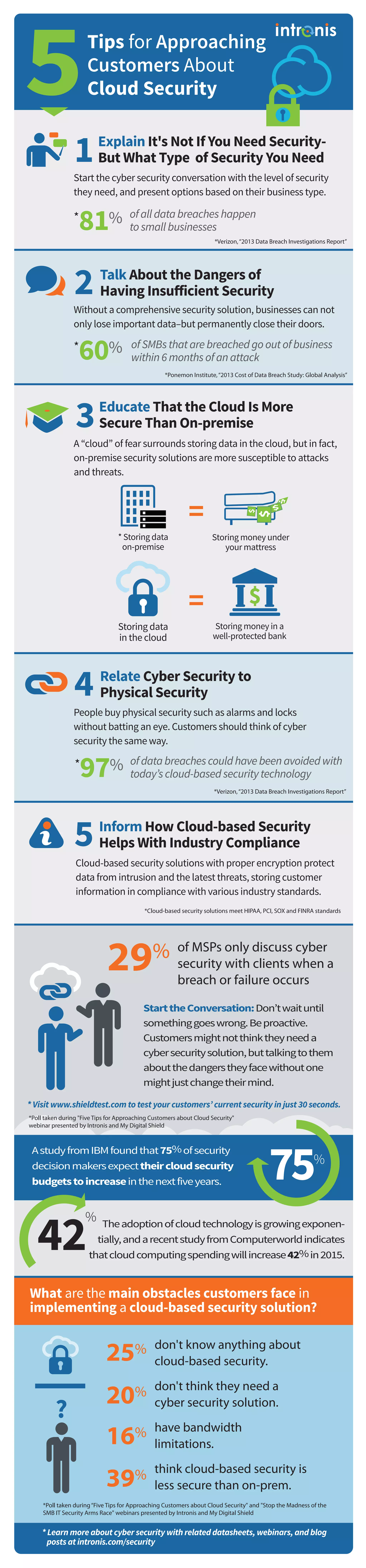
A study from IBM reveals that 75% of security decision-makers anticipate increased cloud security budgets in the next five years, driven by a 42% spike in cloud computing spending projected for 2015. The document highlights the vulnerability of small businesses to data breaches and emphasizes the superiority of cloud-based security solutions over on-premise systems. It advocates for proactive discussions about cybersecurity with clients, stressing the importance of compliance and the need for proper security solutions.