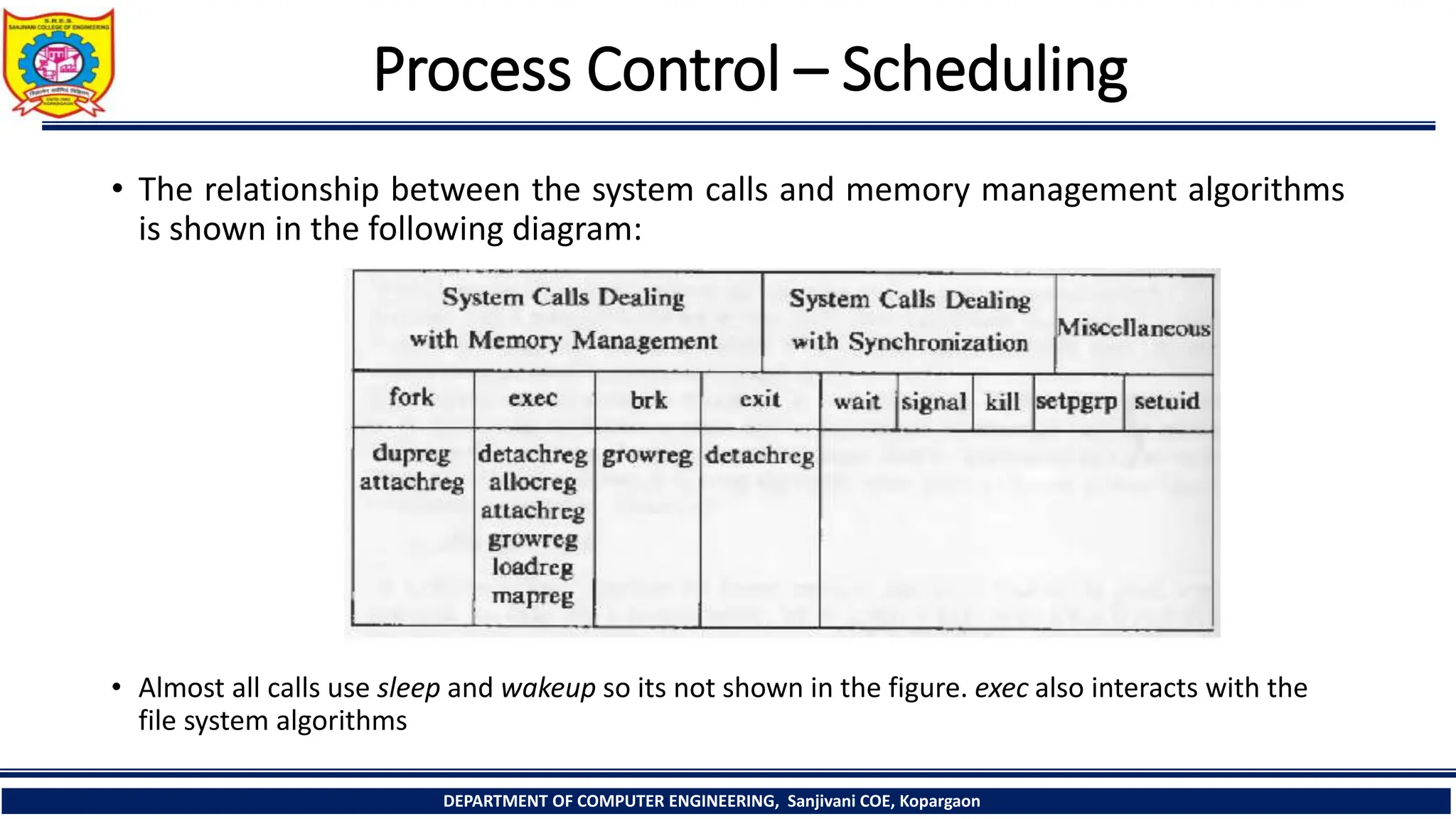
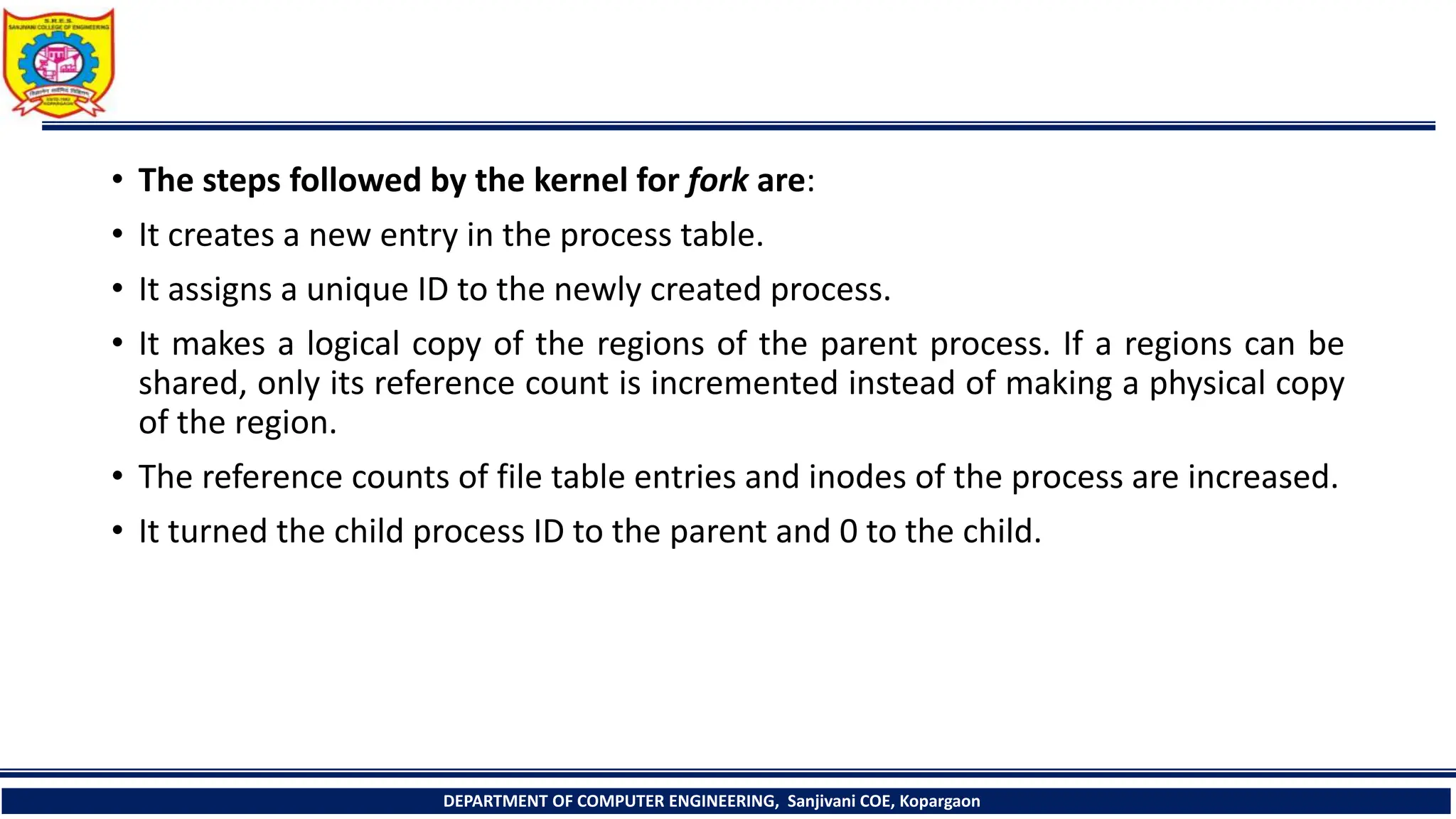
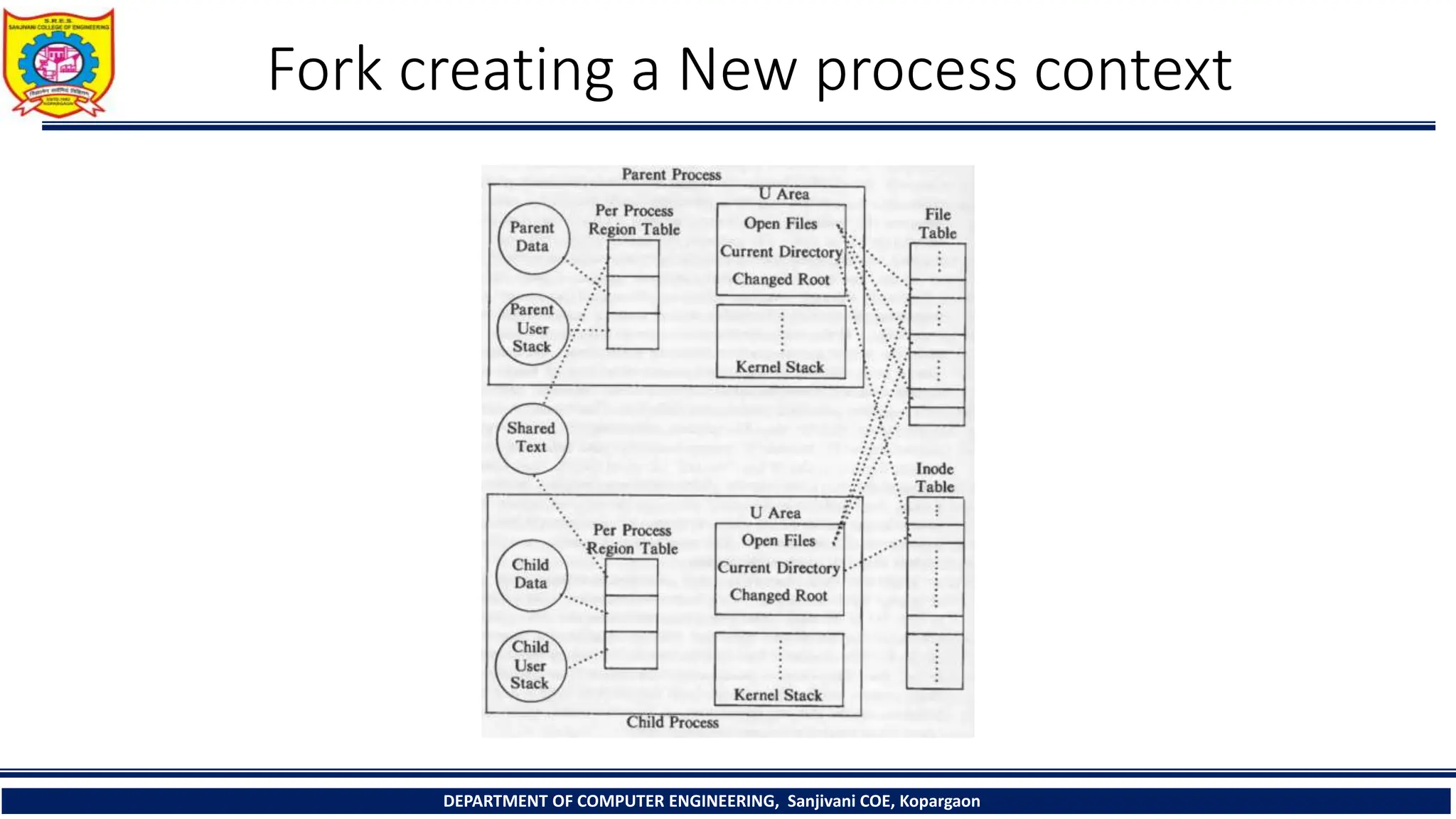
