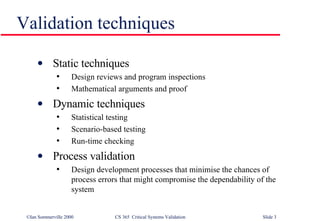
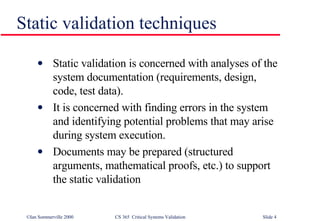
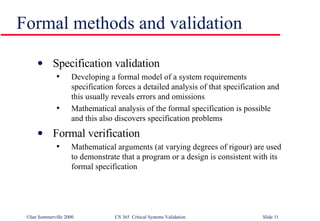
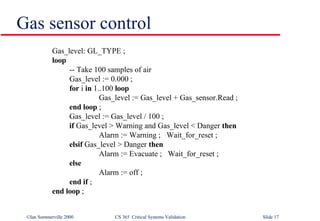
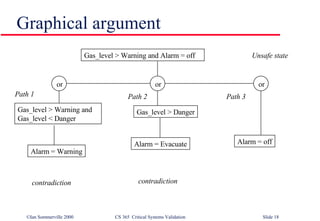
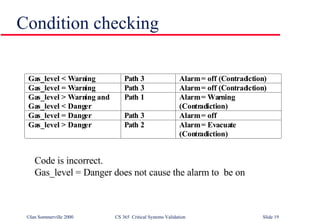
The document discusses techniques for validating critical systems, with a focus on validating safety and reliability. Static validation techniques include design reviews and formal proofs, while dynamic techniques involve testing. Reliability validation uses statistical testing against an operational profile to measure reliability. Safety validation aims to prove a system cannot reach unsafe states, using techniques like safety proofs, hazard analysis, and safety cases presenting arguments about risk levels. The document also provides an example safety validation of an insulin pump system.