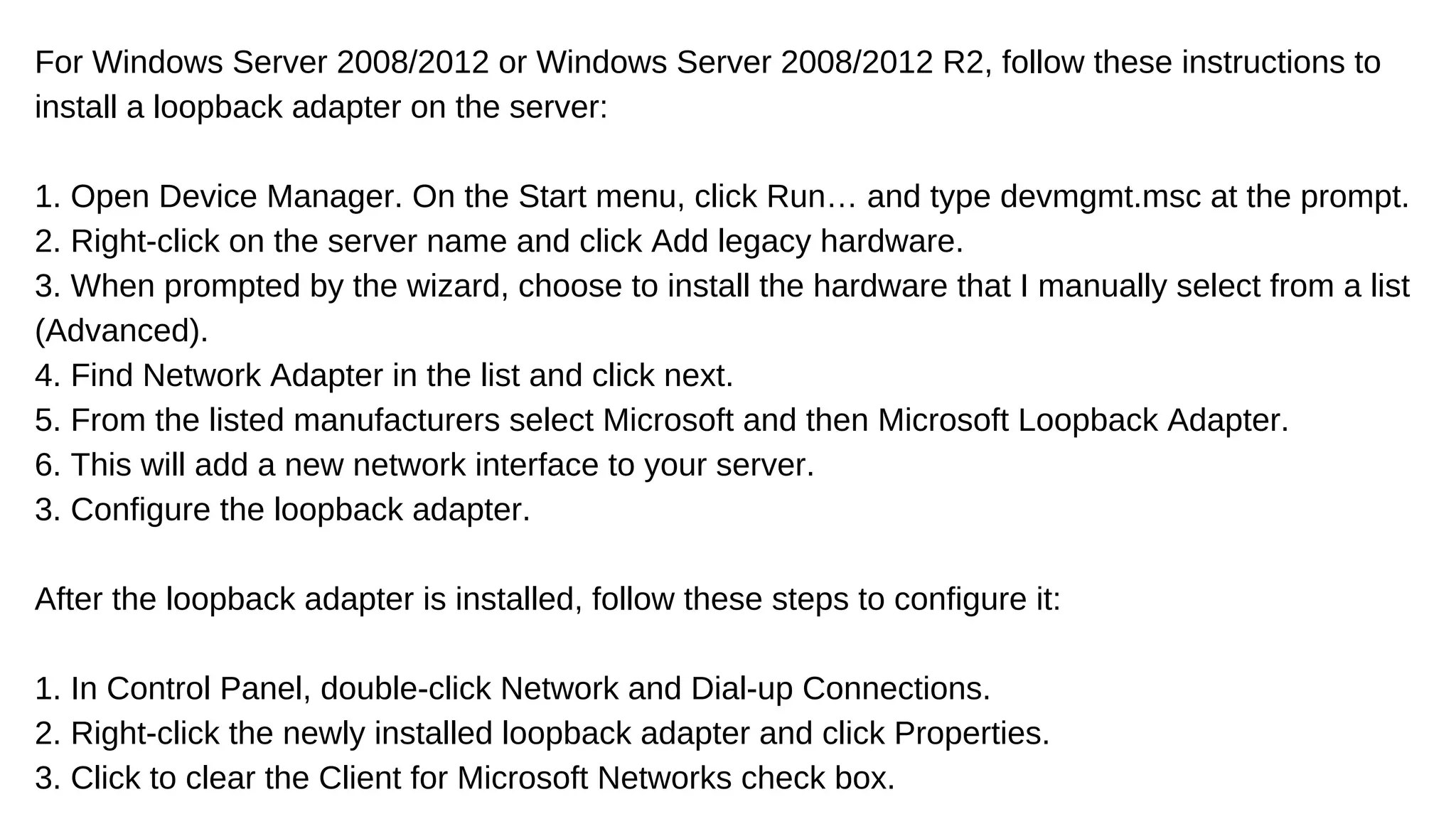
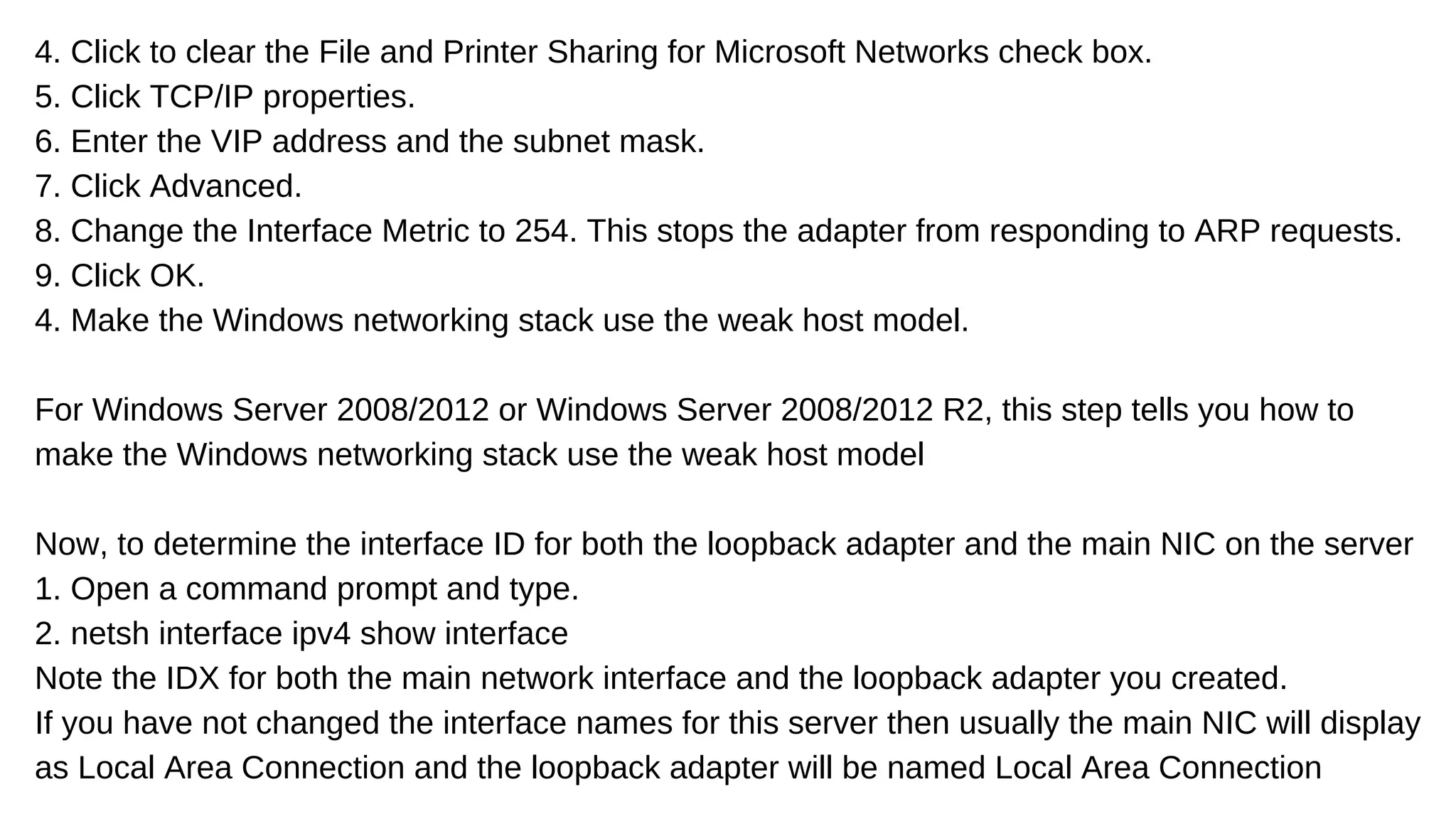
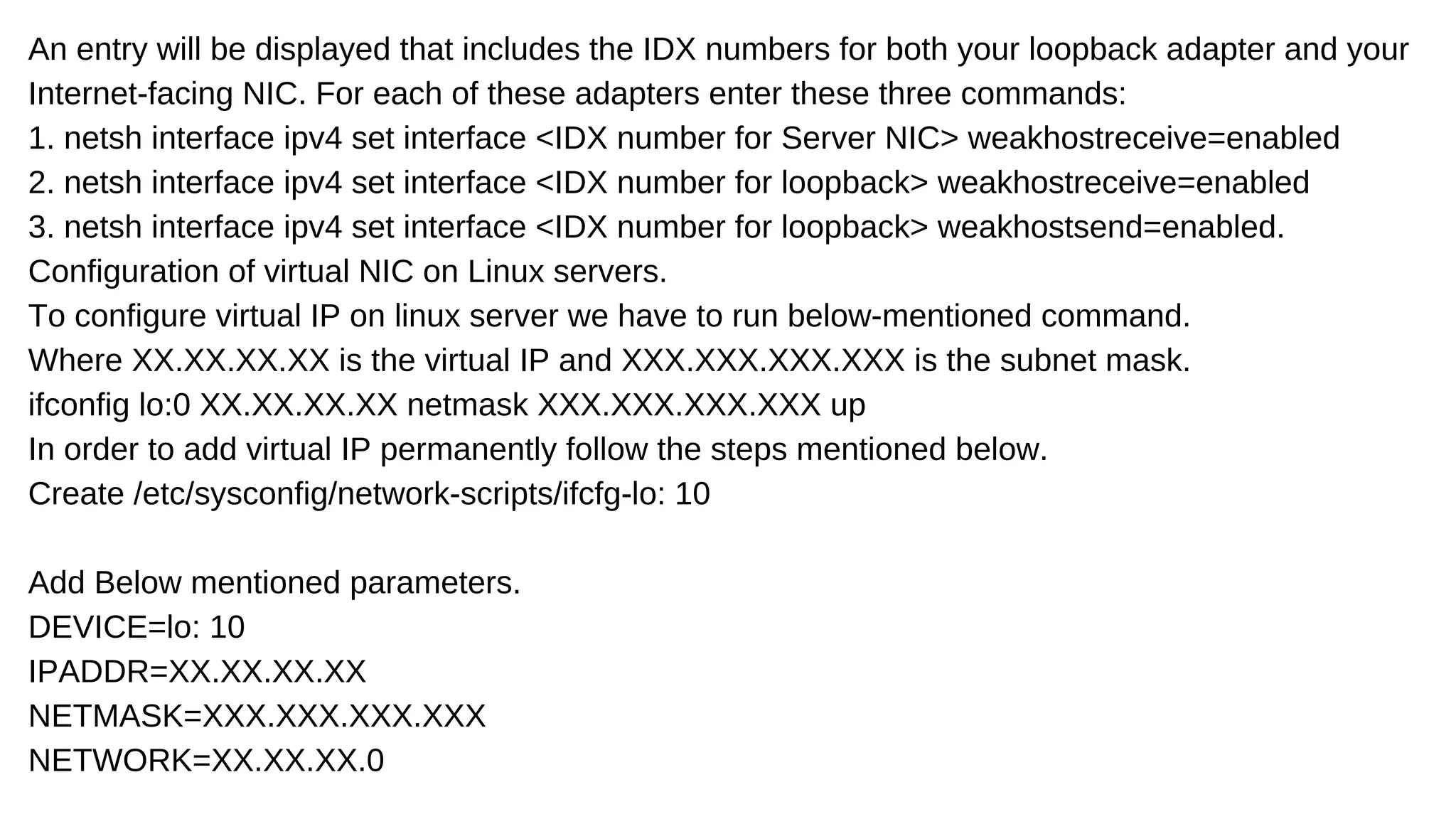
The document discusses the importance of load balancers in managing website traffic to prevent downtime and improve network performance by distributing workloads across multiple servers. It outlines various load balancing algorithms and their benefits, as well as detailed configuration steps for both Windows and Linux servers. Additionally, it compares hardware and software load balancers, highlighting the advantages of each and promoting Web Werks as a reliable service provider for high-traffic websites.