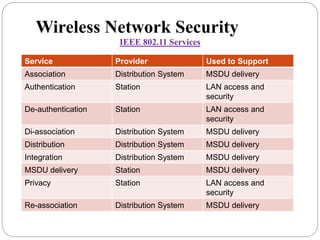
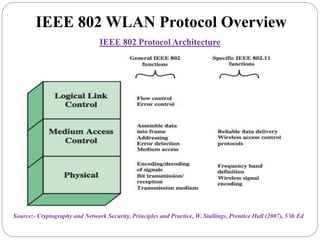
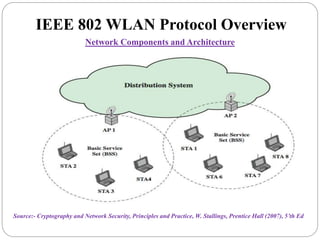
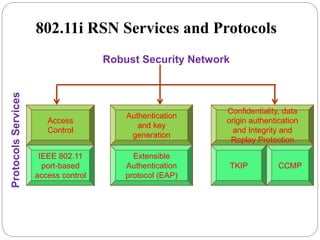
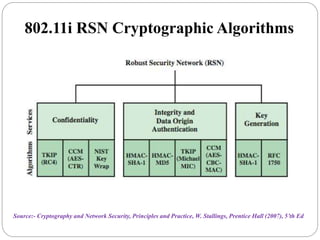
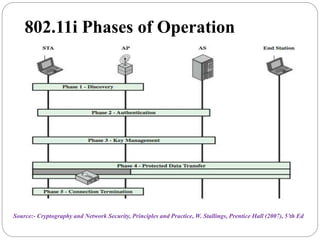
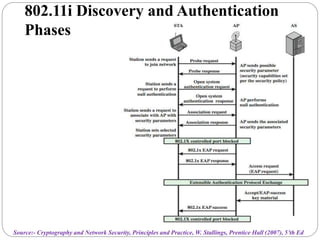
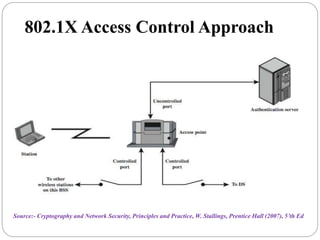
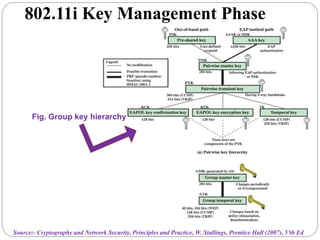
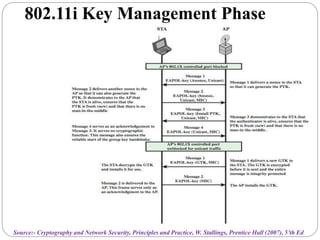
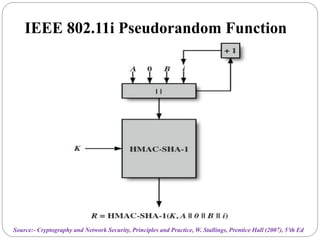
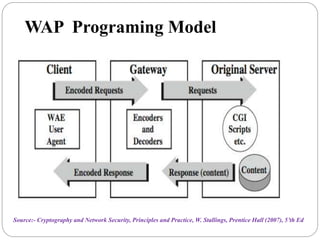
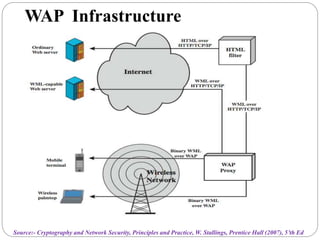
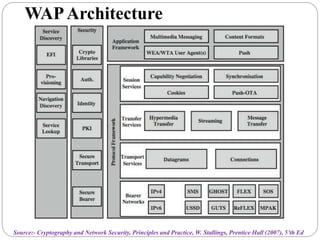
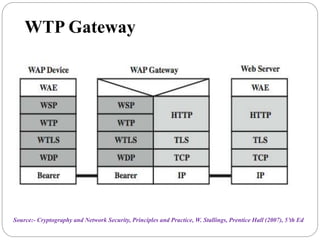
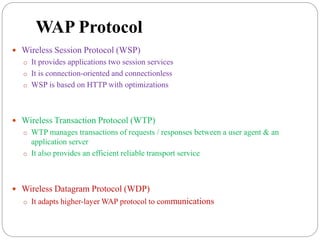
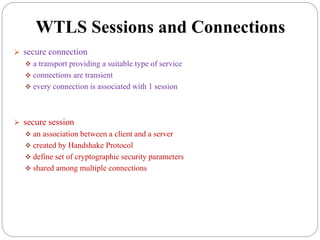
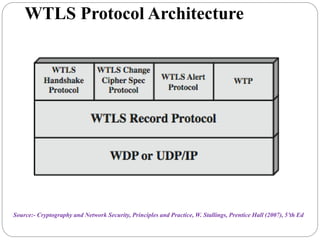
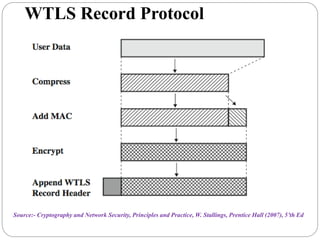
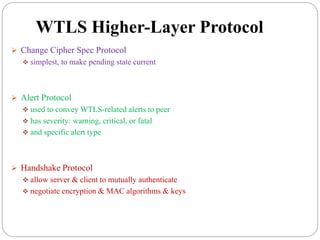
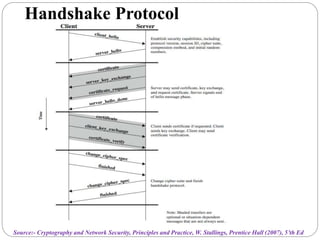
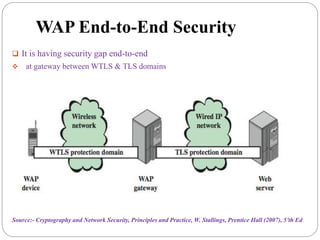
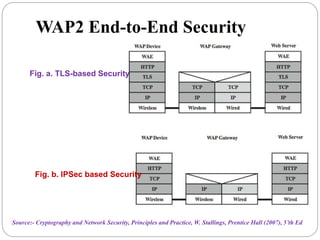
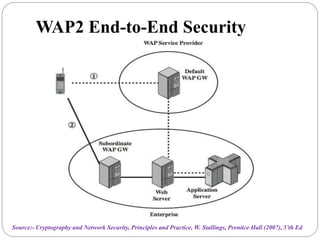
This document summarizes wireless network security standards and protocols including IEEE 802.11, WPA, WAP, and WTLS. It discusses authentication, encryption, and key management in 802.11i and the phases of operation. It provides an overview of the WAP programming model, markup language, and architecture including the WTP gateway. It describes how WTLS provides security between mobile devices and gateways based on TLS, and its handshake protocol. Finally, it mentions the security gap between WTLS and TLS domains when moving to WAP end-to-end security.