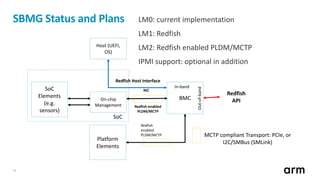
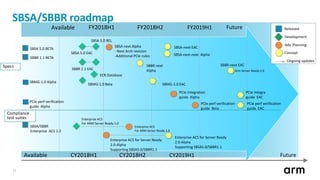
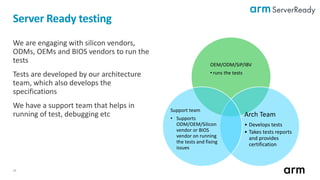
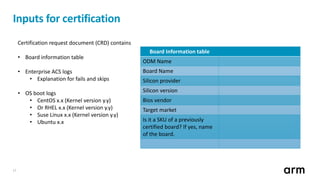
The document outlines updates and specifications related to ARM's ServerBase System Architecture (SBSA) and ServerBase Boot Requirements (SBBR) aimed at enhancing server interoperability. It details the progress on upcoming versions, including SBSA v5.0 and SBBR v1.1, and introduces the process for submitting engineering change requests. Additionally, the document highlights ongoing improvements in PCI Express (PCIe) and mentions resources for testing compliance with the SBSA and SBBR standards.