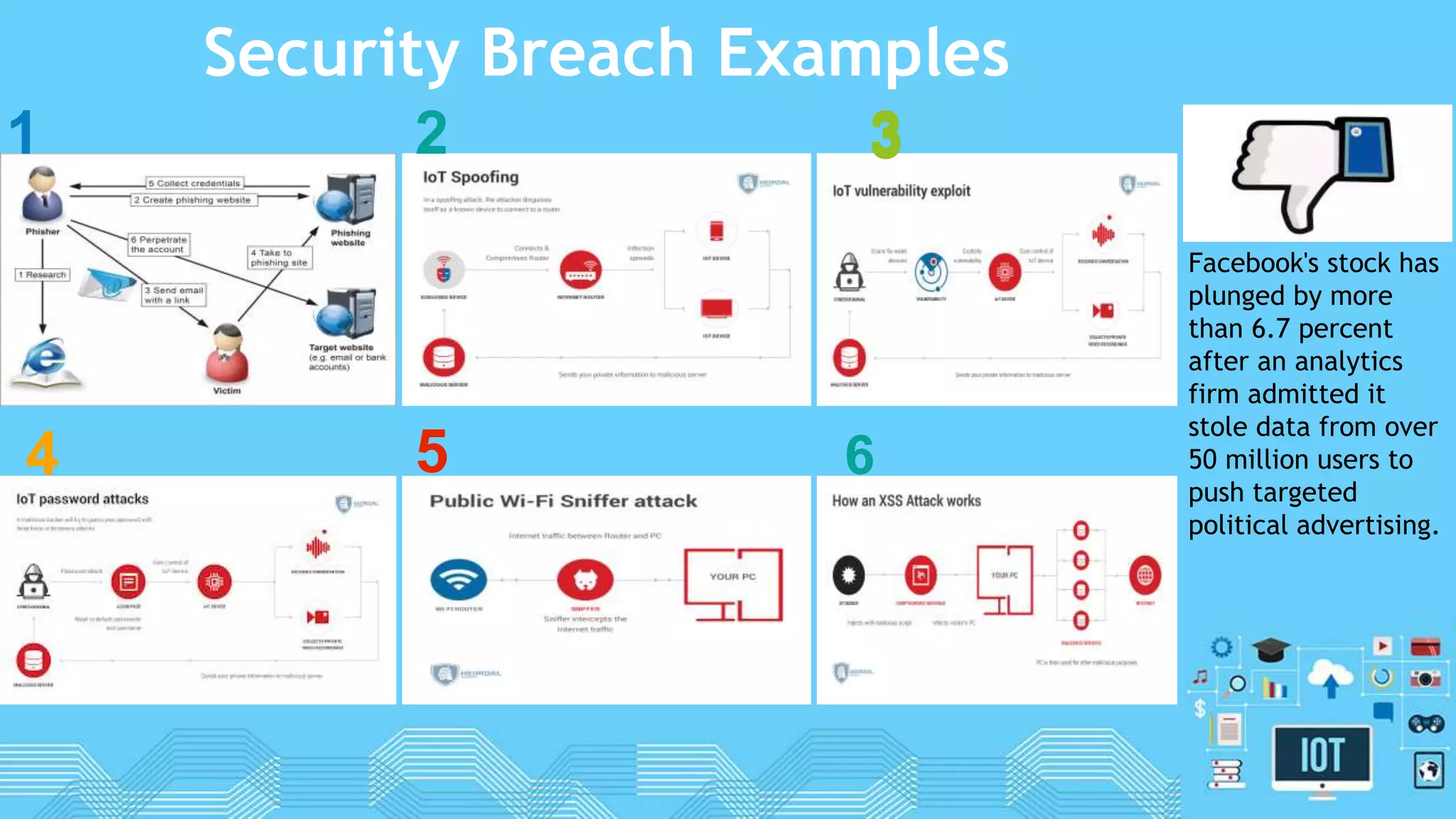
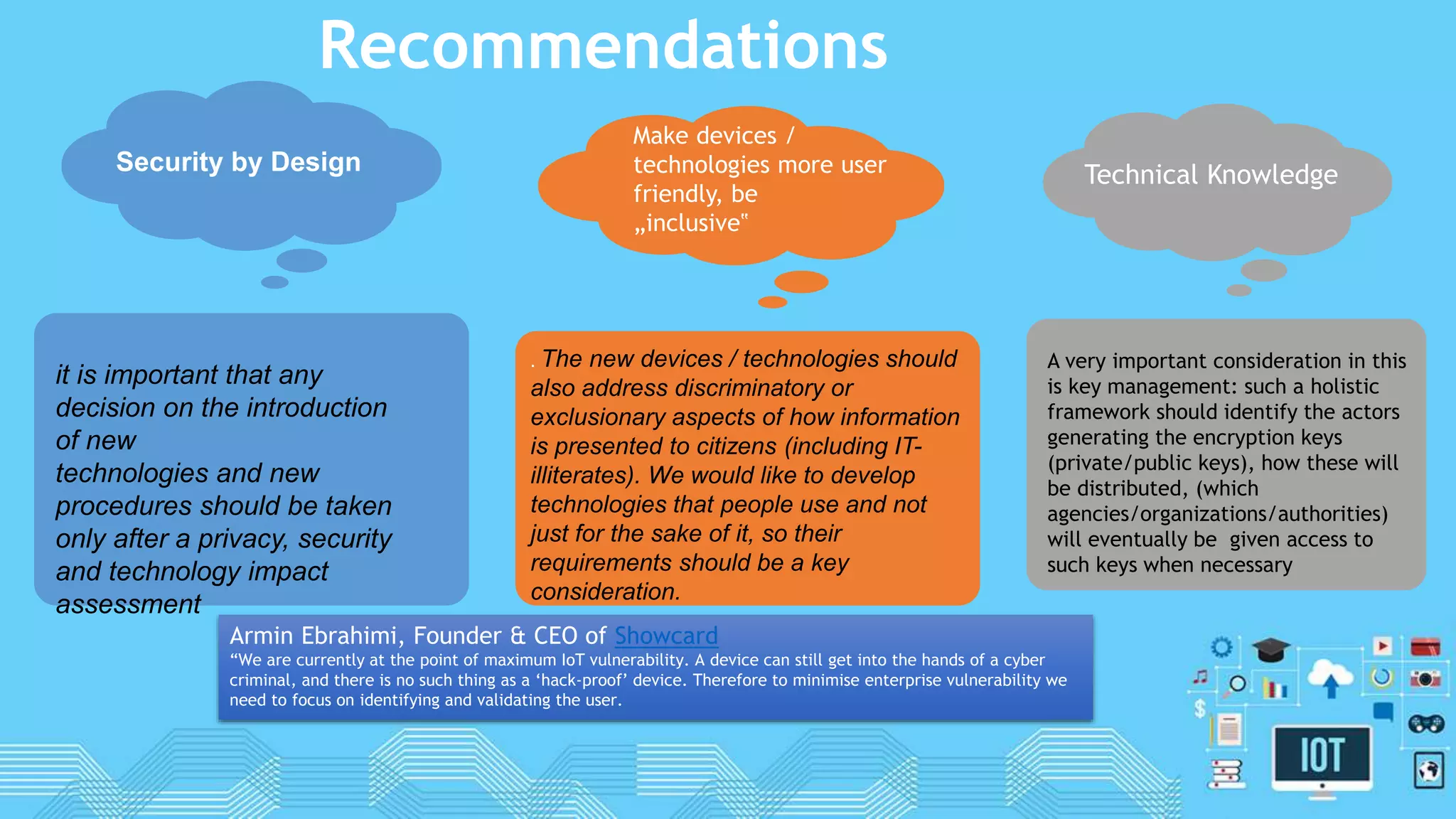
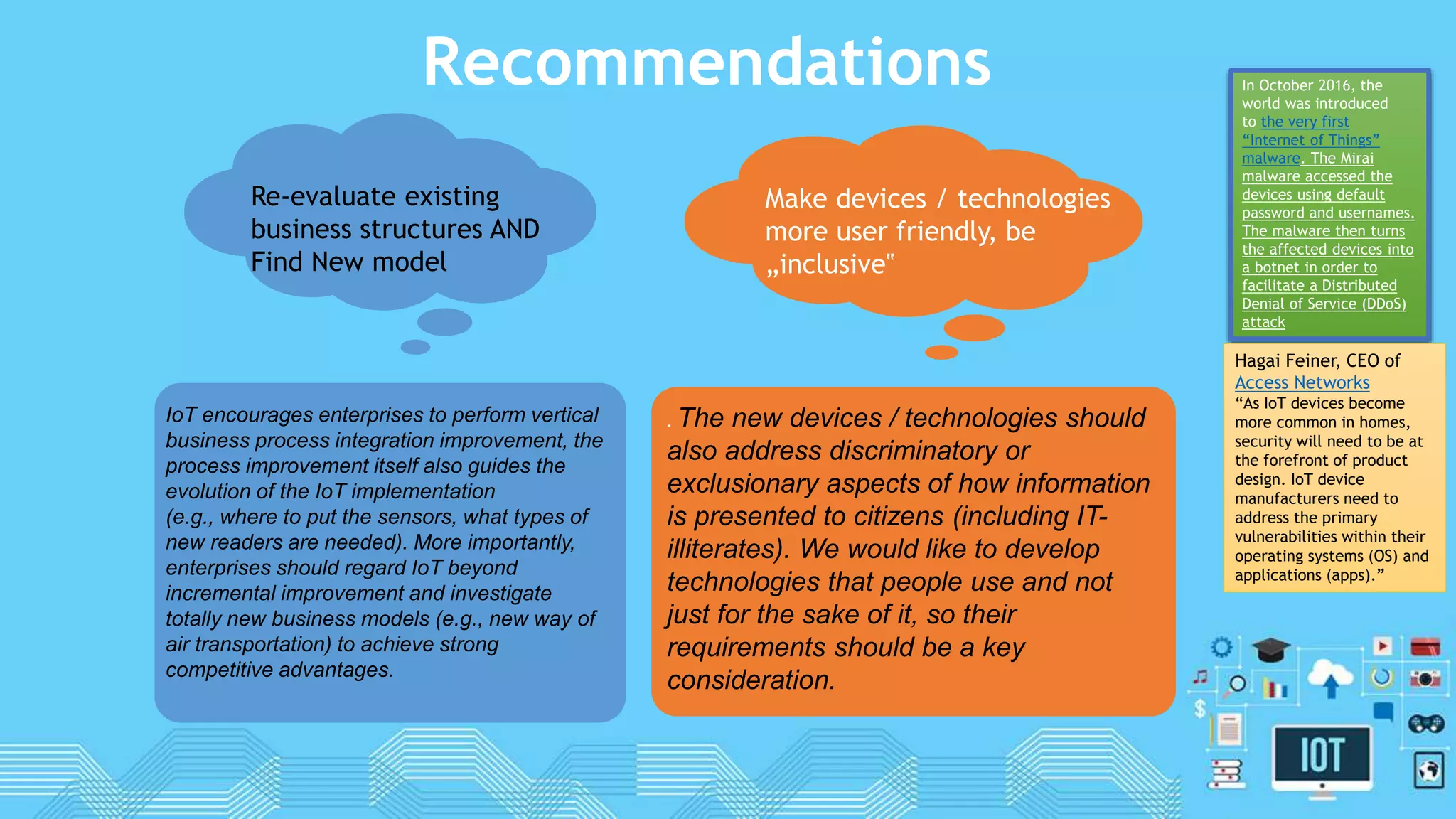
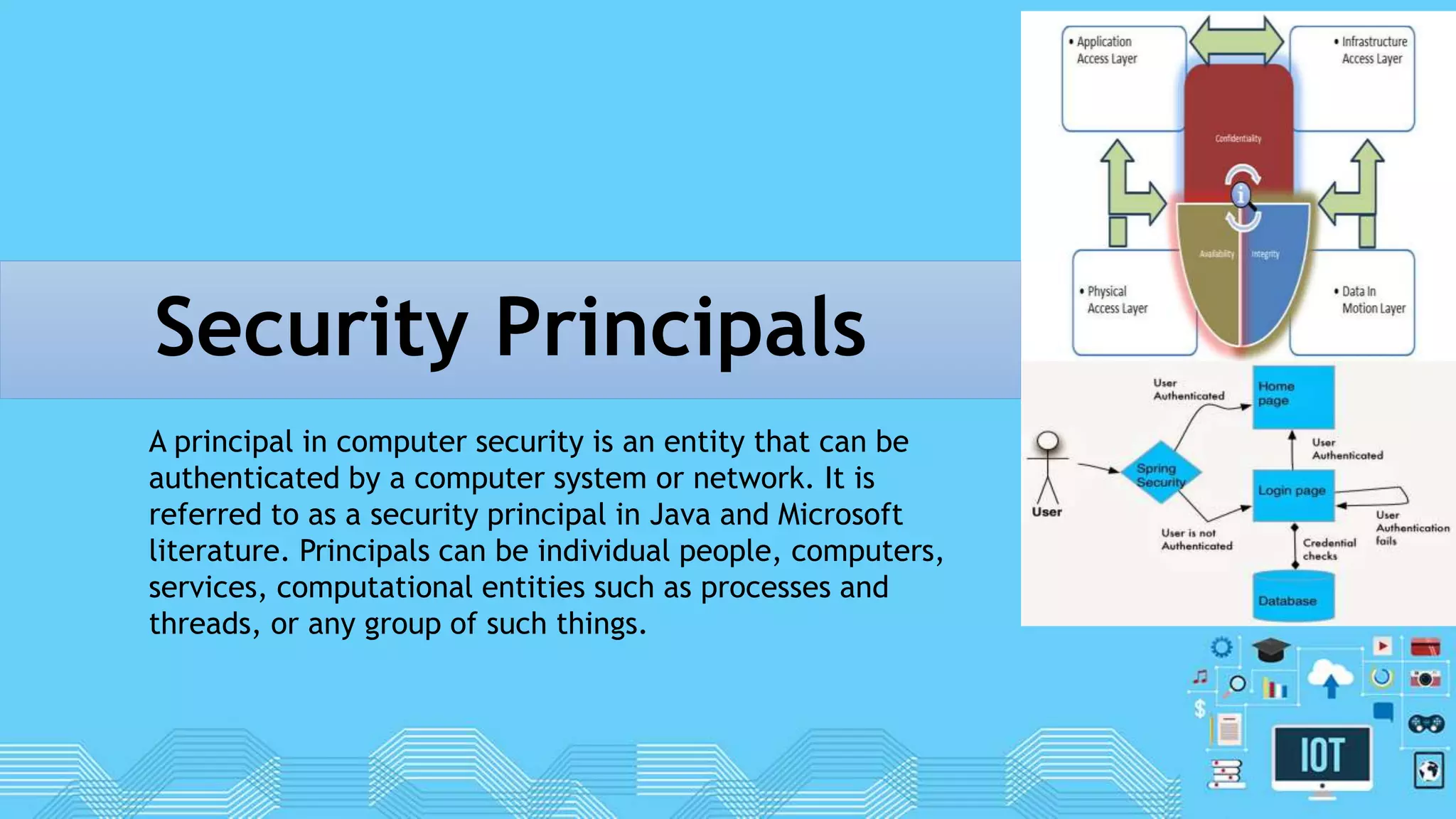
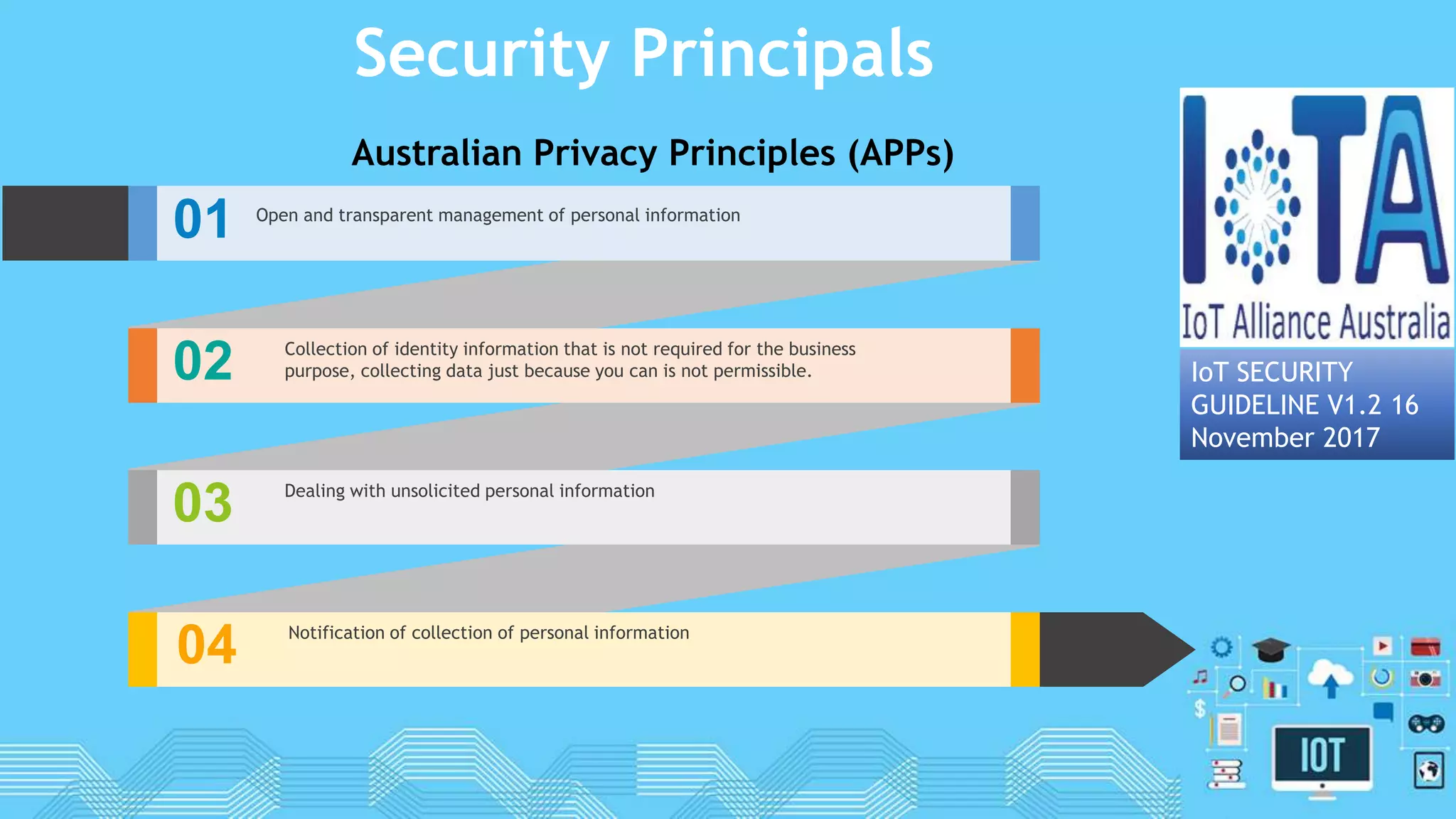
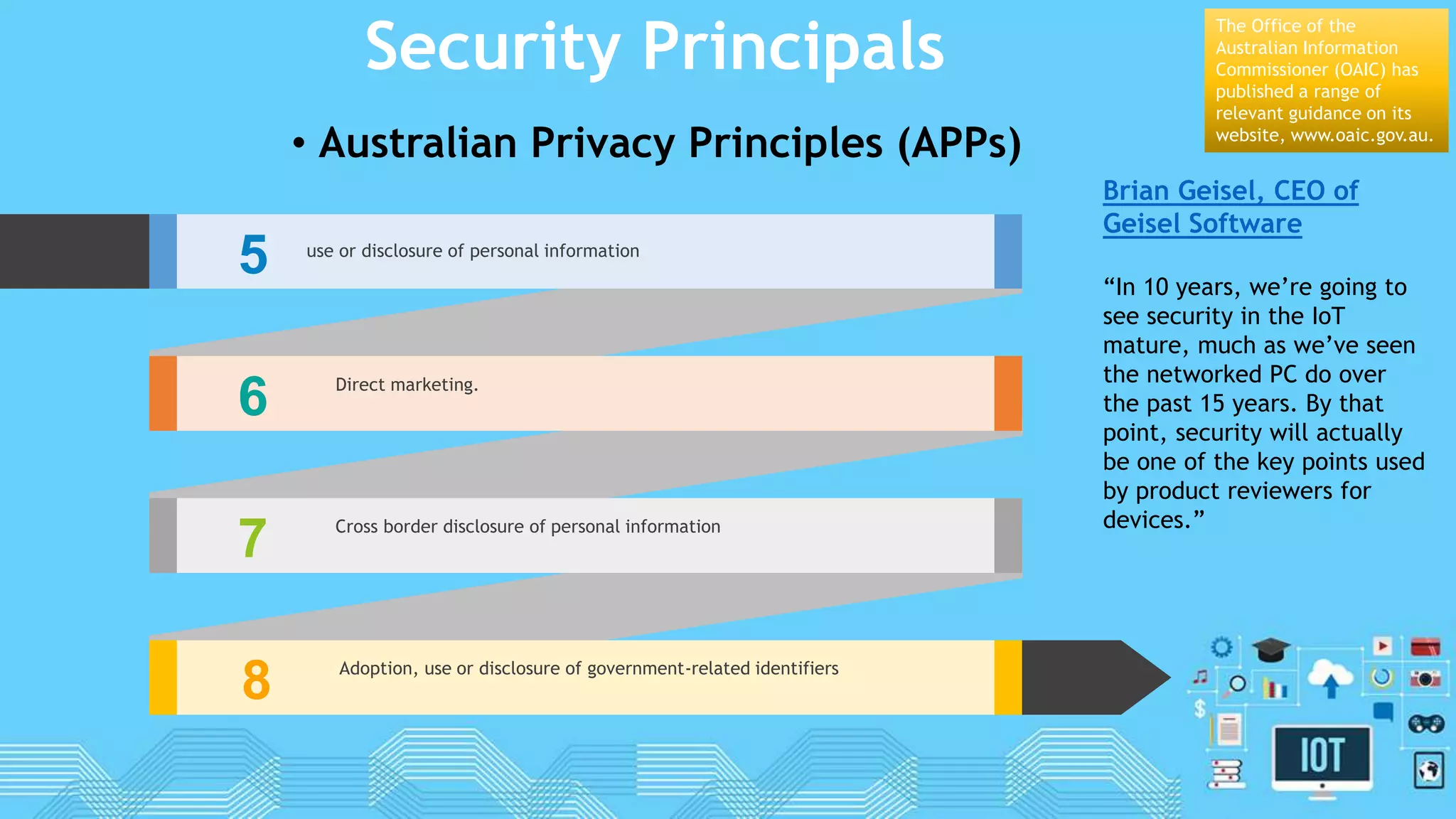
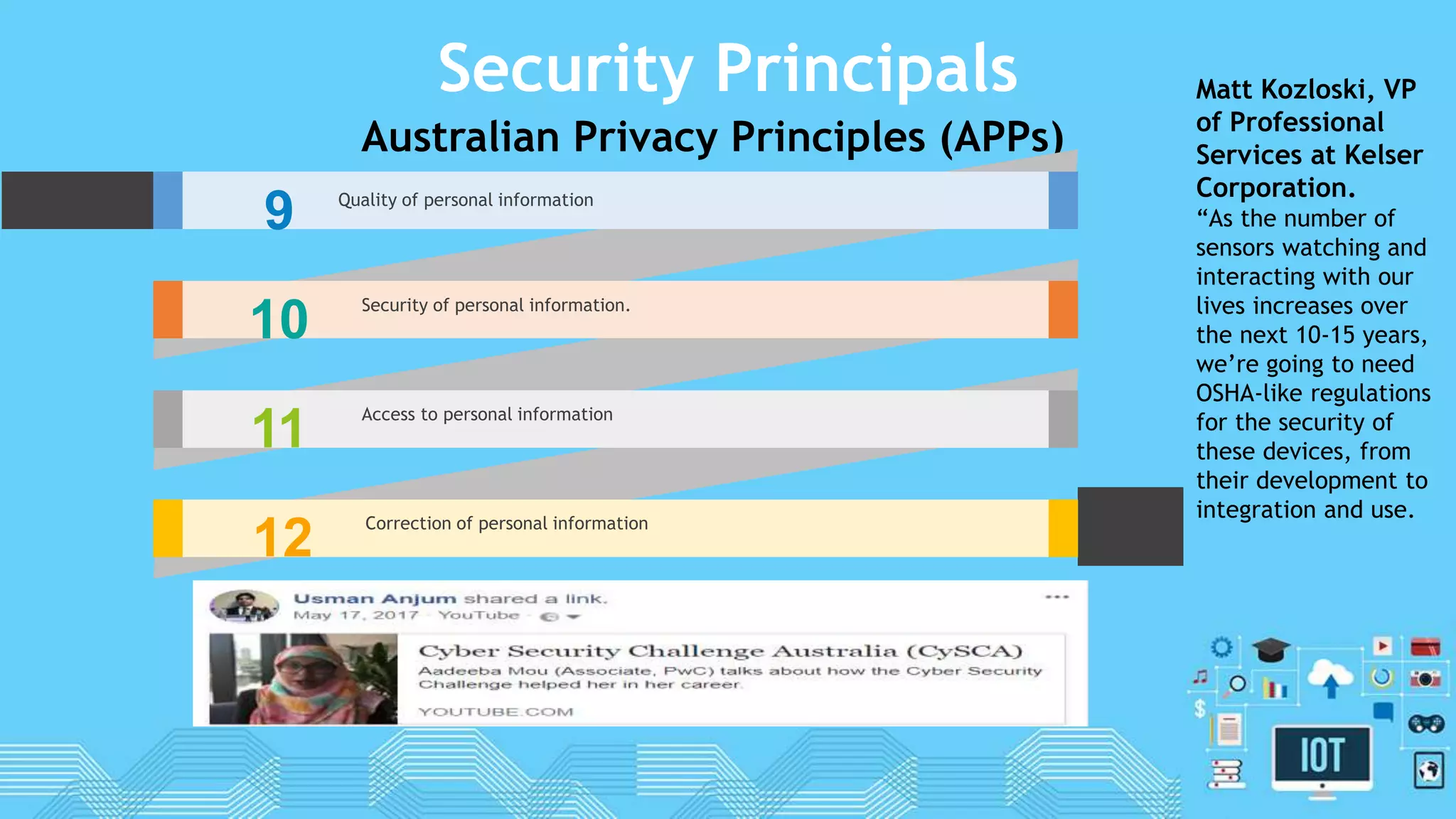
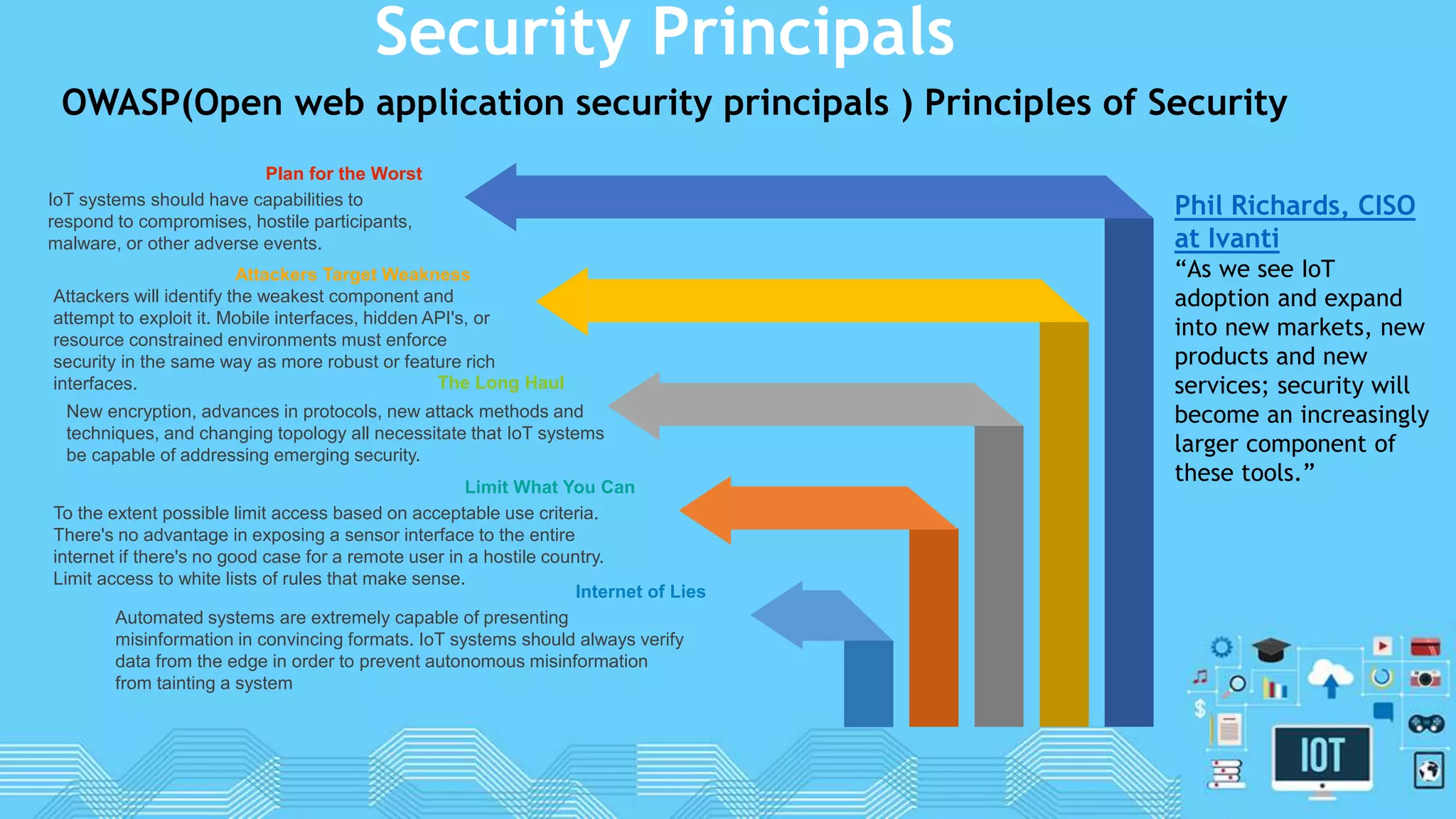
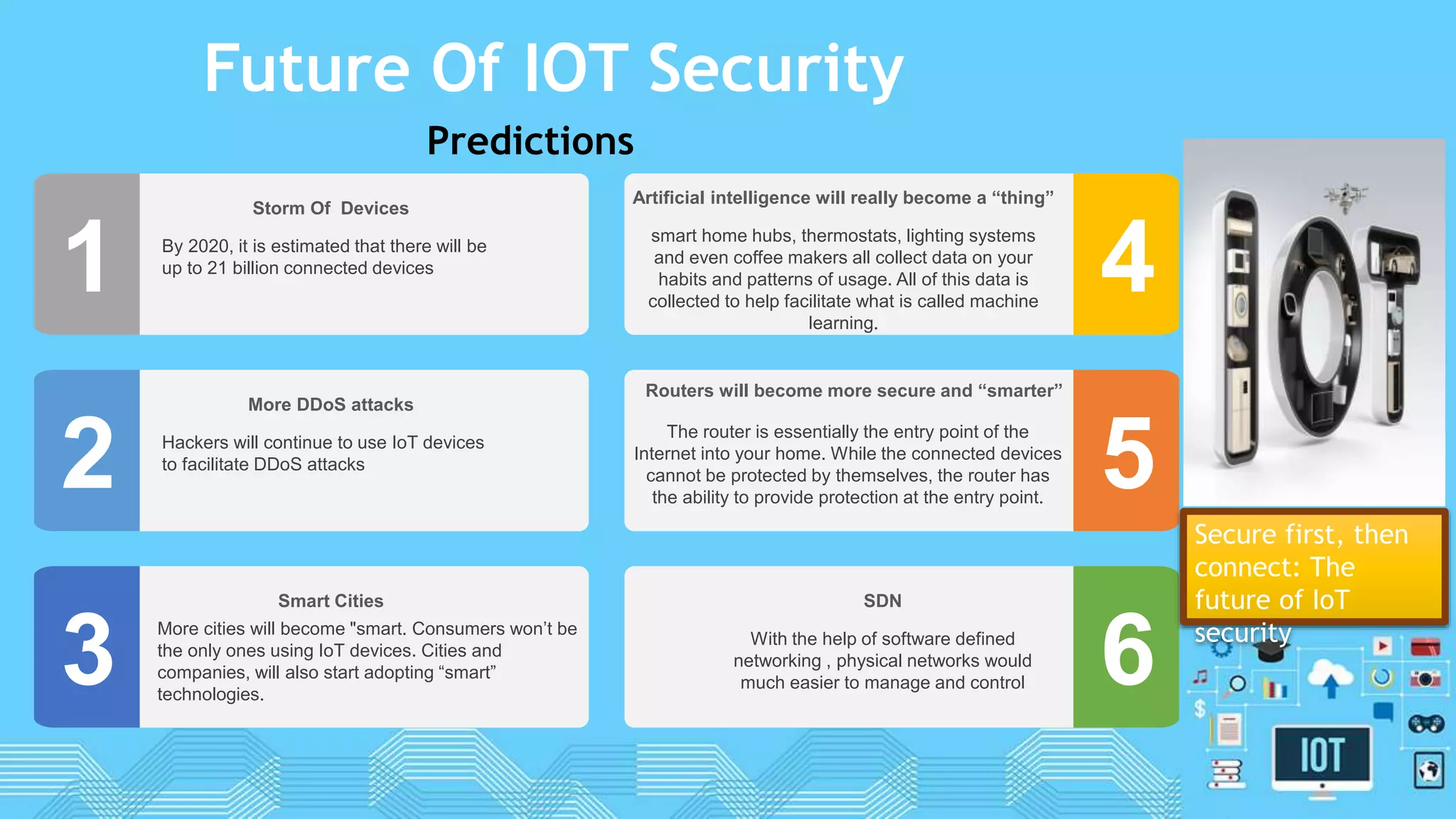
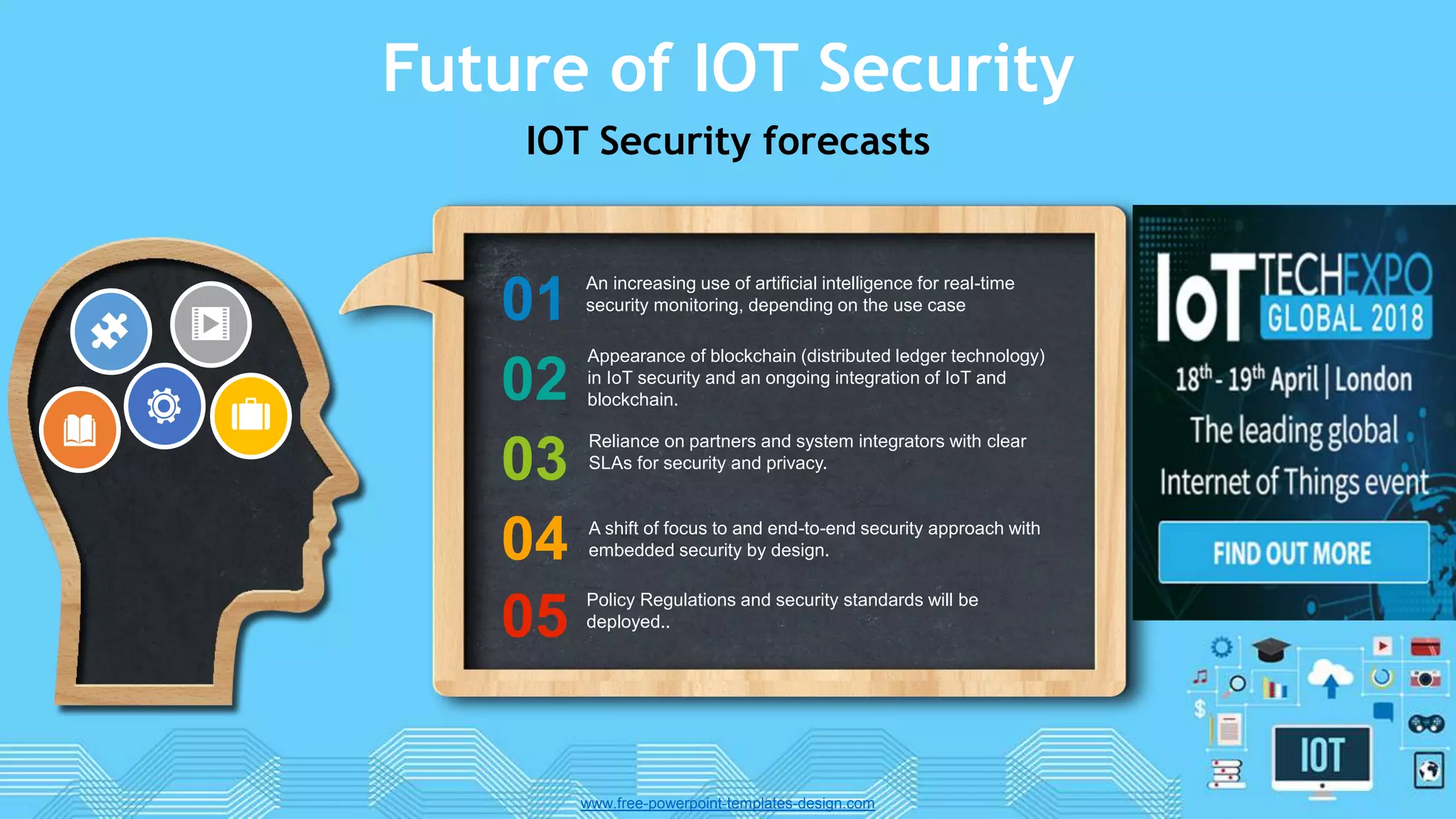
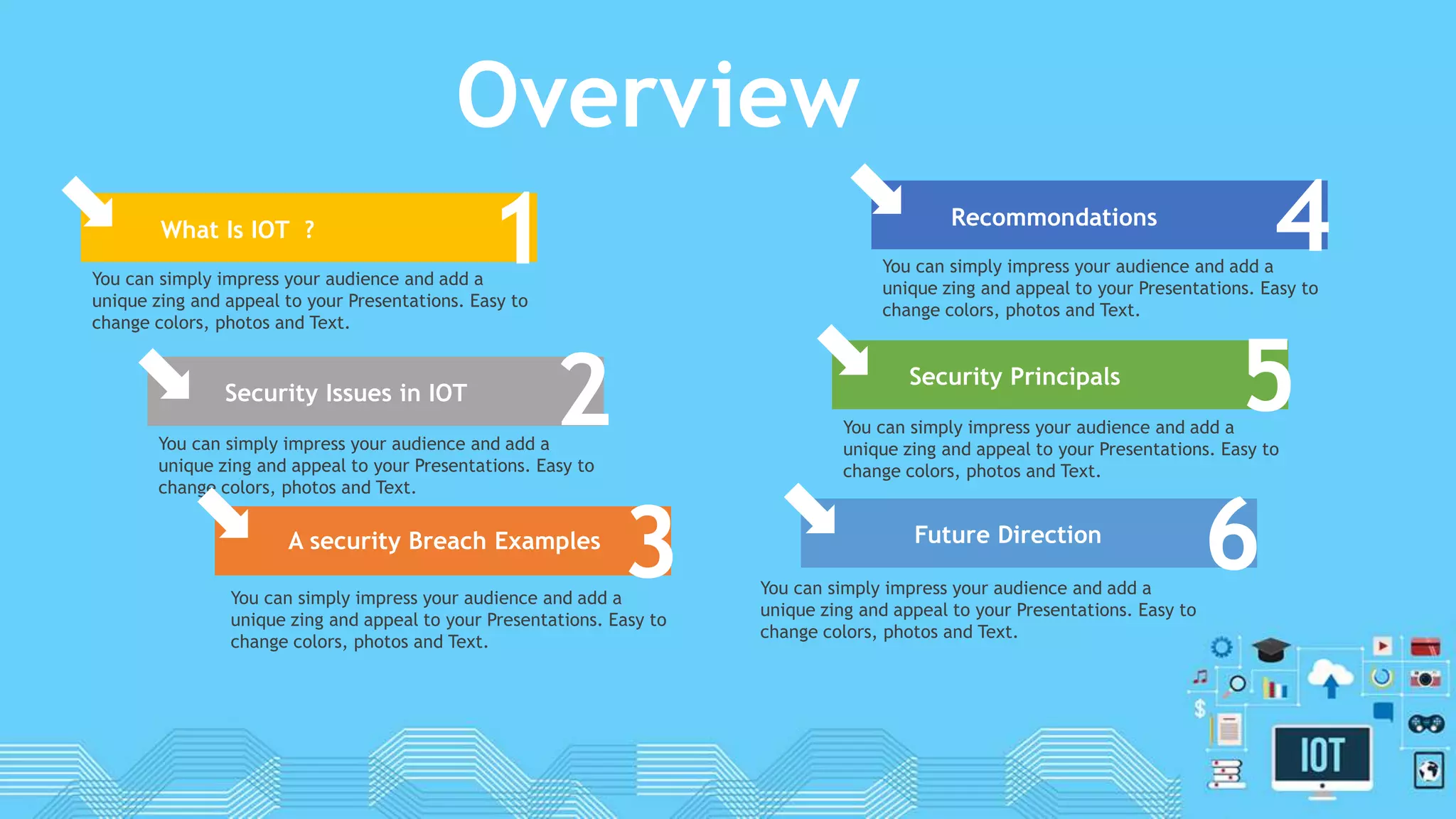
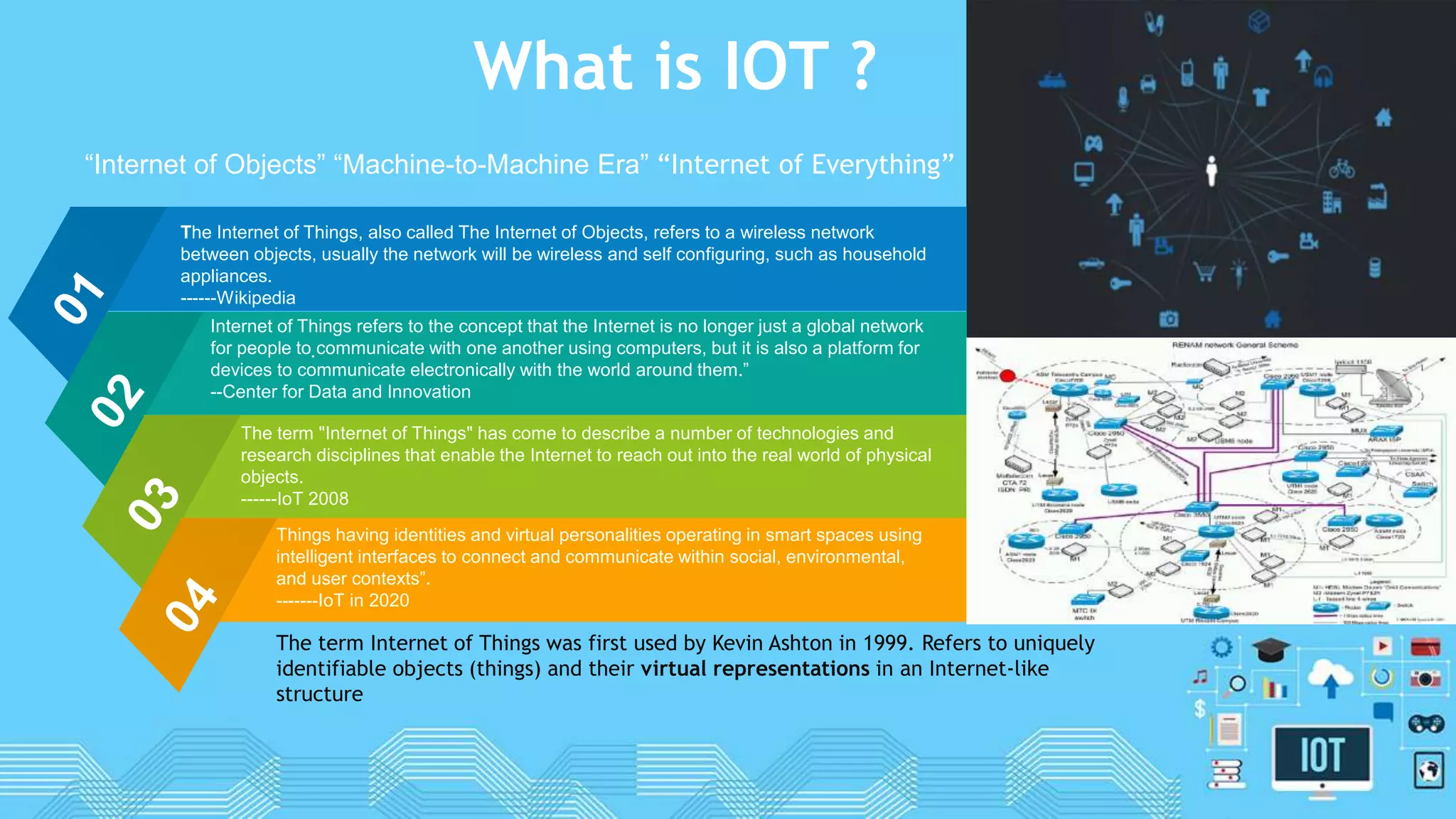
The document discusses internet of things (IoT) security. It begins by defining IoT and its