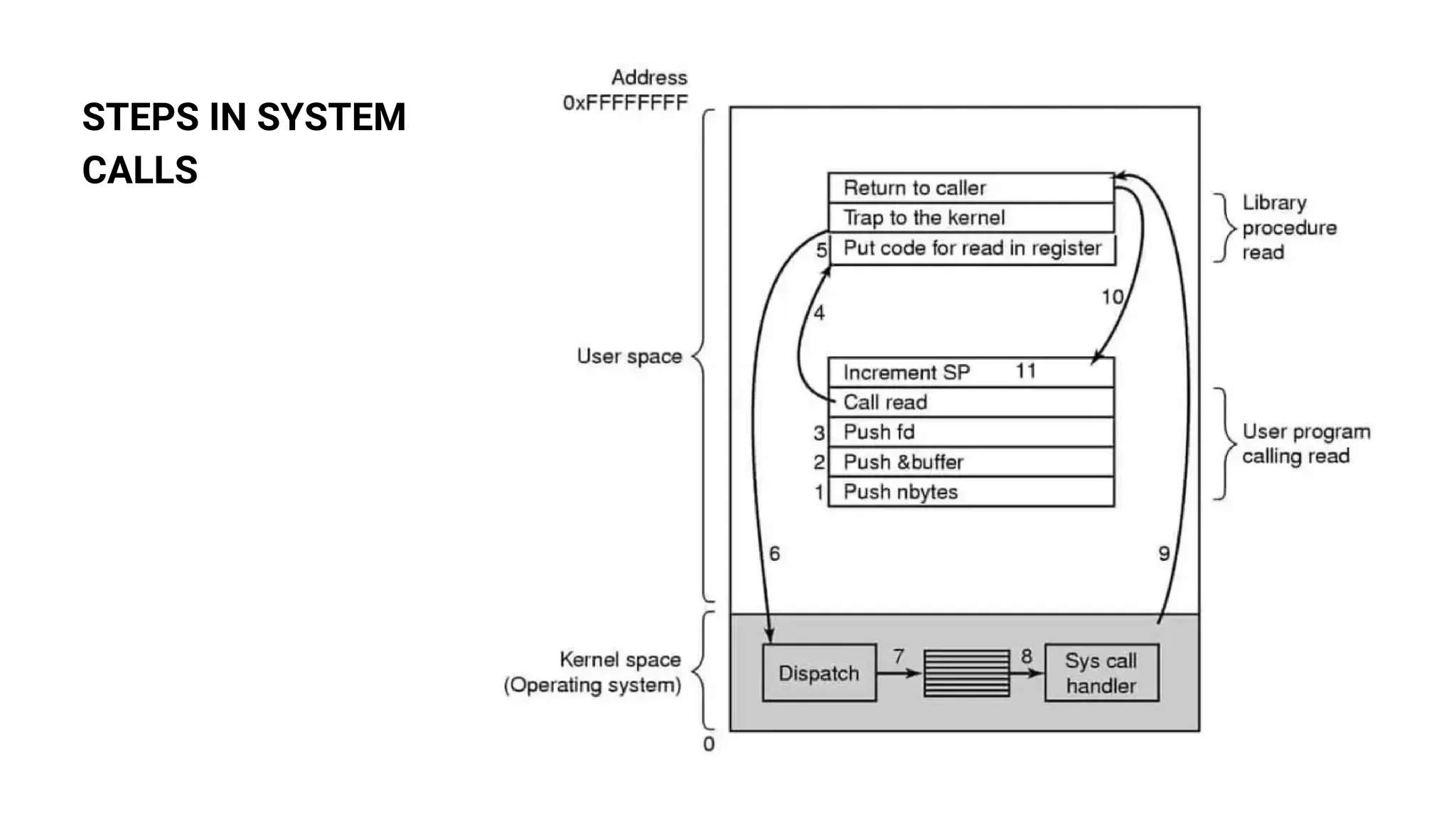
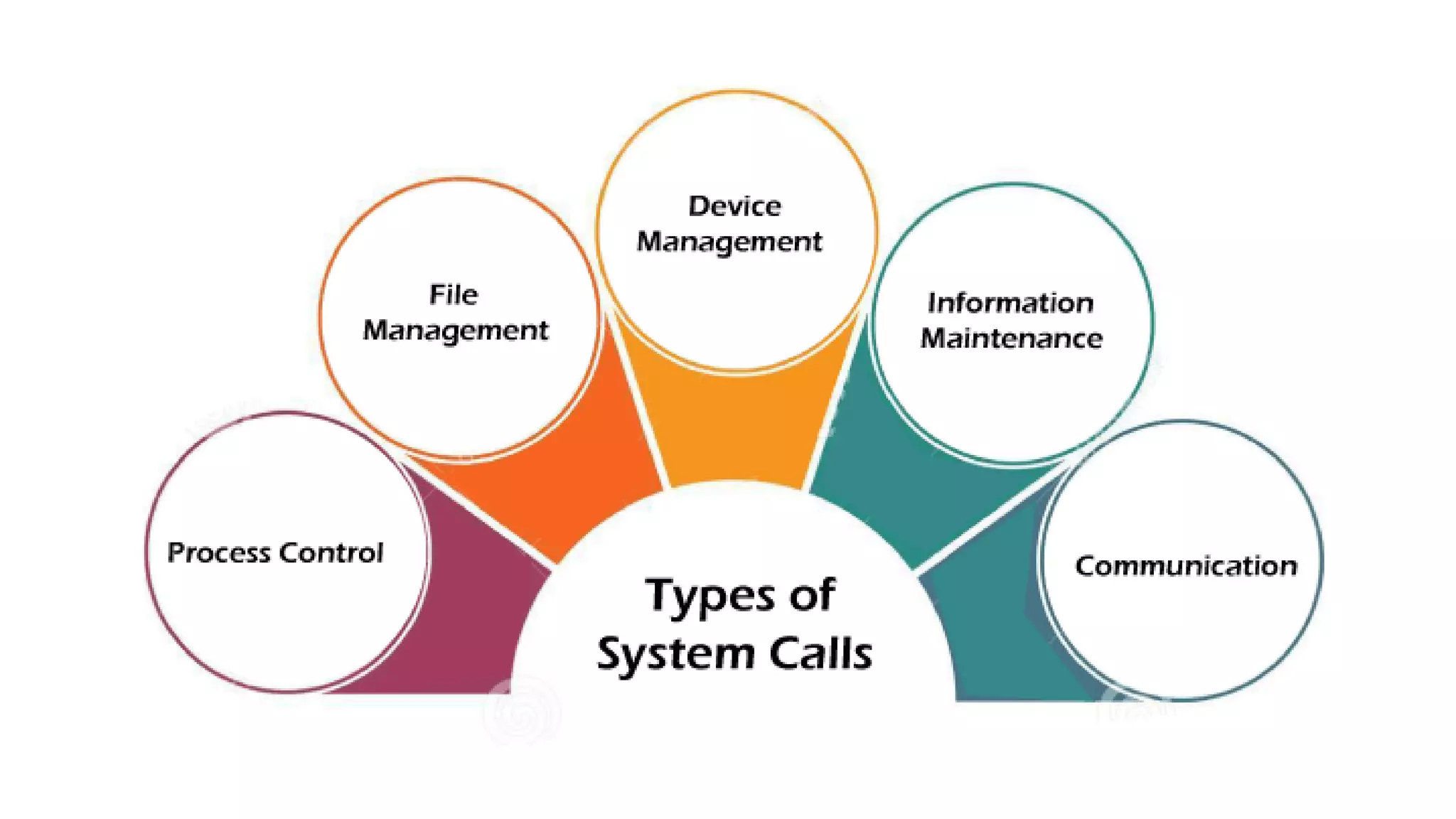
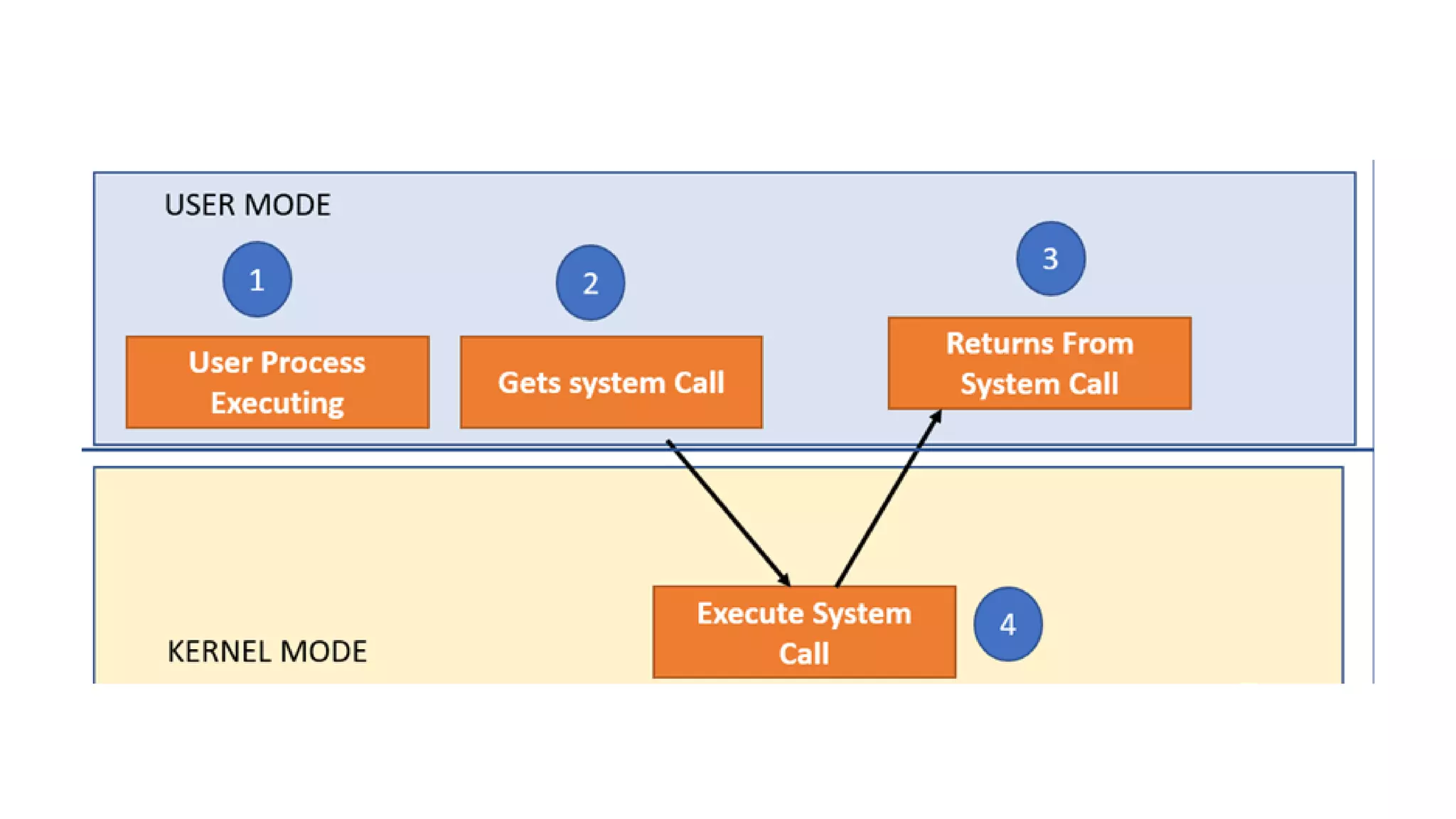
