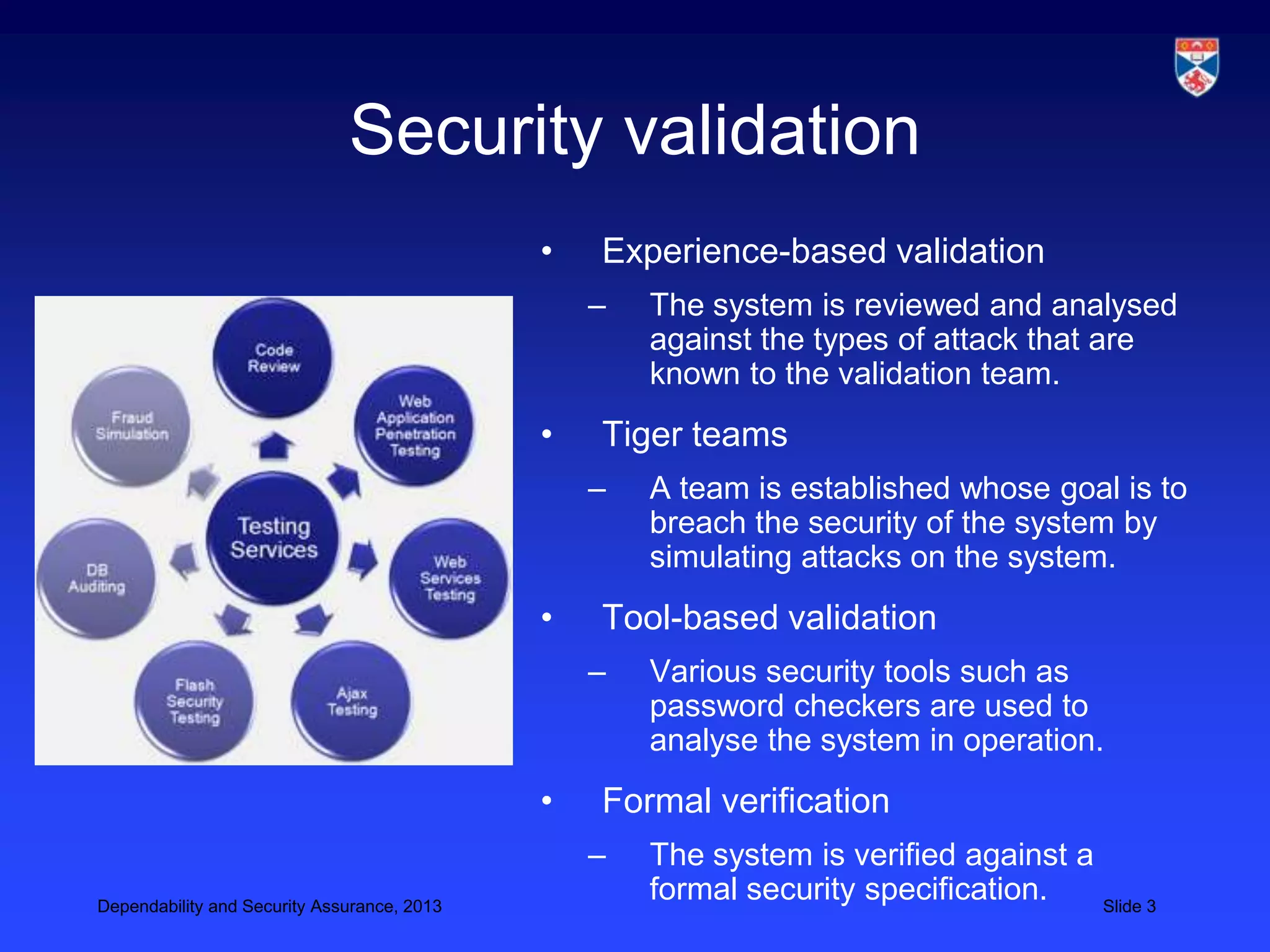
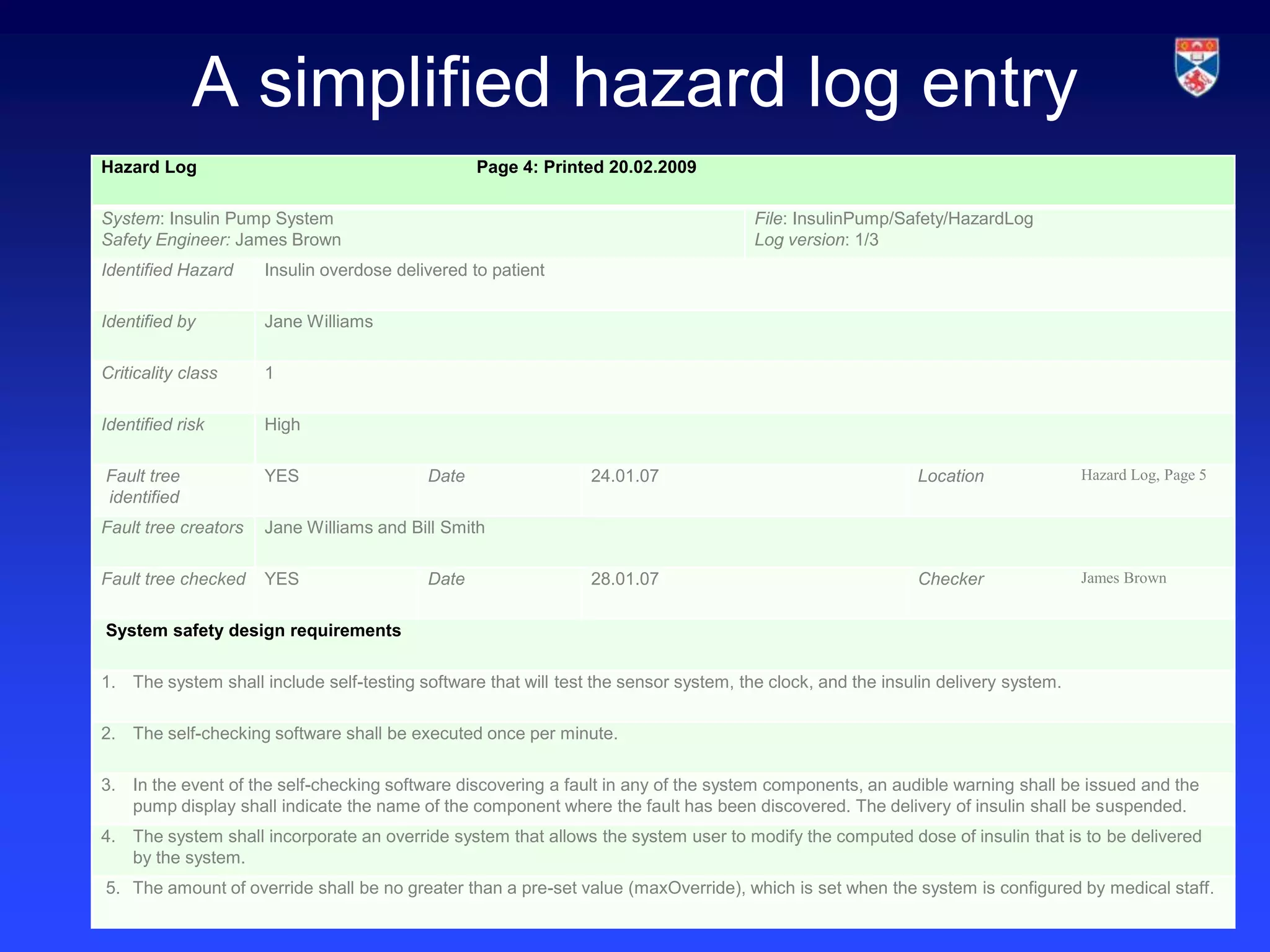
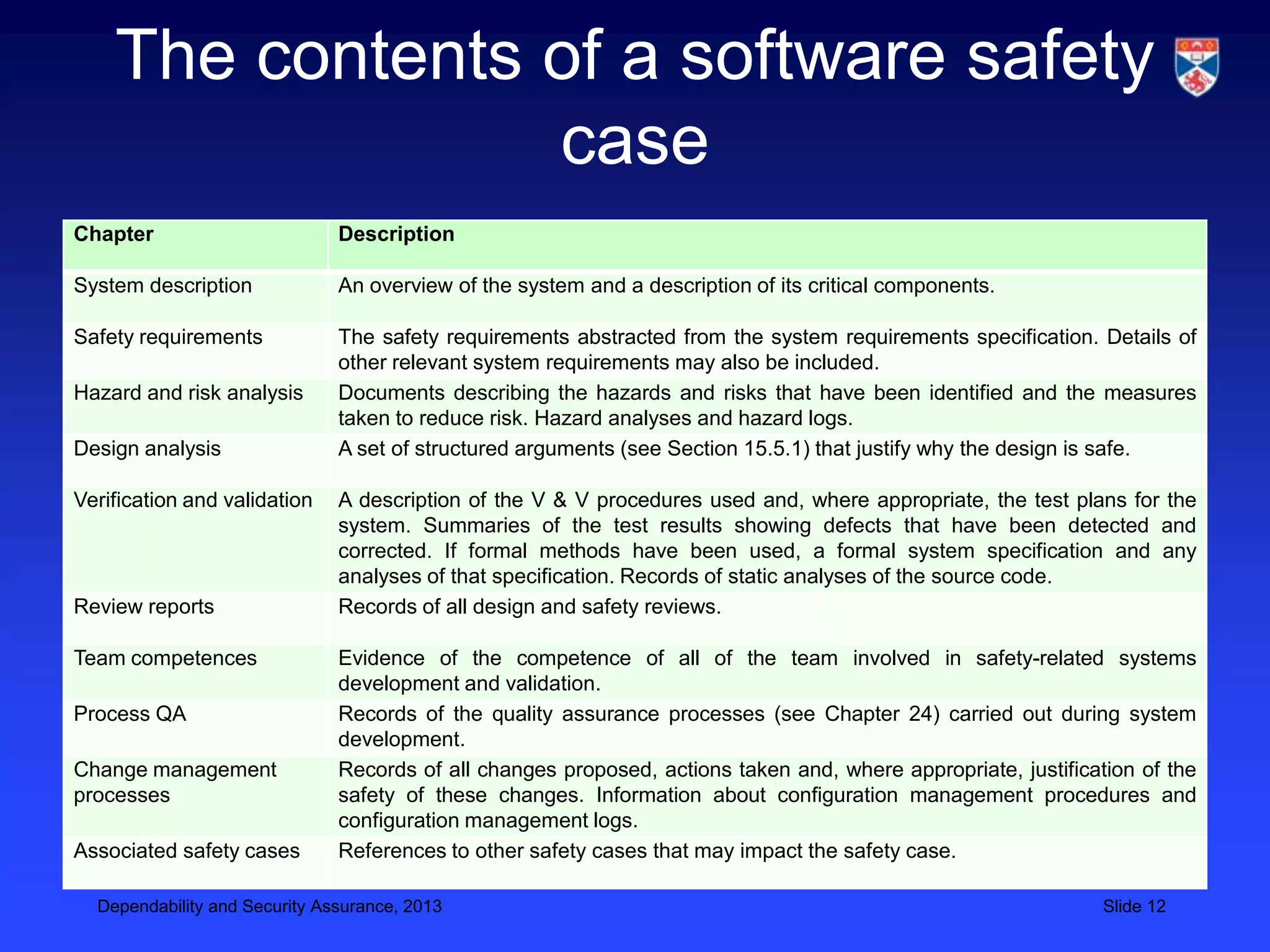