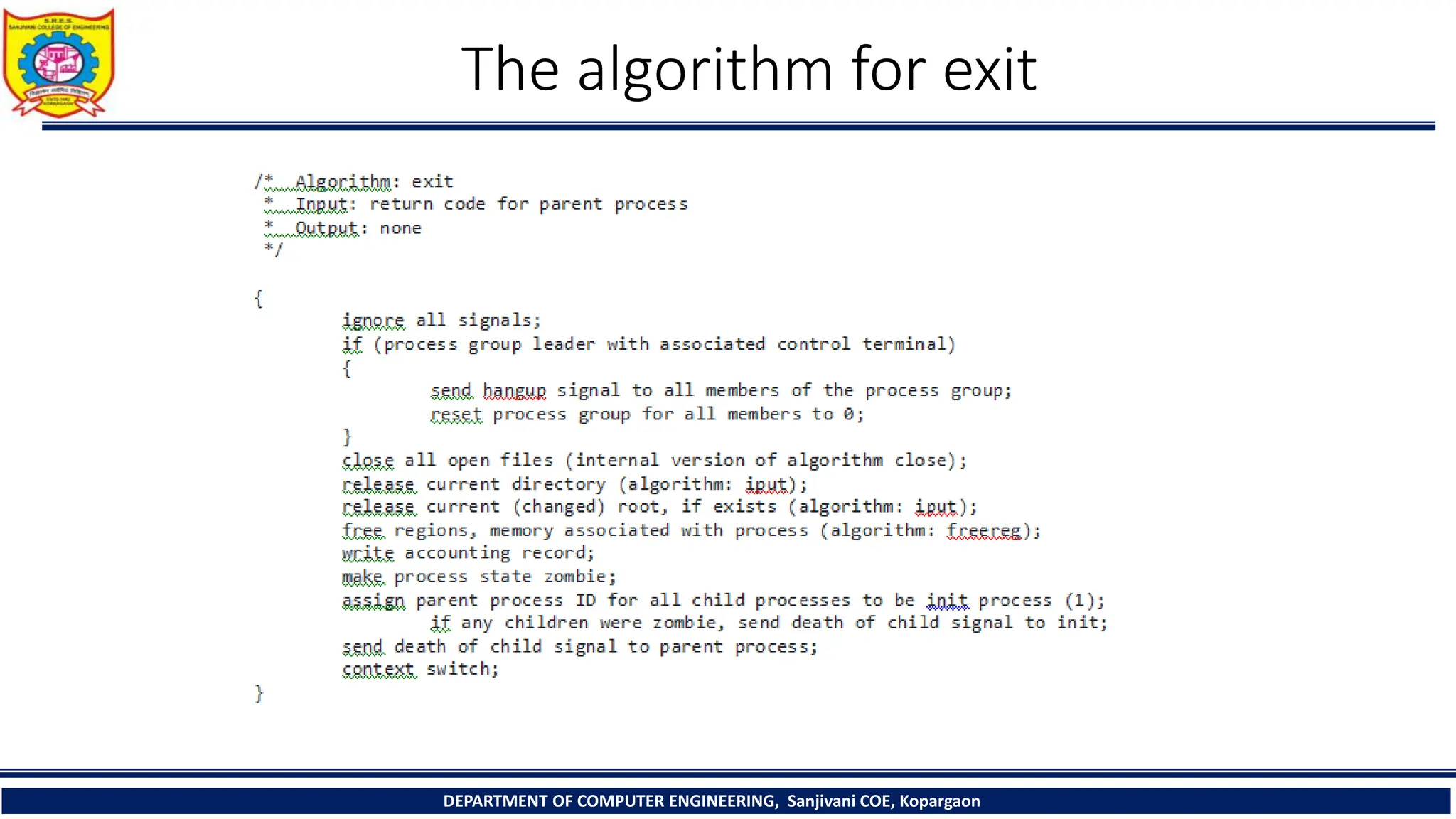
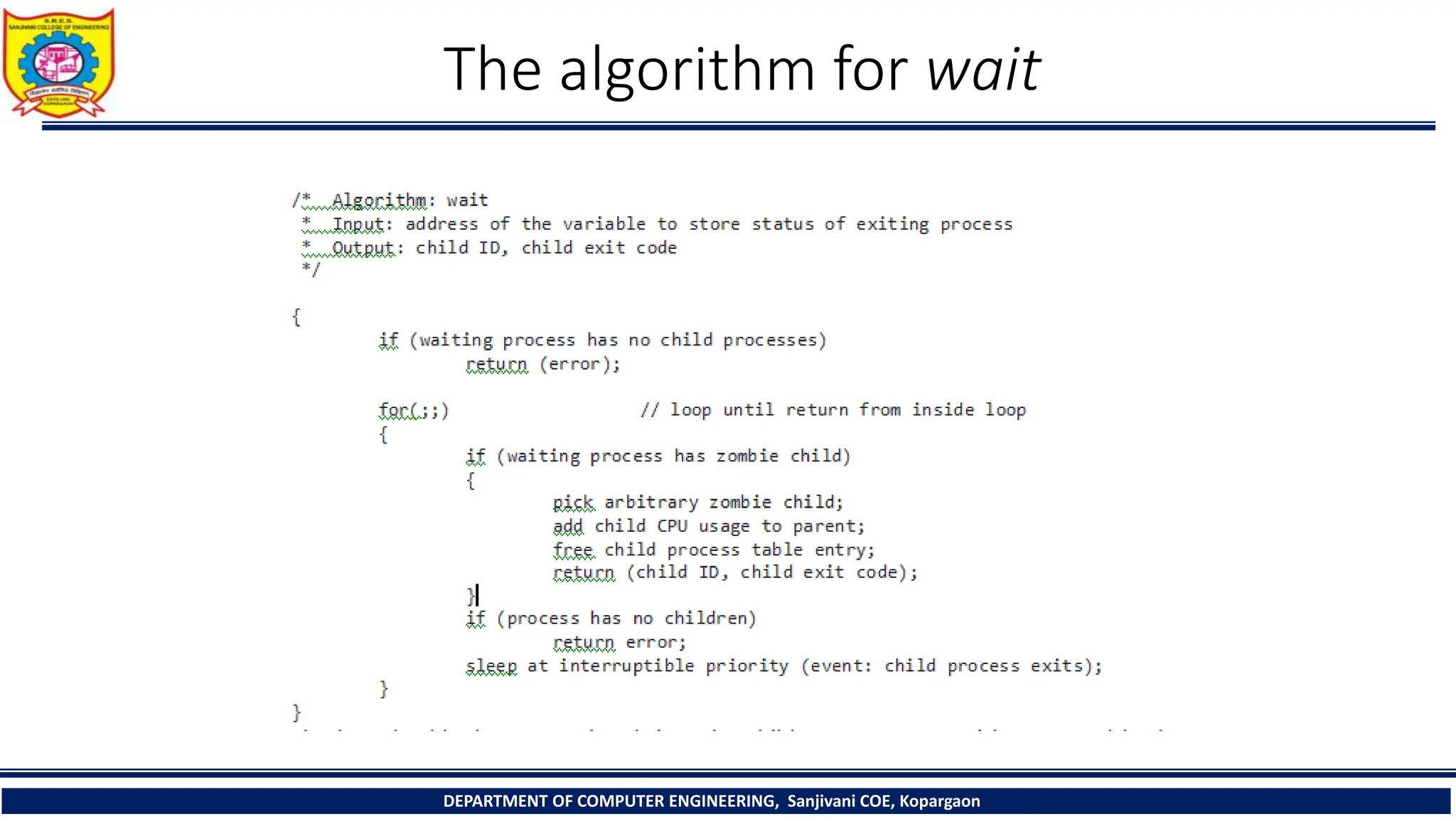
The document outlines the structure and management of processes in Unix systems, detailing concepts like process creation, scheduling, signals, and termination. Key functionalities such as the fork and exec system calls are explained, along with signal handling and user ID management. It also provides insights into process control algorithms and the interaction between various system components.