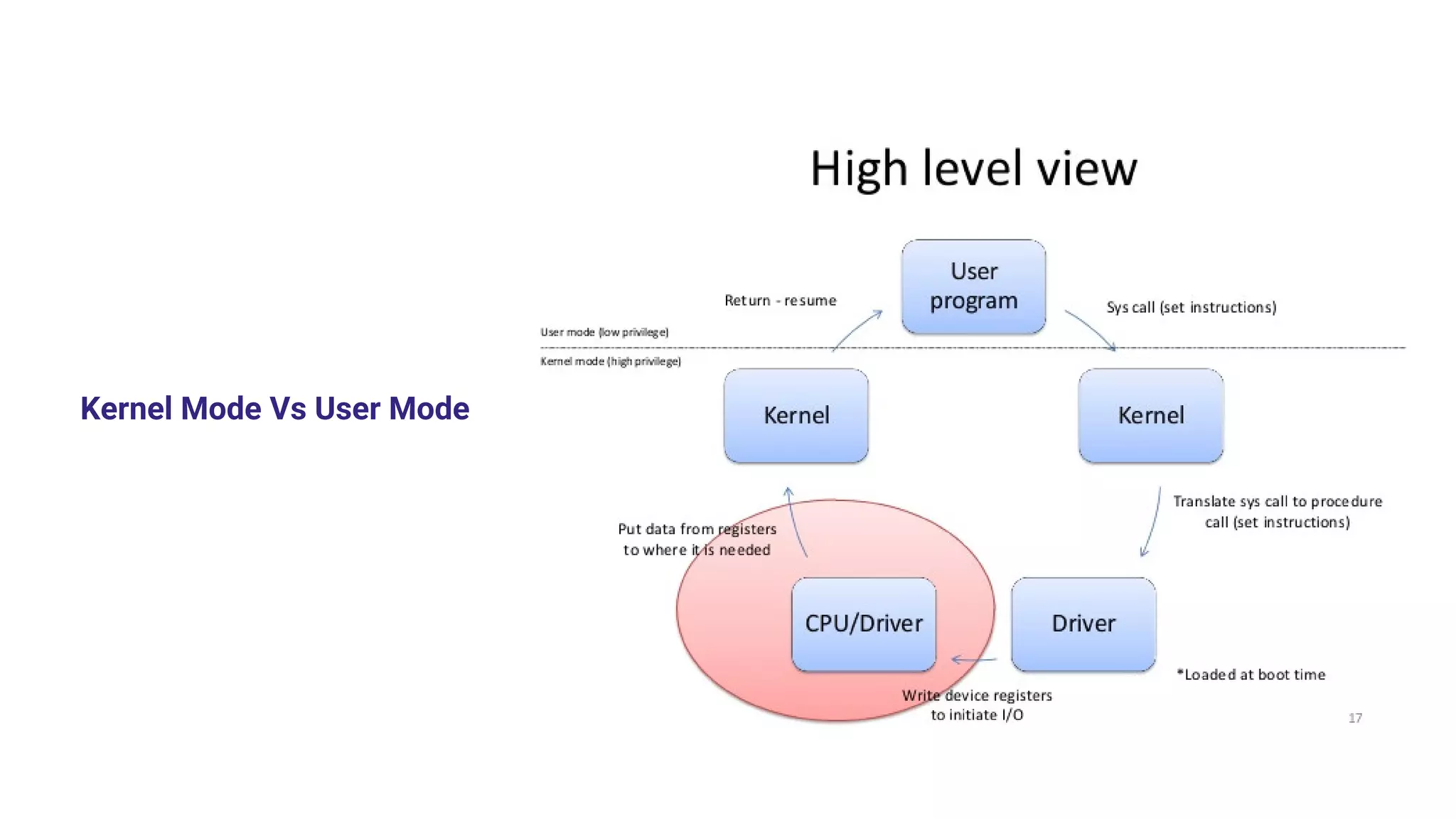
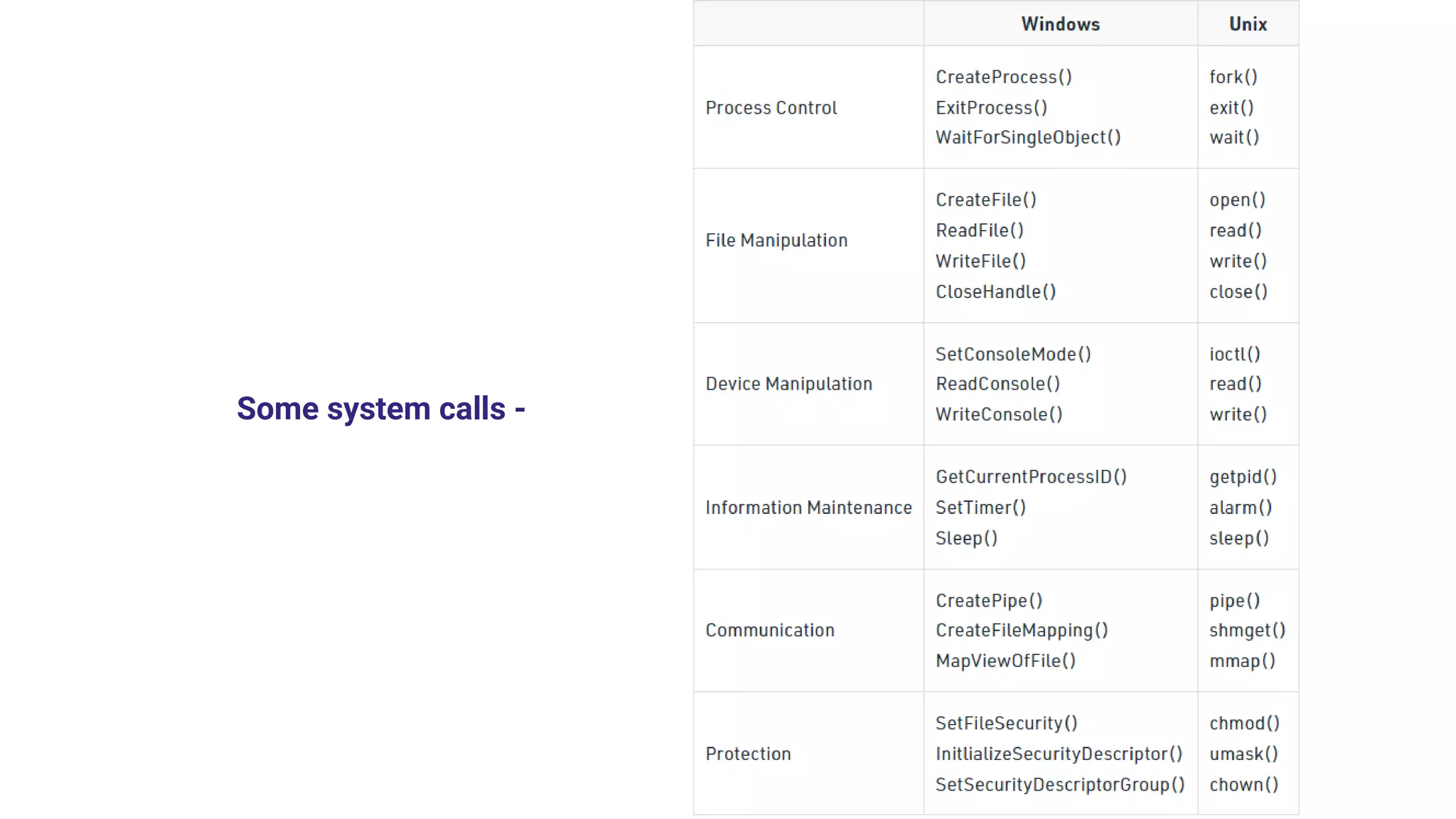
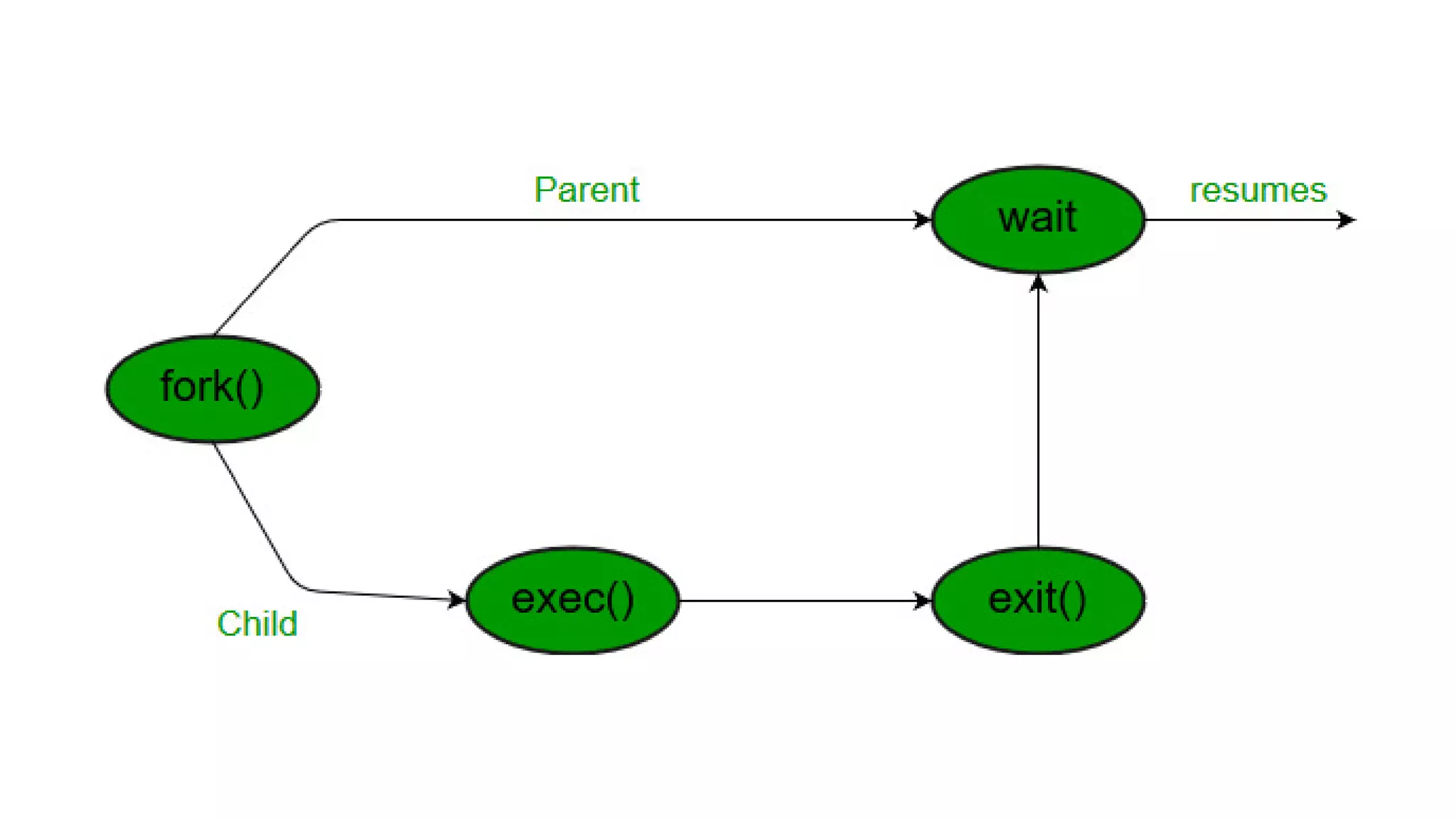
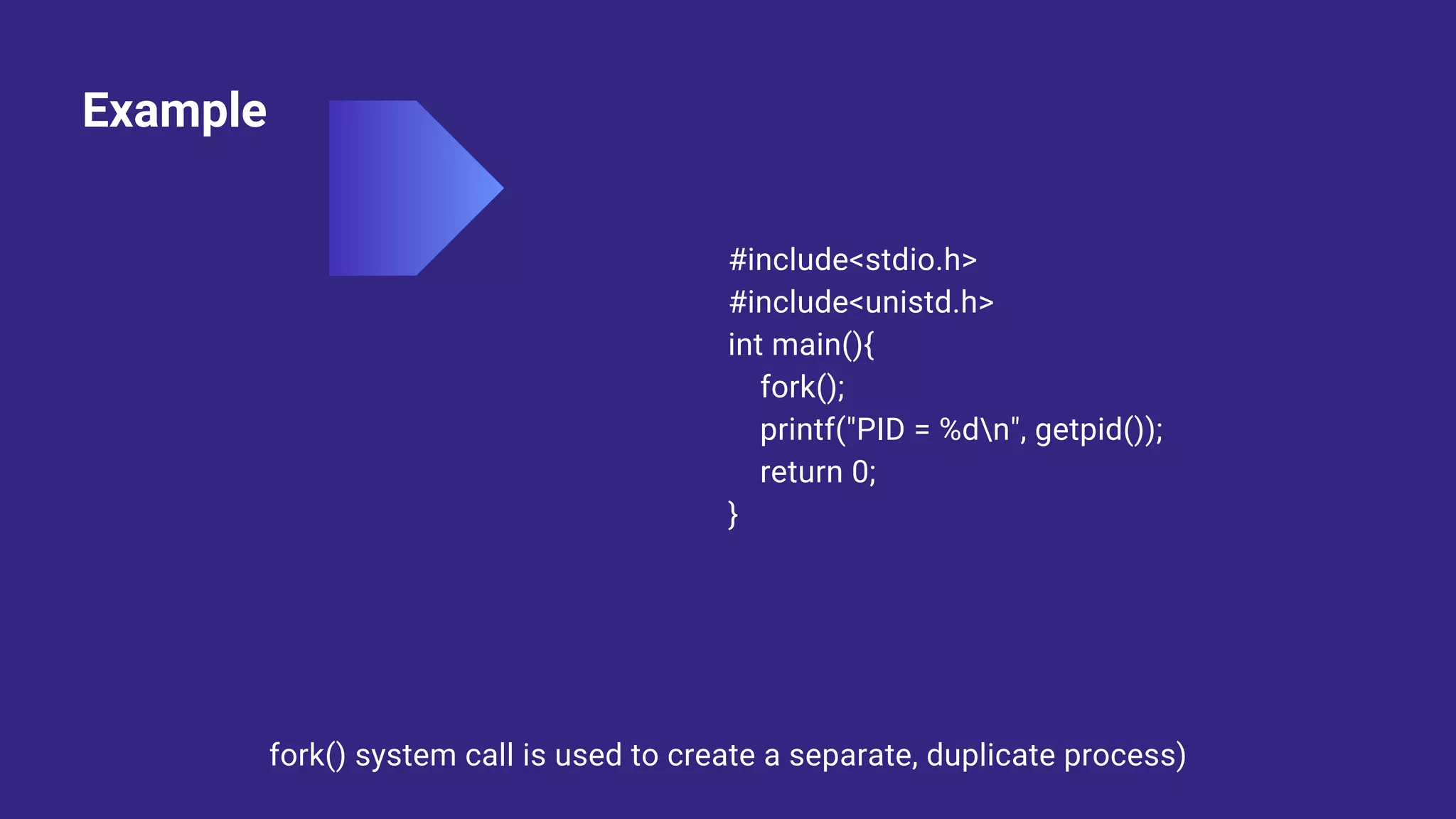
