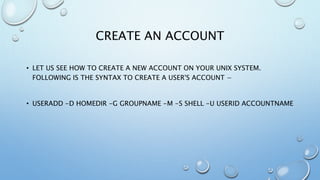
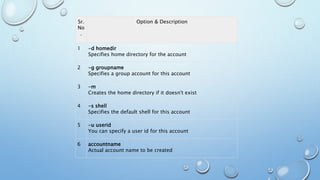
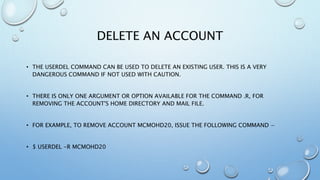
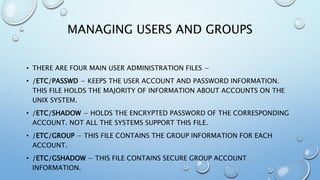
This document provides an overview of processes and process management in Linux. It discusses key topics such as:
- Processes are created through the fork system call, with the creating process becoming the parent and new process becoming the child.
- Processes can run in the foreground or background. The ps command is used to view running processes.
- The kill command terminates processes by sending a signal, with no arguments using the default SIGTERM signal.
- Parent processes use wait to suspend until child processes complete before continuing. Scheduling and priorities can be configured through nice, sleep, at, cron, and other commands.




















![CREATE A GROUP
• WE WILL NOW UNDERSTAND HOW TO CREATE A GROUP. FOR THIS, WE NEED TO
CREATE GROUPS BEFORE CREATING ANY ACCOUNT OTHERWISE, WE CAN MAKE USE
OF THE EXISTING GROUPS IN OUR SYSTEM. WE HAVE ALL THE GROUPS LISTED IN
/ETC/GROUPS FILE.
• ALL THE DEFAULT GROUPS ARE SYSTEM ACCOUNT SPECIFIC GROUPS AND IT IS NOT
RECOMMENDED TO USE THEM FOR ORDINARY ACCOUNTS. SO, FOLLOWING IS THE
SYNTAX TO CREATE A NEW GROUP ACCOUNT −
• GROUPADD [-G GID [-O]] [-R] [-F] GROUPNAME](https://image.slidesharecdn.com/linuxsystemadministration-201209055728/85/Linux-system-administration-23-320.jpg)