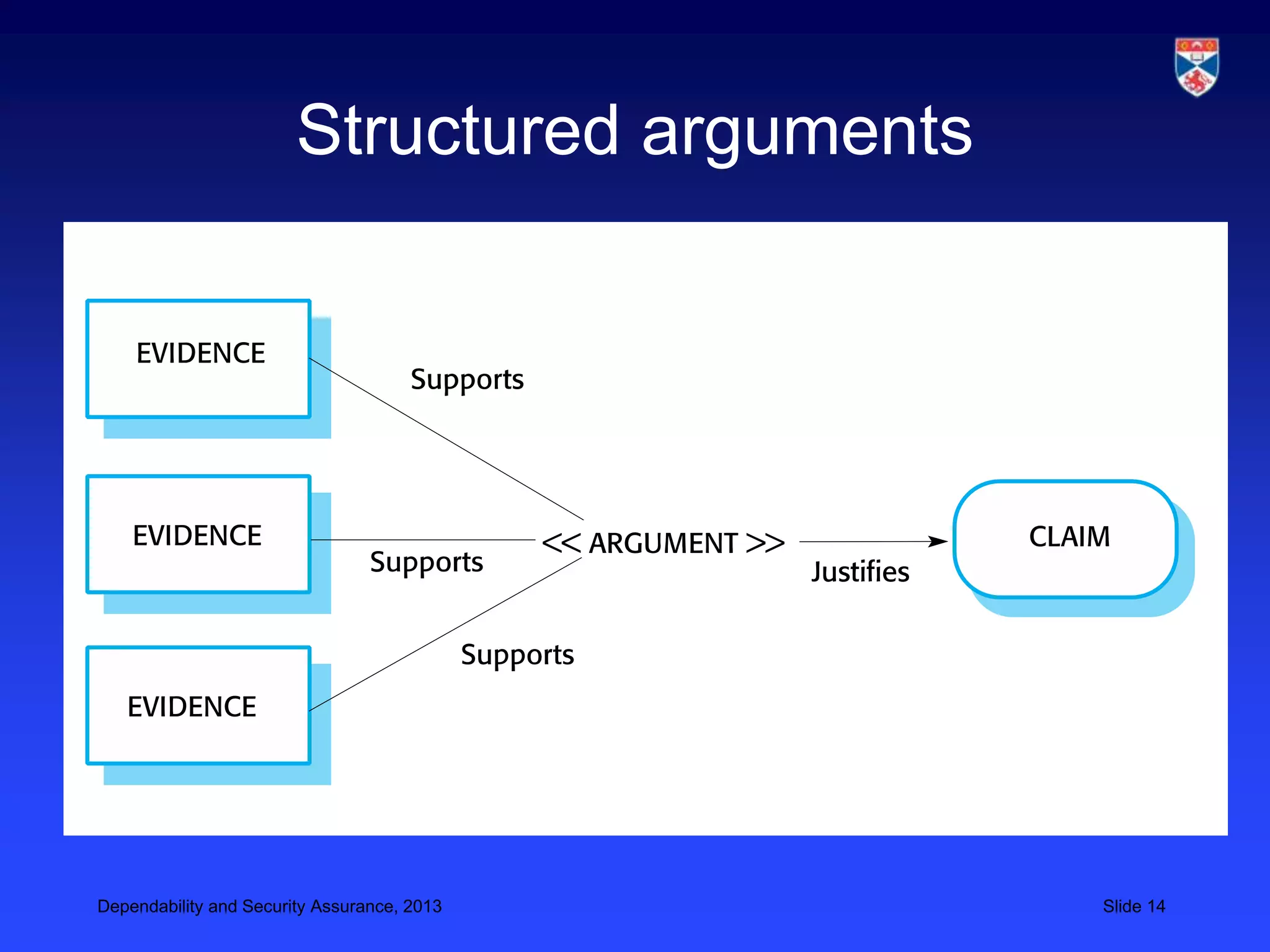
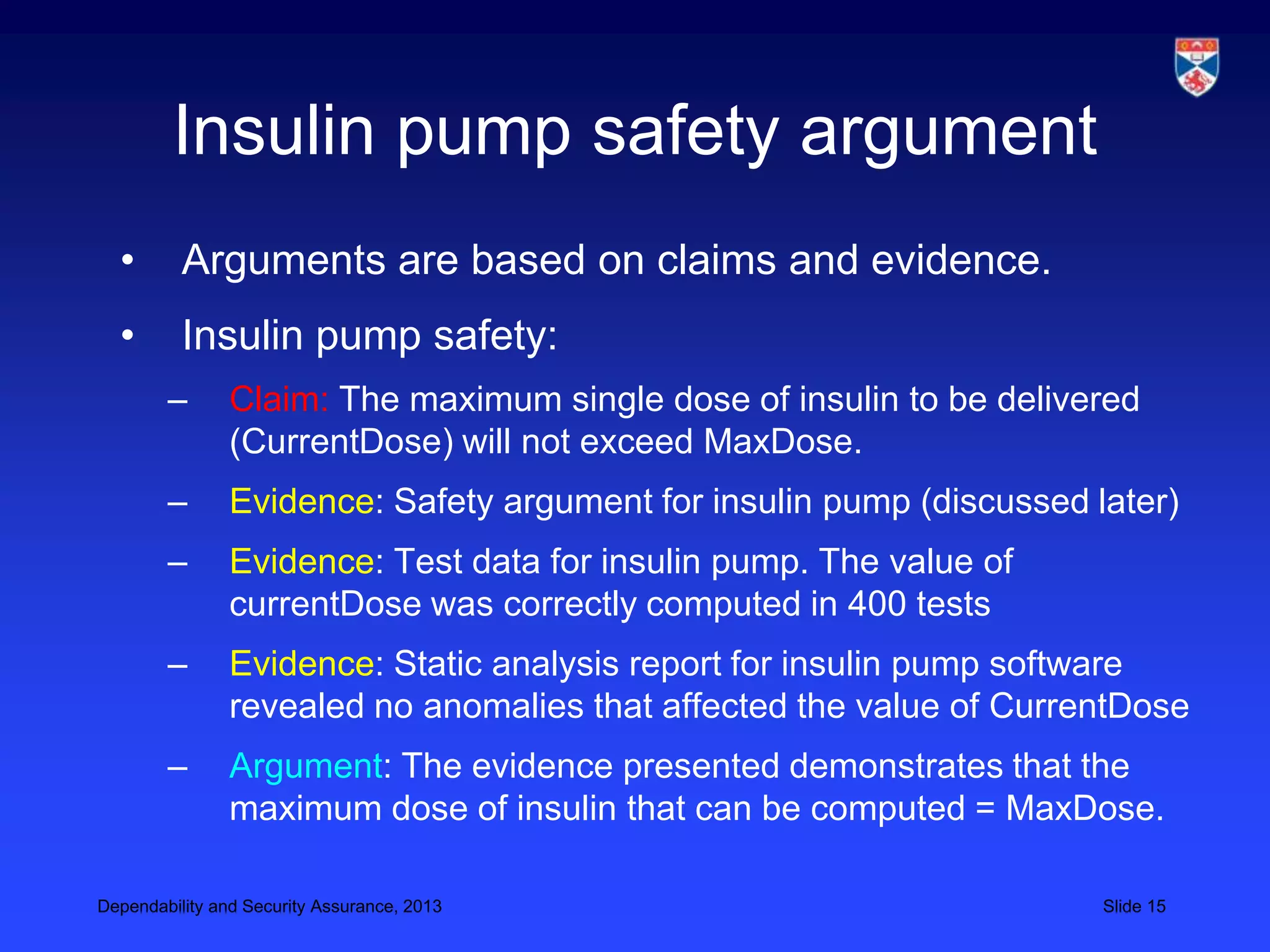
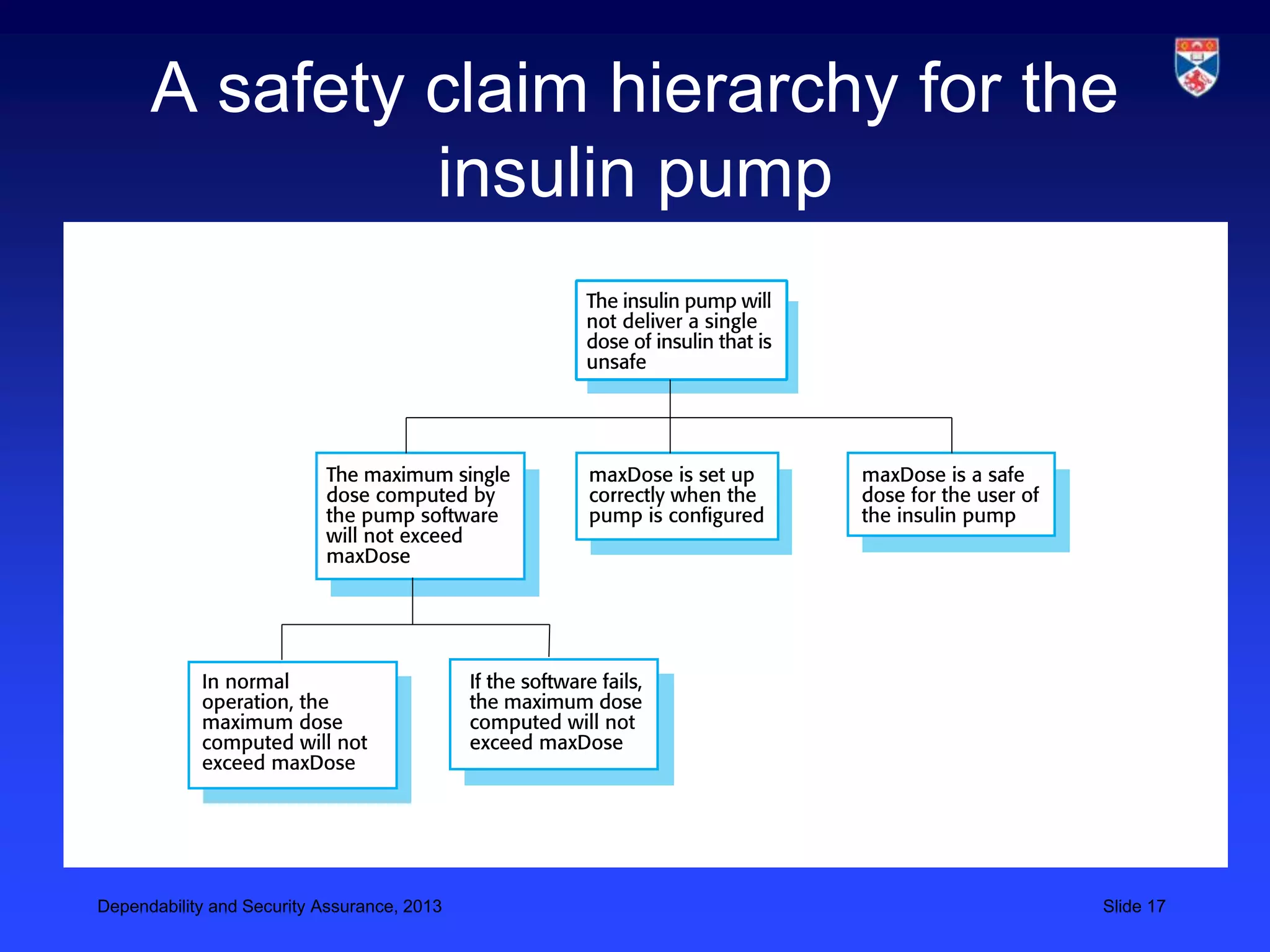