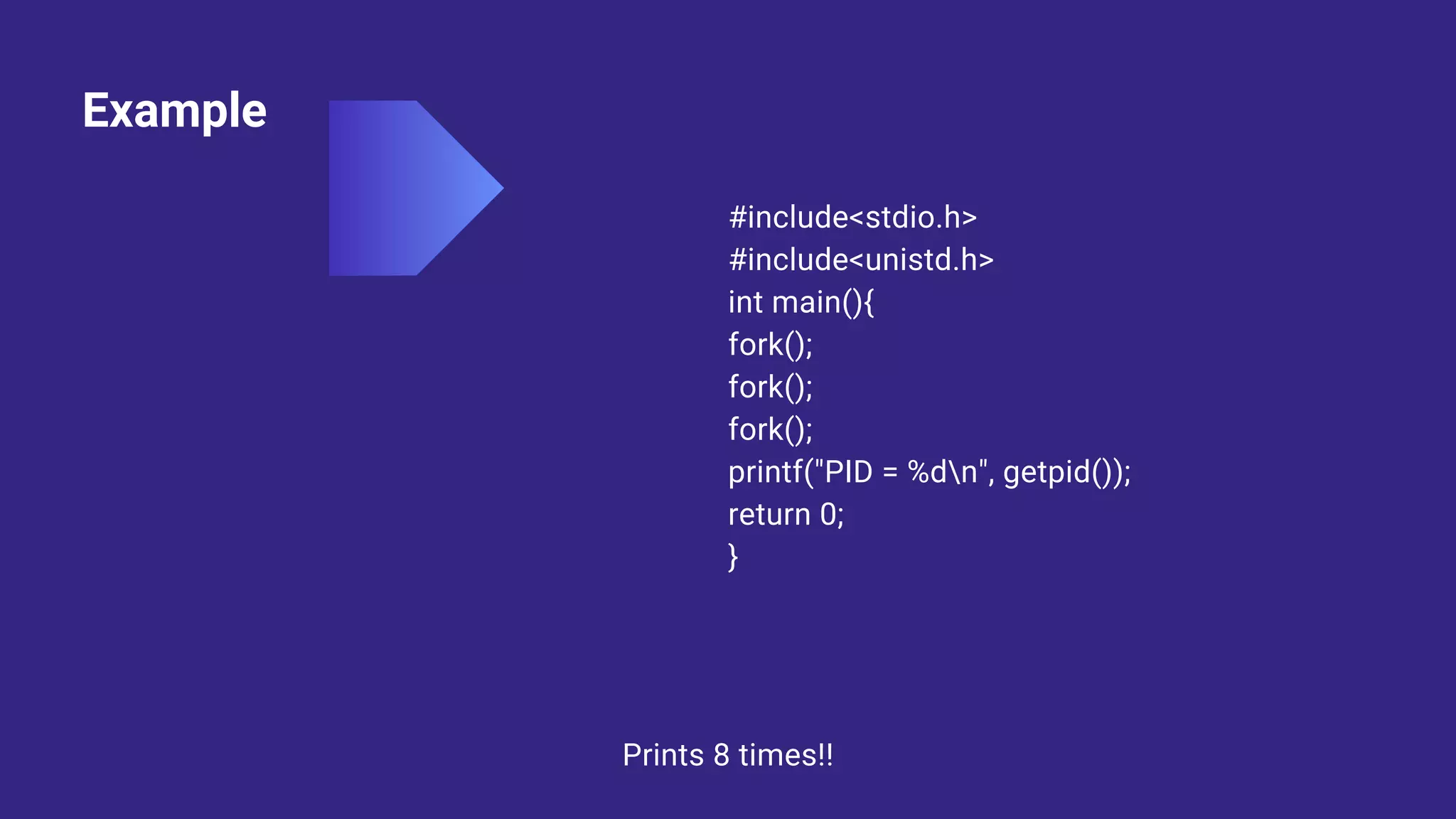
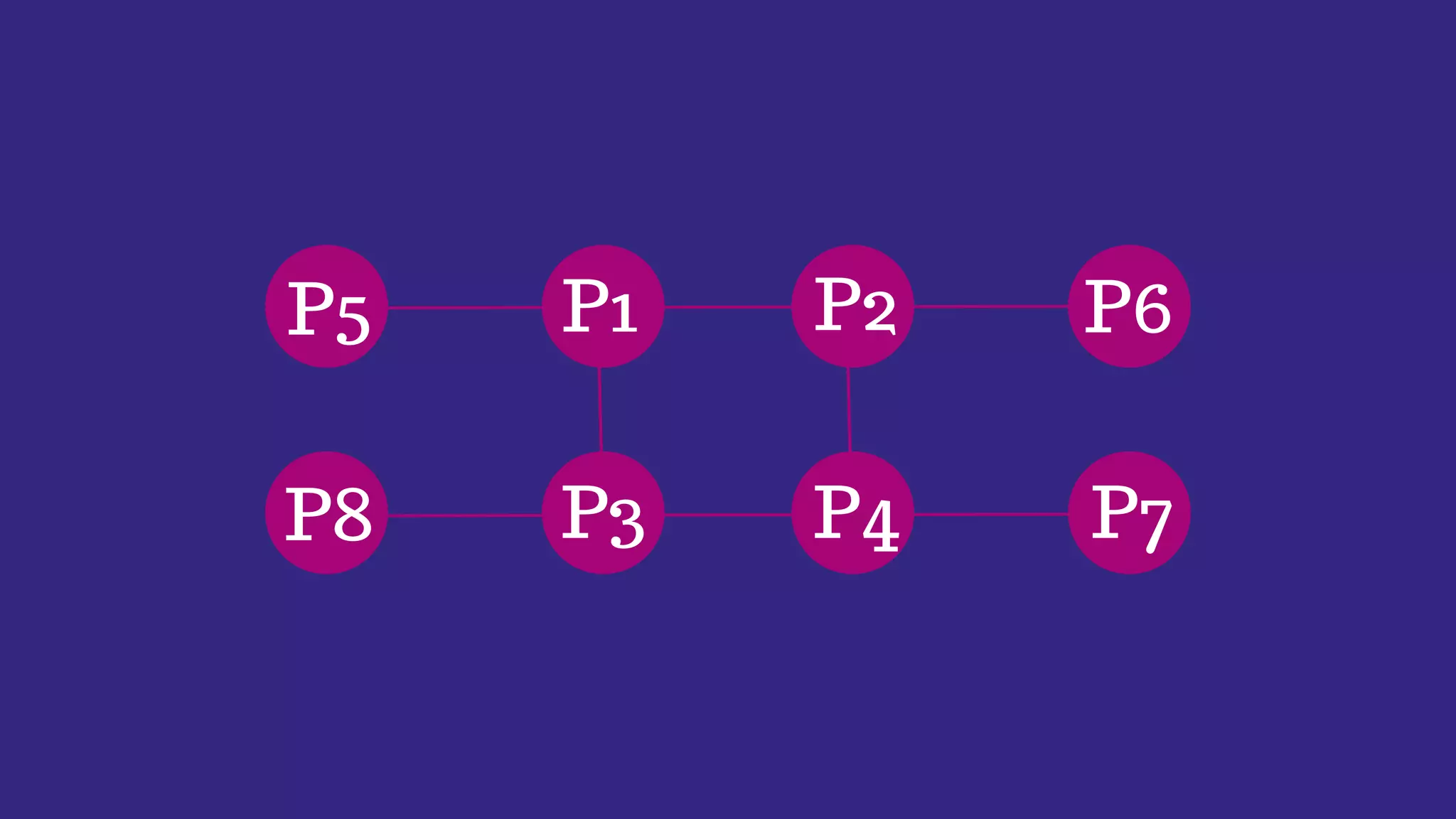
System calls allow programs to request services from the operating system kernel. Some common system calls include read and write for file access, fork for creating new processes, and wait for a parent process to wait for a child process to complete. The steps a system call takes include the program pushing parameters onto the stack, calling the library procedure to place the system call number in a register, triggering a trap instruction to switch to kernel mode, the kernel dispatching the system call to the appropriate handler, the handler running, then returning control to the user program after completing the operation.







