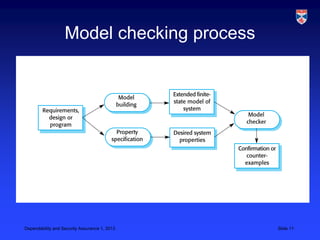
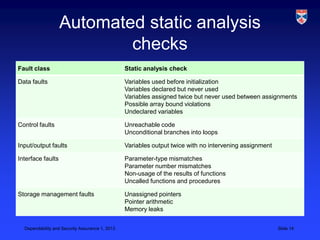
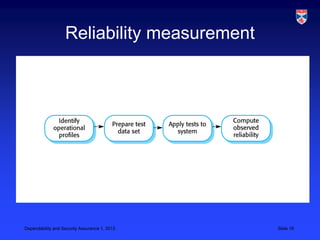
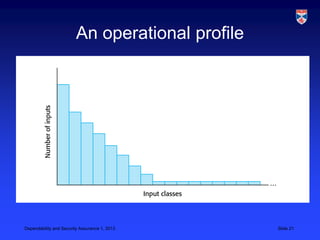
Critical systems require additional validation processes beyond non-critical systems due to the high costs of failure. Validation costs for critical systems are significantly higher, usually taking over 50% of development costs. Various static analysis techniques can be used for validation, including formal verification, model checking, and automated program analysis. Statistical testing with an accurate operational profile is also used to measure a critical system's reliability.