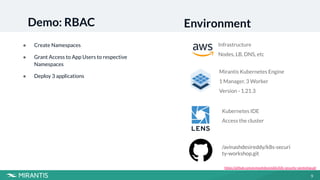
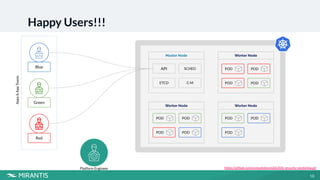
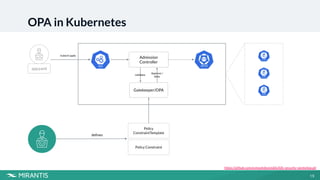
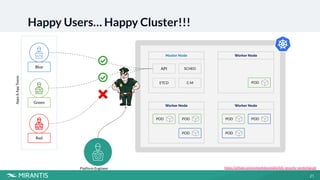
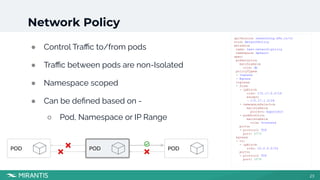
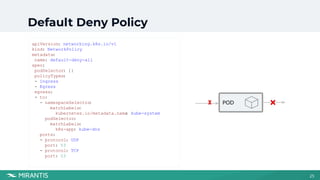
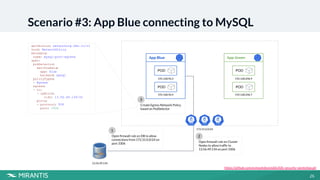
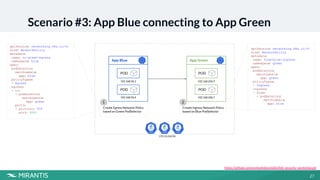
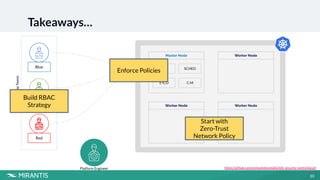
This document summarizes a workshop on Kubernetes security presented by Avinash Desireddy and Anoop Kumar. The workshop covered Role-Based Access Control (RBAC) to grant users access to Kubernetes resources, using Open Policy Agent (OPA) and Gatekeeper to enforce cluster-wide policies, and network policies to control traffic between pods. It provided demonstrations of creating RBAC roles, restricting node port usage and enforcing resource limits with OPA policies, and allowing traffic between applications with network policies. The key takeaways were to enforce policies, build an RBAC strategy, start with a zero-trust approach, and use network policies.



![8
https://github.com/avinashdesireddy/k8s-security-workshop.git
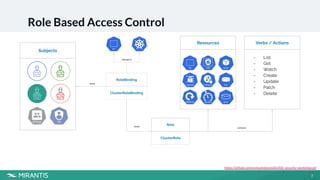
ClusterRoleBinding
RoleBinding
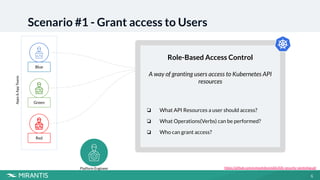
Role Based Access Control
- List
- Get
- Watch
- Create
- Update
- Patch
- Delete
Verbs / Actions
Subjects
Resources
Role
ClusterRole
belongs to
binds
binds
connects
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: role-blue
namespace: blue
rules:
- apiGroups: ["", "apps"]
resources: ["deployments", "services"]
verbs: ["create", "delete", "list"]
apiVersion:
rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: blue-rb
namespace: blue-ns
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: blue
roleRef:
kind: Role
name: role-blue
apiGroup: rbac.authorization.k8s.io](https://image.slidesharecdn.com/mirantis-protalk-kubernetes-security-workshop-220419214742/85/Kubernetes-Security-Workshop-8-320.jpg)