security issues, including privacy, access control, policy enforcement, trust, mobile security, secure middleware, authentication and confidentiality. Examples of security breaches are provided. Recommendations for IoT security include designing for security, making devices more user-friendly, emphasizing technical knowledge, and re-evaluating business structures. Security principles like the Australian Privacy Principles and OWASP principles are covered. Predictions for the future of IoT security include more devices and DDoS attacks, the rise of smart cities, more use of artificial intelligence, more secure routers, use of software defined networking, and an end-to
![Security Issues in IOT
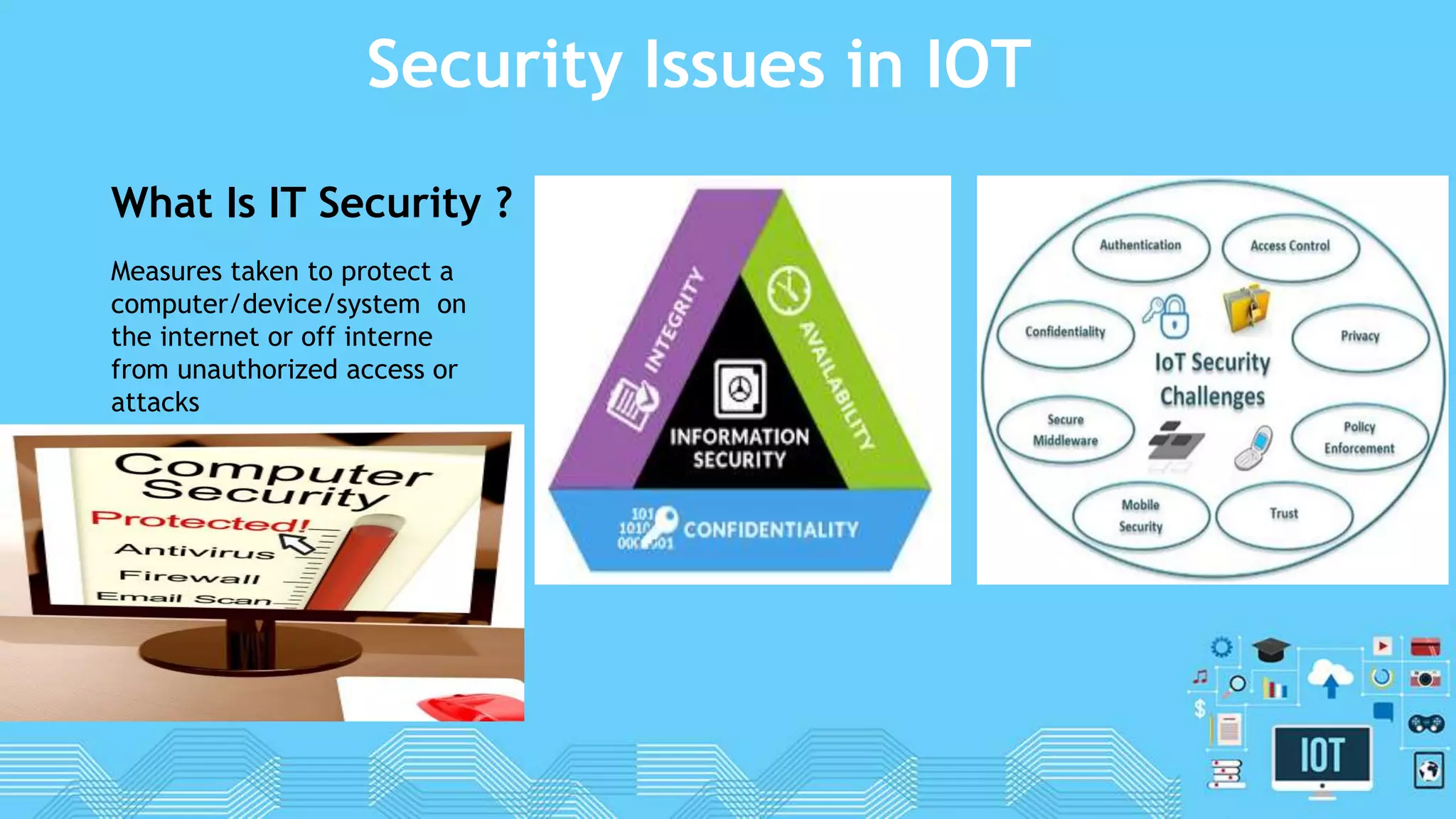
Privacy
The most dangerous part of IoT is
that consumers are surrendering
their privacy, bit by bit, without
realizing it,because they are
unaware of what data is being
collected and how it is being used.
Access Control
Access control deals with access
rights given to the things/devices in
IoT environment. In traditional
database systems, processing of
discrete data is done, however in IoT
processing of flowing data is done.
