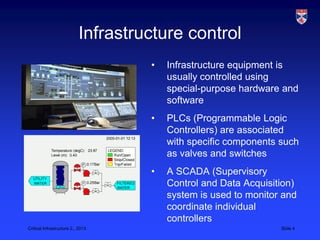
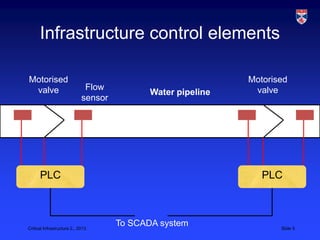
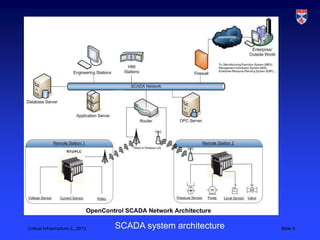
1) SCADA systems are used to monitor and control critical infrastructure through networks of sensors and programmable logic controllers.
2) These systems were traditionally isolated but are now increasingly connected to external networks, making them vulnerable to attacks.
3) Common vulnerabilities of SCADA systems include weak passwords, unencrypted network traffic, and lack of input validation. Improving SCADA security is challenging due to the operational needs of control systems and lack of security experience among operators.