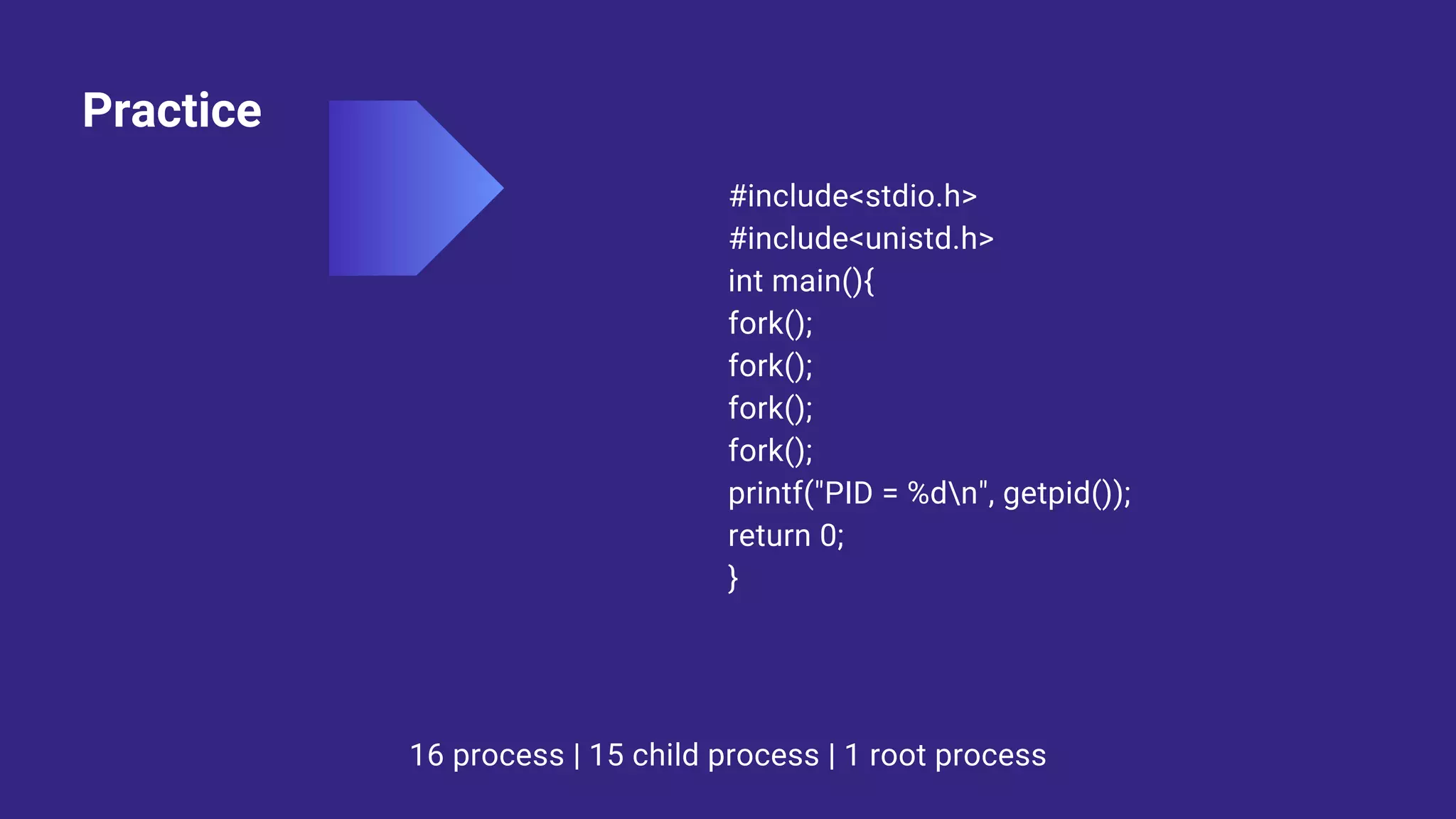
![Example
#include<stdio.h>
#include<stdlib.h>
#include<unistd.h>
#include <sys/wait.h>
int main(){
int fd[2],n;
char buffer[100];
pid_t p;
pipe(fd);
p = fork();
}
if(p>0){
close(fd[0]);
printf("Passing value to child!n");
write(fd[1],"Hello my child!!",15);
printf("n");
wait(NULL);
}
else{
close(fd[1]);
n = read(fd[0], buffer, 100);
write(1,buffer,n);
}](https://image.slidesharecdn.com/systemcalls-introductionos-230415061220-2ff1182d/75/System-Calls-Introduction-17-2048.jpg)