Some of the challenges related to
Access Control in IoT context involve:
How to handle the huge amount of
transmitted data (i.e., in the form of
stream data) in a common recognized
representation? How to support the
identification of?
Policy Enforcement
Policy enforcement refer to the
approaches used for the application of a
set of defined principals in a system.
Policies are set of defined rules which
desire to be acted for the purpose of
maintaining order, security, and
consistency on data. Only few works from
describe literature because of
Trust
The trust idea is used in different contexts
and with different explanations. Trust is a
complicated concept about which no
explanatory acquiescence endures in the
scientific literature, furthermore its
importance is dimensionally identified [7].
A core problem with many applications
towards trust description is that they do not
contribute themselves to the
demonstration of metrics and computation
methodologies.
Andrew Newman , CEO and Founder of Reason Software Company
“IoT security suffers today because the industry currently has many non-standard communication protocols,
making security for these devices incredibly complex.](https://image.slidesharecdn.com/internetiotsecurity-180612213101/75/Internet-iot-security-6-2048.jpg)
![Security Issues in IOT
www.free-powerpoint-templates-design.com
Mobile security
The common IoT vulnerabilities that I often see tie
into poor security on mobile applications," said
Deral Heiland, a veteran penetration tester
(pictured below) who leads Rapid7's IoT security
division[15]. "One of my biggest gripes is data
being stored on mobile apps.". What happens if a
worker simply loses a smartphone with valuable
data on it and that isn't backed up elsewhere?
Secure Middleware
The middleware has several tasks to
perform simultaneously, the primary
being to act as platform for different
technologies, protocols, network
environments, data replication. The top
vulnerabilities because of an insecure
middleware could be: Privacy concerns,
Insufficient authorization, Lack of
transport encryption, Insecure web
interface Inadequate software protection
Authentication & Confidentiality
Different works, describe different protocols and
mechanisms to deal with authentication of a user and
confidentiality of data in the context of IoT. IoT
enables a
constant transfer and sharing of data among things
and
users. In such a sharing environment, authentication,
authorization, access control and non-repudiation are
important to ensure secure communication.
Kyle Wilhoit, Senior Cybersecurity Threat Researcher at Domain Tools
“Any unsecured web-connected device could give cybercriminals an access point to the “backbone”
of a home’s computer network, and lead to the compromising of more important devices.](https://image.slidesharecdn.com/internetiotsecurity-180612213101/75/Internet-iot-security-7-2048.jpg)