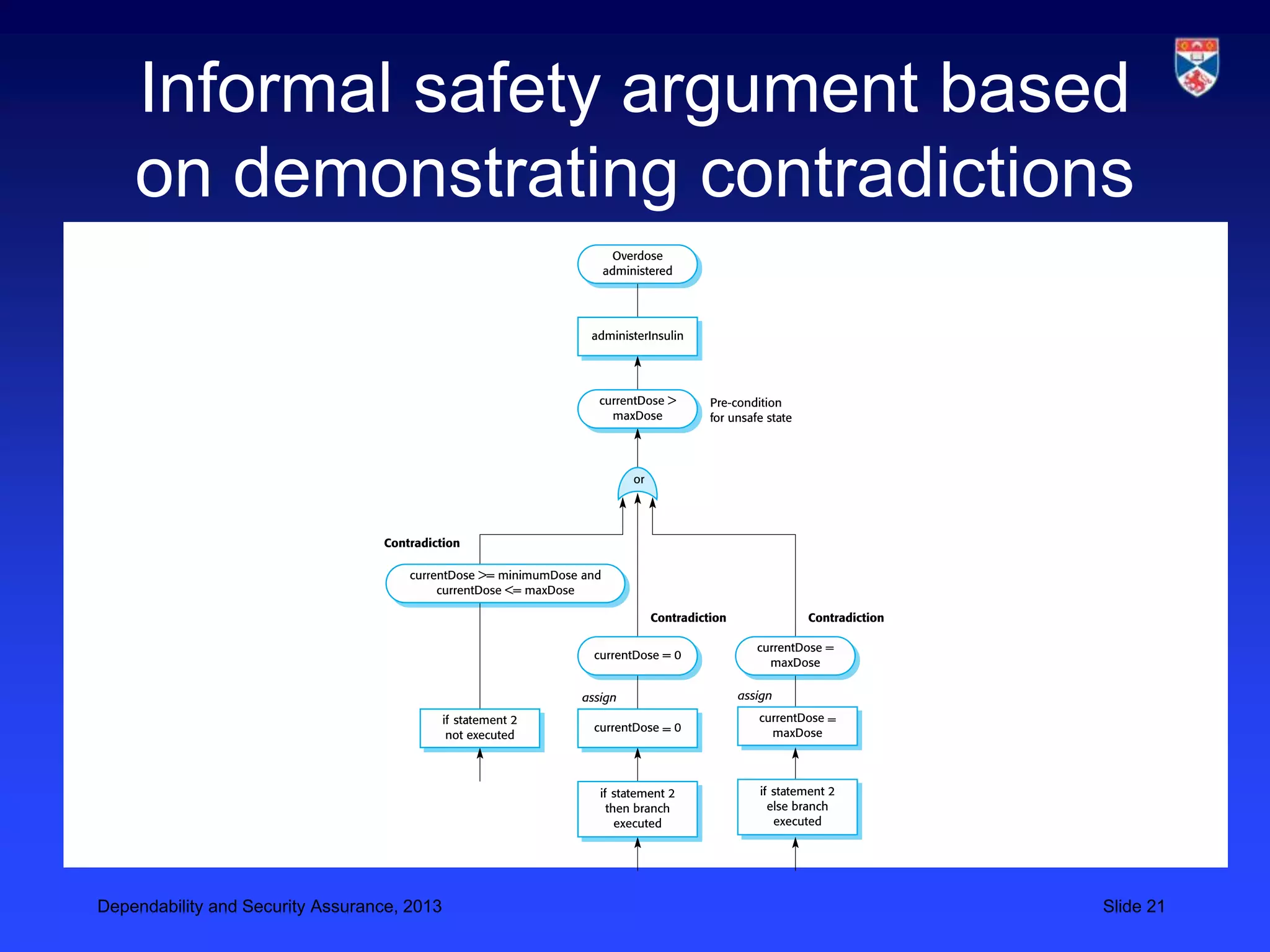
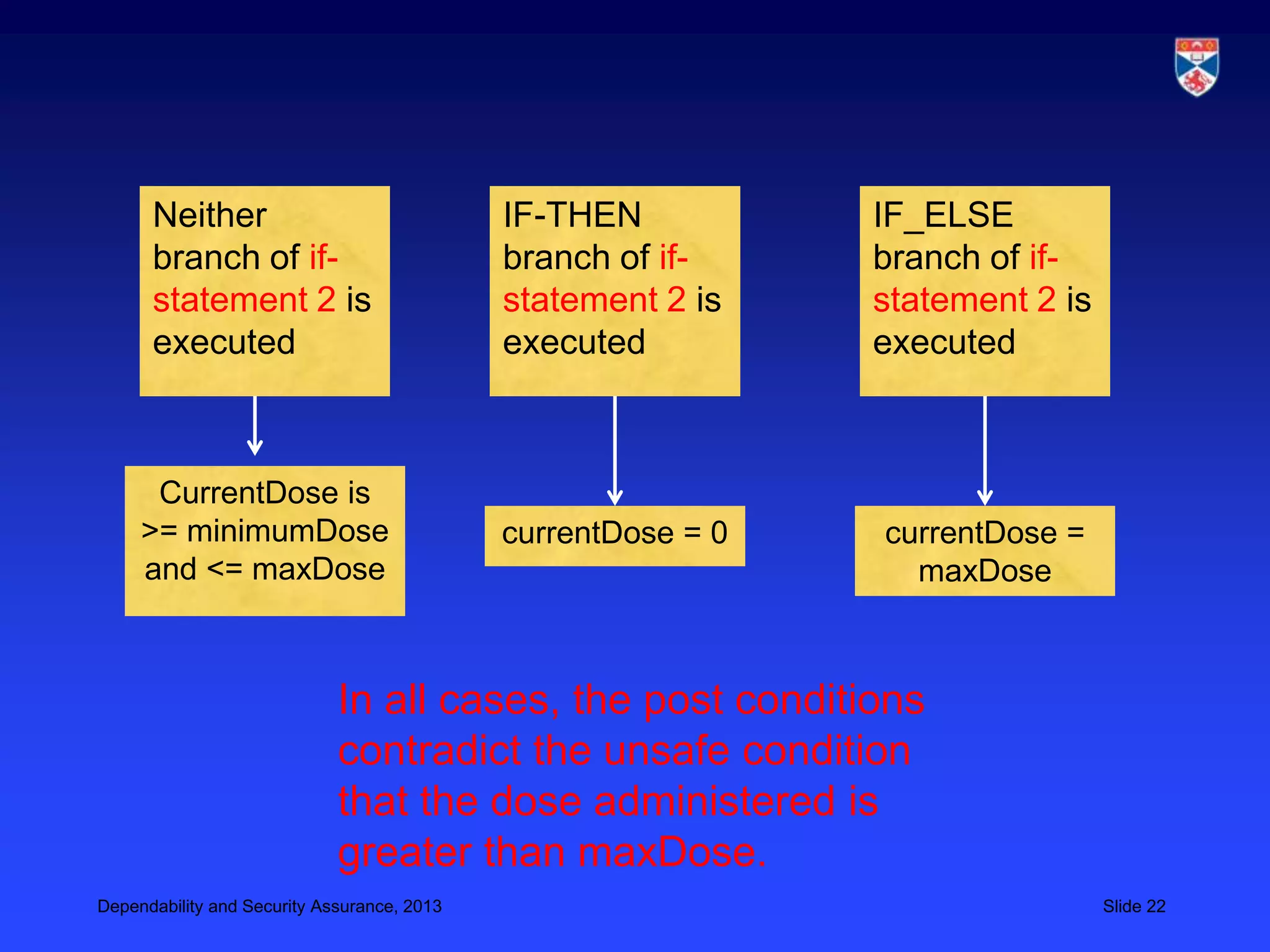
The document discusses security validation techniques like experience-based validation using known attacks, tiger teams that simulate attacks, and tool-based validation. It also discusses the importance of having a well-defined development process for safety-critical systems that includes identifying and tracking hazards. Safety and dependability cases collect evidence like hazard analyses, test results, and review reports to argue that a system meets its safety requirements. Structured safety arguments demonstrate that hazardous conditions cannot occur by considering all program paths and showing unsafe conditions cannot be true.