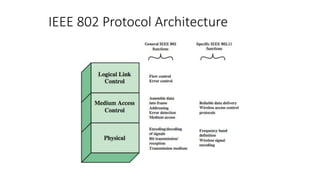
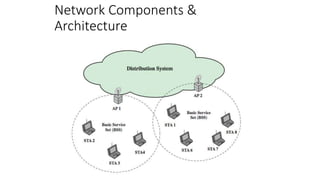
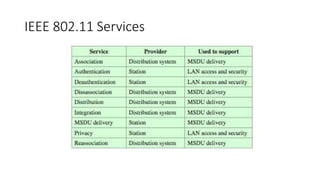
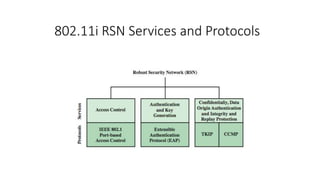
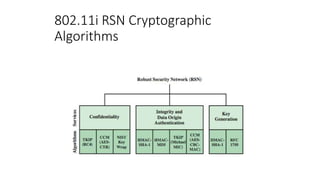
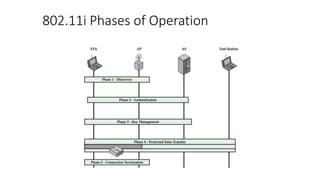
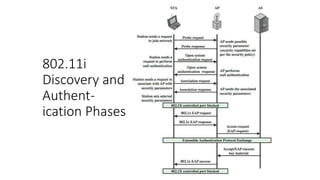
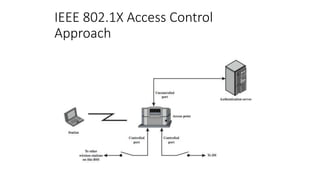
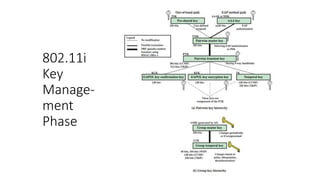
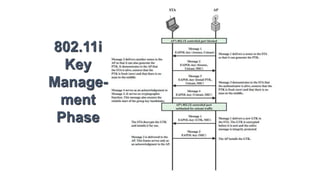
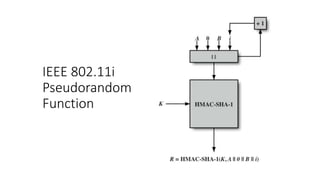
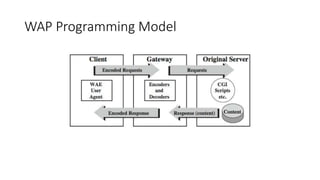
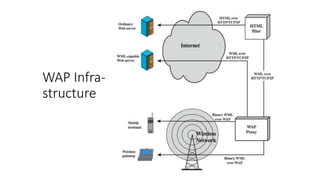
The document discusses the history and standards for wireless local area networks (WLANs) and security. It describes how the IEEE 802.11 standard was established and how the Wireless Ethernet Compatibility Alliance (later the Wi-Fi Alliance) was formed to promote interoperability. It also summarizes the evolution of WLAN security standards from the flawed Wired Equivalent Privacy (WEP) protocol to the 802.11i and Wi-Fi Protected Access (WPA) security enhancements.